PFSENSE : Disable WAN WebGUI on Virtual IP port for use later
-
Hello everyone,
I would like to disable WebGUI port on WAN(port 80) for use later with the NAT, Is it possible ?
Thank you
-
huh? Just because pfsense listens on 80 on all IPs for its webgui - you can still forward it.
But you can have pfsense webgui listen on any port you want, if you don't want it to listen on 80 then just change it.
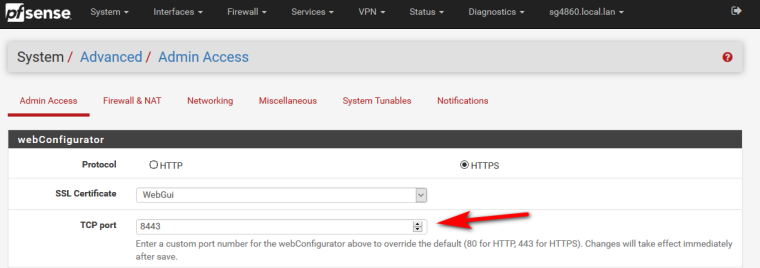
-
No, I'm sorry, I didn't specify that I was using the virtual IP address (10.1.1.251, for example) and that I wanted to remove or disable the access port (80) to WebGUI. Because I want to use NAT on 10.1.1.251:80 and redirect to a LAN IP address, if it's possible.
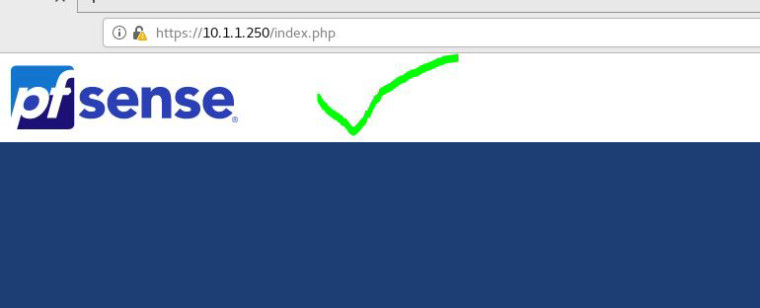
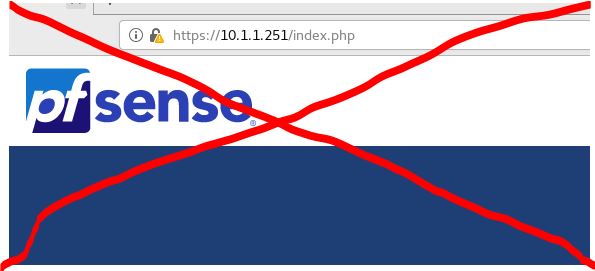
Thank you !
-
And again you can change the port the webgui listens on..
And again it doesn't matter if it listens on a vip.. NATs happen before! So nat away..
So your wan is rfc1918 - WTF you need to nat for? Natting from rfc1918 to rfc1918 doesn't make a lot of sense in the first place.
-
Yes, i understand and i just tested, but it's not that i would like.
I would like redirect all paquets to destination of my virtuel IP(10.1.1251) located on my WAN interface (10.1.1.250) to my LAN IP(192.168.1.2).
I would like for all ports like 80, 443...etc(from 1 to 65535) redirect them to my LAN IP.I don't konw if i was clear
Thanks
-
Then do a bit of RTFM: https://www.netgate.com/docs/pfsense/book/nat/1-1-nat.html
-
Exactly^ but still pretty much zero reason to NAT at all from rfc1918 to 1918 unless you have to use overlapping networks - which is bad choice.. If you have 2 rfc1918 networks that overlap - then just change 1, not like there is not plenty of networks to use in rfc1918 space.
-
Ok thank you for all these responses, please excuse me for not reading the documentation properly.
Problem solved thanks ! ;) -
All,
Looking to disable the WebGUI listener on any interface except the Management NIC. Reason: the ability to use HAProxy (for security reasons) on all other ports. Part of this goes to the point that you WANT management on it's standard port (443) on the Management NIC and not have a listener on any other interface. This should be "a reasonable reason" for both purposes - restricting the listener to only the management NIC, keeping it on the default port for standardization and being able to utilize HAProxy on other NICs.
Did attempt to play with the config, but appears that the software stomps on the config file (for nginx). Thus, even trying to manually tool it results in an unsuccessful result.
Thanks!
-
Any manual edits of configs will most likely be overwritten on service restart, reboot, upgrade, etc.
If you want to call out to just listen on interface X and not listen any other interfaces you should put in a feature request on redmine..
-
FWIW - submitted it and the response was a bit disheartening. Apparently a ticket has been open over 8 years ago on this issue. A work-around was suggested. The primary issue with "work arounds" is that at some point when a firewall's configuration is complex enough - it begins to look like a spaghetti mess. Some years ago was tasked with auditing and cleaning up a firewall where it was on the order of somewhere around 36k lines.
Every change to code on a product has a cost, but hopefully at some point this issue (and like issues) will be resolved so that work arounds aren't required. Not to mention the fact that adding unnecessary complexity simply aids in the probability of mistakes or inadvertent passing of unintended packets. There's an interesting line between simplicity and the ability to provide enough "configure-ability" to meet a variety of needs.