Captive portal
-
@free4 said in Captive portal:
reconfigure a captive portal while some users are connected to it cause trouble for these users.
Very true.
To make a long story sort, for now (2.4.4) : when reconfiguring portal setting, flush all users.
If not, you'll be in for a hard time.To see why :
Enter console, option 8 and typeipfw table all listNote the list of IP's (users) who are connected.
Now, configure your captive portal zone, validate and retypeipfw table all listSee that the 2 tables that contains the connected user is empty now.
But, the Status page in the GUI of the captive portals will show that these very same users are still "connected".
Result : these users won't be able to reconnect.
-
thanks for the info, if I Disconnect all users after a CP reconfiguration all users will be able to reconnect on the CP.
now I still have one more problem, when I enable a CP on WORK_NETWORK i get blocked traffic on HOME_Network blocked by a default rule until I disable all CP or do a reboot.
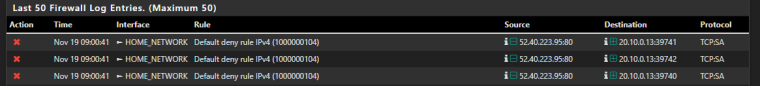
i don't see why CP and traffic on my Home network are related.
Br,
Vuko -
@vukomir said in Captive portal:
when I enable a CP traffic on HOME_NETWORK
How do you enable traffic ?
@vukomir said in Captive portal:
when I enable a CP traffic on HOME_NETWORK that is not part of any CP
CP traffic that is not part of the CP ?
Also :
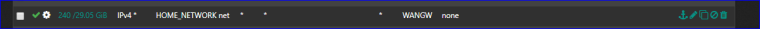
Why the Gateway here ?
-
@gertjan
i update my last post. my problem is:When I enable a CP on WORK_NETWORK i get blocked traffic on HOME_Network blocked by a default rule until I disable all CP or do a reboot. i don't have CP on HOME_NETWORK
the gateway is specified to allow internet connection from HOME_Network
Vuko.
-
Ok.
What is your LAN side setup ?
You have a (one ?!) LAN interface, activated 2 VLAN's on it - you have a VLAN managed switch that separates the two VLAN's for you, and several LAN connectors on that switch that represent your HOME network and WOK network - right ?Slowly but surely, I guess the VLAN setup is "done" yet.
I never used VLANs, and prefer using separated NIC's for my LAN (which is my "work" or company" LAN and a second LAN (OPT1 interface) for my Wifi resevered "hostile" (== clients of the company).
Both interfaces have their own GUI firewall rules - separated, non overlapping networks.
This works out of the box for a decade or so. -
I have a lagg0 on 3 NIC's and 6 VLAN's over that VLAN
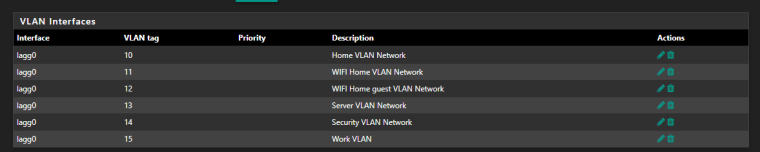
I also have a VLAN managed switch that separates all my VLAN.
my setups are working as it is now, the only problem I have is when I enable CP.on VLAN you also have a separated GUI interface per VLAN.
-
Ok, I was just checking.
CP works perfectly well on a VLAN.About the "1000000103" rule ( see /tmp/rules.debug )is the default "back-off rule" rule that kicks in if there are no other, more permissive rules on a used interface.
So, IPv4 traffic comes in on an interface without ( any ? ) GUI firewall rules. -
I found the rules in the file
Outbound NAT rules (automatic)
#---------------------------------------------------------------------------
default deny rules
#---------------------------------------------------------------------------
block in log inet all tracker 1000000103 label "Default deny rule IPv4"
block out log inet all tracker 1000000104 label "Default deny rule IPv4"don't understand why this rule kick's in only when I enable CP(CP is not enabled on the same VLAN where the rule is applied)
Vuko
-
About you image https://forum.netgate.com/assets/uploads/files/1542545594673-beae0120-f3b1-4c9d-8488-5ea5055fb288-image.png
Is this this the HOME network ? WORK network ? the CP network ?
The first rule : the anti lockout rule. Port 81 ?Rule 2 :I don't see the use oof the second "HOME_NETWORK to HOME_NEWORK " rule. pfSense can't block or even "see" traffic on the same network segment.
Rule 3 : No one one the HOME_NETWORK connects to the SERVER_NETWORK.
Rule 4 : WIFI_NETOWRK ?
Rule 5 : same as 3.
Rule 6 : The gateway issue .... dono why you should use a gateway here.
Rule 7 : this is not the 1000000103 rule, so packets that are blocked are not using this Interface / these rules.
So, it's something else you didn't showed yet.
-
it's the HOME network
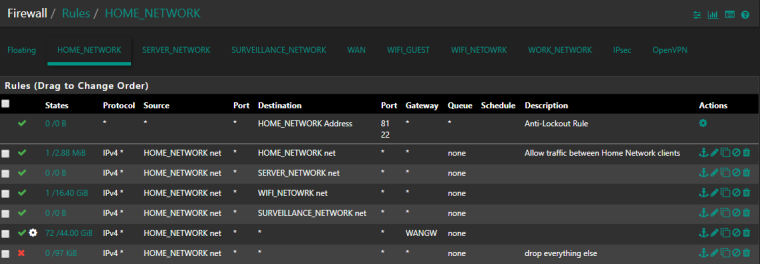
this my my Work Network
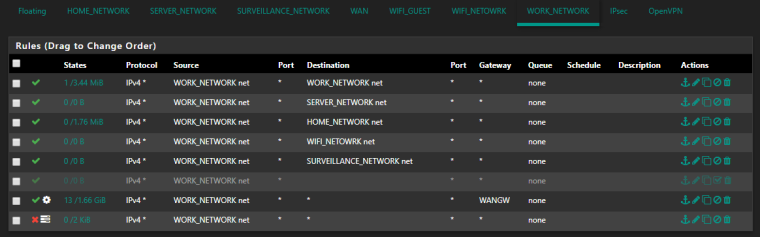
regarding the rules
if i disable rule 2 i was not able to communicate in the same subnet at least in the past ~ 2year ago
rule4: WIFI and LAN are 2 separated network but able to communicate between each other
Rule 3 and Rule 5 are with 0 traffic because they are not used very often and I rebooted my firewall
rule 6 allows internet access from the HOME VLAN -
Not related to the current issue :
regarding the rules
if i disable rule 2 i was not able to communicate in the same subnet at least in the past ~ 2year agoI can even shut down pfSense, and all devices on my "LAN" can still communicate with each other.
This is not some pfSense thing in the present or the past, it's more "this is how IP works".The main issue : I'm running out of suggestions .....
-
Hi,
so I removed all rules from my home network
and I still get the same error, also doing telent to google.com on port 80 I will not work.
-
These are my LAN firewall rules :
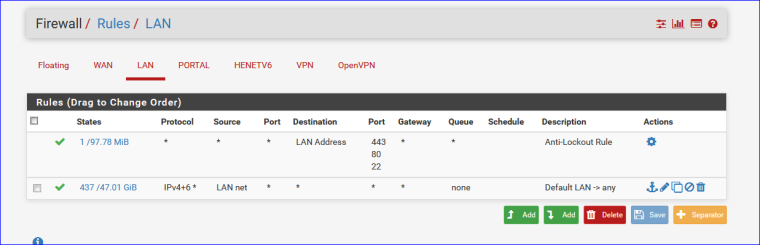
Only minor differences.
The lockout includes "443" (need to prepare for the e dying 80)
Second rule : same as yours, but I added IPv6 because IPv4 is as "Games of Throwns : maybe one more season, and that's it""
So, your issue is not related to the firewall rules.
It's probably some Interface thing or one hop further along : the switch. -
so, I tried connecting directly to the PFSENSE via cable and head the same problem :(, it's not related the switch.
I did a risky update to 2.4.5-DEVELOPMENT and now the problem is gone :), don't know why yet.
and to answer one of your previous question why I specify Gateway for internet access, because if want that role to apply only to internet traffic and not allow access to other VLAN's/Networks
Vuko
-
@vukomir said in Captive portal:
and to answer one of your previous question why I specify Gateway for internet access, because if want that role to apply only to internet traffic and not allow access to other VLAN's/Networks
I understand.
My ... dono what, says that an alias to all other neworks, and negate that alias in the destination, is 'better".