Hyper-V 2016 + virtual pfSense + Windows ADDS, DHCP, DNS + VLANs
-
I want to post this because I couldn't find a solution to my environment. And I assume there has to be others that are trying to accomplish this setup.
Goal: Create an isolated virtual lab environment using the following... Hyper-V 2016, Server 2016(ADDS,DNS,DHCP), Windows 10 clients, and pfSense Virtual Router with multiple VLANs.
Everything would work without much configuration until I got to the VLAN setup. By default, Hyper-V configures each VMNetworkAdapter as "untagged". This is fine if everything is on the same subnet. But I needed to dig a little deeper...
Step 1: In Hyper-V, create two virtual switches.
WAN Switch
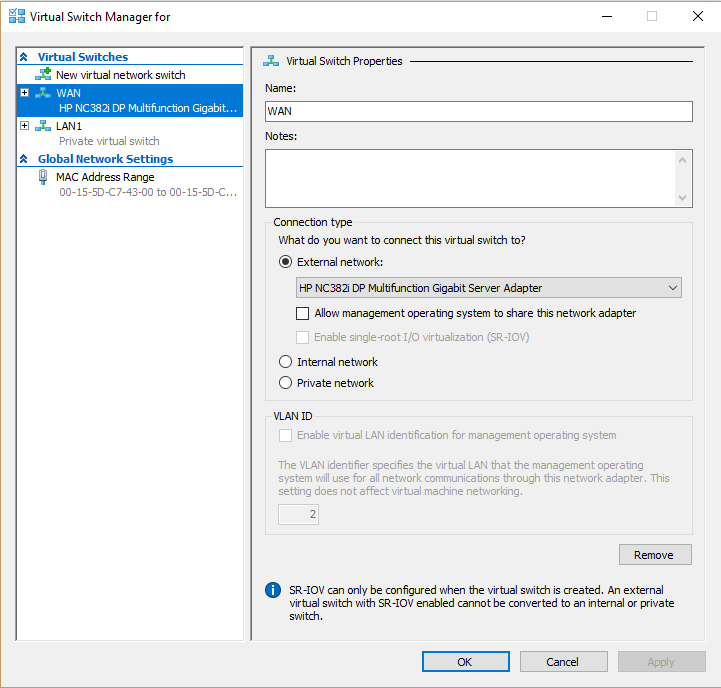
LAN Switch
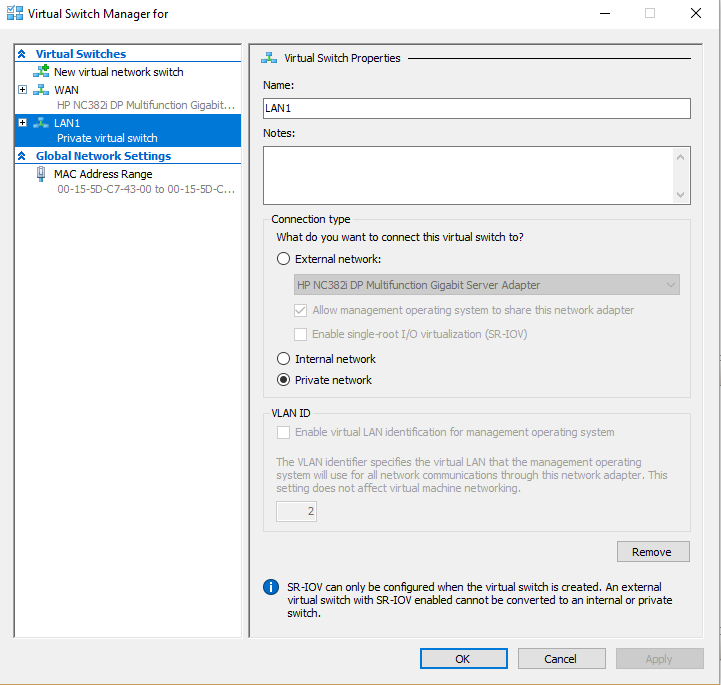
Step 2: Create all of your VM’s (Server, Workstations, and pfSense router)
Step 3: Assign the LAN and WAN switch to your pfSense VM. Then on each VM, assign the LAN switch and set the VLAN ID according to which subnet you want the machine a part of.
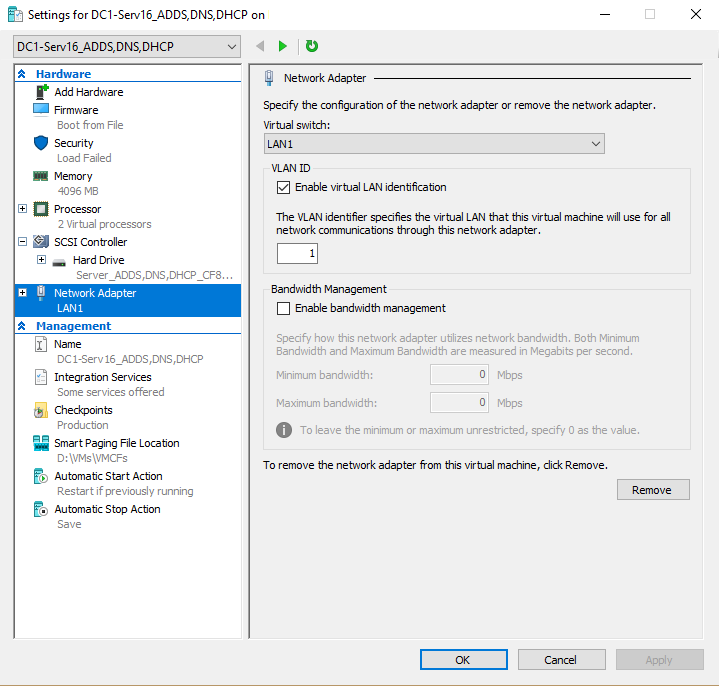
Step 4: Use the following PowerShell commands on your Hyper-V host.
To view all VMNetworkAdapters:Get-VMNetworkAdapter –allTo view all VMNetworkAdapter VLAN assignments:
Get-VMNetworkAdapterVlan *Find the Mac address of your pfSense LAN switch from above. Use that in the following command to make the port a trunk for all VLANs and set the native vlan as 1:
Get-VMNetworkAdapter –VMName “xxxxxxxx” | Where-Object MacAddress –EQ xxxxxxxxxxxx | Set-VMNetworkAdapterVlan –Trunk –AllowedVlanIdList “1-4094” –NativeVlanId 1Step 5: Configure your pfSense router. I used the following settings:
- Set WAN with Static IP and gateway (depends on your network) and assigned it to interface hn0
- Set LAN with Static IP, no gateway, no DHCP, no IPv6, assigned it to interface hn1 (This is your virtual routers new IP address)
- OPT1: Create VLAN 2, set static IP, no gateway, no DHCP, no IPv6 and assigned it to hn1.2
- OPT2: Create VLAN 3, set static IP, no gateway, no DHCP, no IPv6 and assigned it to hn1.3
On web Interface:
- System/Advanced/Firewall&NAT “NAT” TFTP Proxy (highlight OPT1&2)
- System/Advanced/Networking “Ipv6 Options” Allow IPv6 (uncheck)
- System/GeneralSetup “System” Set hostname and Domain
- System/GeneralSetup “DNS Server Settings” Set your local DNS server IP
- System/GeneralSetup “DNS Server Settings” Disable DNS Forwarder (check)
- System/GeneralSetup “Localization” Set timezone
- Firewall/Rules/LAN “Rules” Delete default rules
- Firewall/Rules/LAN “Rules” Create a new rule:
- Interface “LAN”
- Protocol “ANY”
- Source “ANY”
- Destination “ANY”
- Extra Options “Show Advanced”
- Advanced Options “Allow IP Options” (Check)
- TCP Flags “Any Flags” (Check)
- Copy this rule to OPT1 and OPT2.
- Firewall/Rules/OPT1 Change OPT1 rule to:
- Interface “OPT1”
- Firewall/Rules/OPT2 Change OPT2 rule to:
- Interface “OPT2”
- Services/DHCPRelay Enable (Check)
- Services/DHCPRelay Interfaces (Select OPT1&OPT2)
- Services/DHCPRelay Append circuit ID (Check)
- Services/DHCPRelay Destination Server (IP of local DHCP server)
- Services/DNSResolver/GeneralSettings “General” Enable (Uncheck)
- Services/DNSForwarder “General” Enable (Uncheck)
Step 6: Configure your Windows server for AD DS, DHCP and DNS
Step 7: Power on your workstations and all should be on the right subnet with a DHCP address from your Windows server
-
I did the same thing on my 2012r2 earlier but I ran into something strange with the vlan part - it works, for a couple of days and then it just stops. no traffic att all can get through regardless of what you do. Not even arp. Nothing helps untill I add or remove a nic on the vm. Don't have to configure it, just a change of the numbers of adapters in the pfsense vm and it wworks again for som days ..........
Never found the root cause for it but im suspecting the e1000 driver. Simply gave the pfaense more nics and gave them a vlan each as workaround
-
@mats I've seen the same thing with 2012r2 and doing a trunk. But it seems to work fine with 2016 or 2019.
-
time to plan an update then. After all I do got licenses for 2019 when it is rereleased
-
on which interface are you connecting to your physical lan ? Are you using the wan interface for this ? Why not use different private switches for each vlan ?
-
@swinn I’m using Server 2016 on a Hp DL380 G7.
-
@actionhenk Yes, I’m using my wan interface with one of my 4 physical nics. I am using only one virtual switch for the whole lan. Since it’s a layer 2 switch, it can pass vlan traffic, so I didn’t want to have multiple lan interfaces and switches. This setup is the same as a physical setup, which was the plan.
-
@actionhenk One downside of using an interface for each vlan is that you are limited to eight interfaces per vm.
-
@swinn you can make it twelve if you want to. 8 standard + 4 legacy but I agree, if you can do vlan trunking stable - it's more flexible