Configuring pfSense as OpenVPN client
-
Show a screen shot of the actual thing you are entering that results in the error. No insult intended, but it sounds like you are confused.
What is RFC1918/32?
-
@derelict said in Configuring pfSense as OpenVPN client:
Show a screen shot of the actual thing you are entering that results in the error. No insult intended, but it sounds like you are confused.
Well, I am now. Entering where? I mentioned several errors in different cases.
What is RFC1918/32?
I'm a wrong person to ask this question. It should be addressed to @jimp.
RFC1918 / 32is what he enters asSourceon this video (at 35:20), I just blindly copied it. -
OK. /32 has nothing to do with anything. What matters is the contents of your RFC1918 alias there.
It is intended that the RFC1918 alias be a network alias containing:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16The RFC1918 alias would be created in Firewall > Aliases
I didn't watch the whole video. It might have been presumed one would know to do that basic step.
-
I created "RFC1918" alias and specified it as a
SourceinFirewall / NAT / Ooutbound: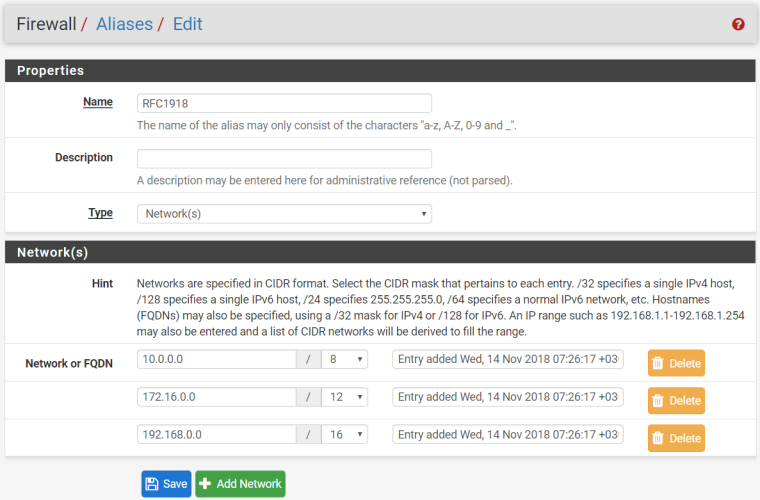
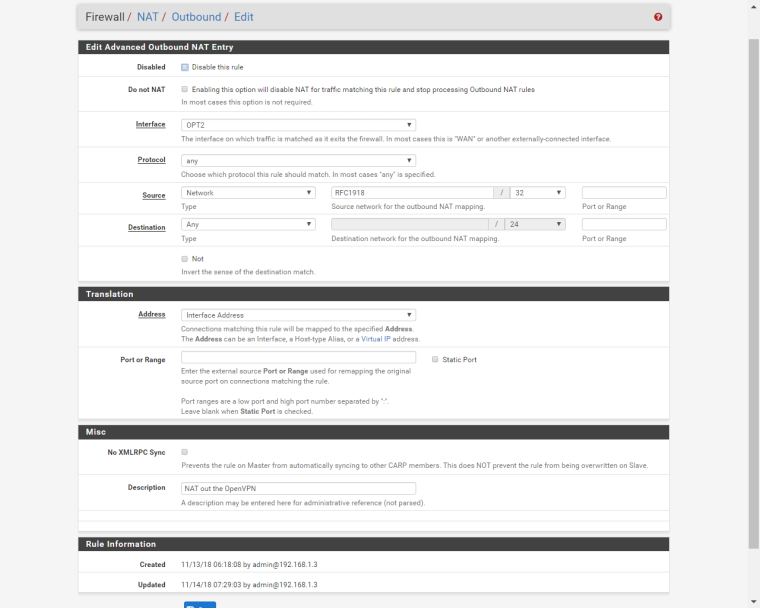
Alas, internet through OpenVPN still doesn't work.
-
This OpenVPN provider does not route all the traffic via VPN, but only traffic to certain websites. So how to make pfSense use routes sent by this OpenVPN server?
-
It doesn't work that way. Or at least I have never seen one that takes that responsibility.
You either accept a default route from them or you policy route the traffic you want over the VPN.
If they are sending you routes and you trust them, uncheck Don't pull routes on the client configuration.
-
@derelict said in Configuring pfSense as OpenVPN client:
It doesn't work that way.
Usually VPN doesn't work that way, but this particular one - does.
uncheck Don't pull routes on the client configuration.
It is unchecked.
I don't know, what else should I try to make it work? Maybe it is simply impossible to make pfSense work with this type of OpenVPN?
-
Are you getting routes from them? Simple enough to look at pfsense route table... Do you see a shitton of routes? To wherever you would want to go out your vpn vs the default one?
Your not sending traffic out a specific gateway are you - if so then your not using the pfsense route table no matter what or how many routes it has in it.
-
@johnpoz said in Configuring pfSense as OpenVPN client:
Are you getting routes from them? Simple enough to look at pfsense route table... Do you see a shitton of routes?
I see many
/sbin/route add -net XXX.XXX.XXX.XXX 192.168.100.1entries in OpenVPN log (where XXX - are various IP addresses).I also see these same IP addresses in
Diagnostics / Routeswith gateway being192.168.100.1(that is IP address assigned by pfSense to OpenVPN inteface).Your not sending traffic out a specific gateway are you - if so then your not using the pfsense route table no matter what or how many routes it has in it.
In
Firewall / Rules / LANI editedDefault allow LAN to any rulesetting gateway to be OPT2 (192.168.100.1), that is OpenVPN interface. At this point I lose internet connection. If you mean something else, then please explain how do I send traffic out a specific gateway? -
Seeing route -add doesn't mean it actually happens.
Look in the actual route table.. If you set openvpn to NOT pull routes they could be set to be put in but not actually put in.. Setting a gateway yes will force traffic out that gateway, and the route table will not even be looked at.
So if your wanting IP x to go out vpn and IP y to go out your wan without the vpn then setting gateway all traffic will go out that interface.
What is your outbound nat setup like - even if the traffic would be allowed to go out the vpn and get where it ultimately needs to go, if you do not nat your local traffic to the vpn interface IP its not going to work.
-
@johnpoz said in Configuring pfSense as OpenVPN client:
Look in the actual route table.
Isn't
Diagnostics / Routesa route table? Like I said, these IP addresses are there. If it is not a route table, then where should I look for it in pfSense?What is your outbound nat setup like - even if the traffic would be allowed to go out the vpn and get where it ultimately needs to go, if you do not nat your local traffic to the vpn interface IP its not going to work.
I didn't change
Firewall / NAT / Ooutboundsetup since I posted screenshot of these settings. Interface is set to be OPT2 (OpenVPN).Could you please describe step by step how should I set up pfSense to work with this OpenVPN? If it is even possible? I guess otherwise I just will have to accept that pfSense simply cannot be configured to work with this OpenVPN provider.
-
What VPN provider is this?
Have you verified that the routes being pushed actually cover the addresses of the sites you think should be routed that way?
Are any of the
route addlogs indicating failure?Are the pushed routes actually going tinto the routing table?
If so, pfSense and OpenVPN are working fine here.