AWS Pfsense OpenVPN no access to private subnet
-
Will update the topic:
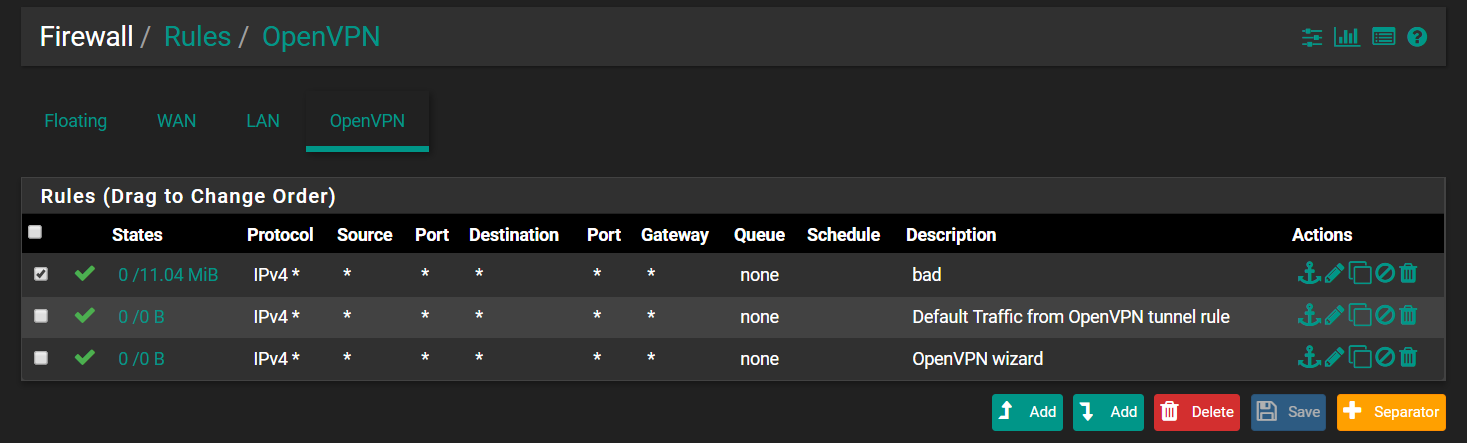
-
sorry, should have also requested LAN rules as well. please post those too.
-
@isolatedvirus no worries, thank you for your time. Updated the topic with the requested information!
-
can you confirm pfsense can ping the instance (.58)
Also confirm the following:
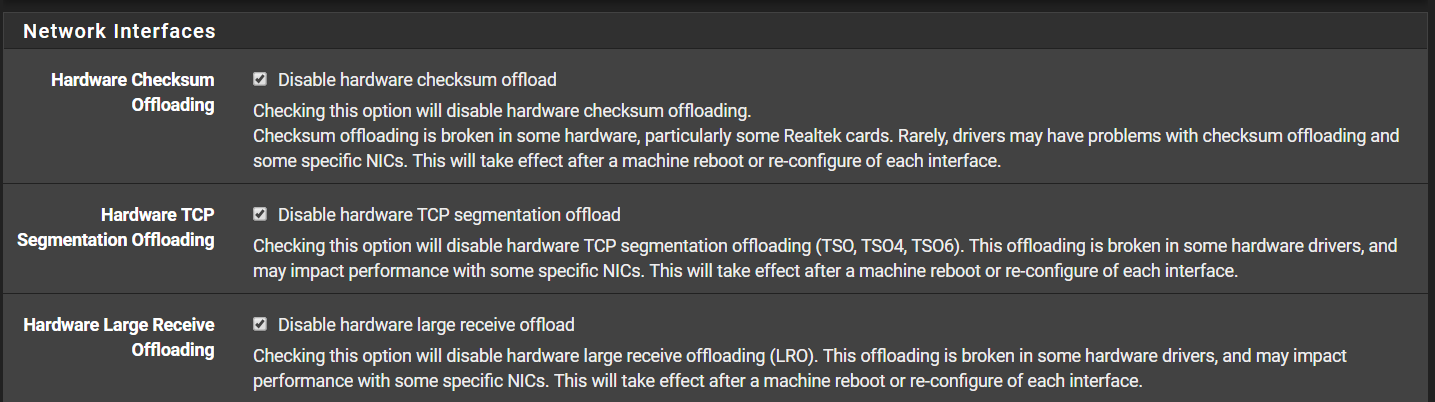
System->Advanced->Networking
-All offloading is disabled (Checksum/TCP Seg/Large Receive -
Yes pfsense can ping all instances in the private subnet.
Confirmed:
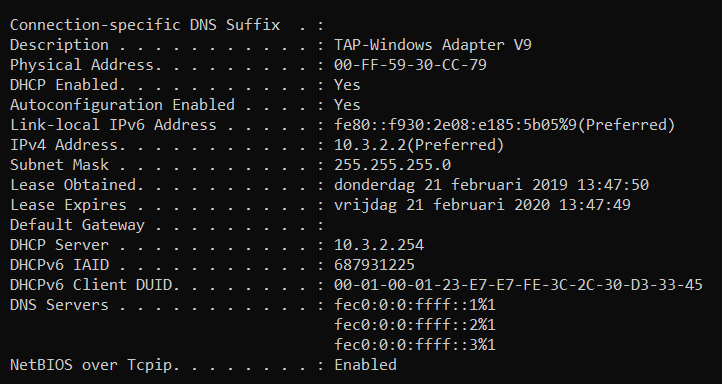
I don't get a default gateway when connecting to the vpn, could that have something to do with it?
-
ok i think it might be a route or firewall entry on the linux host itself.
You can post your screenshots of your OpenVPN server config, but i doubt theres an issue there primarily because: Windows can ping the firewall tunnel IP and the firewall interface on the subnet in question. This leads me to believe youre forwarding the correct routes for the vpn.
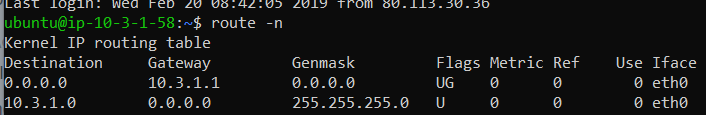
Post the route table and firewall config for the linux host.
-
@isolatedvirus ok, thank you for your reply. I currently have 2 linux hosts in the private subnet (which has access to the internet for now otherwise I could not SSH into the hosts):
Nagios XI on centos:
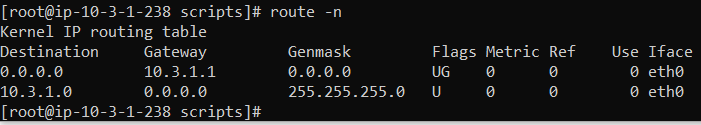
Ubuntu server:
firewall is off:
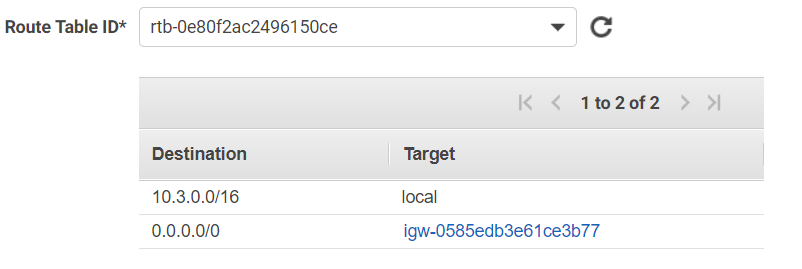
Amazon private subnet (should be without internet access):
-
your hosts have their gateway set as 10.3.1.1, it should be 10.3.1.5 (PFSense Lan) unless you have another gateway in the environment.
Otherwise, set a route for your VPN subnet to point to 10.3.1.5 on the linux hosts
-
@isolatedvirus said in AWS Pfsense OpenVPN no access to private subnet:
10.3.1.5
Yes this worked!
I can now ping my private subnet instances from the vpn client.
Do you happen to know why the default gateway gets set to 10.3.1.1?
Everytime I make a new instance it sounds like I need to change the default gateway manually.Thank you for your time and help.
-
I'm not sure why. If youre handing out IP's behind pfsense via DHCP i'd check the dhcp config to verify youre not handing out the wrong gateway config.
Its also possible that this is just a AWS thing, since im not familiar with AWS i cant really say.
-
What have you done in the VPC routing table so it knows to send traffic for the 10.3.2.0/24 subnet back to the pfSense interface?
-
Is this regarding the default gateway of the instances?
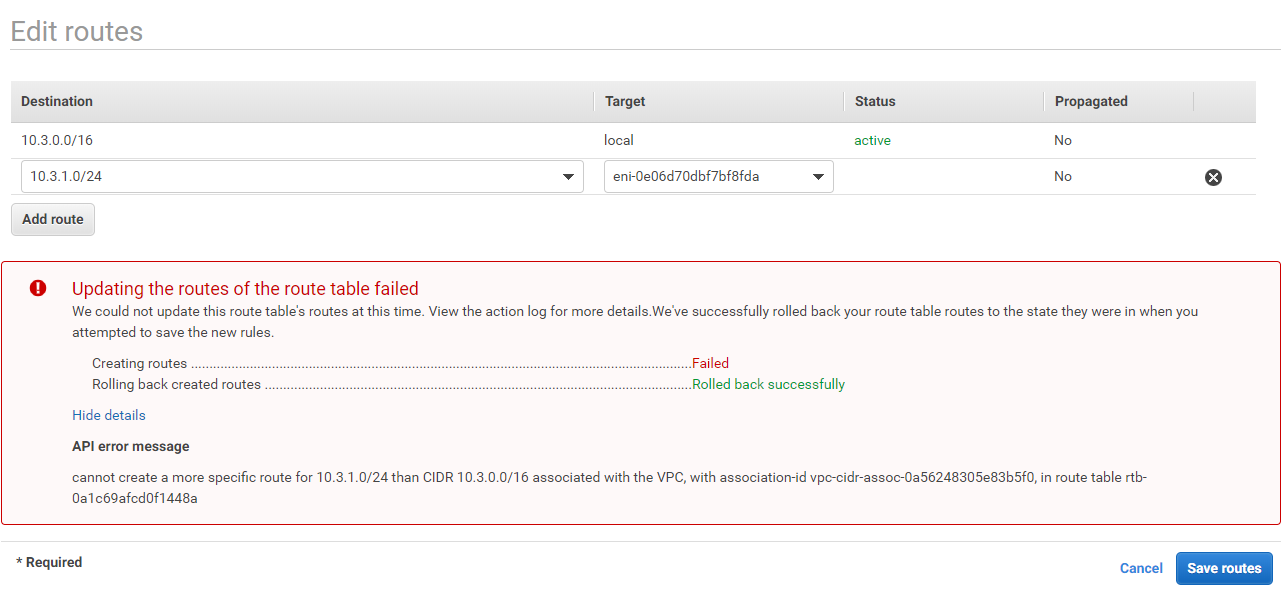
I thought I should edit the route table of the private subnet to point to 10.3.1.5 which is the LAN side of the pfsense firewall but it won't let me do just that:private subnet
-
You can't use subnets contained inside your VPC subnet anywhere but the VPC itself.
Use something outside of that for the other side of the VPN. Sorry. That's just the way AWS works, as you can see from that error message.
-
@Heikum in my case hardware checksum offloading chacked solved the problem. Thanks!
-
@Leonardo-Fernandes That is only when using ena adapters and is fixed by a later version of the ena driver in pfSense 2.5.0.
-
@leonardo-fernandes You are my hero. Thank you very much. My OpenVPN with AWS works perfectly now