SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui
-
Thanks all! I think at this point our PF Appliances are so messed up that it is pointless at this point to keep beating a dead horse. I am going to take down our secondary PF Appliances, and rebuild them, see if all works as it should, and if it does swing traffic to the the secondary, then rebuild the primary PF appliances. We only have 4 (2 Primary and 2 Secondary), so it shouldn't take to long, and I have backups of the configurations so that should speed up rebuilding.
-
Well if you throw your hands up in the air when we're finally getting closer to finding out what's wrong, it'll never be fixed, if it does turn out to be a bug.
I did find one issue that wouldn't have triggered a restart when toggling some of the checkboxes that need an nginx restart (like the GUI redirect), but it isn't quite what you are hitting.
-
Can't post our config.xml file as it errors on here as "Detected Spam" and won't post it.
-
I can fix that, just need to spam the thumbs up on your posts so Akismet will pass you through.
Also don't need the whole config.xml just the
<webgui></webgui>tags and what's inside. -
Should be good to post now.
-
Also, FYI, clicking Save on system_advanced_admin.php will not trigger a rewrite of the nginx configuration unless something changed that requires it. For example, changing the web server port, protocol, etc. So opening the page and clicking save won't help, but if you switch the port to something else (say, 4433) it would restart with the new settings, then you can change it back. But doing option 11 from the console should always rewrite the nginx config from the contents of config.xml and then restart the web server.
-
I have changed the port to 4433, switch from http to https and save : the webgui is accessible via https on port 4433, from there I have explicitly set the port to 443 and again : get error SSL_ERROR_NO_CYPHER_OVERLAP.
I am staying on 4433 for now...
-
@xenicle said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
I have changed the port to 4433, switch from http to https and save : the webgui is accessible via https on port 4433, from there I have explicitly set the port to 443 and again : get error SSL_ERROR_NO_CYPHER_OVERLAP.
I am staying on 4433 for now...
You must have port 443 taken over by some other daemon or NAT that isn't the GUI.
-
I might have some more insight regarding the issue.
I was playing around in pfsense v2.4.4 and I've somehow ran into the same/similar issue again

When I access
192.168.1.1(pfsense box) over HTTPS I get theSSL_ERROR_NO_CYPHER_OVERLAPerror, however when I got topfsense.localdomain(HTTPS or HTTP - which redirects to HTTPS) it works fine.
Maybe this means the SSL certificate isn't bound to the IP but the domain name only?Does this mean pfsense was setup incorrectly by the user (e.g. me)? But that doesn't explain why it initially worked

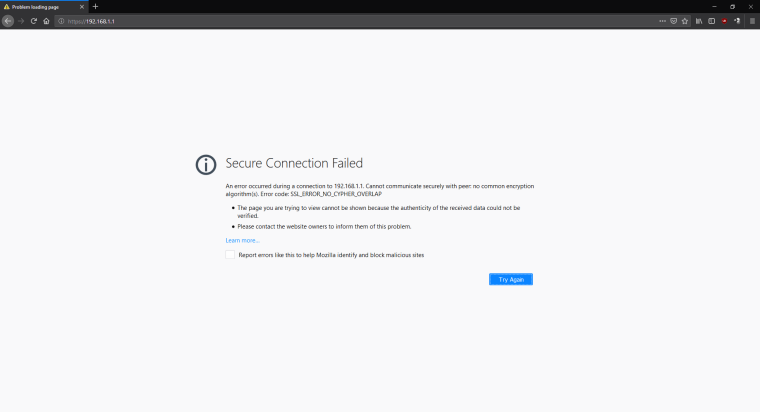
-
Are you certain your workstation is hitting 192.168.1.1 when going to pfsense.localdomain? Try to open a command prompt and ping pfsense.localdomain, see what it's actually hitting.
-
I ran into similar trouble recently. I responded to an old post on the forum as to a solution.
Have you tried this solution? https://forum.netgate.com/topic/123072/ntopng-https-redirect-protocol-error-after-configuration-in-version-2-4-1/2
EDIT: Certificate attributes > Alternative Names could be the issue as to why you can connect via FQDN and not the IP.
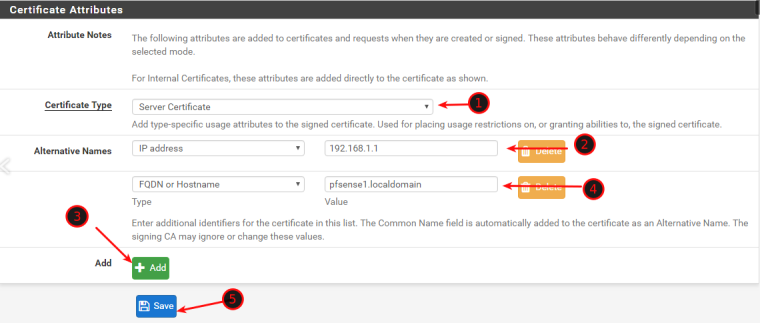
-
@jimp pfsense.localdomain is definitely resolving to 192.168.1.1 (in my case, as per above images)
-
@crbon said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
@jimp pfsense.localdomain is definitely resolving to 192.168.1.1 (in my case, as per above images)
The images don't prove that, however. Try a ping and see what happens. Maybe your computer is resolving that hostname to the WAN IP address, for example, or another local interface. It could explain the discrepancy.
A mismatched SAN/CN wouldn't have anything to do with the cipher. It would still work, but complain that the certificate didn't match the host. It would not affect encryption.
-
@jimp Sorry I wasn't clear. I just did ping pfsense.localdomain and it does resolve to the 192.168.1.1 address.
Windows 10 has crapped itself, I cannot do windows search to get the snipping tool to show it
-
@crbon said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
@jimp Sorry I wasn't clear. I just did ping pfsense.localdomain and it does resolve to the 192.168.1.1 address.
Windows 10 has crapped itself, I cannot do windows search to get the snipping tool to show it
The path for Snipping tool is: %windir%\system32\SnippingTool.exe
-
@jgravert Thanks for the tip!
-
@jgravert @jimp I think if we blend both of your comment we are coming close to the core issue.
When accessing 192.168.1.1 from my phone I get error NET::ERR_CERT_AUTHORITY_INVALID (phone does not have Bitdefender AV), but I can press advanced and then Proceed to 192.168.1.1 (unsafe).
When the access the same IP 192.168.1.1 from my PC (running Bitdefender AV Free Edition) I get the SSL_ERROR_NO_CYPHER_OVERLAP error message instead,and there is no way to bypass it.
By going into the Settings -> Protection, you are able to switch off 'Protection Shield', after doing so the SSL certificate issue will disappear.So that means the AV (Bitdefender in this case) is messing with the connection/certificate as a defense mechanism?
(I have ntopng installed as per @jgravert 's reference to the other thread)
-
@crbon said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
When the access the same IP 192.168.1.1 from my PC (running Bitdefender AV) I get the SSL_ERROR_NO_CYPHER_OVERLAP error message instead, and there is no way to bypass it.
So that means the AV (Bitdefender in this case) is messing with the connection/certificate as a defense mechanism?
(I have ntopng installed as per @jgravert 's reference to the other thread)
Defiantly Bitdefender Scan SSL (Encrypted web scan) is active. You may need to flushdns, cache, then restart your browser after turning off Scan SSL in Bitdefender. I had to in order to get mine working again.
Alternatively if you get new CA and Certificates then install them on your PC it shouldn't matter if Scan SSL is active.
If that doesn't work you may need to completely remove Bitdefender from the PC then reinstall it.