WAN interface only to be manged
-
HI,
Im setting up a PFsense box for a customer, they have requested- Two IP's, so all we need to set up is access to one IP- only to be used with the web interface
How do I go about this without making a LAN network with port forwarding, or useing the shell command to disable the firewall via shell to access itany help would be much appreciated.
~Dafoxx
-
huh? What exactly is this other IP going to be used to access. When you give pfsense only 1 interface and IP it would be a WAN IP.. You can for sure create a VIP (2nd IP) but what would this IP be used to access?
-
The first IP will be just used to manage PF nothing else,
the other IP will be used for servers on its network (the customer is setting that part up), we only want to make the GUI accessible. -
So it will have a LAN... Then yeah create a VIP on the wan and setup 1:1 nat or port forwards to get to stuff behind pfsense.
-
I have the VIP set, Thanks, but how would i forward it when the PFsense IP is the same as the external IP? its a direct nat connection
-
huh?
If the wan IP is say 1.2.3.1/29 you create a vip say 1.2.3.2/29 and use that as the dest IP in the forward or 1:1 nat.. How could the VIP be the same IP as pfsense wan?
Their servers would be on the pfsense lan say 192.168.0/24 - are you saying this lan is public as well and part of the 1.2.3.0/29 or larger wan network?
So you would 1:1 nat or port forward dest 1.2.3.2:80 to say 192.168.0.100:80
-
The PFsenese IP is direct NAT, so the IP of it is the Public IP (is being hosting in a DC)
-
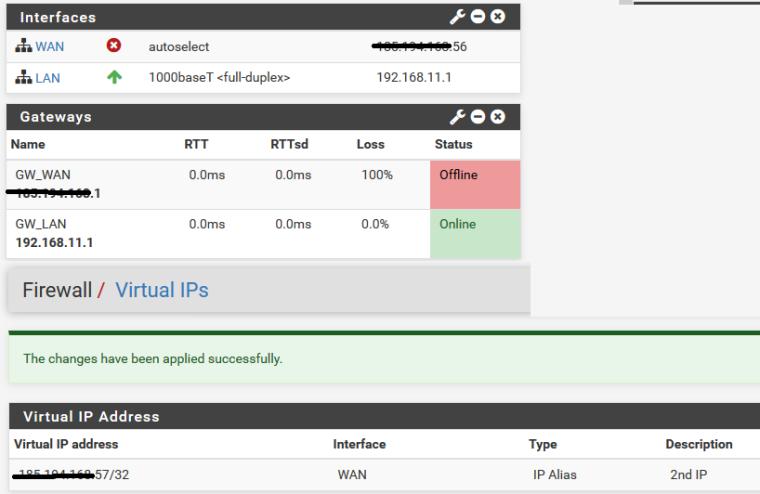
I have say .55* as the PFsense (this is external)
and the Wan of .56* as Virtual IP
Is it not possible to just make it accessible on .55?
Im quite new to this setup sorry if i seem nooby :) -
Lets be clear here to WAN and LAN IPs of pfsense..
A WAN IP would be an IP that has a gateway to get to other networks.. The LAN would be another network behind pfsense router/firewall.. These IPs would not be in the same network...
Are you wanting to use pfsense as transparent firewall - ie a bridge setup?? WHY?
You put pfsense in the DC... You give it a public IP on the WAN in the DC - ie connected to the public... And all the other devices would be on the LAN of pfsense which would be rfc1918 space..
-
It's not my kit :)
But yes that's correct, i dont know what the customer needs for the LAN aside, all my gole here is the make the GUI available, i want to know if its poss/how to make the GUI available for the .56* address.Dont worry about the no gateways and WAN, its not racked yet.
I've set up a LAN rule of 192.168.11.1 for pf with a forward rule, should that be enough for this setup?
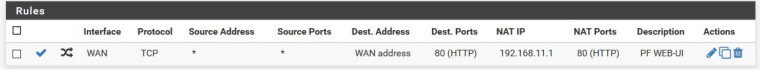
-
I think someone needs to read the pfsense book or something.. If you created a GW on the lan - this now becomes a WAN connection..
You want to make the gui available from where? Out of the box it will be available via the LAN IP.. Lan do not have gateways on them.. It's not a lan if there is a gateway set.. It becomes a transit network to some other router - or a WAN connection.. Then automatic nat shit happens, etc.
If you want to make the web gui available via the WAN interface IP - then just create a firewall rule on the wan tab to allow access..
-
From the Public Internet IP, Not lan.
think its working as expected now -
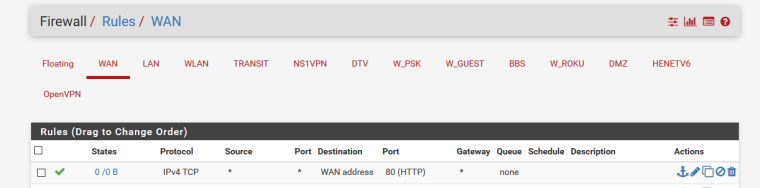
All that is required to allow access from the wan side is a firewall rule on the wan interface.
Keep in mind you need to test this from the WAN side... Hitting the wan IP from the lan is going to be allowed by the default any any rules on the lan..
Post up your wan interface rules.. All you need a dest wan address and port the port you have the gui listen on, etc.
-
Thats in the above Image, and yeah ive just tried it direct and its working correctly
now to see how well the customer does at breaking it!
thanks for your help, I just wasn't sure. ive only ever set up PF on EXSI and HyperV -
You don't need a VIP to allow access to the web gui via the wan IP..
Nor do you need to NAT it...
I would use https vs just 80... And prob change the webgui to listen on a odd ball port.. To be honest I would never open up webgui to the public IP.. If you have to atleast lock it down to specific source IPs.
Its a simple firewall rule on the wan interface.. And there is ZERO differences between running pfsense on VM or hardware.. Pfsense works exactly the same.
-
Ah, I've changed that over thanks, and yeah ill suggest to the customer to use openVPN, then we dont need the other IP for his server.