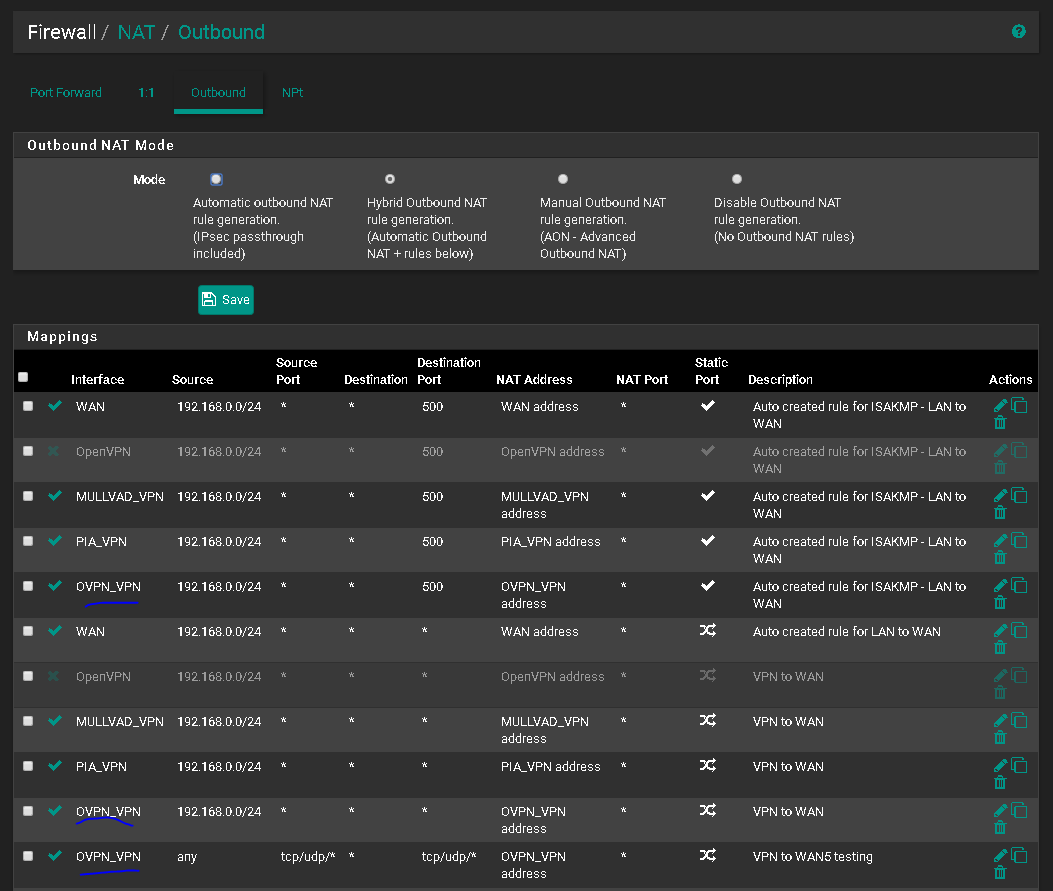
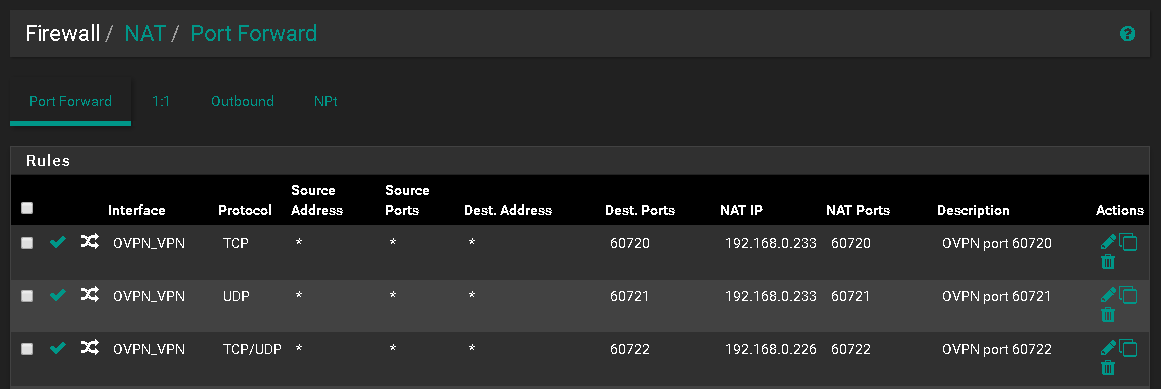
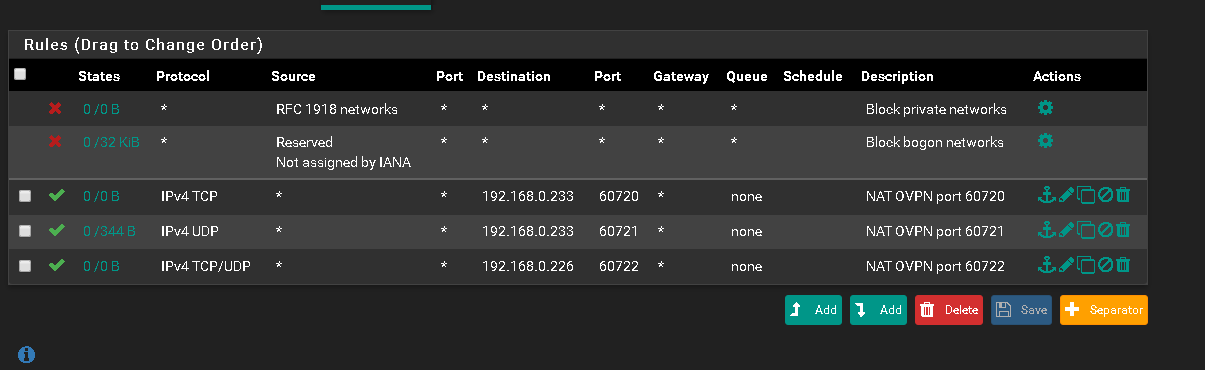
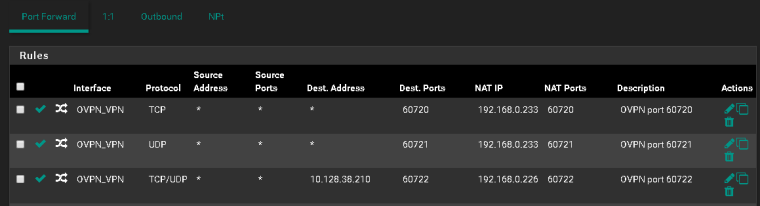
Port Forwarding
-
Yes, there is little traffic from VPN provider that will go to my dc ++ and utorrent.
I have looked at that clip, but does he open ports because I could not see it?
Tell me where you want to see and I send pictures?
-
From my memory he is not showing exactly how Port Forwarding from any VPN Provider works, but giving an idea how this stuff generally works (assign/configure VPN Interface, Firewall Rules, and so on).
-Rico
-
I have followed this https://www.reddit.com/r/PFSENSE/comments/6edsav/how_to_proper_partial_network_vpn_with_kill_switch/.
-
@sweden_cool said in Port Forwarding:
Yes, there is little traffic from VPN provider that will go to my dc ++ and utorrent.
If your VPN provider forwards the ports to you it should work with a port forwarding rule on the interface you've assigned to the vpn appropriate client instance.
But I'm in doubt, you get these ports really forwarded. Just use packet capture from the pfSense Diagnostic menu on the OpenVPN interface group to check that out.
-
Got this when I tested this with port 60722.
https://www.yougetsignal.com/tools/open-ports/
16:43:50.836144 IP hidden.38.210.36996 > hidden.106.182.60722: tcp 0 16:43:50.836197 IP hidden.38.210.8440 > hidden.106.166.60722: tcp 0 16:43:55.057344 IP hidden.98.246.60232 > hidden.38.210.60722: tcp 0 16:43:56.055547 IP hidden.98.246.60232 > hidden.38.210.60722: tcp 0 16:43:56.062655 IP hidden.98.246.60236 > hidden.38.210.60722: tcp 0 16:43:57.058936 IP hidden.98.246.60243 > hidden.38.210.60722: tcp 0 16:43:57.059579 IP hidden.98.246.60236 > hidden.38.210.60722: tcp 0 16:43:58.058874 IP hidden.98.246.60243 > hidden.38.210.60722: tcp 0 -
On the OpenVPN interface, not on WAN?
Which devices to that IPs belong to? Hidden....Have your already assigned an interface to the vpn client instance and activated it?
-
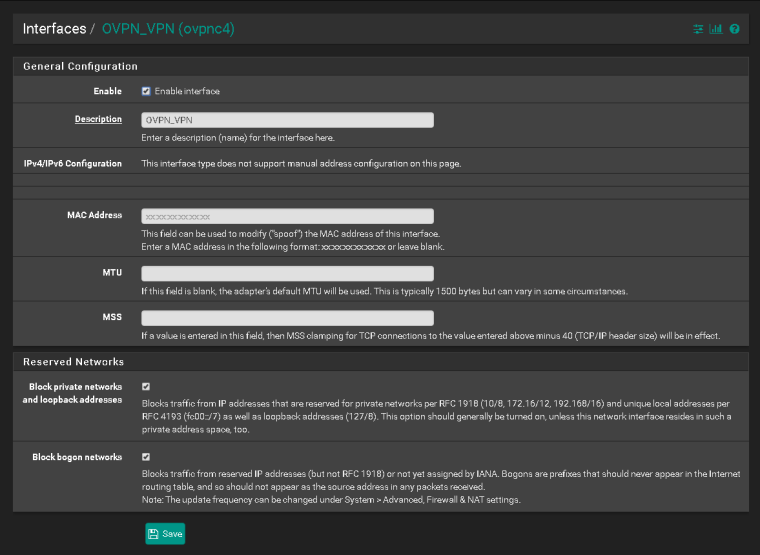
Interface: OVPN_VPN
18:52:16.939183 IP 185.157.161.152.53234 > 10.128.38.210.60722: tcp 0 18:52:17.965667 IP 85.224.149.157.29710 > 10.128.38.210.60722: tcp 0 18:52:18.658740 IP 91.240.66.48.53899 > 10.128.38.210.60722: tcp 0 18:52:18.964428 IP 85.224.149.157.29710 > 10.128.38.210.60722: tcp 0 18:52:19.523353 IP 81.25.149.133.62243 > 10.128.38.210.60722: tcp 0 18:52:19.701724 IP 83.254.161.10.50540 > 10.128.38.210.60722: tcp 0 18:52:19.946048 IP 185.157.161.152.53234 > 10.128.38.210.60722: tcp 0 18:52:20.554269 IP 90.230.23.44.4481 > 10.128.38.210.60722: tcp 0 18:52:20.918101 IP 185.86.107.205.38543 > 10.128.38.210.60722: tcp 0 18:52:20.967947 IP 85.224.149.157.29710 > 10.128.38.210.60722: tcp 0 18:52:21.214450 IP 185.86.106.150.57721 > 10.128.38.210.60722: tcp 0 18:52:21.581429 IP 90.230.23.44.4481 > 10.128.38.210.60722: tcp 0 18:52:21.654341 IP 91.240.66.48.53899 > 10.128.38.210.60722: tcp 0 18:52:21.925520 IP 185.86.107.205.38543 > 10.128.38.210.60722: tcp 0 18:52:22.567468 IP 81.25.149.133.62300 > 10.128.38.210.60722: tcp 0 18:52:23.597319 IP 90.230.23.44.4481 > 10.128.38.210.60722: tcp 0 18:52:23.848450 IP 198.199.98.246.37355 > 10.128.38.210.60722: tcp 0 18:52:23.941114 IP 185.86.107.205.38543 > 10.128.38.210.60722: tcp 0 18:52:24.341094 IP 85.24.253.39.58219 > 10.128.38.210.60722: tcp 0 18:52:24.839786 IP 198.199.98.246.37357 > 10.128.38.210.60722: tcp 0 18:52:24.846481 IP 198.199.98.246.37355 > 10.128.38.210.60722: tcp 0 18:52:24.972598 IP 85.224.149.157.29710 > 10.128.38.210.60722: tcp 0 18:52:25.836596 IP 198.199.98.246.37357 > 10.128.38.210.60722: tcp 0 18:52:25.841382 IP 198.199.98.246.37360 > 10.128.38.210.60722: tcp 0 18:52:25.946941 IP 185.157.161.152.53234 > 10.128.38.210.60722: tcp 0 18:52:26.841404 IP 198.199.98.246.37360 > 10.128.38.210.60722: tcp 0 18:52:27.351544 IP 85.24.253.39.58219 > 10.128.38.210.60722: tcp 0 18:52:27.660667 IP 91.240.66.48.53899 > 10.128.38.210.60722: tcp 0 18:52:27.693316 IP 90.230.23.44.4481 > 10.128.38.210.60722: tcp 0 18:52:28.102717 IP 185.86.107.205.38543 > 10.128.38.210.60722: tcp 0 18:52:28.299994 IP 193.138.218.165.49558 > 10.128.38.210.60722: tcp 0 18:52:28.721840 IP 78.67.17.227.41246 > 10.128.38.210.60722: tcp 0 18:52:29.329428 IP 193.138.218.165.49558 > 10.128.38.210.60722: tcp 0 18:52:29.642628 IP 78.67.17.227.41246 > 10.128.38.210.60722: tcp 0 18:52:31.345281 IP 193.138.218.165.49558 > 10.128.38.210.60722: tcp 0
-
10.128.38.210 is your virtual vpn address, I guess?
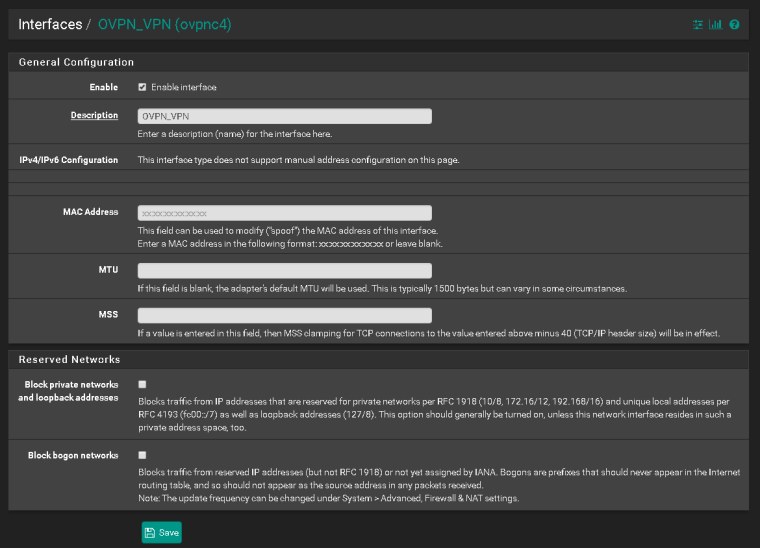
So you should use this one as destination in the port forwarding rule.However, the problem which the screenshot shows is the check at "Block private networks..." in the vpn interface settings. Since your clients IP (here obv. 10.128.38.210) is a private one, you must remove that check, otherwise all incoming connections get blocked.
-
-
Yeah, exactly.
Does it work now?
-
-
Set the destination of the NAT translation to OVPN_VPN address.
Be sure the rules passing the traffic do not match on the OpenVPN Group tab, but do match on the OVPN_VPN tab. The easiest way to be sure is to not have any rules on the OpenVPN tab. Care will have to be taken if you have other OpenVPN servers or clients defined.
Be sure the default gateway of the 192.168.0.233 host is pfSense.
Be sure the firewall on 192.168.0.233, if any, passes traffic from arbitrary sources.
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.html
If you take more packet captures, please do them on the 192.168.0.0/24 interface the server is on. If you don't see any traffic there, check all of the above again.