How do I allow VNC from one subnet to another?
-
OMG dude...
Sniff on pfsense egetnett interface for 5900 tcp... Try and get to your 192.168.10 address from your 192.168.0 address.
Do you see traffic?? What is the source IP?
Now sniff on the airplay interface for tcp 5900 and try and get there again... Do you see pfsense send on the traffic???
"hey, 192.168.1.4 on the Egetnett wants to talk to somebody on the .10 net, so I'll route it".
Pfsense KNOWS how to route to any network connected to it... You do not have to create any routes... You have to allow it via a firewall rule on egetnett interface.
You say that 192.168.0 can get to the internet... So how is the default gateway of this server your 192.168.0 behind NOT pfsense IP address in the 192.168.1 network?? If its NOT then NO its never going to get to the 10.. Does this server your 192.168.0 have some other default gateway.. Does it have some other connection to the internet that you say the 192.168.0 can get to?
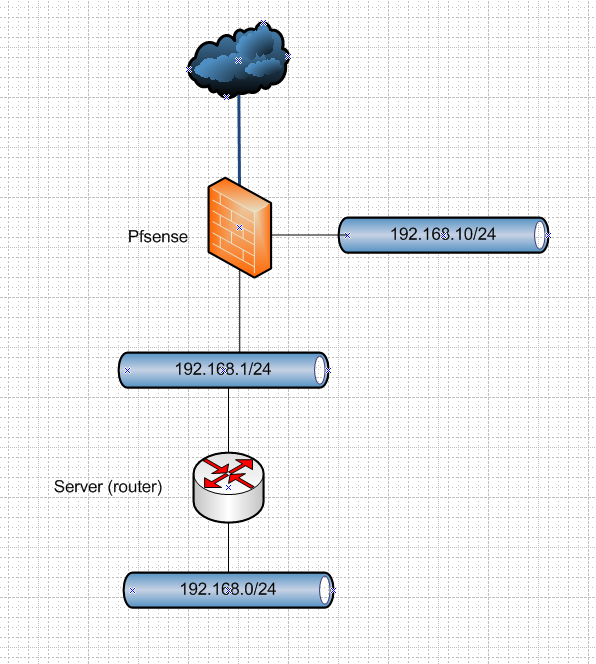
This is your network???
-
I need to set up something that can sniff on that network. I'll try to do that tomorrow and see if I can find out something.
The default gateway to Internet in my internal network is the server , 192.168.0.1, and the default gateway for Window's Routing and remote access (and NAT) on the server is 192.168.1.1, which is the pfSense box. And the 0 segment has no other way to the internet than Server --> pfSense --> ISP Internet router
-
Sniff on pfsense egetnett when you try and got vnc on the 192.168.10 address... If pfsense does not SEE this then no you can never get there.. Maybe your server is blocking it from going out?
This is really 30 seconds to figure out with simple packet capture on pfsense to validate traffic gets there and is sent on..
-
Sorry, I answered before you put in that network pic. Yeah, that's basically my network, at least the part of it that I am trying to get to work now.
I hadn't seen the package capture function on pfSense before, but I tried it now. I did packet capture on the Egetnett and nothing was shown that tried to go from 0.50 to the 10.x segment. Then I tried a VM that's connected directly to the 1.x segment (physically on the server, but totally separate from the 0.x network), and there I could see the packages going back and forth.
So it seems obvious that the server has no idea where to send stuff to 10.x segment, I need to figure out how to tell it that.
-
@mastiff said in How do I allow VNC from one subnet to another?:
from 0.50 to the 10.x segment.
OMG dude... No shit you would not see traffic from 0.x your server is NATTING the traffic to 192.168.1.4 - how else could stuff on the 0 get to the internet... Pfsense has NO clue to the 192.168.0 network..
Your server has only its default gateway right 192.168.1.1 (pfsense) so it sends ALL traffic there that is not local.. Do you maybe have this 192.168.0 with a /16 mask or something??
-
No, it's a 24 mask. But I meant that I don't see any VNC traffic AT ALL when when trying to get from 0.50 to the 10.x segment. So there's no VNC traffic coming out of 1.4 either.
-
Well then you need to figure that out on your downstream server - pfsense can not let you into the 10 network on port 5900 if it never gets there.
Seems pretty impossible if your default gateway is pfsense, unless your server is blocking traffic to rfc1918 space.. Can your 192.168.0.50 box ping say 192.168.1.1?
You would have to allow that on your egenett rules.. I don't recall what they were now..
From the rules you listed - sorry but its not possible for those 192.168.0 boxes to be getting internet through pfsense.. Since rules on that interface only allow access to the egetnet address.. So unless you were using proxy?? On pfsense?
Unless you have rules below what you posted for 5900 dest..
-
Yeah, I know. It has to be lost somewhere on the server, I guess that's because it doesn't know where to send requests to the 10.x subnet. I tried to set up static routes to do that, but it didn't do anything.
And yes, I can ping both the pfSense box and the VM that's running on the Egetnett. So the server should not block 1918. I am not using proxy. And yes, I have other rules, I just cut out the rule for the 5900. Default LAN to any rule should cover that, right? Also now for testing I have a rule on Egetnett allowing anything to Airplay net.
-
FOUND IT! It was the server, and I saw it when I used route print. An old, static route from an experiment several weeks ago was overriding the new static route I had set up. I deleted the old route, and now it works. Thanks for you help!

Edit: The weird thing is that the old route was taking presedence over the new route, which I had with metric 1. I have no idea why.
-
9 days ago in #2 I told you about Asymmetric/check your Routing.

-Rico
-
Rico, turned out that it wasn't that at all. The routing I thought was wrong was only for internal use on the server, I didn't check the RAS routing table, which was correct. So something strange happened in the pc. But now I'm back with the problem, only different. After fiddling with the rules for both airplay and egetnett I see what seems to be happening. I see the VNC packages on the Airplay net, but they are blocked. Because I get this:
Dec 9 20:43:58 AIRPLAY Default deny rule IPv4 (1000000103) 192.168.10.101:5900 192.168.0.50:50613 TCP:SANow that confuses the heck out of me, because I keep getting that even with this rule on the very top of Airplay:

Shouldn't that rule let everything through? Also I can't understand why I'm seeing the internal IP of the client, and not the 192.168.1.4 IP of the server, but perhaps that's the way it is so that the server can send it on to the correct client?
-
SA screams of Asymmetrical traffic!!!
Shouldn't that rule let everything through?
NOT when it is not SYN... You do NOT need rules on airplay to allow return traffic that is started from egetnett... The state will allow the return traffic...
Like I said draw up your network.. If your seeing SA.. Means you are asymmetrical.. Ie send the Syn,ACK back to firewall where the SYN came from some other path that the firewall did not SEE.
-
I will try. What is the software/website you're using to make your drawings? It seems quick and easy compared to the stuff I've tried.
-
I use visio.. But there are plenty of places to do online drawing..
Here is ascii art one that is pretty slick
https://textik.com/#
there is giffy
https://www.gliffy.com/examples/network-diagramsHere is the thing if your multihoming shit - then you going to have issues with asymmetrical traffic unless you KNOW what your doing.. Its real simple to not have asymmetrical traffic... ONLY put stuff on 1 network, and any upstream/downstream routers would be connected with transit networks
-
Thanks for the drawing tips! But it seems like I don't need them this time.
 I really don't get this. The 10.4 NIC is still nowhere in the RRAS routing table, but I can see that it is assymetrical traffic. So for now I have given up on using the clients for VNC and instead VNC into the server and then from that to the 10.x devices. At least that way I will keep the bulletproff failsafe in the totally static 10.x network for my automation. I am going to find out how to avoid this in a Windows Server forum. Thanks for the patience, I'll put on my flame retardant raincoat and you now get to say "I told you so".
I really don't get this. The 10.4 NIC is still nowhere in the RRAS routing table, but I can see that it is assymetrical traffic. So for now I have given up on using the clients for VNC and instead VNC into the server and then from that to the 10.x devices. At least that way I will keep the bulletproff failsafe in the totally static 10.x network for my automation. I am going to find out how to avoid this in a Windows Server forum. Thanks for the patience, I'll put on my flame retardant raincoat and you now get to say "I told you so". -
If your 192.168.1 is only transit, and your server has connection to it and its .0 network behind it.. And this .0 network is not connected to anything else then its not possible for you to have asymmetrical traffic.
How would traffic get to the 10 devices other then via pfsense connection?
Do you have multiple layer 3 over the same layer 2 network? Ie do you have devices with different IPs plugged into the same dumb switch? And thinking they are on different networks?
-
That's the confusing thing. The only assymetric way I should be able to get from the clients on the 0 network would be through the going like this:
Client...................RRAS server NIC...........Server NIC excluded from RAS
192.168.0.50 -- -> 192.168.0.1 --------------> 192.168.10.4 -------------------> 192.168.10.xAnd that's what I don't understand. I think I'll have to get down to the technical room and go over the connections. I recently moved the server from one rack to another (I needed more space for the whole house audio amps, they got HOT because they were to close together, so I split the system over two racks) and it is possible that there is a wrongly plugged cable connecting the 1.x and the 10.x network, or perhaps even the 0.x and the 10.x network. That's the only think I can imagine. That would be a lot of hours wasted on a network cable...
-
Your server is multihomed - it has a connection in the 10.. As I stated doing such a thing leads to problems - especially if you do not fully understand how the protocol works and will not be coming to a device on the 10 from another direction.
You do understand that if its directly connected then there is a ROUTE!!!!
You hit the server and tell the server hey, send this to 192.168.10.X
Server - sure directly connected to that network, and hey I arp for X and its here on this network... Let me throw that SYN out to it for you..
10.X sees that SYN from 192.168.0.50... Say hey yeah I listen on that 5900 port, let me move that traffic up the stack for you hey... Hey it says yeah lets talk,, he sent me this syn,ack he wants me to send back to you.. Oh lets see 192.168.0.50... hmmm I don't know how to get there.. Let me send that to my friendly default gateway pfsense at 192.168.10.1 - he will know how to get it to the 0 network..
Pfsense - says sees the SA... Sorry bud NO state.. Dropped!!!
-
I do know that. And I too think that's what happening. The thing is that what's a route locally on the server and what's a route on Routing and Remote Access, dealt out to the clients of the server, at least in theory should be two different things. That's why there are totally different route tables for RRAS and Route print on a server. So the clients shouldn't even be able to go through the 10.4 NIC as long as that's blocked in RRAS.
But I will check the cabling, and I'll see if I can find out if RRAS routes and local server routes are to be totally separate, and that it may be a configuration mistake on my server. I have put in a question about that on a server forum. This is something new for me, even after almost 20 years of running "indows server (from 2000 Advanced Server) at my home and my cabin.
-
Dude we stopped using RRAS like 20 some years ago... I have supported "server" since NT 3.51 days... Got my MCSE back on NT 4 and 2k..
There are much easier ways to route traffic then using windows that is for damn sure.. For starters your using one - pfsense..
Not sure what you think putting device behind windows is getting you other then more complexity?