pfBlockerNG-devel feedback
-
@veldkornet said in pfBlockerNG-devel feedback:
So first off, was it supposed to be .*conf? Or *.conf? Secondly, what's this pfb_dnsbl_lighty.conf file?
No this is not the correct way. Moving the asterisk as you did will include other temporary files that are in that folder.
You seem to have some other issue with the Resolver configuration.
Goto the pfSense DNS Resolver and increase the log verbosity to 2, and then review the resolver.log for additional clues.
-
Hi all
Everything was working fine no changes have been made but for the last couple days
i have been getting the errors listed below
DNSBL OUT OF SYNC
*** DNSBL update [ 1308990 ] [ 1308991 ] ... OUT OF SYNC ! *** [ 10/10/18 17:52:40 ]
followed listed instructions above to try and correct the errors with no luck
DNSBL log attachAlso getting
domain/ referer feed
iadsdk.apple.com [ Unknown ] Unknown
DNSBL-HTTPS | Unknown Unknown
ocsp.digicert.com [ Unknown ] Unknown
www.youtube.com [ Unknown ] Unknown
DNSBL-HTTPS | Unknown Unknown
DNSBL-HTTPS | Unknown Unknown
liveupdate.symantec.com [ Unknown ] UnknownAnother
disable log under floating rules doesn’t not seem to work for me, i created
ipv4 list disable logs for that list and global log is also disable but the rules
is still being created with log enable.
0_1539269924600_DNSBL.txt -
The sync is off by one, so its not critical in the sense that its still going to block the domains listed. There is a disrepancy of the number of domains listed in the Unbound DB vs the /dnsbl/ folder.
I'd suggest a Force Reload and see if that fixes it.
-
@bbcan177
I started seeing the SQLite3 error myself:Warning: SQLite3::exec(): database disk image is malformed in /usr/local/pkg/pfblockerng/pfblockerng.inc on line 3931 Warning: SQLite3::exec(): database disk image is malformed in /usr/local/pkg/pfblockerng/pfblockerng.inc on line 3934 Warning: SQLite3::query(): Unable to prepare statement: 11, database disk image is malformed in /usr/local/www/widgets/widgets/pfblockerng.widget.php on line 297I first noticed it today when logging on to check for updates. The message appeared after the update.
2.4.5-DEVELOPMENT (amd64) Current Base System: 2.4.5.a.20181025.0115 built on Thu Oct 25 01:16:47 EDT 2018 FreeBSD 11.2-RELEASE-p4 pfBlockerNG 2.2.5_17I read thru the posts on how to fix. Just wanted to know know if there is any information you want before I take action.
-
@xentrk said in pfBlockerNG-devel feedback:
I started seeing the SQLite3 error myself:
Warning: SQLite3::exec(): database disk image is malformed in /usr/local/pkg/pfblockerng/pfblockerng.inc onThis is a different issue. I sent you a PM.
-
Just saw that _18 was online! Great! So installed it with the new wizard, really nice touch!
Quick question before having a bigger look into it: The wizard created an alias on LAN per default. In the corresponding DNSBL page flagged with "CARP beta" there's an option to change that to a CARP VIP: Why not use an Alias for the CARP VIP (on LAN) instead? The advantage would be that a) you don't have to configure a full CARP interface setup (and have problems like in another thread, that pfBNG always uses VHID 1 and that's potentially dangerout!) AND as an alias on top of an existing CARP interface - and I would assume almost every CARP setup uses a CARP VIP on LAN - you won't have to think about syncing either, as Alias-style VIPs on CARPs are synced via VirtualIP standards. Also you would use the already configured (and working) LAN VIP as your carrier and failing over with it, too. So I can see no problems with that.
If CARP setting stays, than I'd recommend adding VHID field for configuring that, too, as always using 1 (as said above) is potentially dangerous with other clusters in the same network broadcast domain.
Greets,
Jens -
@jegr said in pfBlockerNG-devel feedback:
Just saw that _18 was online! Great! So installed it with the new wizard, really nice touch!
Thanks. Yes it was on the list of to-do items... List just never stops ;)
Quick question before having a bigger look into it: The wizard created an alias on LAN per default. In the corresponding DNSBL page flagged with "CARP beta" there's an option to change that to a CARP VIP: Why not use an Alias for the CARP VIP (on LAN) instead? The advantage would be that a) you don't have to configure a full CARP interface setup (and have problems like in another thread, that pfBNG always uses VHID 1 and that's potentially dangerout!) AND as an alias on top of an existing CARP interface - and I would assume almost every CARP setup uses a CARP VIP on LAN - you won't have to think about syncing either, as Alias-style VIPs on CARPs are synced via VirtualIP standards. Also you would use the already configured (and working) LAN VIP as your carrier and failing over with it, too. So I can see no problems with that.
If CARP setting stays, than I'd recommend adding VHID field for configuring that, too, as always using 1 (as said above) is potentially dangerous with other clusters in the same network broadcast domain.I am not a user of CARP, so all feedback appreciated about it.... I can definately add a "VHID" option and will checkout the Alias option also...
I will see if one of the pfSense Devs will help offline to ensure I am covering all bases...
Appreciated!
-
@bbcan177 said in pfBlockerNG-devel feedback:
I am not a user of CARP, so all feedback appreciated about it.... I can definately add a "VHID" option and will checkout the Alias option also...
If no one would report other, I'd go with the Alias option if I'd be you ;) Piggy-backing the existing CARP VIP is far easier than creating a separate CARP interface and is also recommended bei the devs itself to reduce network multicast/broadcasting overhead. :)
Offering the CARP option, too, would cover those missing corner cases, whereas someone doesn't use a VIP on LAN (or other interfaces) for some reason or another. :) -
Please I need help with strange behaviour of pfBlockerNG-devel in my network.
I have logs full of denied connections to UA servers 176.119.4.9:53 UDP and 176.119.4.8:53 UDP.
After some research I found that pfsense box is asking continuously for PTR 8.4.119.176.in-addr.arpa and PTR 9.4.119.176.in-addr.arpa. According to "lsof -n|grep UDP" on pfsense box process who is generating these reguest is "php_pfb"..:php_pfb 47639 root 15u IPv4 0xfffff8004cb469e0 0t0 UDP wan_IP:36014->isp_dns_IP:domain
I believe this issue is same as mentioned here.. https://www.reddit.com/r/homelab/comments/9u4nqm/windows_dns_server_dnsexe_sending_to_known_bad/
Thanks for any help
pfBlockerNG-devel 2.2.5_19
pfsense2.4.4-RELEASE (amd64) -
Increase the pfSense Resolver -> Log Verbosity -> 3 (I can't remember if 2 is enough to log outbound DNS requests). Then review the resolver.log to see which Lan device on your network is making those requests.
-
I´ve already done that.
This Lan device is internal DNS server. From logs it´s trying to resolve PTR 8.4.119.176.in-addr.arpa and PTR 9.4.119.176.in-addr.arpa queries by contacting 176.119.4.9:53 UDP and 176.119.4.8:53 UDP. But these queries are coming from pfsense box.In pfsense dns logs is visible that pfsense is asking not only my internal LAN DNS but ISP DNS server as well.
And connections from my LAN DNS server are denied by pfBlockerNG
(to servers 176.119.4.9 and 176.119.4.8 ....this range is blacklisted via feed https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt) -
I was alerted of a crash recently and had to manually restart the two pfBlocker processes:
pfb_dnsbl - pfBlockerNG DNSBL service
pfb_filter - pfBlockerNG firewall filter serviceI am running pfBlockerNG-devel net 2.2.5_22
Crash report begins. Anonymous machine information: amd64 11.2-RELEASE-p6 FreeBSD 11.2-RELEASE-p6 #3 518496b29ae(RELENG_2_4_4): Wed Dec 12 07:41:44 EST 2018 root@buildbot2.nyi.netgate.com:/build/ce-crossbuild-244/obj/amd64/ZfGpH5cd/build/ce-crossbuild-244/pfSense/tmp/FreeBSD-src/sys/pfSense Crash report details: PHP Errors: [26-Mar-2019 14:29:44 America/Chicago] PHP Fatal error: Allowed memory size of 536870912 bytes exhausted (tried to allocate 4096 bytes) in /usr/local/www/pfblockerng/pfblockerng_log.php on line 192 [26-Mar-2019 14:29:44 America/Chicago] PHP Fatal error: Allowed memory size of 536870912 bytes exhausted (tried to allocate 12288 bytes) in /etc/inc/notices.inc on line 105 -
@TekGamer You attempted to open a large log file in the Log browser and it ran out of memory. Either need to download the file and view in an offline viewer or view that file from the shell.
-
@BBcan177 Ok, in a future release, is it an option for you have the viewer not attempt to load a log file if it is too large, and just display a message to download it to view in an offline viewer? So it doesn't crash?
-
You can manage the log files size in Log Settings (max lines)
Some of the other types of files available to browse are just too big for any browser/viewer.Increasing memory on the system might help, but again there are limits in what you can do in a browser.
-
I’ll check my log size, I did leave it at the default. As for RAM, I already have 16 GB, which is the max my Qotom Q575G6 supports.
-
You can increase some memory limits in /etc/inc/config.inc, however the changes will be lost on pfsense upgrade.
// Set memory limit to 512M on amd64. if ($ARCH == "amd64") { ini_set("memory_limit", "512M"); } else { ini_set("memory_limit", "128M"); } -
I installed pfBlockerNG-devel on a fresh 2.4.4 system.
For the Firewall 'Auto' Rule Order, how do I get the "Default Order"(original format) into the drop down selection list? I don't want to allow pfB_Pass/Match before all other rules - I just want pfB_Block/Reject same as pfBlocker 2.1.4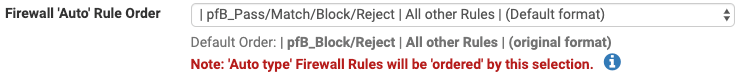
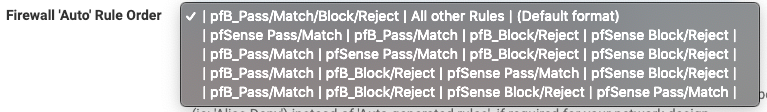
-
@Double-K
Those are the default settings now... If none of those Auto rule settings work for your needs, you can always use "Alias Type" Action settings and manually create the firewall rules to suit. Click on the blue infoblock icon for the Action setting for more details. -
@BBcan177 Thanks! Any plan to offer both options (the new default format & the old original format)?