Problem with vpn on OpenVPN
-
Hi @JKnott. IPsec is to close the connection with our firewall, openvpn because the other side isn't managed by us. Can i make this kind of connection possible or only i can choose one of this kinds of VPN?
-
You should be able to do it, as a VPN is simply another IP path. We'll need a bit more info about your configuration though.
-
@garona Hey
Do you have access to both routers with IPSEC tunnel ?
If so, you can try to solve your problem
What is the address of the network behind the OPENVPN tunnel ?
what is the address of the network that is behind the IPSEC tunnel ?The solution is to create an additional phase 2 ipsec tunnel specifying the openvpn networks and the network behind the ipsec tunnel as the source and destination. And on the reverse side of the tunnel settings should be mirrored
There are other solutions to this problem . But for this we need to see a diagram of your network and you have to understand that you can change in this scheme
Can you show the IPSec tunnel phase 2 settings ?
-
Hi @Konstanti Yes, i have access to both routers.
100.100.100.0/24 is the network behind openvpn tunnel.
172.72.70.0/24 is the network behind ipsec.
I will create the other phase 2, but i want to know what is the other possibilities to solve this problem.
Actually we have the ipsec vpn between a pfsense and a cisco router, and this tunnel is acessible, i can ping ips of the network on pfsense, i can't only reach on openvpn tunnel, i tried use command push "route" on openvpn but i don't have success.
Is a route problem, right? -
@garona said in Problem with vpn on OpenVPN:
Ipsec in its pure form does not know how to route traffic.
Thus, it can only transfer traffic between networks from phase 2.
Nothing else.
the command "push route" here is absolutely useless -
@konstanti ok, thanks for fast reply, the only solution is the phase 2 between the openvpn and remote network(172.72.70.x), right?
-
@garona Yes
Need to test this theory
As far as I understand , from cisco it is necessary to change acl -
@garona
and on the pfsense side, we need to add another phase 2 -
Ok, i'll test this and tell you what happened later.
Thanks for the help. -
@konstanti
Ok
For example
cisco side
access-list 100 permit ip 172.70.70.0 0.0.0.255 100.100.100.0 0.0.0.255
pfsense side
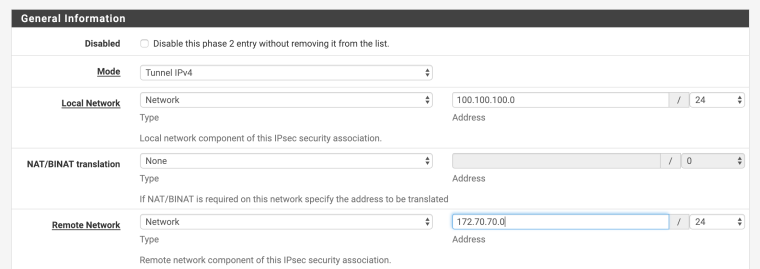
Forgotten
The network behind openvpn can be different if you use NAT .
About this we must remember
I gave an example , assuming that NAT is not being used