Getting a list of .bid IP's
-
I don't use pfB but could't you just add *.bid to the DNS blackhole or something?
-
No because they are not asking my DNS for an IP so it can't reject it. It would need to do a reverse lookup on the IP and get the name and then block on that and I don't think pfBlocker does than. That is why I need the IP range or addresses to enter in which does work.
-
.bid is just a TLD and any associated IP addresses would be totally random. There is no natural association between domains and ip addresses.
-
Are you certain the servers are actually in
.bidand not just using that as an e-mail address? If it is the latter, your mail server can likely be configured to reject any mail from*@*.bid -
No not the email address. Have been tracking the header data backwards. Yes some of them may be spoofed but certainly not all. The email addresses have all sorts of stuff in them so not reliable to exclude by that either. I did try and it was more work than simply hitting delete. Even tried filtering on subject lines.
Was getting heaps of those "I put a virus on your computer and watched you do naughty things. Pay me in bitcoin" that seem to be doing the rounds at present. Got 20 of them in three days at one point. Filter put a stop to most of those. -
You do understand the IPs that are are registered to domains that are in the TLD .bid would be changing second by second across the planet right..
IP has zero to do with DNS - zero... I can register ANY IP to a FQDN I have..
So host.domain.com can point to 1.2.3.4, or otherhost..someotherdomain.bid could also point to 1.2.3.4
For a PTR record who owns the IP block, and controls this space with their registrar can point the netblock to a NS for resolving the reverse... So it might resolve, it might not resolve that owner can have 1.2.3.4 PTR resolve to anything they want, etc..
How about you post up some headers of this spam, so we can see some IPs your wanting to block..
-
Okay here is one that just came in. I have remove the machine names
Received: from xxx.jv.net.nz (192.168.0.3) by xxx.jv.net.nz (192.168.0.3) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.1.669.32 via Mailbox Transport; Tue, 8 Jan 2019 08:38:40 +1300 Received: from xxx.jv.net.nz (192.168.0.3) by xxx.jv.net.nz (192.168.0.3) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.1.669.32; Tue, 8 Jan 2019 08:38:39 +1300 Received: from uncle.xtraincies.bid (185.207.36.201) by xxx.jv.net.nz (192.168.0.3) with Microsoft SMTP Server id 15.1.669.32 via Frontend Transport; Tue, 8 Jan 2019 08:38:39 +1300 DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=k1; d=xtraincies.bid; h=Mime-Version:Content-Type:Date:From:Reply-To:Subject:To:Message-ID; i=contact@xtraincies.bid; bh=QcL4Cbcr04iMmh7K8Bxu2+xbaXc=; b=B7DmX6LXPzwKThCI3UcYEHfUGaKjbgKnpXEo+zwA5uZlQdCQys4kkoa4v805vj1yPlf7JKeKQ/ul xhpYzv7Tns/t0IpGX8ibTC768NPnD4jsiv0YSFOAVFH4Tgv7VQSgcGhlGEgTNI35/GVZtZfe5vdD qkCMabdhvNwk+Hp7kMg= DomainKey-Signature: a=rsa-sha1; c=nofws; q=dns; s=k1; d=xtraincies.bid; b=OW/Rxj/UP0IAnUrtzl/juXM2pff6DAwO2rV0J+xG5BgGP+dK9PszaZPw27Ey6PO4iQk7Xlm8xVrI bsVajwAhXcIUvzDqMDx4W/8e8wB3kR6npCZjIYqWbtETrRblbWuSUbmx8bl6K6N66YqHeFZrgQAq fcGWwEHFJgG0xLBDQC0=; Mime-Version: 1.0 Content-Type: multipart/alternative; boundary="45c5754eadb092f72706788563141694_b6d9_2907f" Date: Mon, 7 Jan 2019 20:37:52 +0100 From: "MoveWise Offer" <contact@xtraincies.bid> Reply-To: "MoveWise Affiliate" <support@xtraincies.bid> Subject: Save Average of 25% On Moving Cost Today! To: <johnv@jv.net.nz> Message-ID: <l5rcfnuohcm8zk8e-ryhowl112k44cwy7-2907f@xtraincies.bid> Return-Path: 44194-46809-168063-9345-johnv=jv.net.nz@mail.xtraincies.bid X-MS-Exchange-Organization-Network-Message-Id: 3e6c0ea7-8c14-49c5-378a-08d674d7b962 X-MS-Exchange-Organization-PRD: xtraincies.bid X-MS-Exchange-Organization-SenderIdResult: None Received-SPF: None (xxx.jv.net.nz: contact@xtraincies.bid does not designate permitted sender hosts) X-MS-Exchange-Organization-SCL: 6 X-MS-Exchange-Organization-PCL: 2 X-MS-Exchange-Organization-Antispam-Report: DV:3.3.5705.600;SID:SenderIDStatus None;OrigIP:185.207.36.201 X-MS-Exchange-Organization-AVStamp-Enterprise: 1.0 X-MS-Exchange-Organization-AuthSource: xxx.jv.net.nz X-MS-Exchange-Organization-AuthAs: Anonymous X-MS-Exchange-Transport-EndToEndLatency: 00:00:01.3345153 -
@veldthui said in Getting a list of .bid IP's:
185.207.36.201)
In pfBlockerNG-devel is a new Feeds tab. You can try to add the "Mail" specific IP blocklists...
That 185 range is full of crap.... Alienvault feed would have blocked that event from getting thru. But jimps advice was good... You can do a good chunk of this with the mail server.
Recommend to add some RBLs and RHSBLs atleast from Spamhaus .... -
Thanks. Will try that. I tried to add them to exchange but Microsoft killed that and now you need an Edge Server to do the IP block lists from Spamhaus and I can't afford the extra license for the Edge Server.
Will check out the feeds tab. -
Tried to add the Zen Spamhaus list and got what I originally got when I tried it.
Says it cannot resolve zen.spamhaus.org and I can't resolve it with ping or any other tool.
-
@veldthui said in Getting a list of .bid IP's:
185.207.36.201
why not just block all of Turkey ;)
What comes out of their other than crap? ;) Just use pfblocker so some of those spam countries can not even talk to your mail server..
Do you do business with anyone in Turkey?
That IP is on a billion freaking blacklists
https://mxtoolbox.com/SuperTool.aspx?action=blacklist%3a185.207.36.201&run=toolpage
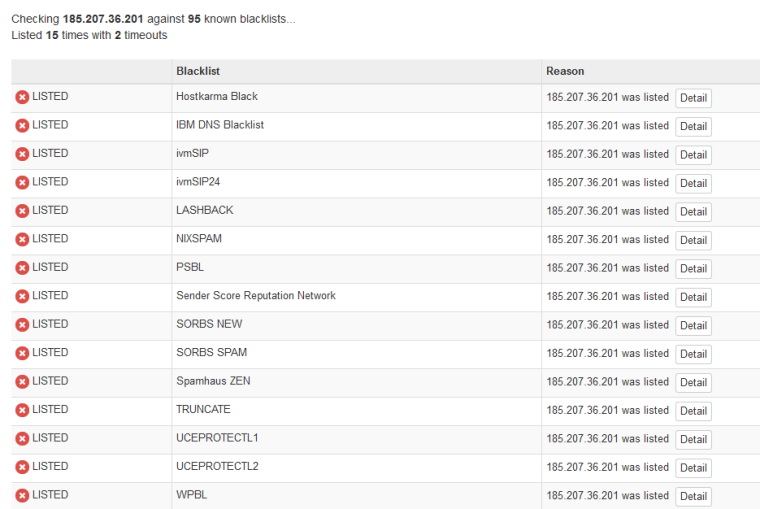
If your mail server can not talk to black lists maybe you should be fixing that...
-
Along with what johnpoz is saying, I would never run a mail server without zen.spamhaus :) Plus there are a few others that will really help in limiting spam.... I would also move away from Exchange into something postfix based like Zimbra.
-
Zen does not appear to be active. Tried looking it up on the DNS and says it is down.
Moving away from Exchange is not an option as there too much money spent on it to simply ditch it. Others have help pay for this as well. As I said with the Edge Server IP block lists can be used but again it cost more license fees for what is basically a relay just to filter spam. If I can filter most of the spam then I am happy.
-
@veldthui said in Getting a list of .bid IP's:
Zen does not appear to be active.
Zen is not down, you query it with a reverse ptr like so:
56.234.122.212.zen.spamhaus.orgThen the response tells the mail server if its listed in the zen database based on the IP in the answer (ie: 127.0.0.11)
https://www.spamhaus.org/zen/ -
;; QUESTION SECTION:
;201.36.207.185.zen.spamhaus.org. IN A;; ANSWER SECTION:
201.36.207.185.zen.spamhaus.org. 60 IN A 127.0.0.3Yup there is your IP you posted which .3 mean
"Direct snowshoe spam sources detected via automation"What does your exchange box use for dns? You can not be using say google or something - they not going to allow that to work..
-
Ah thanks for explaining how the spamhaus works. No my exchange server uses the local DNS on my domain controller. When it can't find an answer it will forward which now goes to pfSense and out from there.
-
@veldthui said in Getting a list of .bid IP's:
now goes to pfSense and out from there.
And pfsense is resolving - or is pfsense set to forward?
Do a simple dig or nslookup - do you get an answer from zen.spamhaus.org? if not you need to figure out where the dns is breaking down..
But for example if I ask google the same question I get back
$ dig @8.8.8.8 201.36.207.185.zen.spamhaus.org ; <<>> DiG 9.12.3-P1 <<>> @8.8.8.8 201.36.207.185.zen.spamhaus.org ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 48738 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;201.36.207.185.zen.spamhaus.org. IN A ;; AUTHORITY SECTION: zen.spamhaus.org. 9 IN SOA need.to.know.only. hostmaster.spamhaus.org. 1901082102 3600 600 432000 10 ;; Query time: 59 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Tue Jan 08 15:02:55 Central Standard Time 2019 ;; MSG SIZE rcvd: 124Because they do not allow it to work that way.. You need to be asking them directly, if you need to forward vs resolving your stuff - then you could setup a conditional forwarder for spamhaus so that you ask their ns directly.
-
pfSense is doing the resolving. I was querying spamhaus wrong so my bad there.
However I have added Alienvault to my IP block list and have not had any spam for the last two days. Still getting stuff from my webserver provider from the control panel but working on that now. -
@veldthui said in Getting a list of .bid IP's:
and have not had any spam for the last two days.
Music to my ears :)