openvpn packets getting returned over WAN gateway and not VPN gateway
-
If it were simple, I would want that for only one VLAN (and only one remote domain even) but I'm finding routing in pfSense to be so scattered across things that I want to keep it stupid simple until I get my head around all of the pieces and parts.
Ultimately, I'm only doing this so I can watch blackout NHL.TV on my Rokus. But for now, the true idiot's guide is what I'm after.
-
Okay so you want to pick and choose what devices go over vpn on a certain subnet ?
-
That would be truly ideal, but if it isn't simple I might shy away from it.
-
@scottlindner
It's simple so basically the screenshots I provide is what you want. Just ignore the ports that I open.Tell me what network and ips on that network you want to go over vpn. I'll cook up a screenshot or 2 for you based off what you want to happen .
-
Here are the internal LAN IPs I want routed over the OpenVPN Client: 192.168.13.67, 192.168.13.76, 192.168.13.78
I really appreciate this!
-
@scottlindner
Do you have another network other than the 192.168.13.x/24?
If you do have a second network does that network need to go over the WAN or VPN? -
@sesipod yes. I have the untagged LAN carrying tagged traffic (trunk) and four tagged VLANs all going out over the gateway group which includes my WAN interface and a broadband interface as failover.
-
@scottlindner
oh geez ...
Well you can basically follow the screen caps above but ignore the Rules I have for OPT3 network. I am at work right now so I do not have my pfsense page up. Try the below and let me know ( if ) it works out for you. I basically made everything on the 13.x stay on the WAN unless you made a rule for the individual IP on that network.- OpenVpn RULES tab
You should have noting in there.
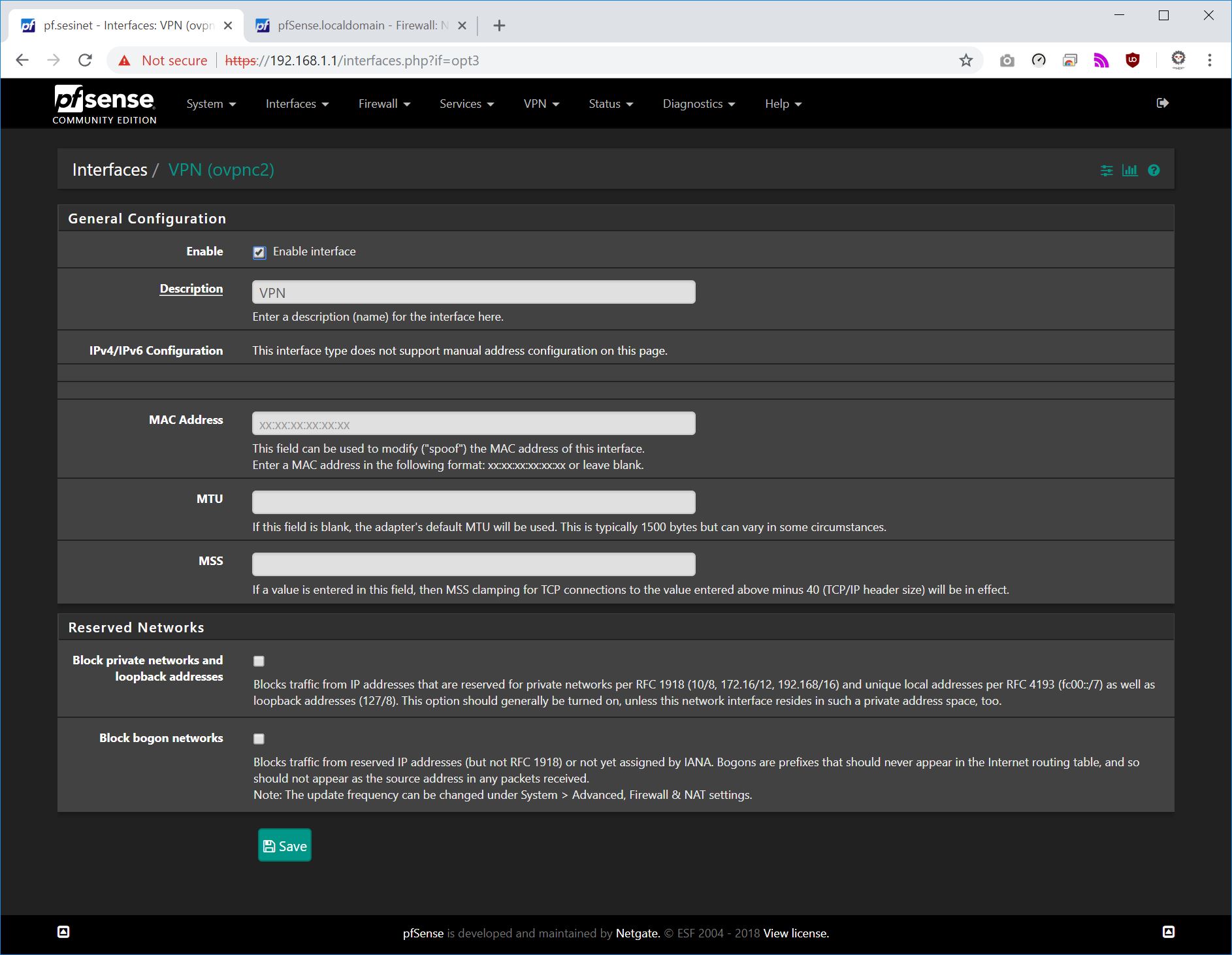
- Interfaces
You should have the vpn interface assigned mine is called OPT3 above. You just add it and then press save making sure that it's enabled.
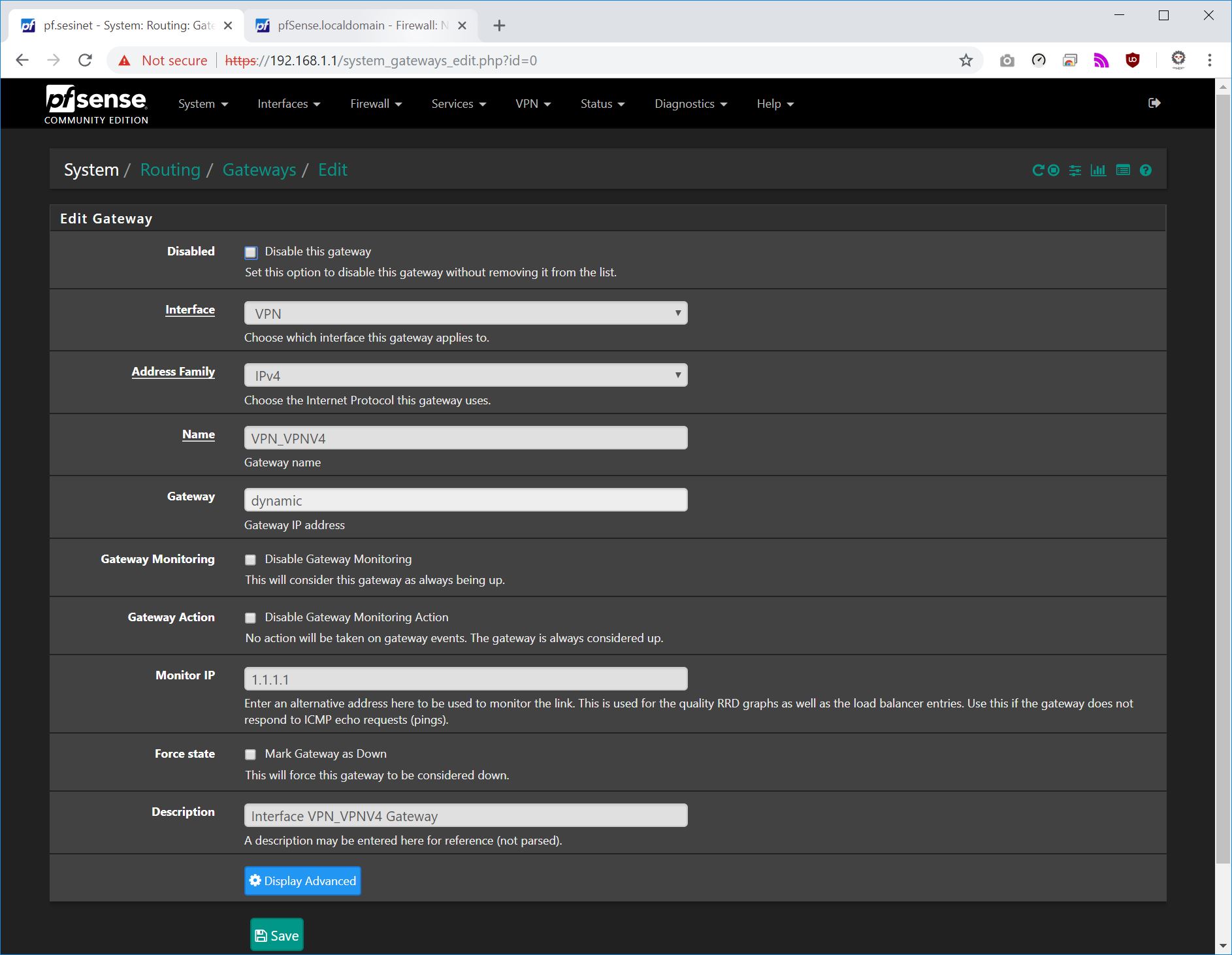
** I do not think that you have to set the vpn interface as the default gateway. However in my screen shots above I did and everything is working. You might want to test this. I do know if you do that you will have to update your rules for each network that is intended for WAN to have the advanced option gateway set as WAN
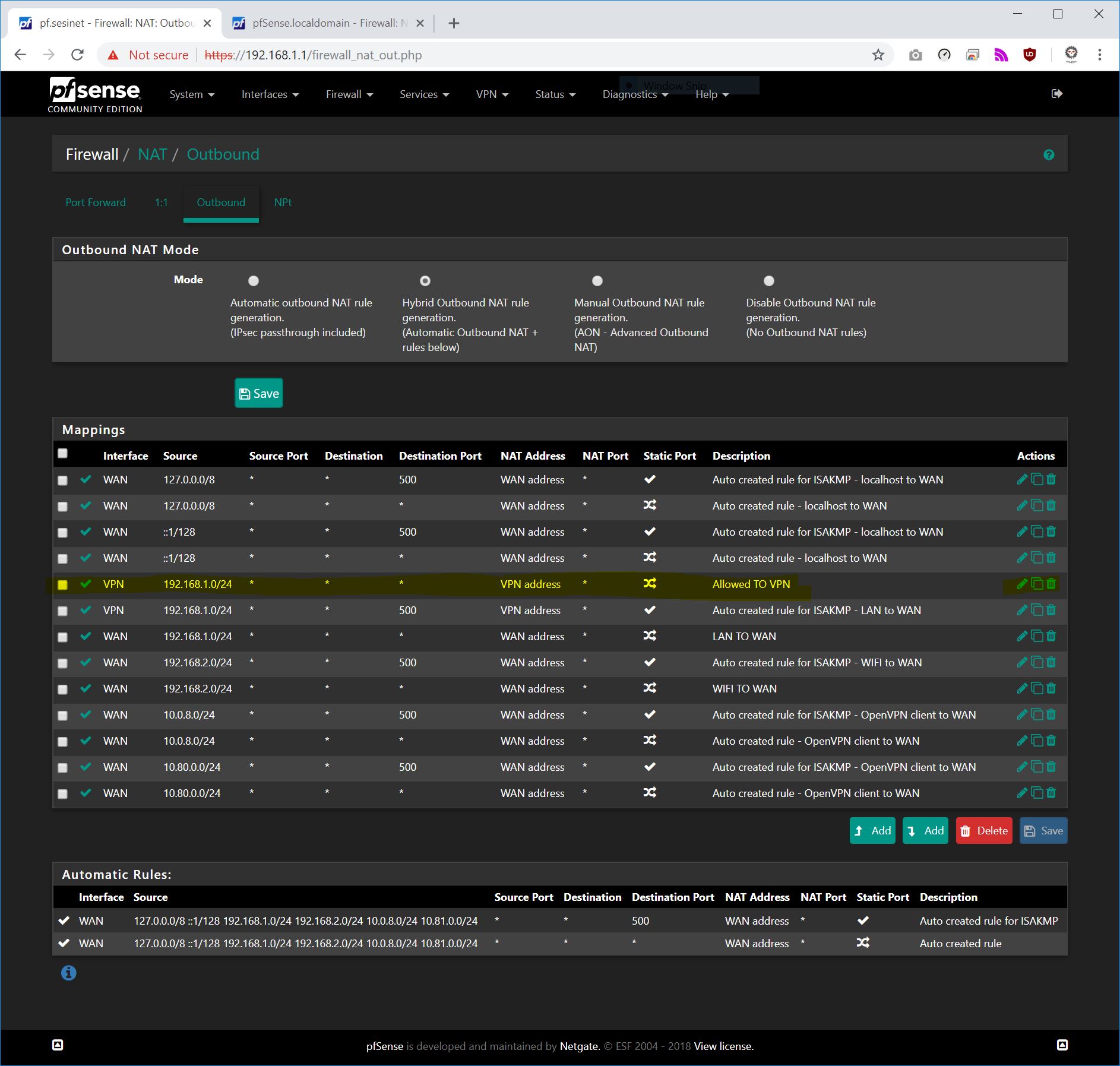
- outbound nat page
Switch to (hybrid) or (manual)
For the 192.168.13.x/24 network copy the existing WAN interface mapping. In the new mapping setup change the Interface to your VPN Gateway interface. Put the new mapping above the WAN mapping for this .13.x network.
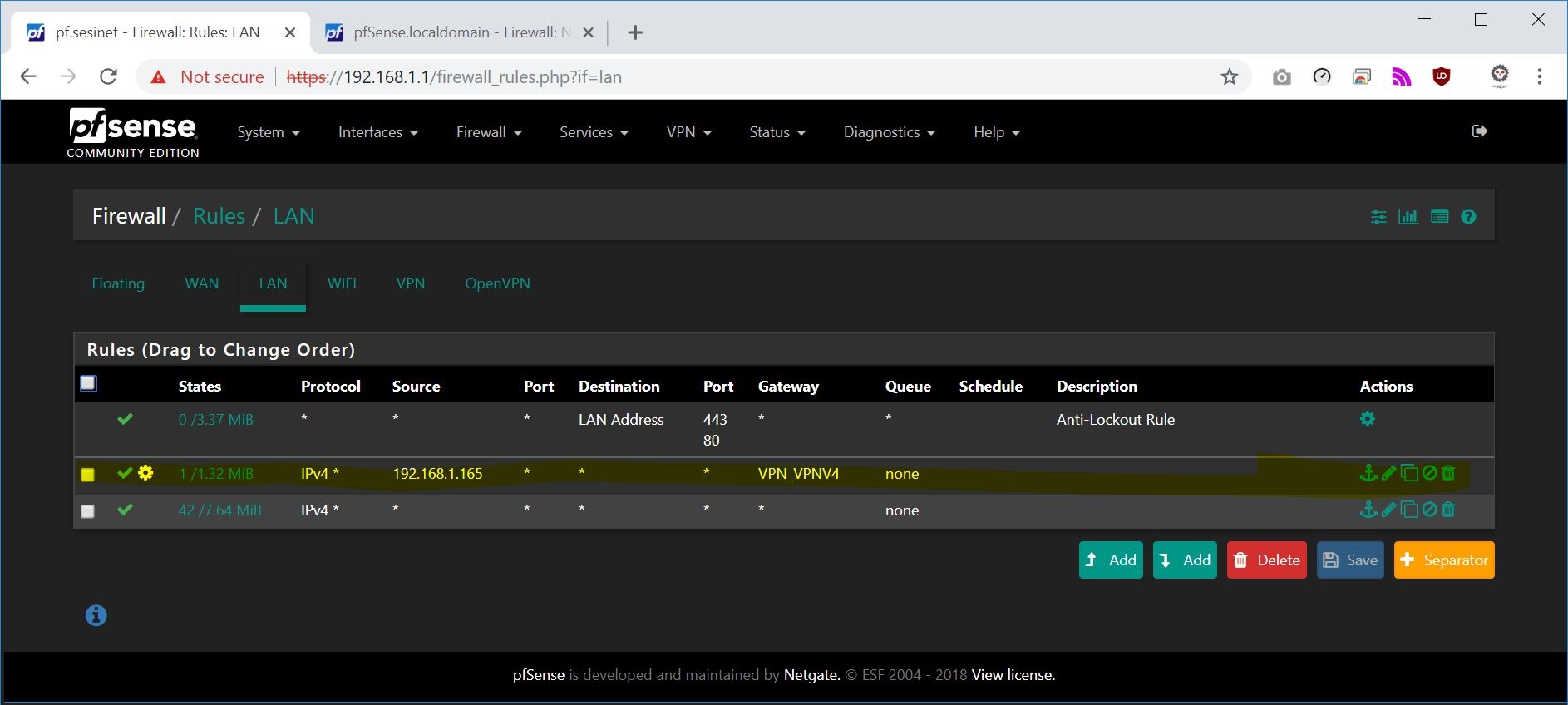
- Rules Tab
13.x network Tab:
Starting out we will setup the 3 ips that you want over the VPN these rules should be placed above all others. ( rules 1-3 ) the last rule ( rule 4 ) is stating anything else will take WAN gateway.
Rule #1
Protocol: IPV4 ALL
Source: 192.168.13.67
Port: ANY
Destination ANY
PORT: ANY
(advanced) - Gateway - VPN GatewayRule #2
Protocol: IPV4 ALL
Source: 192.168.13.76
Port: ANY
Destination ANY
PORT: ANY
(advanced) - Gateway - VPN GatewayRule #3
Protocol: IPV4 ALL
Source: 192.168.13.78
Port: ANY
Destination ANY
PORT: ANY
(advanced) - Gateway - VPN GatewayRule #4
Protocol: IPV4 ALL
Source: (networkname) net
Port: ANY
Destination ANY
PORT: ANY
(advanced) - Gateway - WAN Gateway. -
I swear I'm doing everything you have specified here but the moment I switch on the OpenVPN Client all WAN access dies for the LAN and all VLANs.
-
Check Don't Pull Routes in the VPN client.