Site-to-Site trafic redirection
-
Could you not just Policy Route his traffic to your main office with Firewall Rules?
I'd skip that redirect-gateway def1 stuff if possible...-Rico
-
Hi Rico,
And how would set that rule?
When I try anything else then redirect-gateway, I either lost internet or nothing is route through the vpn tunnel.
Am having headake on that one.
Thanks,
nginfo -
@nginfo Hi
https://www.netgate.com/docs/pfsense/routing/directing-traffic-with-policy-routing.htmlOn the client side , on the Lan interface, you need to create a rule that will redirect traffic from client through the openvpn tunnel. To do this, change the default gateway to openvpn gateway.
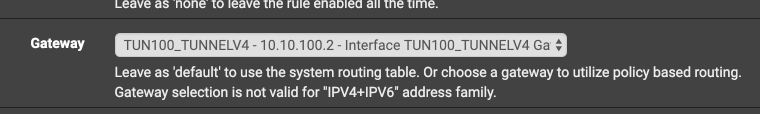
This rule must be located above the other rules.

In this case, the "redirect-gateway def1;" option is not needed
-
And check out https://www.netgate.com/resources/videos/openvpn-as-a-wan-on-pfsense.html for more detailed information.
-Rico
-
Hi guys,
thank you for the links. It seems to work fine now.
Do you know if it is possible to block internet if the VPN is down?
Rightnow if the VPN_gateway is down, trafic goes through WAN_gateway and the client site don't want that.
Thanks,
nginfo -
@rico said in Site-to-Site trafic redirection:
Could you not just Policy Route his traffic to your main office with Firewall Rules?
I'd skip that redirect-gateway def1 stuff if possible...Agreed. Looks like you may have eventually done it already, but what you'd want to do is assign the client tunnel to an interface, policy route traffic sourced from the client-end to the headend and then NAT it out the headend WAN.
Do you know if it is possible to block internet if the VPN is down?
Rightnow if the VPN_gateway is down, trafic goes through WAN_gateway and the client site don't want that.There may be several ways of doing this, but one way is to simply add a block all immediately below the policy route line.
-
OpenVPN Kill Switch: https://forum.netgate.com/topic/67692/openvpn-kill-switch/6
-Rico
-
This summarizes it:
https://www.infotechwerx.com/blog/Prevent-Any-Traffic-VPN-Hosts-Egressing-WAN
You need to mark the traffic on the firewall rules that policy route the traffic to the VPN and block traffic with that mark outbound on WAN.
-
Hello,
thank you everyone for your help. Everything seems to work perfectly now.
I fixed the problem by checking Skip rules when gateway is down (System, Advanced, Miscellaneous)
Thank you again.
Nginfo -
Yeah. I don't like that solution but if it works for you, great. Be sure you have a block rule after that or it will just go out WAN.
-
@derelict Yes I do. I took it from Netgate video.
so far it is the only solution that worked for me, so I'll take it :)