Vlans No Switch?
-
@johnpoz said in Vlans No Switch?:
Yeah their AP are the same lack of understanding design..
Same with their support staff. When I contacted them, they couldn't understand that VLANs should act as logically separate LANs, with no traffic passing between them. When I was able to reach 2nd level support, they accepted there was a problem, but no fix was forthcoming.
-
@johnpoz Using the Dgs-1100-08 is there a way to make vlans work with pfsense I spent all day messing with stuff I had it easier using ddwrt
-
Of course there is, but you have to understand what you are doing with VLANs in the first place.
In general:
If you assign a pfSense interface (Interfaces > Assignments) to:
igb0 - it will be on the untagged, native VLAN on the switchport it is connected to.
If you create VLAN 10 on igb0 and assign an interface to:
VLAN 10 on igb0 (igb0.10) it will be excpecting the switchport it is connected to to be tagging VLAN 10.
-
It sounds like I'm really close the way I had it I was trying to tag 4 vlans on one interface had DHCP serverss enabled I bet you it's the 802.1q tagging on the switch I'm doing wrong and it's probably cause I was treating it like ddwrt I thought it would ignore the Interfaces if I dropped them out of vlan 1 I thank you every little discussion seems to help I literally am still working on this since last night so yeah I'm really not as smart as i think
-
Why don't you post up a picture of what what you did.. I could fire up the one I have and show you the setup for exactly what you want it but it is drop dead simple
And you can use vlan one as your native - this isn't a enterprise network with policy and procedure about vlan 1 use, etc..
So your lan interface in pfsense has
192.168.1.0/24 on it
Lets create 2 other vlans
vlan 10, 192.168.10.0/24
vlan 20, 192.168.20.0/24These vlan are running on your lan interface..
So the port connected to lan of pfsense would be
vlan 1 (untagged), vlan 10 and 20 tagged. the pvid of this port would be vlan 1Now on your other ports you set them for either vlan 10 or 20 UNTAGGED... And pvid of vlan they are in 10 or 20..
For a port running to your AP it would be just like the port connected to pfsense lan
vlan 1 (untagged), vlan 10 and 20 tagged. the pvid of this port would be vlan 1edit: Here I pulled it off the shelf and connected it.. While I was at it updated its firmware ;)
ver 1.00.B031, current beta just came out this month..Anyhoo - as stated above for example..
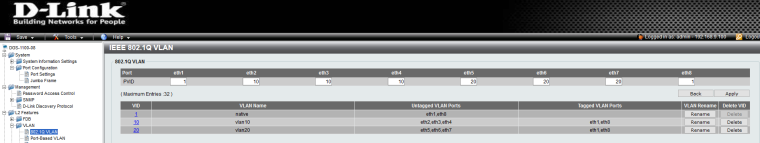
So say pfsense would be connected to port 1, and your AP would be connected to port 8..
While 2,3,4 would be devices in vlan 10, 5,6,7 would be devices in vlan 20 -
i was tagging ports on vlan 1 and tagging the ones you had untagged and i kept getting confused cause everything warned about using vlan1 thank you so much i am going to test it tonight and it took alot for me to follow this simple thing i got severe memory problems and attention
-
You can for sure change if you want the management vlan or default vlan of your switch.. I have mine set to vlan 9 for example... Then again I do this for living for like 30 years ;)
Vlan 1 is just the default - it means nothing in the big picture.. Any enterprise level switch will allow you to change the default vlan.. Your 30$ smart switch maybe not - but its not a bad thing using it.. Its just the default untagged vlan.. Be it 1, be it 10 or whatever id you assign.. its nothing more than the default vlan of the switch that ports are in that are not assigned to a different vlan..
In a soho sort of setup for sure you can just use vlan 1 as your default untagged network on your switches... Only in enterprise and controlled networks do they have policies that say you have to change the default vlan.. It doesn't really mean anything really from a security point of view on the big picture.. Its just BS policy ;)
It makes more sense to make sure that ports that are not used are actually disabled, etc. etc..
-
Okay with your switch configuration on the LAN interface that all worked for some reason it wouldnt on my opt1 interface RE1 but I assume i may have misconfigured it since i was so tired when attempting to do it...Next thing is Do i need to make rules to block cross traffic ? or does pfsense or the switch allready do that? My network has no Hardened rules right now which isnt good so I need to start reading all that and i watched a video where they setup vlans and you had to block all other vlan networks and allow dns and i was thinking that was wrong i just assumed that pfsense or the switch would automatically set the basic vlan to isolate and then you would be allowed to unsecure it if you wanted but im not an expert. THANK YOU You Saved me Months Of confusion. i just have default to any rules but thats very temporary
-
Traffic entering the firewall passes according to the rules on that interface.
No traffic is passed unless you pass it.
If you want to pass traffic you need to pass it.
If you want to block exceptions to that you need to block it.
-
@derelict you are the man, simple and clear description of approach to firewalling world.

Not needed "months" of learning to understand basic 's of how to pfSense handle firewalling rules.
Regards. -
@babiz No that is simple I just didnt understand How to setup my switch properly and while they do have 24 7 tech support for first 30 days they make me more confused than just attempting to do I know its simple now but their are somethings my brain just doesnt comprehend and thank you all for your Help I learned something from everyone
-
@telescopedepth I appreciate people's goodwill.

I understand you, also networking's jobs. you can learn enough, trought forum and community, as I do...
If you really want, nothing is impossible!
Meanwhile I'll reading some nice book like this
Some page for a day, it's easy to follow and full of good pratice, for me.
Regards.(Indeed pfSense book it is) Finally I need to thank so much pfsense team for this pretty nice gift, I dicovered few days ago, pfsense book for everyone is a must to have. Cool!