Modem GUI/SSH access stops when pfsence has active PPPOE connection.
-
Hi all of You lovely people.
First of all I wish merry Xmas to all.
Now to the chase.. Hope gurus on here will be able to help.
I have seen loads of topics about DSL modem access behind pfsense but can't find solution for the problem I am having.
As per title.. I have no access to my DSL modem when pfsence makes PPPOE connection and gets public IP. Modem is in bridge mode and pfsence handles PPPOE connection. Configuration is made according to this guide: https://www.netgate.com/docs/pfsense/interfaces/accessing-modem-from-inside-firewall.html
I have tried to make MODEMACCESS interface on another LAN port on my pfsense nic card (it has 4) and connect it to LAN port 2 on my modem (HG612 has 2). Thought modem access could conflict with PPPOE on same port somehow but no. Same result. Everything works until I enable PPPOE connection.
Any ideas?
Thanks in advance. -
Hi,
This :
@girtsj said in Modem GUI/SSH access stops when pfsence has active PPPOE connection.:about DSL modem access behind pfsense but can't find solution for the problem I am having.
is a problem.
LAN interfaces are 'behind' pfSEnse, WAN is in front, and that's where your modem lives.I just checked https://www.netgate.com/docs/pfsense/interfaces/accessing-modem-from-inside-firewall.html and it works for me.
-
@gertjan I did follow that guide. See my post. Interface and NAT rule is configured correctly as far as my understanding goes. Or else I would not be able to reach the modem at all. I can access modem only when PPPOE connection is down or WAN interface (which is configured as PPPOE) is disabled.
-
@girtsj said in Modem GUI/SSH access stops when pfsence has active PPPOE connection.:
I can access modem only when PPPOE connection is down or WAN interface (which is configured as PPPOE) is disabled
This proofs you did not set up things as they should.
How would it be possible to access the modem if your WAN interface is disabled ??It's time (as always) to show rules, NAT, interfaces, network layout, etc.
-
@gertjan WAN(PPPOE) is a virtual interface and this is why another interface to same physical NIC port (em0) can be added for modem access. Wan(PPPOE) is not necessary to access modem.
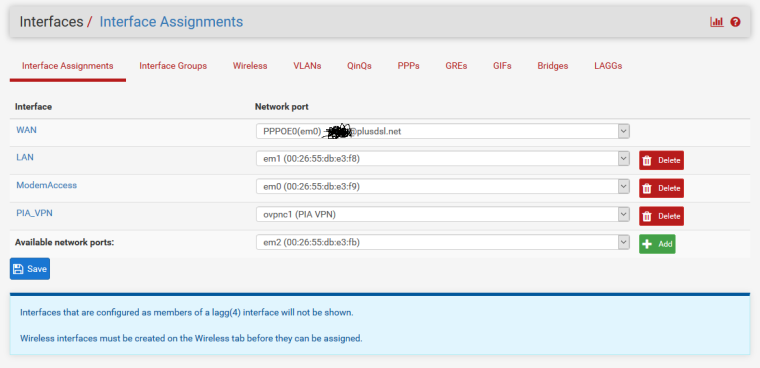
WAN interface:
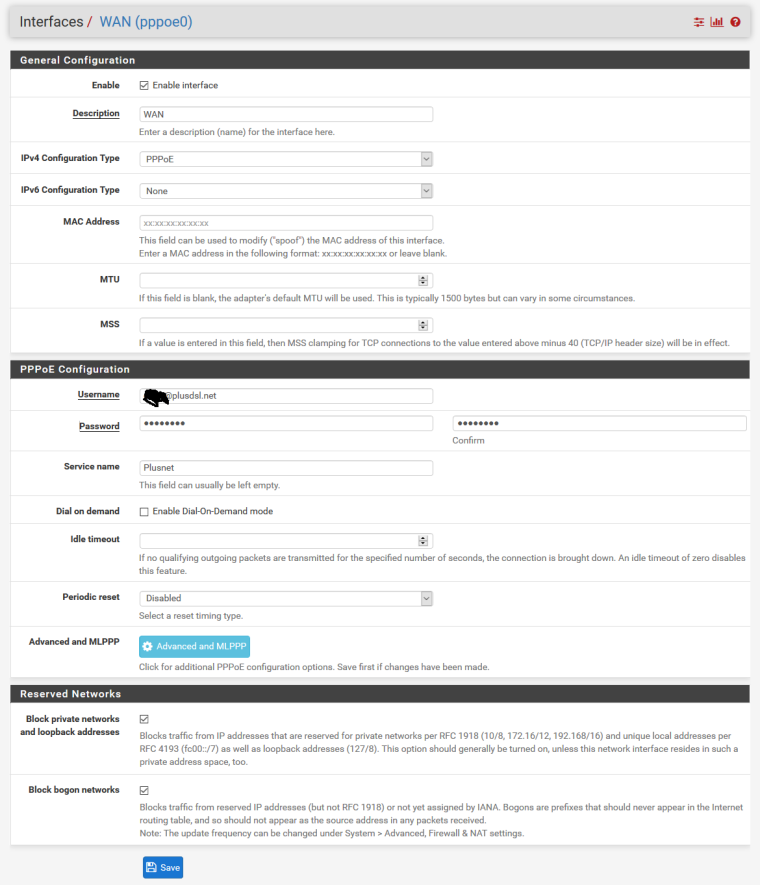
ModemAccess interface:
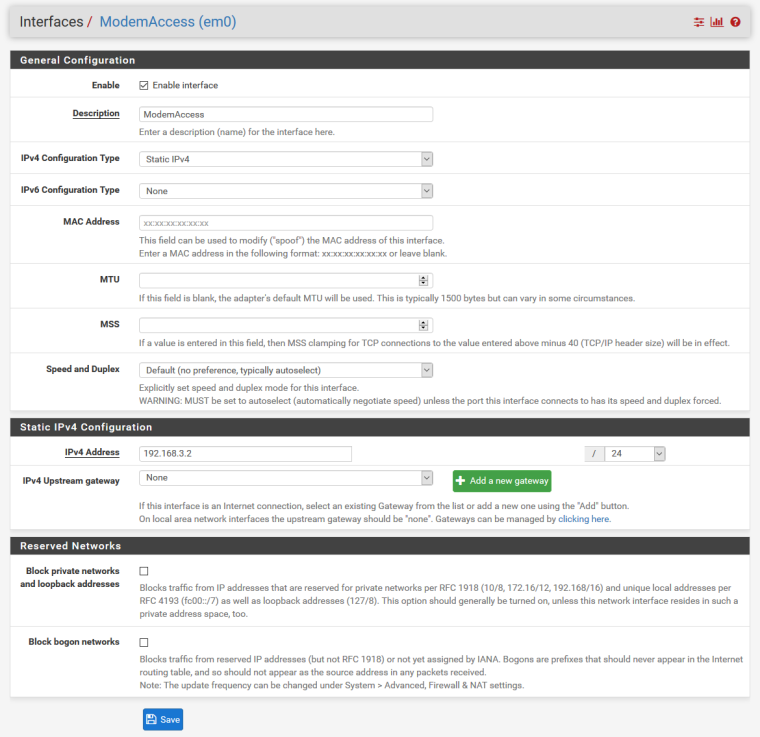
NAT rules:
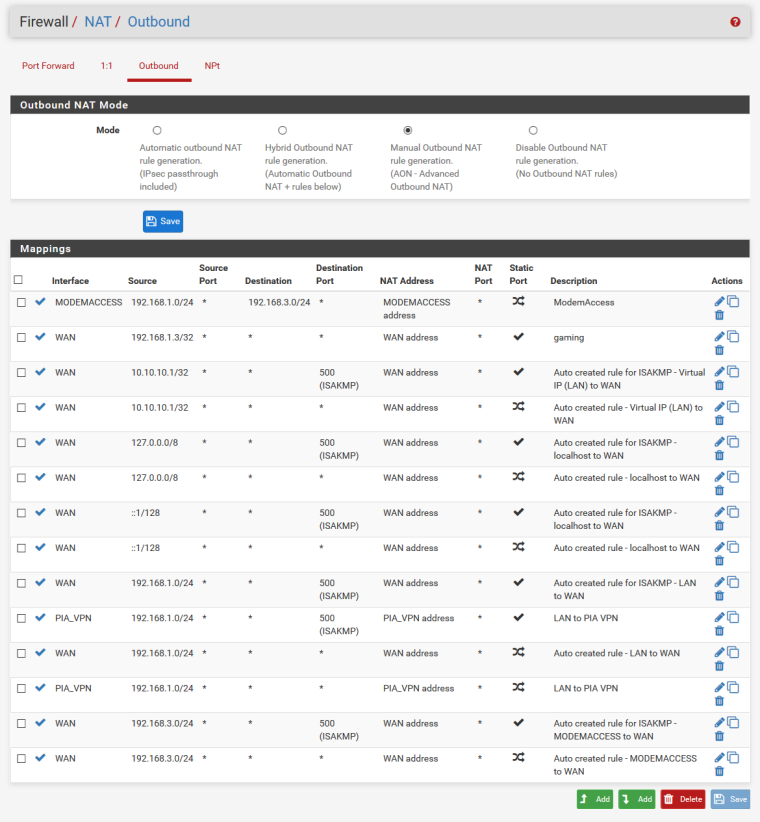
MODEMACCESS rule:
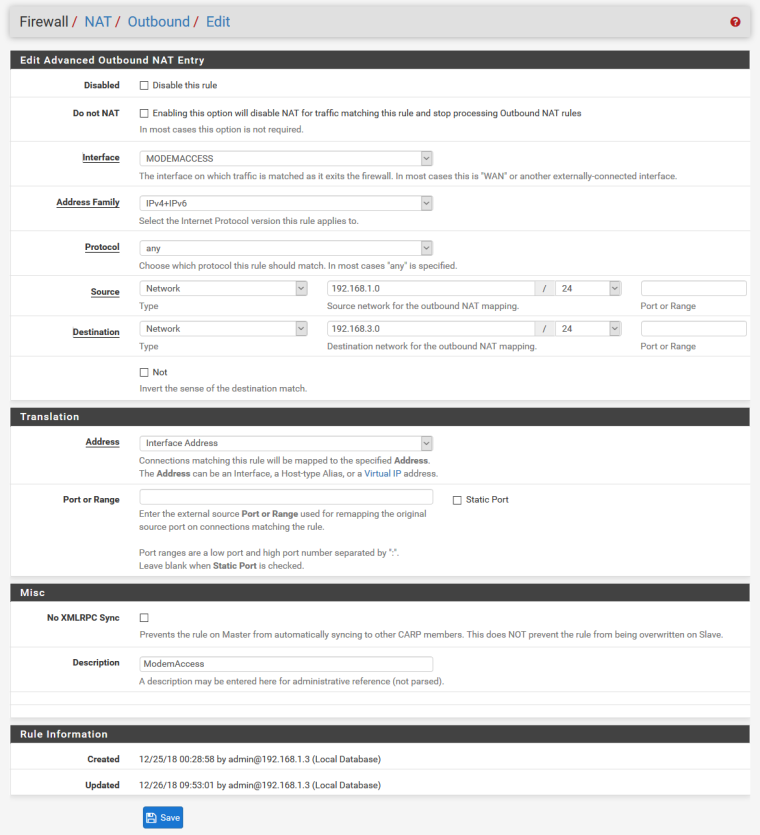
In this configuration modem is not accessible. As soon as I disable WAN interface or change PPPOE login details so connection can't be established I can access my modem.
My setup is quite simple. modem->pfsense->unmanaged swithch (LAN).
Any ideas? -
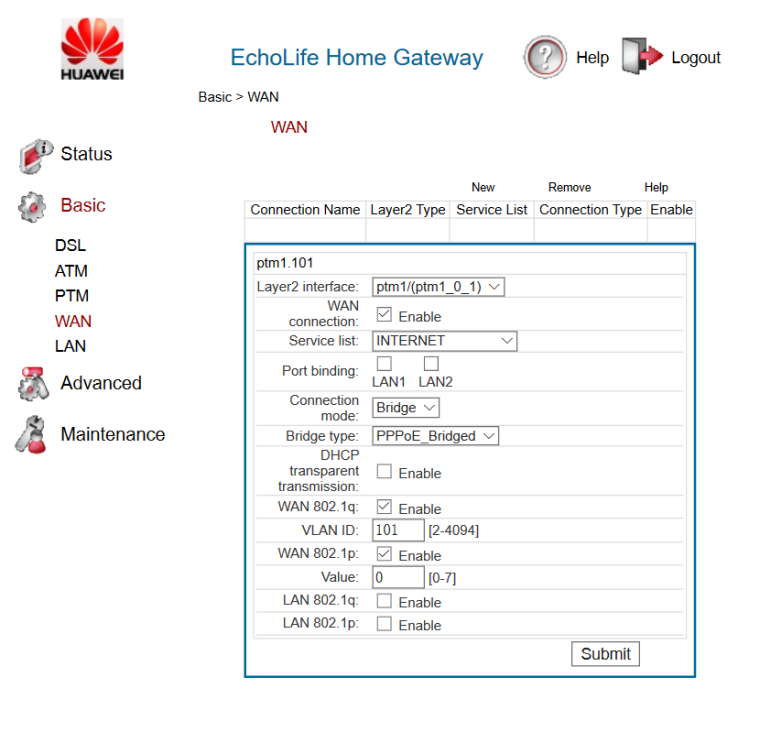
Here are settings on my modem:
WAN
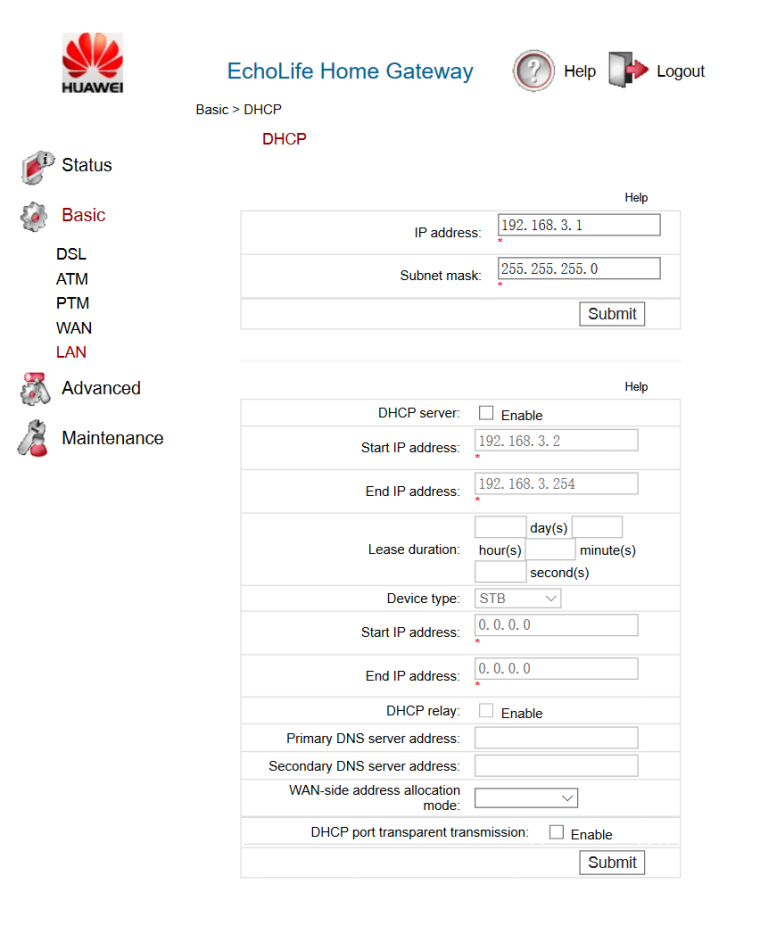
LAN
-
Its an echolife issue.
On your wan setting under service list , just bind it to lan1 not to both (which is the case if you have them both unchecked.
Have the other lan also plugged in on same lan (or vlan) like lan1 lan2 and pf wan port
http://prntscr.com/m0cxuf -
@netblues
I guess You are talking about 2 cable configuration here. If both ticks are unchecked it lets You use only one cable and get internet as well as GUI access. See this:
https://forum.kitz.co.uk/index.php?topic=17671.0
This worked perfectly on tomato router but refuses to work on pfsense when PPPOE link is made.
Putting a tick in to LAN1 binding lets only PPPOE traffic go through. GUI will not work on LAN1. It will be accessible on LAN2 only. Which is not an issue if it would work. I have done what you suggested. Tick on LAN1 and put 2nd cable to my pfsense with another interface created on that port. Same thing. I can access GUI until PPPOE connection is made. -
@girtsj 2nd cable on the same physical pfsense lan via a simple switch?
I have this working with a linux pppoe (centos) and works.I doubt pf is any different accesing hg612.
-
@netblues must be something in settings.. If I plug in 2nd cable to LAN switch there is no access. But then if I manually change IP on my PC adapter properties to 192.168.3.2 (modem is 192.168.3.1) I can access the modem GUI. But then I have no access to internet and pfsense as it bypasses its lan (192.168.1.0).. any ideas? Maybe virtual IP?
-
@girtsj
Hey
Show the rules on the Lan interface
I have a hunch you're redirecting traffic through the openvpn tunnel . -
@konstanti here:
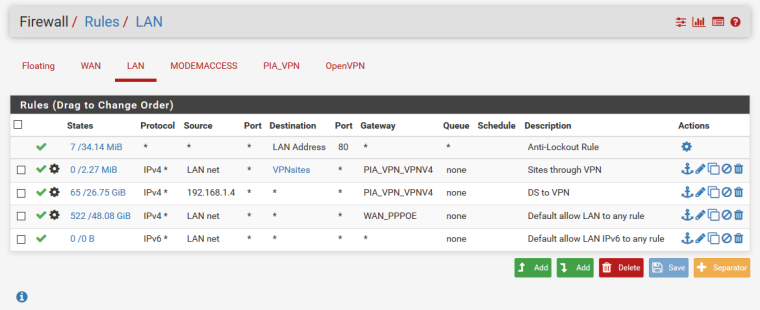
Rule 1 from top forwards certain sites to VPN as some are blocked in UK.
Rule 2 forwards my synology nas to VPN.
Rule 3 forwards the rest of LAN to wan gateway so it dont go to VPN. -
@girtsj
1 NAT not needed
2 create a rule after the first
source 192.168.1.0 / 24 destination 192.168.3.0 / 24 and default gateway
For example
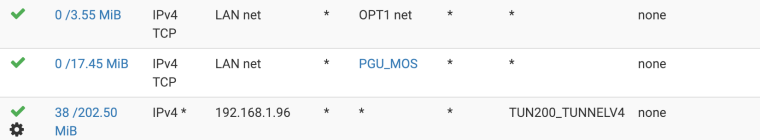
-
@konstanti like this?
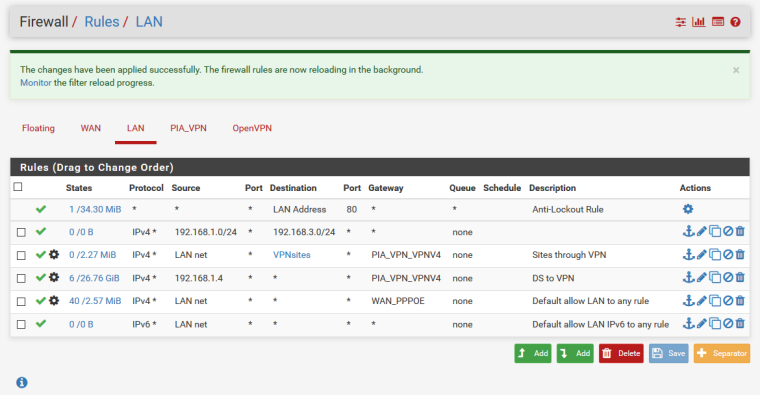
Still no dice.. -
@girtsj
I don't see the ModemAccess interface in the picture -
@konstanti sorry disabled it
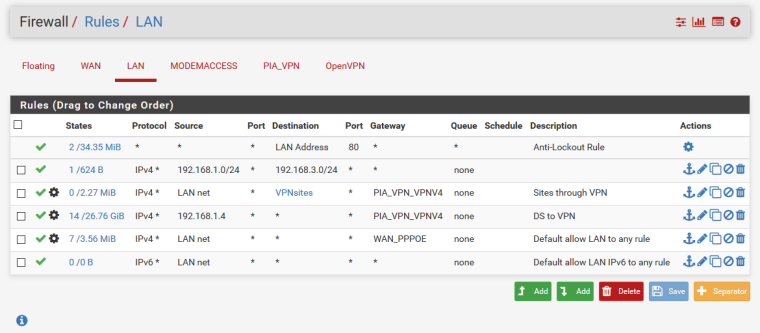
still a no-go -
@girtsj said in Modem GUI/SSH access stops when pfsence has active PPPOE connection.:
still a no-go
Diagnostics/ Packet Capture
Interface ModemAccess
Show me the result of the packet capture.
And Huawei IP route table -
I'm sorry, I think NAT needs
Another option is to change the IP address of the modem, for example, 192.168.1.55/32 with default gateway 192.168.1.1 (don't know which gateway address). And plug the cable from the modem into the network switch . And test the connection -
@konstanti thought that without nat rule it won't work.
Will give this a go. -
I really don't get it.. Huawei PPPOE connection is binded to LAN1 port on modem. GUI access is through LAN2. MODEMACCESS interface on pfsense is on different port than WAN. It all works:
22:12:45.552442 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.552885 IP 192.168.3.1.80 > 192.168.3.2.55771: tcp 0
22:12:45.553547 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.554795 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 610
22:12:45.555131 IP 192.168.3.1.80 > 192.168.3.2.55771: tcp 0
22:12:45.557256 IP 192.168.3.1.80 > 192.168.3.2.55771: tcp 112
22:12:45.557630 IP 192.168.3.1.80 > 192.168.3.2.55771: tcp 434
22:12:45.557918 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.558918 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.559042 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.560042 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.560417 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.560541 IP 192.168.3.2.55771 > 192.168.3.1.80: tcp 0
22:12:45.560628 IP 192.168.3.1.80 > 192.168.3.2.55771: tcp 0
22:12:45.867621 IP 192.168.3.2.31225 > 192.168.3.1.80: tcp 0
22:12:45.867862 IP 192.168.3.2.7015 > 192.168.3.1.80: tcp 0
22:12:45.868066 IP 192.168.3.1.80 > 192.168.3.2.31225: tcp 0
22:12:45.868191 IP 192.168.3.1.80 > 192.168.3.2.7015: tcp 0
22:12:45.868360 IP 192.168.3.2.31296 > 192.168.3.1.80: tcp 0
22:12:45.868690 IP 192.168.3.1.80 > 192.168.3.2.31296: tcp 0
22:12:45.868861 IP 192.168.3.2.34624 > 192.168.3.1.80: tcp 0Until i log into PPPOE. It all goes dead..