Setting up a home lab- need NAT to have internal virtual switch to go into the internet
-
If those guests get DHCP from the ASA the problem is in Hyper-V not pfSense.
All you have to do is create two vswitches, one on the outside for pfSense WAN to your existing, upstream LAN and one on the inside to pfSense LAN and the guests.
Generic terms because I don't use Hyper-V.
-
@derelict if you look at my network diagram this is what i did......
-
If that is what you did, the DHCP wouldn't flow between that switch and the ASA.
It really is as simple as that. Check everything again. This is a Layer 2 problem. Nothing pfSense can do about it.
It could also be the way Hyper-V is connected to the physical network.
Moving to Virtualization.
-
@korr2221 said in Setting up a home lab- need NAT to have internal virtual switch to go into the internet:
and my internal virtual switch have all the VMs connected to that. It's not getting DHCP from the ASA FW.
He stated he VMs were NOT getting dhcp from ASA..
-
Ah. Yeah that works out of the box. Confused by the message in the diagram.
-
@derelict As John said I think you misunderstood my problem. I don't want DHCP to be given by the ASA. It will be given by either pfsense or the Windows 2012 server for the 10.0.0.x /24 network. Anything behind pfsense will get it's own DHCP. The only issue is NAT'ing and somehow the VMs are not getting internet.
-
@derelict Yeah, everyone here so far is telling me this. I thought I had to make an entry in the NAT Outgoing rule. But apparently not? So I guess I'll have to reset it to default and hope it works?
-
Its not HOPE ;) This is drop dead work out of the box simple... I have setup pfsense 100's of times over the years... And it really is clicky clicky up and running.. It is so drop dead simple its just amazing how users manage to mess it up...
There is really nothing to do but answer a couple of questions - like your time zone and what you want to call pfsense and will work.
-
With a simple DHCP WAN and LAN, Automatic Outbound NAT pretty much "just works."
You likely do not need to reinstall. Just save the configuration and reset to factory. You can easily restore the saved config and be right back where you are now.
Tip for a Virtual Lab:
The first thing I usually do after I install a new VM firewall is drop to the shell and run this:
pfSsh.php playback enableallowallwanYou can then just use your workstation to connect to the web gui on WAN (the address is right there above the console menu) so you don't have to connect using a VM. You would, of course want to disable (or source limit) that rule to test WAN firewall functionality.
ETA: DISCLAIMER this is not something you want to do with anything actually on the wild internet.
-
@johnpoz Just did a factory reset, update to the latest version of pfsense.
Did you mess with the lan rules? This no longer matter I reset it to factory default.
Did you mess with the outbound nat tab? factory default.
Your setup is out of the box, click click works.
Are you running any packages? No packages with logging facilities are currently installed.
Does pfsense have internet access? •Unable to retrieve package information. It does not have internet.......
-
If you have no internet from the node itself, nodes behind it won't have internet either.
-
@derelict yes.... but why doesn't it have internet? If I use the same external network adapter in a windows 10 vm it has access to the internet.........i'm accessing the web gui via the LAN address which is 10.0.0.1 /24.... not from the 192.168.1.x interface. It's updated to version 2.4.4.2... i don't get it...... how does it not have internet but able to download and update? LOL
The process will require 24 MiB more space.
[1/1] Upgrading pfSense-kernel-pfSense from 2.4.2 to 2.4.4_2...
[1/1] Extracting pfSense-kernel-pfSense-2.4.4_2: .......... done
===> Keeping a copy of current kernel in /boot/kernel.oldRemoving unnecessary packages... done.
Upgrade is complete. Rebooting in 10 seconds.
Successnvm it has internet...i got the package list after the update
-
ok so if it has internet - then you clients behind it would have internet.
-
@johnpoz clients behind it doesn't have internet.... Any ideas?
-
Can clients ping pfsense IP? Is this what is set for their gateway?
Lets see a traceroute to 8.8.8.8 for example
First hop should be pfsense IP on your VM lan you setup. Do I really have to fire up hyper-v to show you how simple this is?
-
can ping 10.0.0.1 (LAN interface), 192.168.1.11 (WAN interface) fine no problem with no loss
can not ping 192.168.1.1 which used to be the ASA FW, which I am now putting in a normal Netgear Nighthawk hoping it wasn't the firewall.After doing a tracert looks like it don't know what to do with the traffic from 10.0.0.1? This is what I get:
C:\Users\User>tracert 8.8.8.8
Tracing route to 8.8.8.8 over a maximum of 30 hops
1 2 ms 9 ms 4 ms 10.0.0.1
2 2 ms 9 ms 9 ms 10.0.0.1
3 6 ms 8 ms 6 ms 10.0.0.1
4 4 ms 9 ms 7 ms 10.0.0.1
5 * * * Request timed out.
6 * * * Request timed out.
7 * * * Request timed out.
8 * * * Request timed out.
9 * * * Request timed out.
10 *I would like to note a couple things though before I leave for work:
pfsense has the following set:
DNS server(s)
127.0.0.1
75.75.75.75
Version 2.4.4-RELEASE-p2 (amd64)
built on Wed Dec 12 07:40:18 EST 2018
FreeBSD 11.2-RELEASE-p6LAN Interface Config
Static IPv4 Configuration
10.0.0.1NAT > Outbound Rules
Automatic Rules:
Interface Source Source Port Destination Destination Port NAT Address NAT Port Static Port Description
WAN 127.0.0.0/8 ::1/128 * * 500 WAN address * Auto created rule for ISAKMP
WAN 127.0.0.0/8 ::1/128 * * * WAN address * Auto created rule
LAN 127.0.0.0/8 ::1/128 * * 500 LAN address * Auto created rule for ISAKMP
LAN 127.0.0.0/8 ::1/128 * * * LAN address * Auto created ruleWAN Rules
0 /270 KiB- RFC 1918 networks * * * * * Block private networks
0 /22 KiB - Reserved
Not assigned by IANA * * * * * Block bogon networks
LAN Rules
Rules (Drag to Change Order)
States Protocol Source Port Destination Port Gateway Queue Schedule Description Actions
1 /16.65 MiB-
-
- LAN Address 443
80 * * Anti-Lockout Rule
5 /892 KiB
IPv4 * LAN net * * * * none Default allow LAN to any rule
0 /0 B
IPv6 * LAN net * * * * none Default allow LAN IPv6 to any rule
- LAN Address 443
-
GATEWAY
WAN_DHCP (default) WAN 192.168.1.1 192.168.1.1 Interface WAN_DHCP Gateway
GW_LAN LAN 10.0.0.1 10.0.0.1 Interface lan Gatewayedit-
also want to mention I realized Hyper V created this weird Default Switch which is greyed out it state the Default network switch automatically gives virtual machines access to the computer's network using NAT. Any idea if I should be doing this for anything? When I look at it from the host it has a 172.18.19.255 255.255.255.240 network. - RFC 1918 networks * * * * * Block private networks
-
And you did a clean install of pfsense with a wan and lan switch in hyper-v?
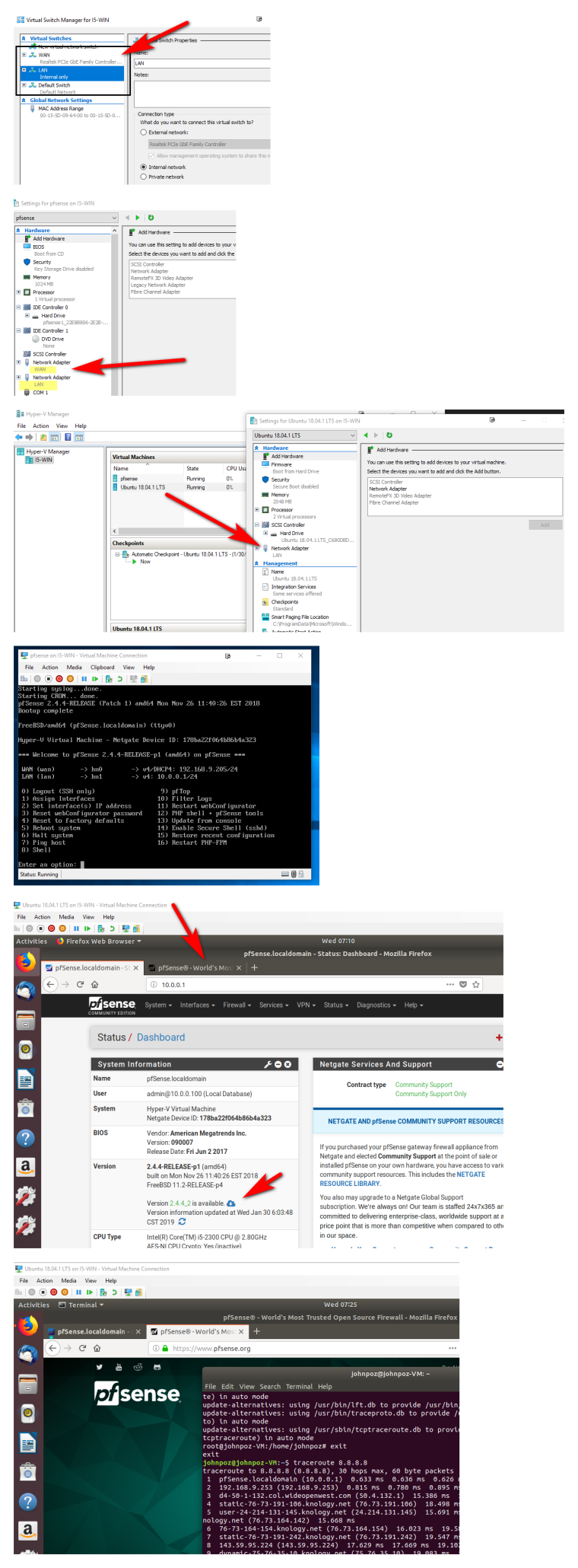
Here this is how freaking drop dead simple this is..
Created my wan external switch, connected to nic on my host machine.
Created an internal vswitch (only for vms)Did a pfsense vm, 2 nic 1 on wan switch, other on lan switch. even set my lan IP to be the same as yours 10.0.0.1/24
Fired up test vm on the internal switch.. It got IP from pfsense dhcp, can access the gui, internet.. If it takes you more than 5 minutes to set this all up you have something wrong..
You can see pfsense sees there is update available - so it can get to the internet.. client can get to the internet through pfsense.. See the traceroute.
-
@korr2221 said in Setting up a home lab- need NAT to have internal virtual switch to go into the internet:
LAN 127.0.0.0/8 ::1/128 * * 500 LAN address * Auto created rule for ISAKMP
LAN 127.0.0.0/8 ::1/128 * * * LAN address * Auto created ruleThat is Never going to work!!! Where is your local network? 10.0.0/24
Here is mine just setup
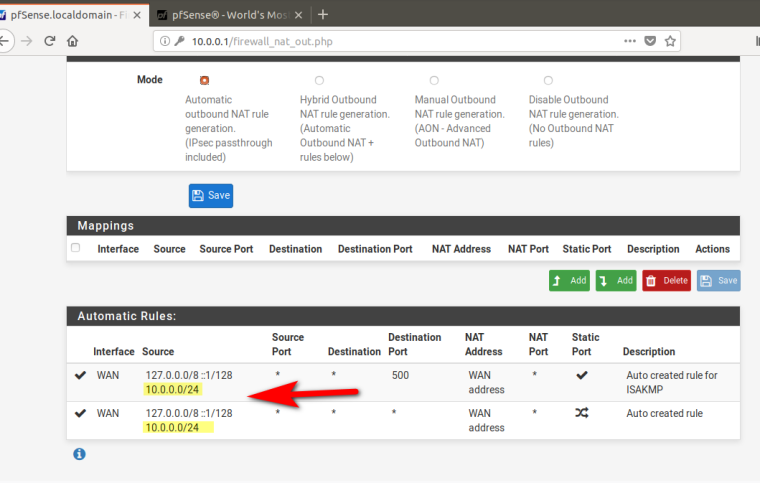
You got something broke if its not creating the automatic NAT for your lan network.
You set a GATEWAY on your LAN interface didn't you to what its OWN address... Pfsense clearly NOT to do that!!!!
GW_LAN LAN 10.0.0.1 10.0.0.1 Interface lan Gateway
How could you think that would work???
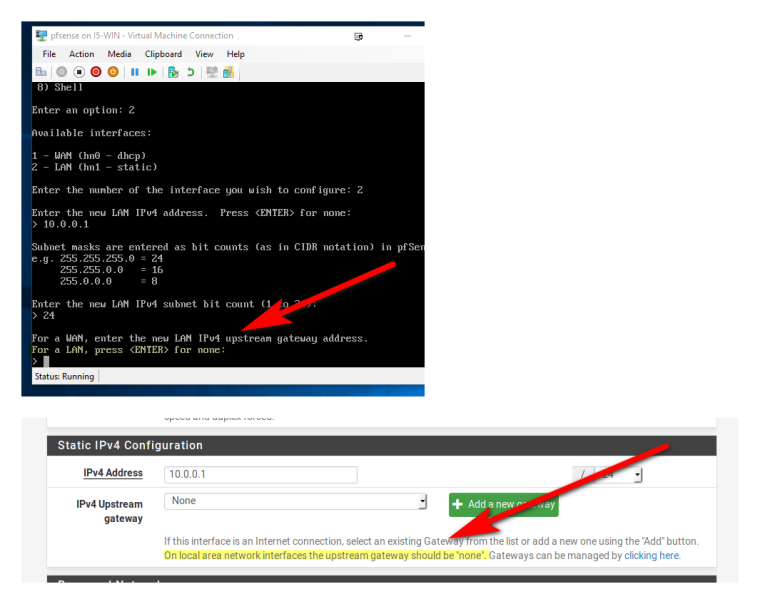
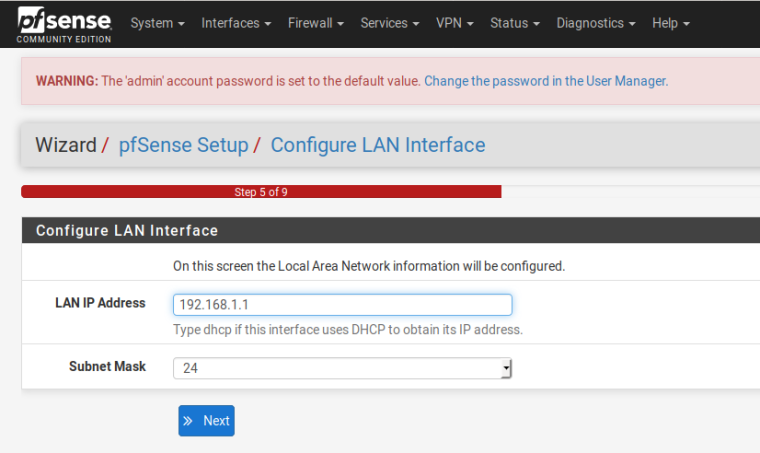
I just went through the wizard again... It doesn't even give you a option to set the gateway on the LAN... You have to go OUT OF YOUR WAY to do that... And then NOT read the info that clearly says NOT to set a gateway if its the local network and not your wan..
-
@johnpoz Bro it must be my pfsense image. lol..... I did not configure THAT! I set everything back to default.
-
Sorry but NO its not the pfsense image..... Out of the box the IP Lan for pfsense is 192.168.1.1/24 with NO GATEWAY.. For it to be 10.x.x.x you had to have changed it... It sure and the F would not have set a gateway to itself.. It just wouldn't!!! Its NOT possible.. You saw my setup, I just ran through it in like 5 minutes... The longest part was downloading the quick VM for ubuntu in hyper-v ;)
Did you download this image of pfsense from somewhere other then pfsense/netgate? Is it some hyper-v image you got from somewhere?