ACME Setup Steps
-
@rmonette said in ACME Setup Steps:
Application Key
Application Secret
Consumer KeyThis comes from here : https://www.ovh.com ....
To be more precise : goto the bottom of that page, look for :
You end up here : https://api.ovh.com/
Read First steps with the OVH APISee also this https://github.com/Neilpang/acme.sh/wiki/How-to-use-OVH-domain-api and other links that Google produce wwhen you ask about pfSense, acme, OVH, API.
Btw : All my domain names come from OVH, but I'm not using their DNS services. I use my own SYS server from OVH, a Debian server with bind. From there it's a RFC 2136 story. No need for API's - just me controlling everything from top to bottom.
-
@gertjan : thank you for the suggestions. Ive been able to generate these keys and add them to the Pfsense. Its currently displaying in the cert manager, but in the Issuer column, it says "Private key only". Anything else I should do at this point? When setting this up, I also used the staging testing option (v2). Also, at this point, do I also have to create TXT records? if so, what should be the authz value?
-
@rmonette
The reason for putting these API keys and secrets, is so that acme package itself can create a TXT record. You would not need to do this manually..That the certificate private key is created, but does not yet have a public key part means that something failed during the issuance of the certificate.. Check the logfile from /tmp/acme or press the issue button, and read the log that it displays on screen. It should tell that its adding a TXT record to your dns, then the result of the acme servers trying to validate its existence.. It might be adding the record failed.?. or it took ovh to long to make the setting effective on their actual dns servers? (there is a delay setting that can mitigate such issue) does the log it mention any error?
-
@piba
Ok... this is what Ive done so far:- Navigate to: https://eu.api.ovh.com/createApp/
1.1 Get AK, AS - Log into FW, create account key
- Get the consumer key by requesting an authentication token from OVH: launch curl request:
curl -XPOST -H"X-Ovh-Application: APPLICATION_KEY -H "Content-type: application/json" https://eu.api.ovh.com/1.0/auth/credential -d '{"accessRules":[{"method": "GET","path": "/*"}],"redirection":"https://www.YYYY.com/"}' - Get the return value from curl, and then, validate the returned url:
{"validationUrl":"https://eu.api.ovh.com/auth/?credentialToken=ZZZZZZ","consumerKey":"AAAAAA","state":"pendingValidation"} - Once validated, enter values in ACME, and create cert request.
That last step seems to be working correctly, as when I validate (click on) the url sent in the curl response, leads me to the OVH page, and asks me to log in, and then redirects me to the site.
The API stuff seems to generate things as needed, but in the end, I get an "invalid domain" error message when requesting the cert via ACME. A few follow up details:
Im trying to create a wildcard cert. the entry in put in the ACME form, was i the format of *.YYYY.COMThis is the end output of the attempt:
[Mon Sep 24 16:51:52 EDT 2018] Registering account
[Mon Sep 24 16:51:53 EDT 2018] Already registered
[Mon Sep 24 16:51:53 EDT 2018] ACCOUNT_THUMBPRINT='XXXXXX'
[Mon Sep 24 16:51:53 EDT 2018] Single domain='.YYYY.com'
[Mon Sep 24 16:51:53 EDT 2018] Getting domain auth token for each domain
[Mon Sep 24 16:51:55 EDT 2018] Getting webroot for domain='.YYYY.com'
[Mon Sep 24 16:51:55 EDT 2018] Found domain api file: /usr/local/pkg/acme/dnsapi/dns_ovh.sh
[Mon Sep 24 16:51:55 EDT 2018] Using OVH endpoint: ovh-eu
[Mon Sep 24 16:51:55 EDT 2018] Checking authentication
[Mon Sep 24 16:51:56 EDT 2018] Consumer key is ok.
[Mon Sep 24 16:51:59 EDT 2018] invalid domain
[Mon Sep 24 16:51:59 EDT 2018] Error add txt for domain:_acme-challenge.YYYY.com
[Mon Sep 24 16:51:59 EDT 2018] Please check log file for more details: /tmp/acme/YYYY-Testing/acme_issuecert.log.Finally, do I, or dont I need a firewall rule to open up the access? The guide seemed to indicate that I needed to open port 80...
- Navigate to: https://eu.api.ovh.com/createApp/
-
@rmonette said in ACME Setup Steps:
Error add txt for domain:_acme-challenge.YYYY.com
When your using DNS-validation you do not need to open port 80 which would be http-validation. It however seems the script is failing to add the required txt record.. Can you try with a regular domain name perhaps? (not a wildcard)
Maybe you could try if a newer ovh api script works better.?. im not sure if something perhaps was changed/fixed in there? https://github.com/Neilpang/acme.sh/commits/master/dnsapi/dns_ovh.sh
It is 'likely' safe to copy just that single file above into the pfSense /usr/local/pkg/acme/dnsapi/ folder..It looks like the script doesn't know how to get the root for your domain. I don't use ovh though so kinda hard to debug where it fails on exactly..
-
Just wanted to follow up with this: Im not sure that the API from OVH is ready for prime time. Instead, I went with DNS-Manual, and everything worked.
I was able to generate a wild card cert, and when doing the initial issuance, I was able to get the [authz] key needed for the TXT record, which I then added to the DNS zone, and then waited a bit, and pressed "renew" in the cert tab. Once I did that, everything got added to the firewall's cert manager, and I was able to use it in HAProxy.
Im pretty sure I know the answer, but given that Im in manual mode, will I need to modify my TXT record every time I need to re-ssue the cert? The cron jobs will launch the process, but, I assume that it will also wipe my TXT authz value every time, and that I will need to modify that entry by hand everytime it is renewed.
Apart from having to renew/use the DNS-Manual approach, this is pretty sweet!
Thank to all for your comments/suggestions!
-
That last part is exact.
The "authz" code from LetEnscrypt will change every time.
So, when renewing manually, the cron "automated" renew won't work for you.Not that I ever worked with the OVH API to renew my certs, I do own OVH (SYS) servers, and a boatload of domain names at OVH.
The very same API is also used by their own Client Manager ( this one : https://www.ovh.com/auth/?action=gotomanager&from=https://www.ovh.com/fr/&ovhSubsidiary=fr ) and should work.
All certs for their clients that use their (OVH) hosted web services have cert now, and they use the same procedure, the same API.What I want to say : persist, look up the doc, you will make it work.
Use this https://api.ovh.com/console/ to add a TXT record to one of your domains using the API, but you are direct command. You will find out what to communicate so that it will work.
See https://api.ovh.com/console/#/domain/zone/%7BzoneName%7D/record#POSTBtw : I'm renewing myself using the RFC 2136 using nsupdate, I'm managing my own domains on a bind DNS server on a dedicated server. Took me some time to set the whole thing up correctly (both side !).
-
Update.
I've been toying with OVH, and for some good new :
I instructed acme/pfSense to obtain a certicate for "papy-team.fr", a domain that I rent @OVH.
Result :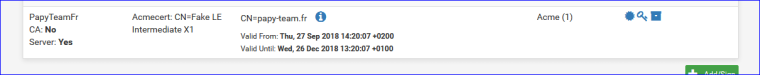
Ok, it a fake one, but the OVH-API works.
If you do it right, this will take you 120 seconds, take my word on it.
Go here : https://github.com/Neilpang/acme.sh/wiki/How-to-use-OVH-domain-api which is nothing more or less then the manual of the acme plugin from the writer : Neil.
Go to the bottom of the page.
Use one of these two :OVH Europe: https://api.ovh.com/createToken/?GET=/domain/zone/mydomain.com/*&POST=/domain/zone/mydomain.com/*&PUT=/domain/zone/mydomain.com/*&GET=/domain/zone/mydomain.com&DELETE=/domain/zone/mydomain.com/record/* OVH Canada: https://ca.api.ovh.com/createToken/?GET=/domain/zone/mydomain.com/*&POST=/domain/zone/mydomain.com/*&PUT=/domain/zone/mydomain.com/*&GET=/domain/zone/mydomain.com&DELETE=/domain/zone/mydomain.com/record/*De difficult part ; replace mydomain.com with "yourdomain.tld" - (5 times).
Use the URL .... just enter your NIC or login code, the password, the duration, a description or two and don't even touch the rights, they are set according the URL already.
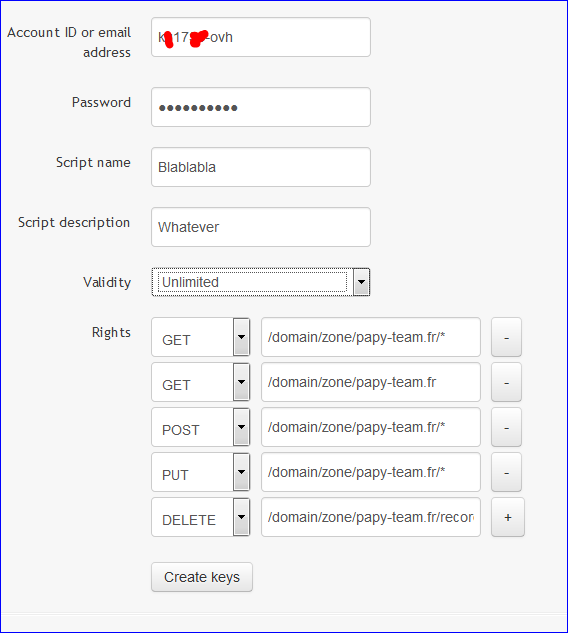
.. and hit Create Keys.
You wind up with a :
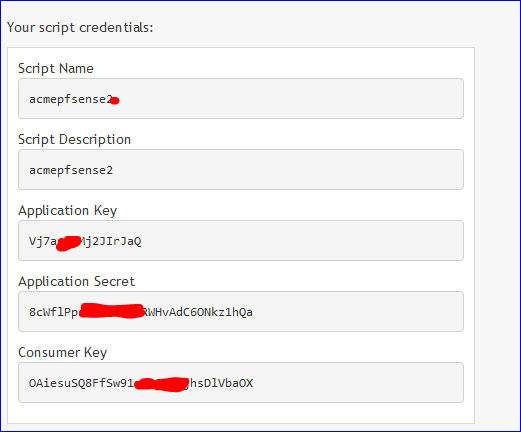
Copy the Application key and secret, and the Consumer Key into the acme settings, the Domain SAN list table.
Done.
As usual, to me 2 hours to understand that it can be done in 60 seconds

-
@gertjan said in ACME Setup Steps:
https://api.ovh.com/createToken/?GET=/domain/zone/mydomain.com/&POST=/domain/zone/mydomain.com/&PUT=/domain/zone/mydomain.com/&GET=/domain/zone/mydomain.com&DELETE=/domain/zone/mydomain.com/record/
Yes! That worked for me as well. The cert is in the Cert Mgr. Quick question: is the TXT record supposed to stay in the DNS Zone? or, is it just needed to temporarily validate the request, when called by the script?
-
Well ... login yourself into the "Manager" (old name of the OVH client access), the one that adminstrates your domain name, and check your DNS zone, look up all the TXT records, it should be gone, because :
No more need for it. The next cert regeneration will produce another code anyway.
The acme OVH-APIplugin, as any other plugin, will wipe what it has added for the test. -
Yep... That was the case (the entry was gone), I wasnt sure if it was a bug or deliberate: I wasnt sure if it was needed post validation. Thank you for clarifying.
-
Wildcards using the API OVH or more in general ?
I'm obtaining a wild card just fine using the pfSenese's acme package just fine.

-
Im all set. I was able to create wild card certs (since Sept 27)