Unable to see local subnet when connected on the VPN.
-
Hi,
I used the OpenVPN wizard on pfSense to create a connection. The goal is a roadwarrior VPN so I can connect from work and access my home lab.
The wizard went great, I created a tunnel network on 192.168.2.0/24
Local network is 192.168.1.x
Now when I connect I get assigned a 192.168.2.2 ip address just fine.
Originally I could not get to websites because the DNS didn't resolve. So I updated it to force DNS resolvers.Now I am connected to the network and I can view websites just fine. But I want to SSH into my machines on the 192.168.1.x network, or view local web-clients on that same network.
What must I change?
-
Well do your clients on 192.168.1 have firewalls running - if so then you need to configure them to allow your 192.168.2 network or no your not going to be able to get to them.
You can also have issues if where your vpn from local network is 192.168.1 or overlaps that network.. 192.168.1 is very very common network so yeah you could run into that many locations for sure.. Why its best to setup your local network to be some less common network.. My lan is 192.168.9/24 for example.
-
Thank you for the feedback.
The local machines are not running firewalls. even if they were I would expect to be able to reach the internal web-clients.
Also don't have a 192.168.1 or 2 network here in the office.
If I did want to change my local network is it a clean change for everything currently using DCHP to pickup a new address?
-
yeah very clean if your all dhcp..
Not sure what you mean by even if running firewalls you would expect to reach them? Can tell you for sure that for example windows machines firewall would block all access to services running from a different network segment unless you had set the rules different.. 192.168.2 is not 192.168.1 so to the firewall its NON local even if its rfc1918 space.
Can you hit the pfsense gui on 192.168.1.x? Can you ping anything on 192.168.1.x? When you do a traceroute from your vpn client you see it send traffic down the tunnel? When you want to go to 192.168.1.x?
example
C:>tracert -d 192.168.9.100Tracing route to 192.168.9.100 over a maximum of 30 hops
1 100 ms 99 ms 110 ms 10.0.8.1
2 105 ms 112 ms 104 ms 192.168.9.100Trace complete.
C:>
That is me trace to a box on my home lan, vpn'd in from work... The high times 100ms is because I have to bounce off a proxy to get to my home network from work - and the proxy is in TX vs Chicago... So traffic goes from Chicago area to Houston, and back ;)
-
@johnpoz I should be able to reach the webclients even if the local servers have a firewall enabled.
For example I should be able to see the local grafana instance while on the VPN.When connected to the VPN from the office:
I can not hit the pfSense GUI.
This site can’t be reached
https://192.168.1.1/ is unreachable.
ERR_ADDRESS_UNREACHABLEI can not ping the pfSense IP
PING 192.168.1.1 (192.168.1.1): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
Request timeout for icmp_seq 3
ping: sendto: No route to host
Request timeout for icmp_seq 4
ping: sendto: Host is down
Request timeout for icmp_seq 5
ping: sendto: Host is down
Request timeout for icmp_seq 6
ping: sendto: Host is down
Request timeout for icmp_seq 7
ping: sendto: Host is down
Request timeout for icmp_seq 8
ping: sendto: Host is down
Request timeout for icmp_seq 9
ping: sendto: Host is down
Request timeout for icmp_seq 10Traceroute fails
Traceroute has started…
traceroute to 192.168.1.1 (192.168.1.1), 64 hops max, 72 byte packets
1 * * *
2 *traceroute: sendto: Host is down
traceroute: wrote 192.168.1.1 72 chars, ret=-1
*traceroute: sendto: Host is down
traceroute: wrote 192.168.1.1 72 chars, ret=-1
*
traceroute: sendto: Host is down
3 traceroute: wrote 192.168.1.1 72 chars, ret=-1
*traceroute: sendto: Host is down
traceroute: wrote 192.168.1.1 72 chars, ret=-14 * * *
5 *traceroute: sendto: No route to host
traceroute: wrote 192.168.1.1 72 chars, ret=-1
*traceroute: sendto: Host is down
traceroute: wrote 192.168.1.1 72 chars, ret=-1
*
traceroute: sendto: Host is down
6 traceroute: wrote 192.168.1.1 72 chars, ret=-1
*traceroute: sendto: Host is down
traceroute: wrote 192.168.1.1 72 chars, ret=-1My linux hosts are more important to me than the windows stuff, so checking my linux hosts iptables have very modest rules all set to allow.
Perhaps there should be some simple questions answered first:
-If I used the pfSense wizard to configure a remote access VPN should I have access to the local subnet?
-Do I need to check a box, or enter an address to do it?
-Should my connection have used the local DNS server or should I have had to force a DNS resolver? This seems like an extra step I didn't see most tutorials take.Basically am I broken or did I configure incorrectly?
-
-
@esteidinger said in Unable to see local subnet when connected on the VPN.:
ping: sendto: No route to host
You sure your even connected to your vpn? what does it show for the route to 192.168.1?
Do a simple netstat -nr when your connected to vpn
Yes if when you ran through the wizard you answered the questions correctly - I you put in your local network.
-
I sure think so. I get an IP address of 192.168.2.2
Looking in OpenVPN inside PFSense
Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_VER=2.4.4 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_PLAT=mac Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_PROTO=2 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_NCP=2 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_LZ4=1 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_LZ4v2=1 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_LZO=1 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_COMP_STUB=1 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_COMP_STUBv2=1 Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 peer info: IV_TCPNL=1 Oct 12 14:06:36 openvpn user 'esteid' authenticated Oct 12 14:06:36 openvpn 44498 144.121.5.10:1194 [esteid] Peer Connection Initiated with [AF_INET]144.121.5.10:1194 Oct 12 14:06:36 openvpn 44498 esteid/144.121.5.10:1194 MULTI_sva: pool returned IPv4=192.168.2.2, IPv6=(Not enabled)I can do the same with ios.
I did put in the local IP range when I used the wizard.
-
Where is your route lets see your netstat -nr from your client.
Your connection log should also show you the route(s).
Fri Oct 12 14:51:54 2018 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.0.8.2/255.255.255.0 on interface {1F3723EC-C42B-4EC6-A2C0-5EAABB0BF77E} [DHCP-serv: 10.0.8.254, lease-time: 31536000] Fri Oct 12 14:51:54 2018 Successful ARP Flush on interface [14] {1F3723EC-C42B-4EC6-A2C0-5EAABB0BF77E} Fri Oct 12 14:51:54 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Fri Oct 12 14:51:54 2018 MANAGEMENT: >STATE:1539373914,ASSIGN_IP,,10.0.8.2,,,, Fri Oct 12 14:51:59 2018 TEST ROUTES: 3/3 succeeded len=3 ret=1 a=0 u/d=up Fri Oct 12 14:51:59 2018 MANAGEMENT: >STATE:1539373919,ADD_ROUTES,,,,,, Fri Oct 12 14:51:59 2018 C:\Windows\system32\route.exe ADD 192.168.9.0 MASK 255.255.255.0 10.0.8.1 Fri Oct 12 14:51:59 2018 Route addition via service succeeded Fri Oct 12 14:51:59 2018 C:\Windows\system32\route.exe ADD 192.168.2.0 MASK 255.255.255.0 10.0.8.1 Fri Oct 12 14:51:59 2018 Route addition via service succeeded Fri Oct 12 14:51:59 2018 C:\Windows\system32\route.exe ADD 192.168.3.0 MASK 255.255.255.0 10.0.8.1 Fri Oct 12 14:51:59 2018 Route addition via service succeeded Fri Oct 12 14:51:59 2018 Initialization Sequence CompletedHere is log from my iphone connecting
2018-53-12 14:53:30 NIP: adding IPv4 address to network settings 10.0.200.2/255.255.255.0 2018-53-12 14:53:30 NIP: adding (included) IPv4 route 10.0.200.0/24 2018-53-12 14:53:30 NIP: adding (included) IPv4 route 192.168.9.0/24 2018-53-12 14:53:30 NIP: adding (included) IPv4 route 192.168.2.0/24 2018-53-12 14:53:30 NIP: adding (included) IPv4 route 192.168.3.0/24 2018-53-12 14:53:30 NIP: adding DNS 192.168.9.253 2018-53-12 14:53:30 NIP: blocking all IPv6 traffic 2018-53-12 14:53:30 NIP: adding match domain ALL 2018-53-12 14:53:30 NIP: adding DNS specific routes: 2018-53-12 14:53:30 NIP: adding (included) IPv4 route 192.168.9.253/32 2018-53-12 14:53:30 Connected via NetworkExtensionTUN -
I am uncomfortable doing a netstat on the work computer. I'll grab a machine at home and do it there.
Appreciate your effort. I'll try not to leave you waiting too long.
-
huh?? its a listing of the routes... You don't have to show ALL of them just validate that it shows your route to 192.168.1.1 pointing to your tun.
You should see them added in your connection log as well as I posted above.
-
There are no 192.168.1.1 entries.
Internet:
Destination Gateway Flags Refs Use Netif Expire
0/1 192.168.2.1 UGSc 64 0 utun5
default 172.20.10.1 UGSc 0 0 en0
71.192.73.47/32 172.20.10.1 UGSc 1 0 en0
127 127.0.0.1 UCS 0 0 lo0
127.0.0.1 127.0.0.1 UH 3 67130 lo0
128.0/1 192.168.2.1 UGSc 3 0 utun5
169.254 link#5 UCS 0 0 en0
172.20.10/28 link#5 UCS 1 0 en0
172.20.10.1/32 link#5 UCS 1 0 en0
172.20.10.1 3a:53:9c 72:64 UHLWIir 4 46 en0 1151
72:64 UHLWIir 4 46 en0 1151
172.20.10.2/32 link#5 UCS 0 0 en0
172.20.10.15 ff:ff:ff:ff:ff:ff UHLWbI 0 6 en0
192.168.2 192.168.2.2 UGSc 16 0 utun5
192.168.2.2 192.168.2.2 UH 2 52 utun5 -
then you didn't answer the wizards questions correctly?
what do you have in your local network?
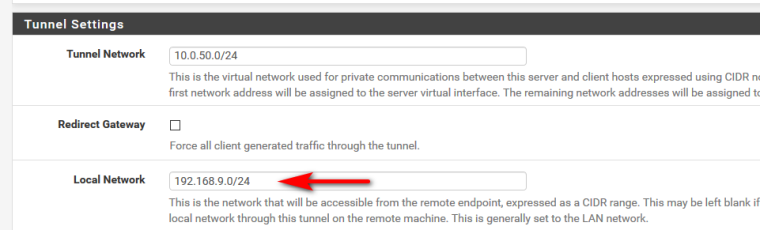
If it doesn't hand you a route - then NO your not going to go down the tunnel to get there...
Looks like you should be going down the tunnel as default
0/1 192.168.2.1 UGSc 64 0 utun5
128.0/1 192.168.2.1 UGSc 3 0 utun5But then you should see your first hop being your the tunnel address..
Did you not let it create the vpn rules? What does yours look like?
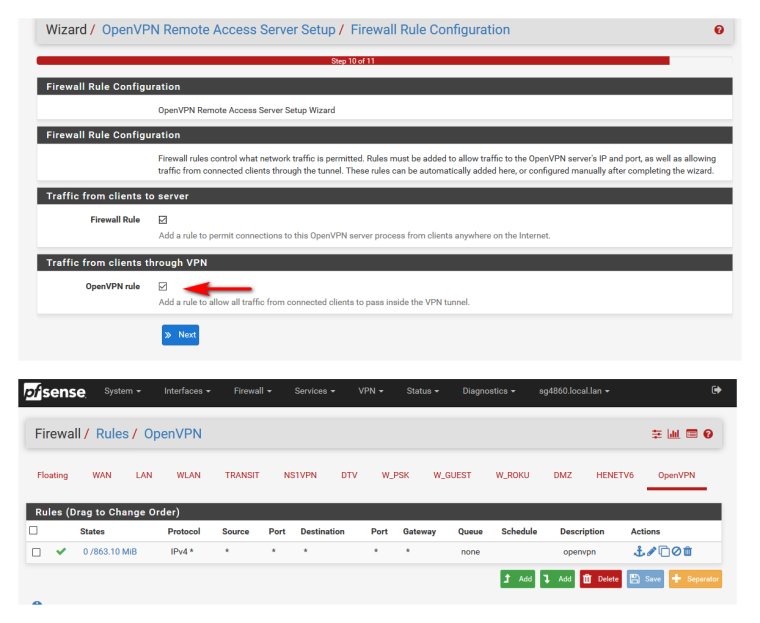
-
Have you tried adding push route statements for the networks you want to reach? By default, OpenVPN only pushes a route for the local network defined in the main config. You will also need pass rules on the lan to accept traffic from the alien network you are coming from.
In the Advanced config section of the VPN a push route statement for a /28 network and a /24 network will look like:
push "route 172.20.10.0 255.255.255.242"; push "route 192.168.0.0 255.255.255.0";
My preferred solution is to use TUN mode only for peer to peer links, and to use TAP mode for road warrior computer configurations. TAP mode lets you extrude the local network directly to the client rather than using a transit network. In my experience it requires writing fewer rules to get traffic flowing. The main drawback is a lack of support for TAP mode on iOS and Android clients.
-
@bfeitell said in Unable to see local subnet when connected on the VPN.:
The main drawback
Why would you want to send broadcast traffic down your vpn? TAP mode is almost NEVER the correct choice.. Your performance is going to suffer as well since you will now be adding all the ethernet headers to all traffic down the tunnel.
local network defined in the main config.
He only has the 1 network, and you can put multiple networks in that config - there is little reason to adding push statements. When you can just define them in the gui where it asks for local networks.
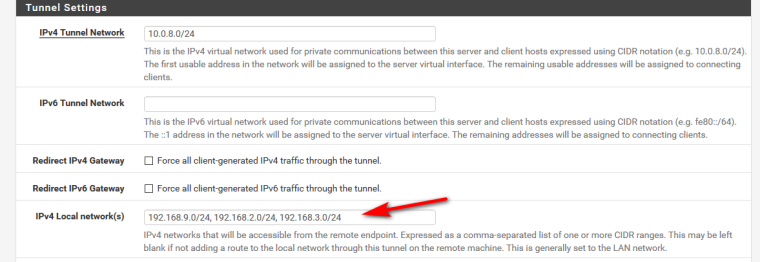
-
I never noticed the change to being able to specify multiple networks in 2.4.x. That's great!