Separate Transparent HTTP Proxy for PCI DSS
-
Hello,
we need PCI DSS audit, so "one server for all" does not meet requirements (PCI Requirement 2.2.12.2.1 Implement only one primary function per server to prevent functions that require different security levels from co-existing on the same server. (For example, web servers, database servers, and DNS should be implemented on separate servers.)
Maybe smb. know or can suggest how to impliment separate transparent proxy server to meet this requirements?
Thx.
-
Anybody?
Auditor send me smth. like this.
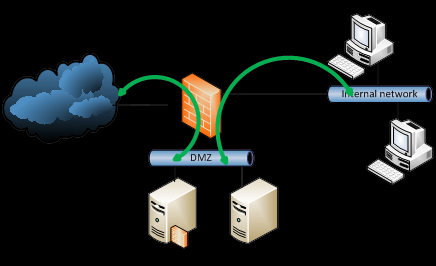
In this case it is not possible to make transparent proxy or redirect to another server where squid will be in transparent mode?
Suggestions?
-
What does running your different services on different boxes have to do with a proxy? Confused to where your proxy comes into play on your requirement..
-
I believe he wants a transparent proxy but isn't allowed to run it on his pfSense box, so he's asking how to implement a transparent proxy by itself.
Suggestions?
Use an explicit proxy instead of transparent. Use WPAD for proxy auto-discovery.
-
If your switching environment supports wccp you could use that to have a transparent proxy... But yeah best best to run proxy where its not the actual edge device like pfsense would be to just set the proxy be some discovery protocol or manual even.
-
If the proxy is in a DMZ separate from the clients then it's easy to do with NAT.
port forward in on LAN for a destination of any, port 80, sent to a target of the proxy on the proxy port
Repeat for 443 if you're doing SSLMaybe exclude the firewall from that, and local things, but that's the general gist. That's all the squid package does internally, just forwards to 127.0.0.1 instead of another box.
If the proxy is in the same subnet as the clients then it's trickier since you'd have to exclude the proxy box as a source in that rule, and work around other issues to mask the source, so don't do that.