New VLAN not receiving DHCP address from its own pool
-
If the workstation is connected to port 1, what port is connected to the pfSense interface?
No. Please don't bridge anything.
What, exactly, are you trying to do.
-
@jahnieboi said in New VLAN not receiving DHCP address from its own pool:
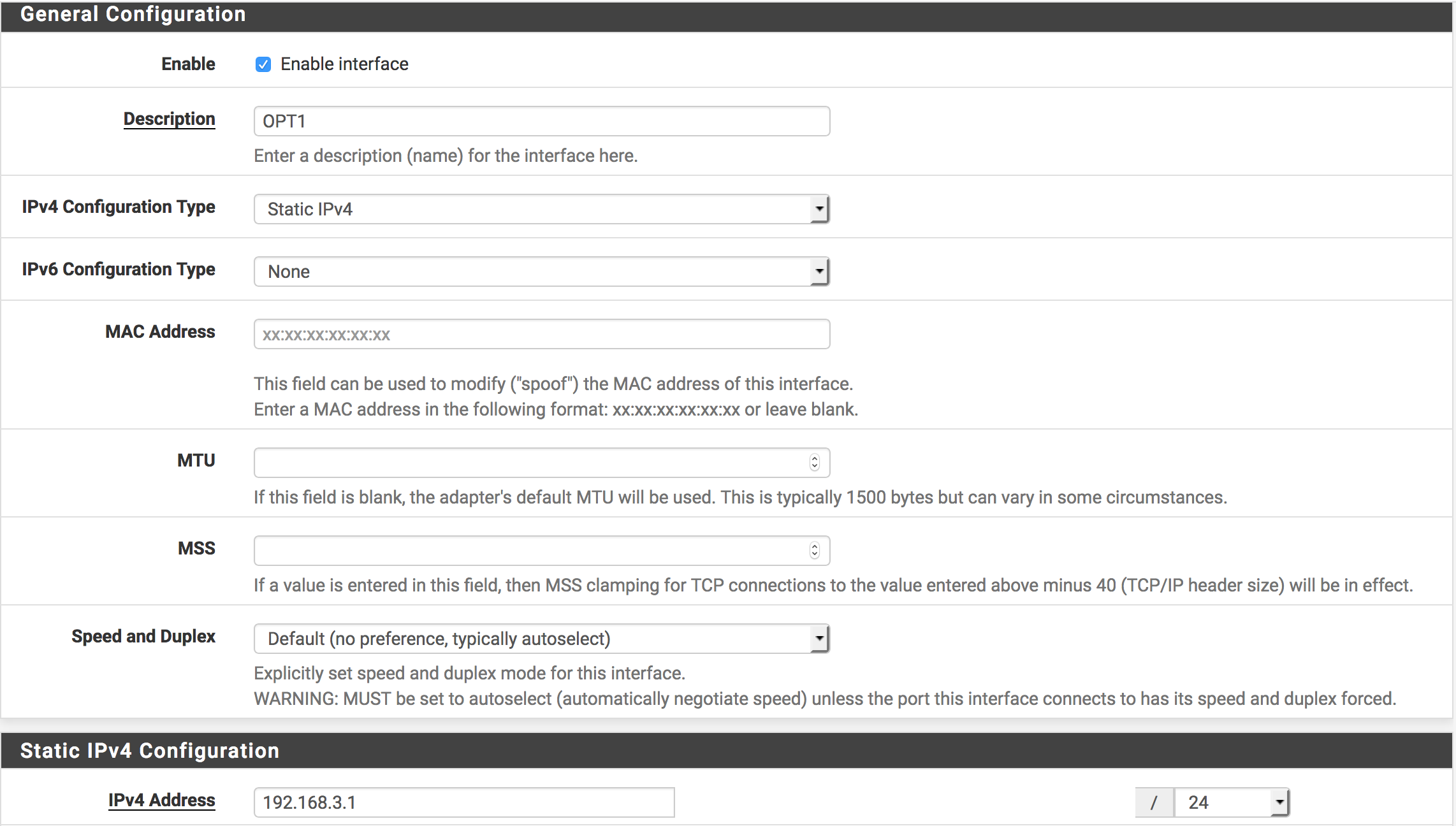
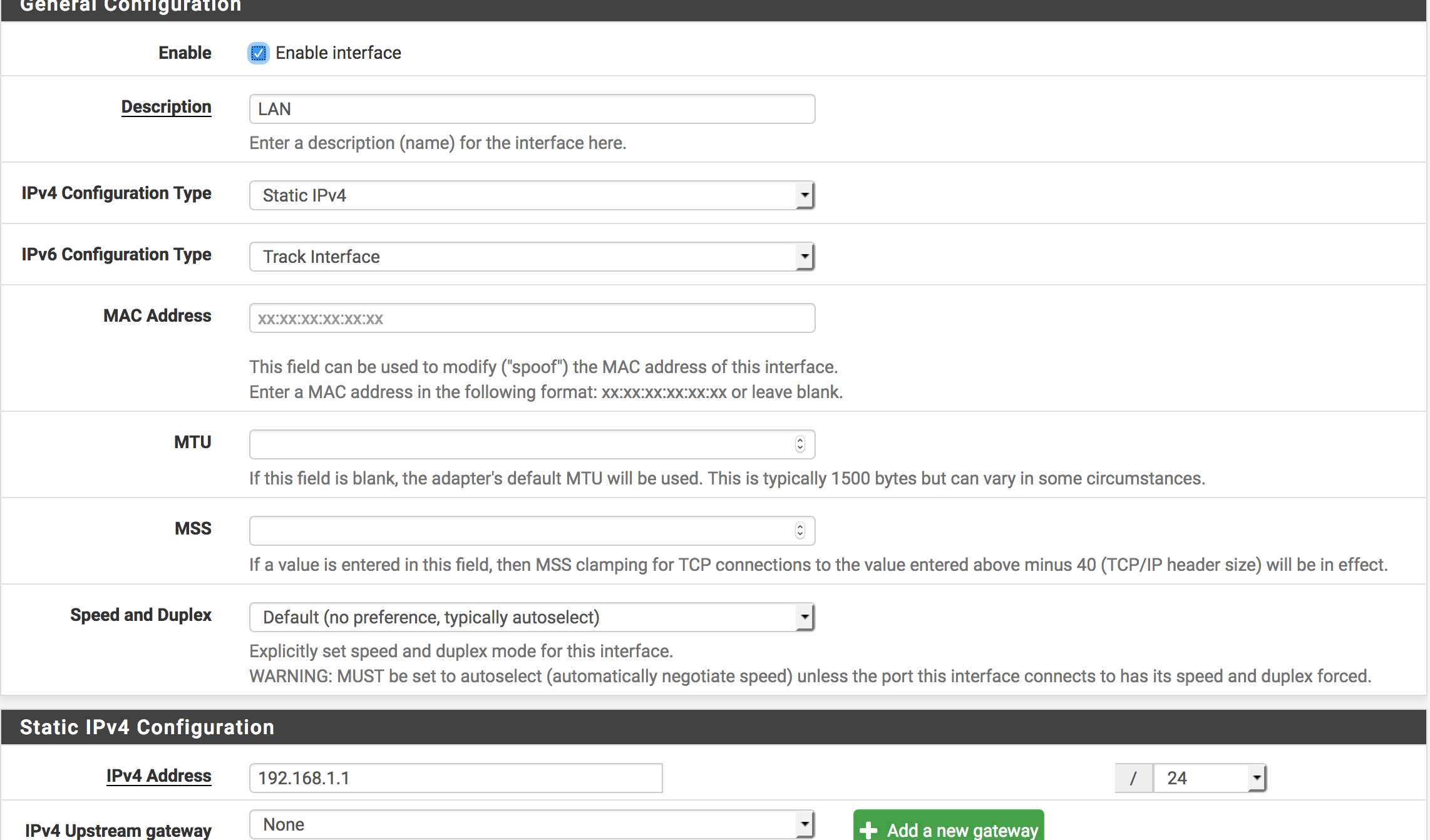
LAN (network port em1 - 192.168.1.0/24)
VLAN (40 on em1 - 192.168.3.0/24)That results in this on em1:
LAN - untagged
VLAN - Tagged VLAN 40That needs to be connected to a switch port that is untagged VLAN 1, Tagged VLAN 40, and has its PVID set to 1.
If you want a workstation to be on VLAN, it needs to be connected to a switch port that is untagged on VLAN 40 and has its PVID set to VLAN 40.
If you want a workstation to be on LAN it needs to be connected to a switch port that is untagged on VLAN 1 and has its PVID set to VLAN 1.
-
@derelict @johnpoz - All I want to do is create a new VLAN (40), which is isolated and contained.
The LAN net (1) has full access going into the VLAN (40), but the VLAN (40) doesn't have access to the LAN (1). One-way trust relationship.
I also have OpenVPN configured, which would only have access to the VLAN (40).
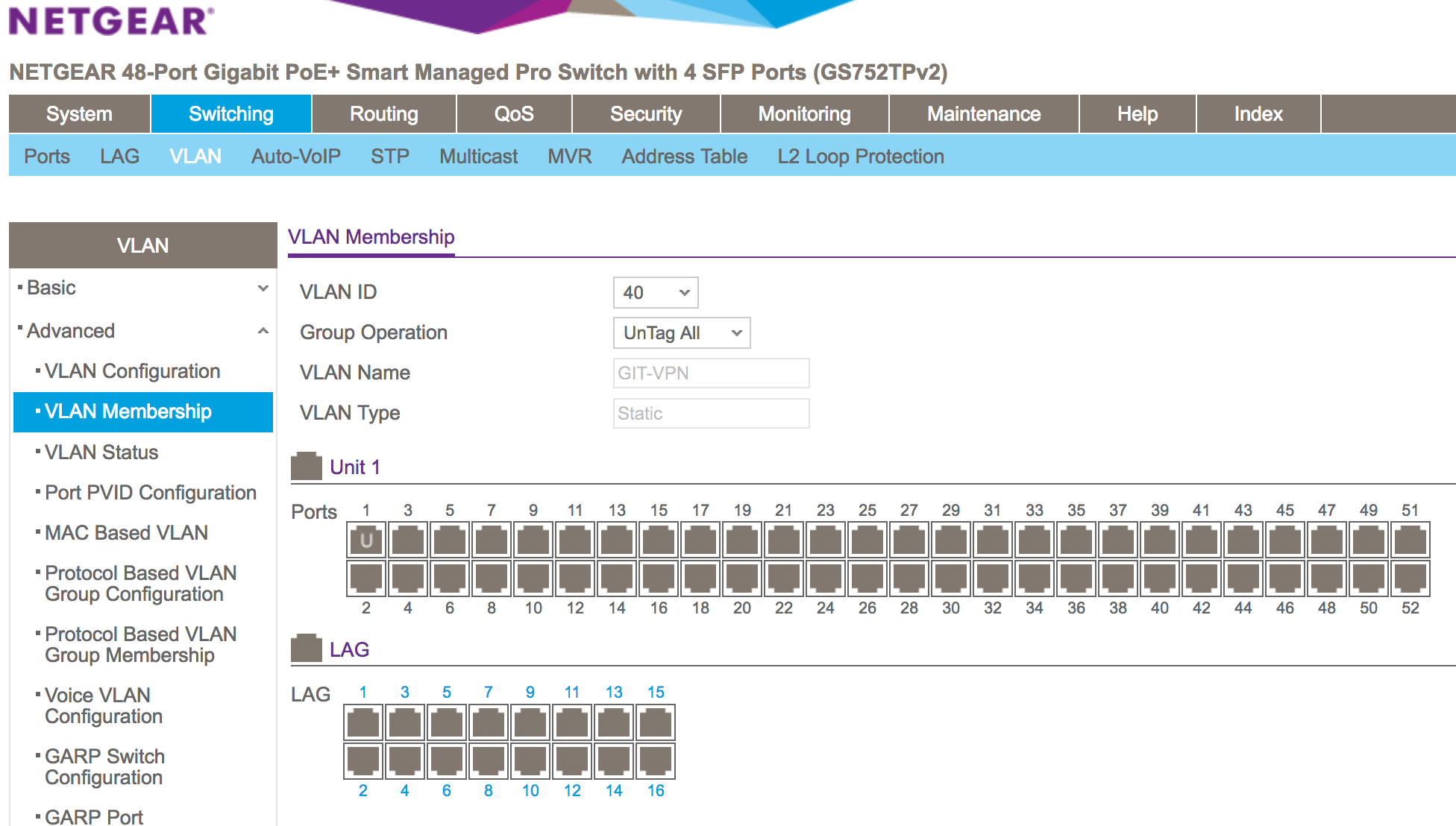
I've made the correction with port tagging. Right now, port 1 on the Netgear switch is set as VLAN 1 untagged and VLAN 40 Tagged.
I'm still experiencing the issue with port 1, only receiving DHCP address from VLAN (1)'s pool. It's not getting any addresses from VLAN (40)'s pool.
When I configure the workstation connected to port 1, with a static IP address of VLAN(40) - it's unable to route and can't even ping it's own gateway (192.168.3.1).
-
@derelict - The pfSense interface is connected to port 48.
-
I'm getting closer!
"If you want a workstation to be on VLAN, it needs to be connected to a switch port that is untagged on VLAN 40 and has its PVID set to VLAN 40." - This is what I need to do and this is what I did, but this time - I did set the PVID to 40 and this time, when I configure a static IP address ... I'm able to now ping the gateway.
However, I can't ping the LAN(1) gateway and can't browse the internet. I've checked the firewall settings and everything looks good there. Anything else that I may need to do?
Also - Thank you for being patient and Thank you for being responsive and supportive!!!
-
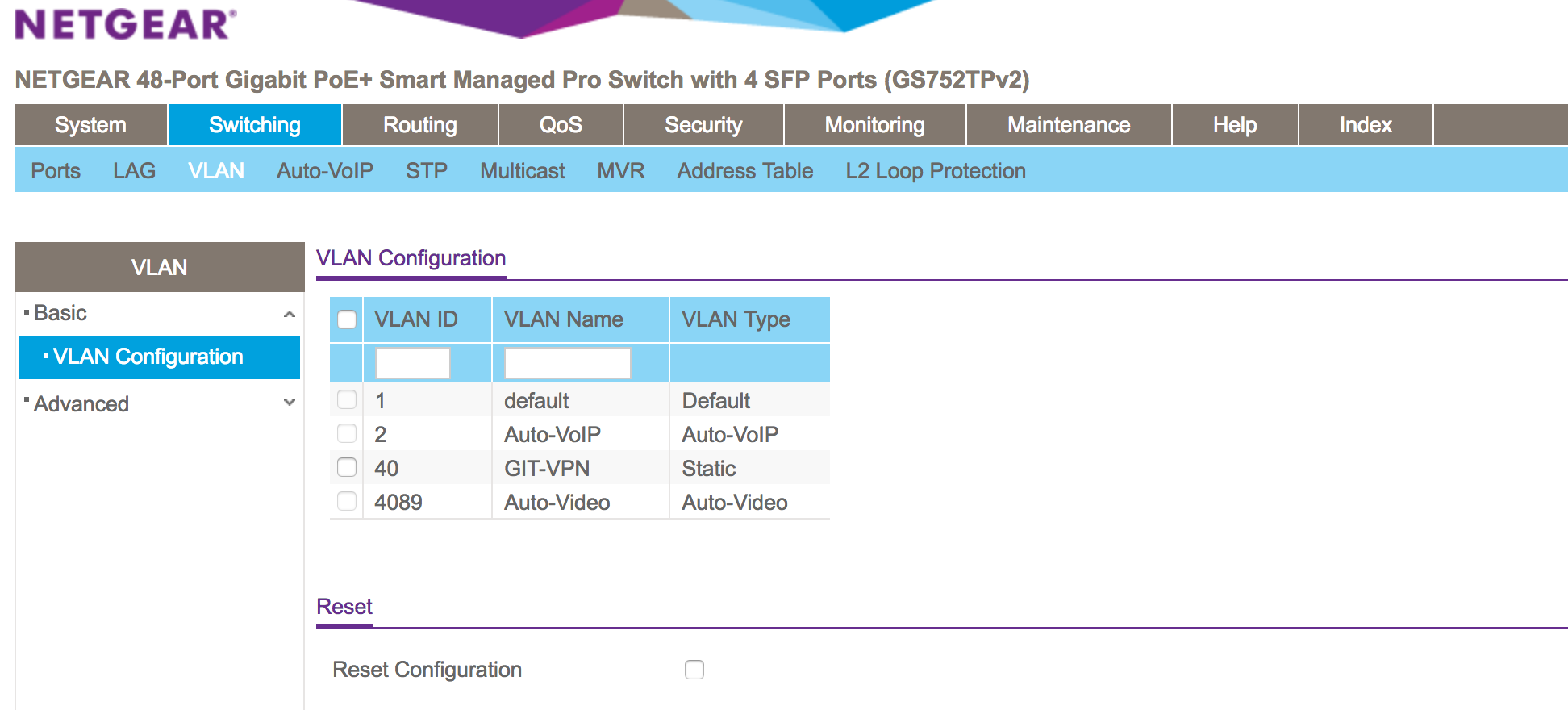
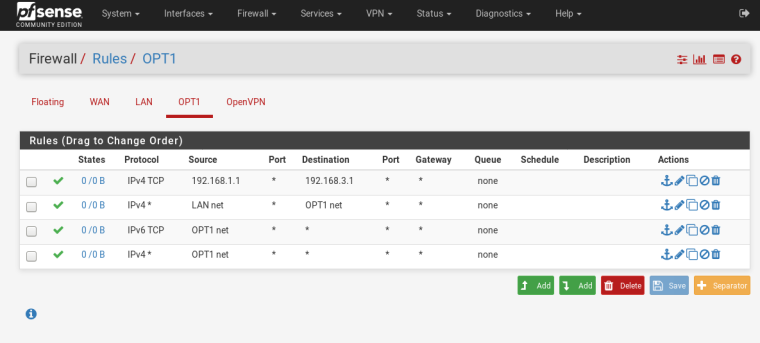
Those rules make no sense..
When would 192.168.1 be source into your opt network of 192.168.3?
When would lan net be a source into opt net? On your vlan interface?your only rule that really makes any sense the last which is opt net any any..
This would allow opt net to go anywhere, internet or lan.. If internet is not working did you mess with outbound nat. Automatic would of allowed your opt1 network to be natted to your wan.
Rules are evaluated as traffic enters an interface from the network its connected too. Top down, first rule to trigger wins.. No other rules are evaluated..
Do you have any rules setup on floating - since none of these rules show any hits, the 0/0 B on the left of your rules..
-
@johnpoz - ur right, out of desperation I added those on top, hoping that maybe it would work!
I removed those - Thanks for the review.
-
Your ipv6 is tcp only... Which you need icmpv6 for ipv6 to function... But pretty sure pfsense adds those in the background when you put ipv6 on the interface.
Derelict told you exactly how to configure the ports connected to both pfsense em1 and the the port your device is connected.. End devices like a PC almost never have any sort of vlan tag set.. They are almost always untagged. Exception might be if you were running say VMs on the box, etc. Or it was routing, etc. etc.
pfsense - 1 UP, 40 T -- switch -- 40UP - PC
That is all there is too it.. .
U = untagged
T = Tagged
P = PVID..PVID is the vlan a switch uses for traffic that hits the interface untagged..
-
@johnpoz - Thank you so much for the clarification and for taking time to explain things.
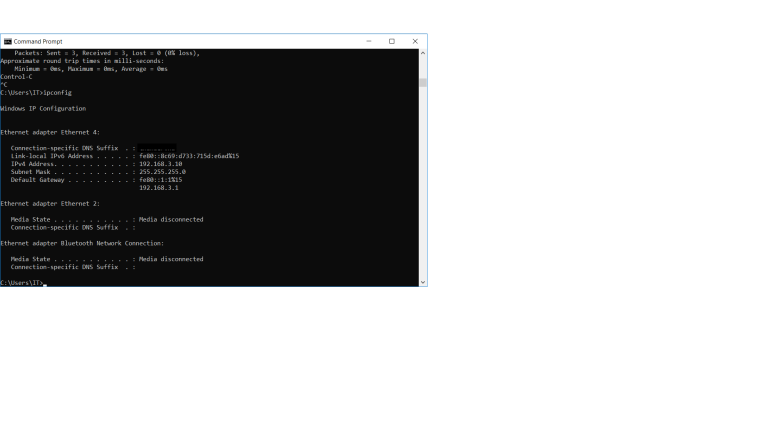
I've now made all of these corrections and I'm at least now able to ping from the PC (192.168.3.10) to the gateway (192.168.3.1) - also getting a response.
However, I'm unable to ping from the PC (192.168.3.10) to the gateway of the default LAN on em1 (192.168.1.1).
From my other computer that's on the main LAN (192.168.1.0/24), I'm able to ping the gateway on the VLAN (192.168.3.0/24), but I'm unable to ping the PC (192.168.3.10).
What am I missing? :(
Again - Many Thanks for your help!!
-
@jahnieboi said in New VLAN not receiving DHCP address from its own pool:
However, I'm unable to ping from the PC (192.168.3.10) to the gateway of the default LAN on em1 (192.168.1.1).
From my other computer that's on the main LAN (192.168.1.0/24), I'm able to ping the gateway on the VLAN (192.168.3.0/24), but I'm unable to ping the PC (192.168.3.10).
There is nothing in the rules that will stop that ping from working.
Most likely suspect is the default gateway set on the source PC (192.168.3.10) itself.
The latter problem could possibly also be a firewall on 192.168.3.10 itself preventing connections from subnets other than its own. It could also be the default gateway setting there.
-
That's what's confusing me. I had put in the correct default gateway on the PC and I've disabled the local firewall on the PC as well.
Any other thoughts? ;-P
-
You'll need to post everything. ipconfig/ifconfig, firewall rules as they exist now, switchport VLAN configurations, etc.
There are only so many things it can be and we've already given you about everything so something must be not set like you think it's set.
-
PC ipconfig output:
Firewall Rules:
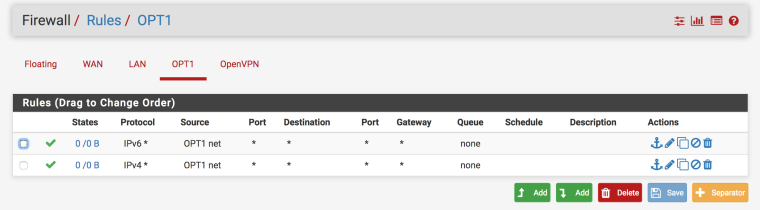
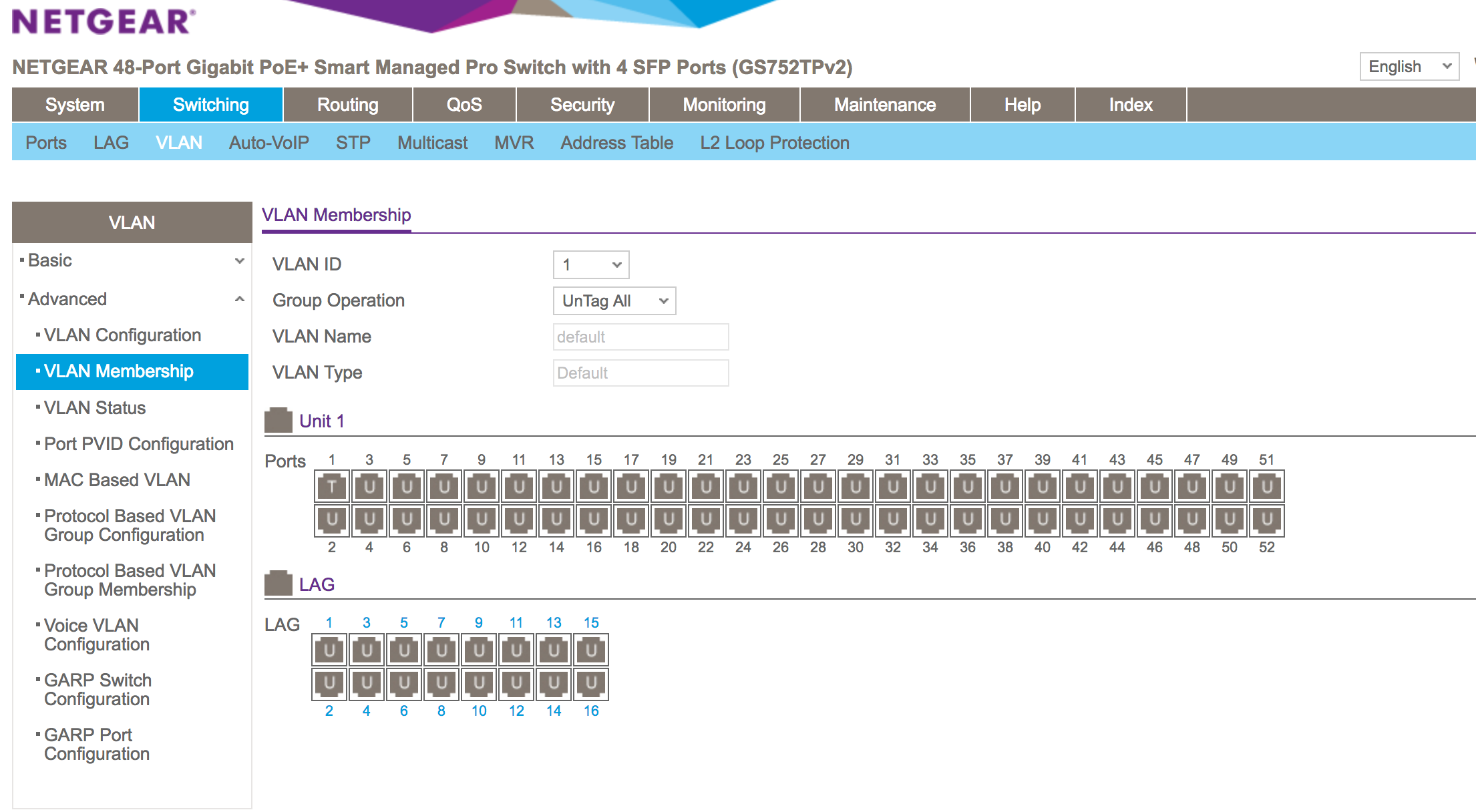
Switch Port config (Netgear):
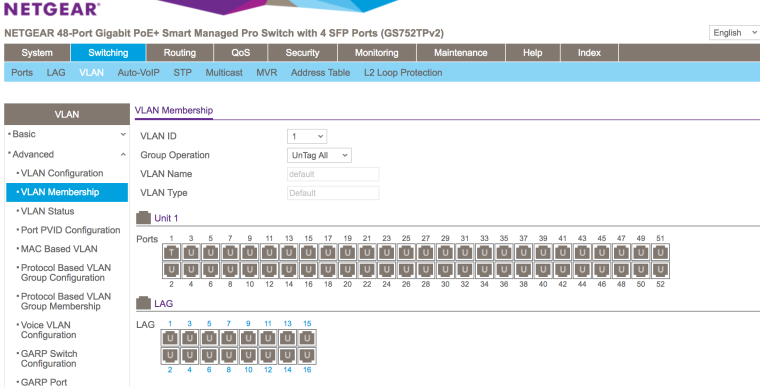
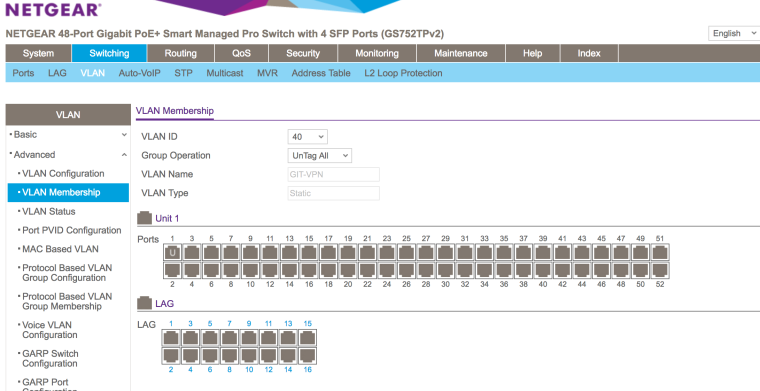
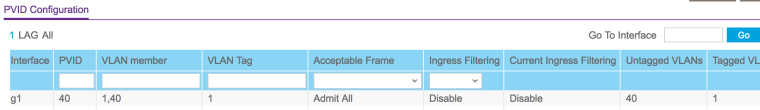
Please let me know if I missed anything or if you need anything else.
Again - Thank you so much!!!! :)
-
OK
What switch port is connected to the workstation?
What switch port is connected to pfSense?
-
Switch port 1 is connected to the PC
< and >
Switch port 48 is connected to pfSense (em1).
-
OK. I see no VLAN configuration on port 48. Why not?
[pfSense] needs to be connected to a switch port that is untagged VLAN 1, Tagged VLAN 40, and has its PVID set to 1.
-
I didn't know it was needed. I didn't want to interrupt the main network. Since port 48 is em1, which is the main LAN.
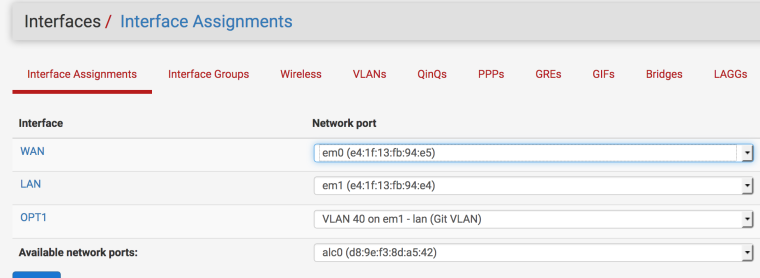
I went ahead and made this change:
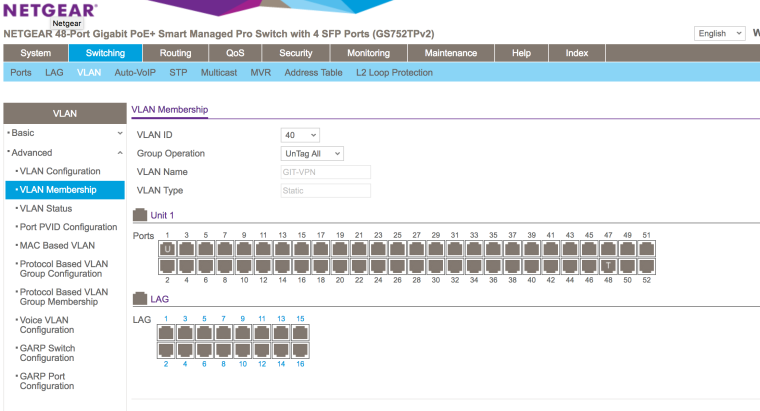
Also, I read somewhere that routing needed to be enabled (is this correct)?:
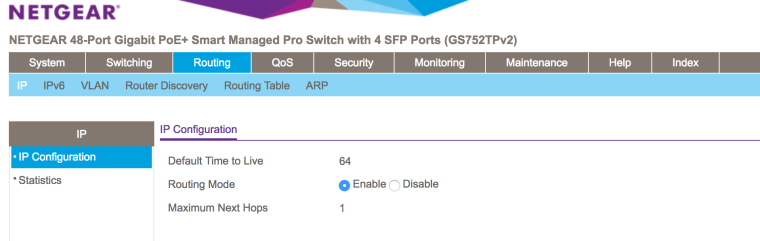
I'm still unable to obtain a DHCP address with these settings - nothing has changed.
-
Now you're using the switch as Layer 3? Why did you enable routing there? You probably just want to slow down that clicky finger.
That looks like it should be working, but I am unclear why you are tagging VLAN 1 to port 1.
Here is what I would do if I were you:
Be sure you have a DHCP server configured and enabled on both LAN and OPT1 on pfSense. Be sure the pool ranges, etc are appropriate for the interfaces.
Reset the switch to factory defaults.
Make port 1 untagged VLAN 40, PVID VLAN 40
Make port 2 untagged VLAN 1, PVID VLAN 1 (This should be the default)
Make port 48 untagged VLAN 1, Tagged VLAN 40, PVID VLAN 1
Connect pfSense em1 to port 48
Connect a workstation configured for DHCP to port 1. It should get an address on OPT1
Disconnect workstation and connect to port 2. It should get an address on LAN.
Have a beer. You deserve it.
-
THANK YOU, THANK YOU, THANK YOU, AND ----> THANK YOU!!!
YOU SAVED MY LIFE AND MY TIME
YOU ARE A GRANDMASTER JEDILORD DERELICT - THE LEGEND!!!
People will search and find my post, they will come and see this final posting and will see how thankful and grateful I am to you!!!
Thanks so much!!! :)
-
So that worked?