DDoS attacks OpenVPN on Pfsense
-
I get DDoS attacks OpenVPN server on Pfsense. How can I stop it?
I have Snort installed but it doesn't look it will block DDoS on OpenVPN connection
Now, I created an Aliases to allow IPs to access OpenVPN for temp block the DDoS.I don't like this idea because it limits people to use OpenVPN on different devices and a lot of administration.
Any suggestion?
-
Denial of service attacks can only be blocked/mitigated upstream, so talk to your ISP.
-
Talk to my ISP and they said don't use OpenVPN and it will solve the problem. FUNNY!!
-
When you say DDoS attacks, do you mean sustained, targeted, high-volume connection attempts that are causing tangible problems? Because it's normal to get unsolicited connection attempts any time you run a server on the open Internet, certainly on the order of hundreds or possibly thousands per day. As long as you have your OpenVPN server configured correctly, that's nothing to worry about really. But if these are true DDoS attacks targeting you specifically, of course that's another matter.
-
Yes, high-volume connection attempts that are causing tangible problems. We limited 10 OpenVPN connections for OpenVPN and all connections are used by "UNDEF" and I disconnected them and then reconnect again. After all 10 connections are been used. Our users cannot sign in at all. I can see the IP but I have no idea how to block it.
I have two sites get the same problem.
-
Are your users working from known addresses? If so, perhaps you could set up rules that would allow them, but not from other addresses. Is there any pattern to where the attacks are coming from? That might also give you something to filter on. Is IPv6 available for the users and server? If so, that might be another way to filter, assuming the attacks are coming in on IPv4. It's much harder to find a target on IPv6, due to the huge number of addresses available.
-
@leungda said in DDoS attacks OpenVPN on Pfsense:
I can see the IP but I have no idea how to block it.
So its just 1 IP? 10, 100, 10,000 different IPs? If you don't want specific IPs to be able to attempt a connection to your openvpn server port. This can be blocked by a simple rule above the wan rule that allows access to your openvpn port.
You can use whole network blocks if coming from large number of IPs in a whole block.. You could use pfblocker to easy assign blocks to whole ranges of IPs used from a specific country, etc.
Can you post some example of IPs that you would like to block.. Them filling up your number of openvpn connections you allow for is a quite different than a volumetric attack filling up your pipe..
You sure its not just a configured client of yours trying to connect and failing, so it just continues to try and try and try?
-
It is an IPv4 address and yes, it is what I am doing is limited all known IPs to access OpenVPN.
I will try to unblock the IP. After I see the IP address, I will post a screenshot.
-
Are you using a static tls key?
Quoting from pfsense configuration screenA TLS key enhances security of an OpenVPN connection by requiring both parties >to have a common key before a peer can perform a TLS handshake. This layer of HMAC authentication allows control channel packets without the proper key to be dropped, protecting the peers from attack or unauthorized connections.The TLS Key does not have any effect on tunnel data.
Puts much less strain on the box and you don't have to administer ip's anymore
Just an idea. -
I don't understand. I've been running OpenVPN for years now, and I've never had any ghost connections tying everything up. I'm being scanned and probed just as much as everyone else. Nothing ever connects to it except for valid users. Does this happen to anyone else? In all my years here, I've never heard of a similar complaint. Is this actually a real problem?
-
I have never see bogus hits on openvpn tie up a connection no..
-
I can say you are lucky
-
@netblues said in DDoS attacks OpenVPN on Pfsense:
Are you using a static tls key?
Are you using a static TLS key? How is your server configured?
-
@kom said in DDoS attacks OpenVPN on Pfsense:
Does this happen to anyone else?
#Metoo.
Having a static IPv4 your years now, but never saw something like that.
TLS Keys : of course, I use these. -
two different sites got attacked. They are different client and network. They got attacked with the same IP address.
How can i extract OpenVPN log from pfsense
-
Whats the IP address, it's not comming from shodan or shadowserver is it ?
I get these almost every day poking my IPsec VPN, create a blacklist in snort if it is.
shadowserver:- 216.218.206.0/24 shodan:- 198.20.69.72/29 # census1.shodan.io 198.20.69.96/29 # census2.shodan.io 198.20.70.112/29 # census3.shodan.io 198.20.99.128/29 # census4.shodan.io 93.120.27.62 # census5.shodan.io 66.240.236.119 # census6.shodan.io 71.6.135.131 # census7.shodan.io 66.240.192.138 # census8.shodan.io 71.6.167.142 # census9.shodan.io 82.221.105.6 # census10.shodan.io 82.221.105.7 # census11.shodan.io 71.6.165.200 # census12.shodan.io 188.138.9.50 # atlantic.census.shodan.io 85.25.103.50 # pacific.census.shodan.io 85.25.43.94 # rim.census.shodan.io 71.6.146.185 # pirate.census.shodan.io 71.6.146.186 # inspire.census.shodan.io 71.6.158.166 # ninja.census.shodan.io 198.20.87.96/29 # border.census.shodan.io 66.240.219.146 # burger.census.shodan.io 209.126.110.38 # atlantic.dns.shodan.io 104.236.198.48 # blog.shodan.io 104.131.0.69 # hello.data.shodan.io 162.159.244.38 # www.shodan.io 159.203.176.62 # ny.private.shodan.io 188.138.1.119 # atlantic249.serverprofi24.com 80.82.77.33 # sky.census.shodan.io 80.82.77.139 # dojo.census.shodan.io 71.6.146.130 # ubtuntu16146130.aspadmin.com 66.240.205.34 # shodan.io 216.117.2.180 # malware-hunter.census.shodan.io 93.174.95.106 # battery.census.shodan.io 89.248.172.16 # house.census.shodan.io 185.163.109.66 # goldfish.census.shodan.io 93.174.95.106 # battery.census.shodan.io 89.248.167.131 # mason.census.shodan.io 94.102.49.190 # flower.census.shodan.io 94.102.49.193 # cloud.census.shodan.io 185.181.102.18 # turtle.census.shodan.io -
Could you tell me how to create a blacklist in snort?
-
Create the blacklist file:-
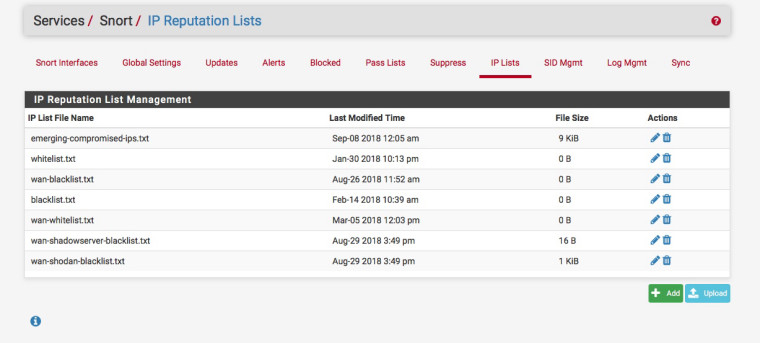
Apply it to the interface:-
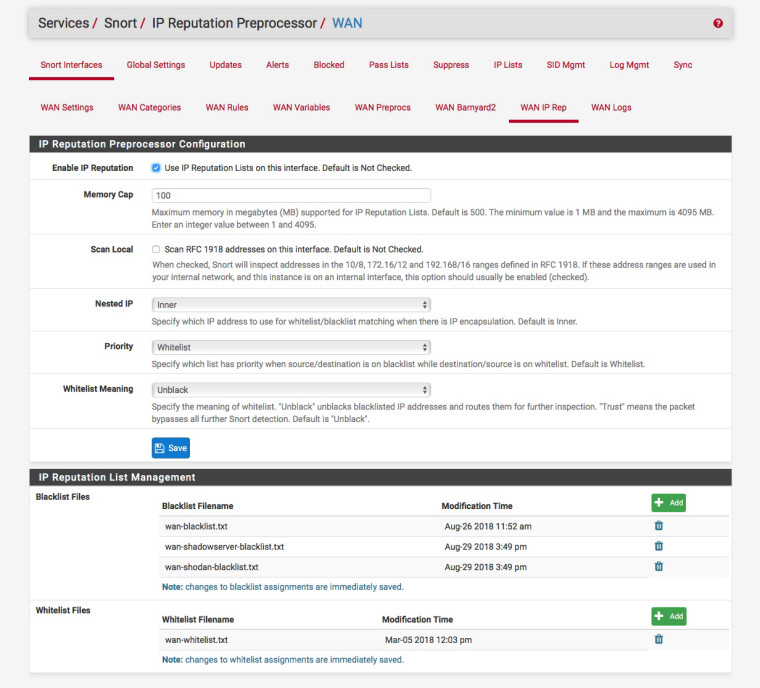
You then should see (spp_reputation) packets blacklisted in the blocked list:-
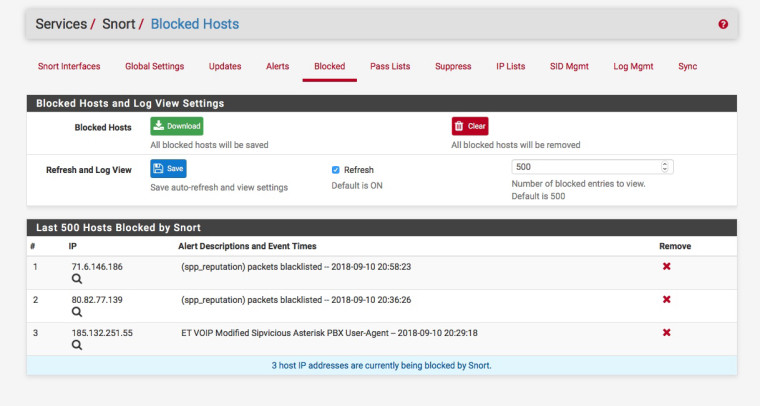
-
Love it. Thanks for your help
-
@netblues said in DDoS attacks OpenVPN on Pfsense:
Are you using a static tls key?
You have been asked this twice now. It's hard to help you when you don't answer questions.