Inter VLAN routing
-
@johnpoz said in Inter VLAN routing:
If you want vlan 103 to talk to 203 then you need a rule that allows said traffic before you send traffic out some gateway. On the vlan 103 interface, and vise versa for 203 to talk to 103
The thing is I don't have internal gateway defined like 10.103.0.1 or 10.203.0.1, all are gateways form public blocks. Can I define internal one and use it then?
-
DONT assign a gateway... Just leave it the default * so it can use its internal routing tables.. Which is knows how to get to networks its direcctly attached to, ie the vlan 103 and 203.
Create a rule on vlan 103 that says dest vlan203 net and does not assign it a gateway. Put this rule ABOVE the rule where your forcing traffic out that failover gateway.
Reverse that for your vlan 203 interface
-
Yeah I didn't notice the policy routing in your rules. Sorry.
https://www.netgate.com/docs/pfsense/routing/bypassing-policy-routing.html
-
Sth is hitting the rule but still getting timeouts
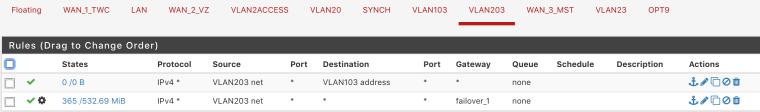
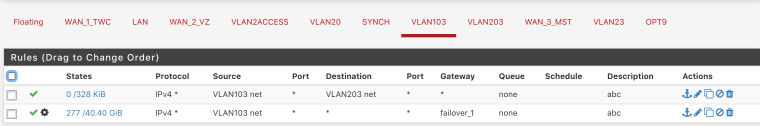
13:16:54.028880 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:54.466404 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 432, length 40
13:16:55.032488 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:56.032418 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:57.032991 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:58.030264 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:59.032380 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:59.467559 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 433, length 40
13:17:00.032288 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:00.476238 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 434, length 40
13:17:01.032384 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:02.032336 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:03.032353 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64 -
And does the other end have a firewall? Windows machines for example out of the box will not answer ping from something not on its local network.
Simple do a sniff on the vlan 103 or 203 interface in pfsense when you ping from the other vlan - do you see the request go out.. If so and no response then its the host..
-
I am not on site but the ping was tested from iphone to printer and from laptop(windows) to printer also
-
Does the printer even have a gateway set... Have seen this too many times to count there the printer does not have gateway set so you can only talk to it from the same network.
-
Yes it does have properly gateway, it was manually changed with IP and subnet.
In my case it is carp IP gw 10.103.0.3 .1 is master .2 is slave -
Then I suggest you sniff... This is not any difficult here.. You connect a vlan, you allow it from the other vlan it works.. Sniff sure the ping is being sent/seen on pfsense ingress interface, and validate it going out the egress interface towards the printer. Maybe someone F'd up the mask on the printer or typo's the gateway.
-
Diagnostics > Ping Set the source interface to the other VLAN. Ping the printer. PCAP on the printer VLAN.
Pretty much guarantee that you will see the requests going out and no reply so you will need to look at the printer configuration.
-
Ping test
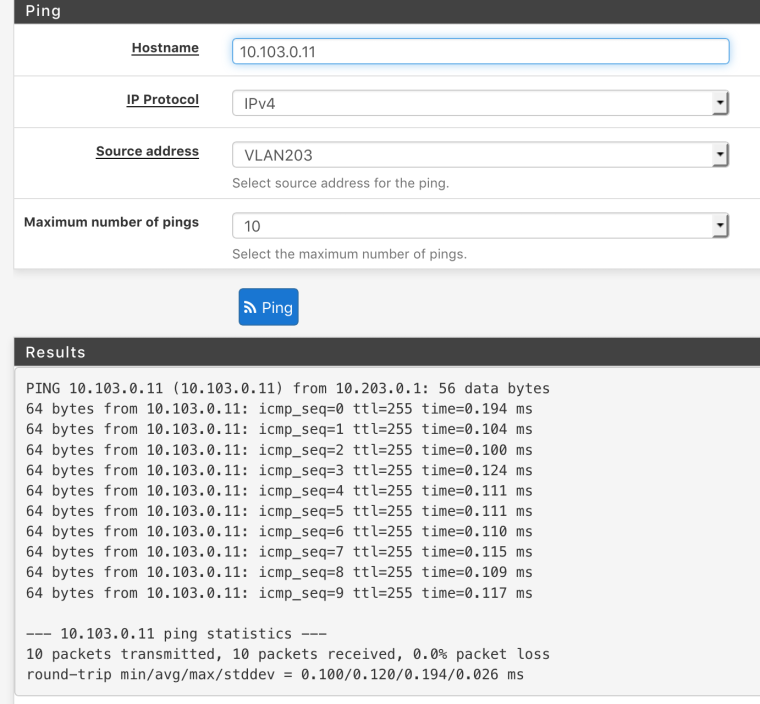
Result
14:35:44.331343 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 0, length 64
14:35:44.331427 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 0, length 64
14:35:45.334231 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 1, length 64
14:35:45.334294 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 1, length 64
14:35:46.334539 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 2, length 64
14:35:46.334604 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 2, length 64
14:35:47.338676 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 3, length 64
14:35:47.338740 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 3, length 64
14:35:48.338985 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 4, length 64
14:35:48.339051 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 4, length 64
14:35:49.343685 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 5, length 64
14:35:49.343749 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 5, length 64
14:35:50.344756 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 6, length 64
14:35:50.344820 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 6, length 64
14:35:51.350321 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 7, length 64
14:35:51.350390 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 7, length 64
14:35:52.352486 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 8, length 64
14:35:52.352550 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 8, length 64
14:35:53.355214 IP 10.203.0.1 > 10.103.0.11: ICMP echo request, id 17098, seq 9, length 64
14:35:53.355276 IP 10.103.0.11 > 10.203.0.1: ICMP echo reply, id 17098, seq 9, length 64 -
So great - are you sure your client you were pinging from pings actually got to pfsense?
-
yes
-
That is what is happening when the real client pings printer while I capture vlan 103 and printer IP 10.103.0.11
14:55:21.548856 IP 10.103.0.11.5353 > 224.0.0.251.5353: UDP, length 184
-
that is NOT a ping.. that is a mdns query to the multicast address.
Pfsense not going to do shit with that.. Unless you had avahi installed and configured.
-
Ok my bad it works, if you look up last screenshoot you will know what I screwed up