DMZ for VMs with VM pfSense
-
@luckyzor said in DMZ for VMs with VM pfSense:
Unfortunately, I can't get IP from the DHCP
Then you have a layer 2 problem.. Or you did not enable dhcp on that interface..
-
@johnpoz said in DMZ for VMs with VM pfSense:
@luckyzor said in DMZ for VMs with VM pfSense:
Unfortunately, I can't get IP from the DHCP
Then you have a layer 2 problem.. Or you did not enable dhcp on that interface..
I found the problem. I don't know why but my configuration file for the 2nd NIC disappeared.
I created a new one. restart network solved.Now I'm back to the DMZ zone:
I create the isolate VN as @viragomann said.
When add this interface as OPT in pfSense with no rules, I have access to LAN net.
I started to go to rules -> DMZ -> Create Rule.
Created a rule to block everything. surprise, I still have access from LAN net to DMZ and vice-versa. is it normal?Thanks for your help
-
No, an isolated network has no connection to anywhere as long as there is no device connected to it which passes the traffic.
If you can't find the leak use traeceroute to investigate which node let the packets pass to LAN.
-
@viragomann said in DMZ for VMs with VM pfSense:
No, an isolated network has no connection to anywhere as long as there is no device connected to it which passes the traffic.
If you can't find the leak use traeceroute to investigate which node let the packets pass to LAN.
@viragomann I created the vDMZ (isolated / no DHCP / ip 192.168.2.0/24)
Attached this network to the VM-http and the VM-pfSense.
Created the DMZ interface with the vDMZ.
Until here is like that I need to do in KVM?
-
The vDMZ must also have no static routes activated. Apart from that, it should be fine.
-
@viragomann said in DMZ for VMs with VM pfSense:
The vDMZ must also have no static routes activated. Apart from that, it should be fine.
I've just added the vDMZ to the VM-http and I can ping the host and the host can ping the VM. how can I block this?
-
Can you also ping the host if you disconnect the pfSense from vDMZ in VMM?
-
@viragomann said in DMZ for VMs with VM pfSense:
Can you also ping the host if you disconnect the pfSense from vDMZ in VMM?
Yes. the vDMZ is not added to the VM-pfSense.
So the problem is in the Host machine I guess, but don't know what to do. -
@luckyzor said in DMZ for VMs with VM pfSense:
@viragomann said in DMZ for VMs with VM pfSense:
Can you also ping the host if you disconnect the pfSense from vDMZ in VMM?
Yes. the vDMZ is not added to the VM-pfSense.
So the problem is in the Host machine I guess, but don't know what to do.I found this route in the Host :
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 virbr0I deleted and now ping doens't work anymore. Is this the solution? thanks for the help
-
That route should have no effect, since there is no router specified. It only defines the network on vibr0 (vDMZ?).
-
@viragomann said in DMZ for VMs with VM pfSense:
That route should have no effect, since there is no router specified. It only defines the network on vibr0 (vDMZ?).
Yes vibr0 is the vDMZ, apparently this route is automatically created when creating the vDMZ with virt-manager.
After deleting this rule. everything works perfectly.
One last question about rules in pfSense:
Is this a good way to configure the rules?
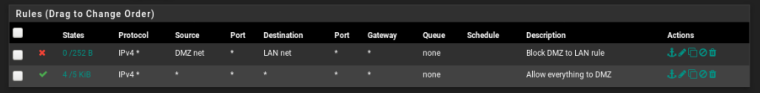
thanks a lot for your help
-
If you enter a network when creating a virtual isolated network in VMM, the host gets automatically the first IP out of it. So if you want it to isolate the vNet also from the host, don't set a network.
I use to add an alias included all RFC1918 networks to block devices from any internal access.
Consider that you will need an additional pass rule to allow access to pfSense itself if you use it as DNS server for the DMZ.