Need to understand why traffic is allowed
-
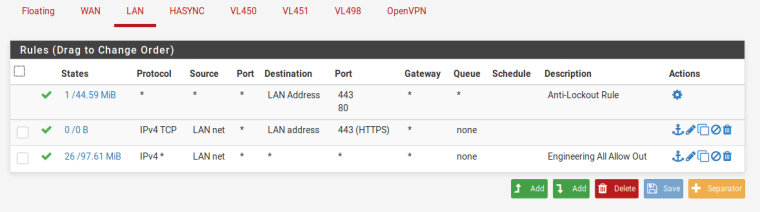
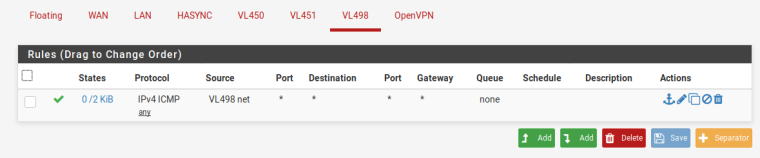
Here are the rules I have currently. LAN is the 10.10.34.0/24 network. I'm routing 10.4.98.0/24 at 10.10.34.254 as a temporary solution to gain connectivity between environments. LAN has all traffic allowed out, so this would allow all traffic to head towards VL498. However, looking at the rules for VL498, there's no rule which would allow the traffic into the environment.
It's my understanding that there's an implicit deny on the interfaces, which I do see when trying to send traffic out of VL498 as everything is blocked unless I make an explicit rule.
-
RTFM:
https://docs.netgate.com/pfsense/en/latest/book/firewall/index.htmlHint: Traffic is only subjected to interface rules when it enters the firewall. Only floating rules can filter traffic leaving the firewall.
-
@grimson said in Need to understand why traffic is allowed:
RTFM:
https://docs.netgate.com/pfsense/en/latest/book/firewall/index.htmlHint: Traffic is only subjected to interface rules when it enters the firewall. Only floating rules can filter traffic leaving the firewall.
Wait, so you can't filter traffic between interfaces? That doesn't make any sense on any firewall.
Where specifically in the manual does it say this, as I've read it and must have missed that part.
-
Sure you can, but your LAN Firewall Rules say LAN net -> any
so why shoud the LAN net not reach VL498 ?-Rico
-
@gryman said in Need to understand why traffic is allowed:
Wait, so you can't filter traffic between interfaces? That doesn't make any sense on any firewall.
If you don't want traffic from LAN to VL498 you put a block rule with destination "VL498 net" on your LAN. That's pretty basic stuff, so really read the book until you understand it.
-
@rico said in Need to understand why traffic is allowed:
Sure you can, but your LAN Firewall Rules say LAN net -> any
so why shoud the LAN net not reach VL498 ?-Rico
It should reach VL498, but then be dropped as VL498 has no rule allowing the traffic in. This is how firewalls work, usually. Now, the exception would be if there's no implicit deny, which I understand there is.
-
@gryman said in Need to understand why traffic is allowed:
It should reach VL498, but then be dropped as VL498 has no rule allowing the traffic in. This is how firewalls work, usually. Now, the exception would be if there's no implicit deny, which I understand there is.
Don't be a thickhead and do some RTFM: https://docs.netgate.com/pfsense/en/latest/book/firewall/rule-methodology.html
-
@grimson said in Need to understand why traffic is allowed:
@gryman said in Need to understand why traffic is allowed:
It should reach VL498, but then be dropped as VL498 has no rule allowing the traffic in. This is how firewalls work, usually. Now, the exception would be if there's no implicit deny, which I understand there is.
Don't be a thickhead and do some RTFM: https://docs.netgate.com/pfsense/en/latest/book/firewall/rule-methodology.html
So basically if traffic comes into LAN, LAN filters the traffic, but then VL498 does not, because it didn't originate from the inbound side of the interface, correct?
So if there's one misplaced rule on one interface allowing traffic out, it can compromise every other interface within the firewall, correct?
-
If you work with firewalls, you can't just misplace anything without shit happens. Understand how it works, setup your stuff properly and test it.
-Rico
-
@rico said in Need to understand why traffic is allowed:
If you work with firewalls, you can't just misplace anything without shit happens. Understand how it works, setup your stuff properly and test it.
-Rico
If you're the sole administrator of a firewall for your home, then yes, you can ensure that everything is always perfect. When you get into enterprise environments, that becomes harder. If a first level support person adds a rule for customer X to allow outbound traffic to *, that shouldn't compromise every other customer on that firewall who are behind different interfaces.
Customer X is in VLAN 500 which is a virtual interface VL500. They want all traffic allowed outbound. What would the correct way look like for this? What rule do you enter to allow traffic out to the internet but not other interfaces within your environment?
I'm trying to understanding these firewalls, but they work much differently than Cisco or Palo Alto which I use on a daily basis.
Usually, you have ingress and egress filtering per interface/zone, depending on the setup. PFS doesn't use zones, but interfaces. The docs say there's an implicit deny on the interface, which I can validate as working, but only on "inbound" traffic from the interface perspective.
Where I'm at now is I need to be able to isolate interfaces from each other. Even adding an explicit deny on VL498 it doesn't stop the traffic from entering that environment.
-
youre forgetting about state tables and related/established connections. Checkpoint/Cisco/Palo Alto all do this as well.
Egress matching can be performed in a floating rule. interface/zone firewalls do things slightly differently, but 99% of it is the same.
You can isolate interfaces with inverse matching.
EX: Lan/Lan Subnet, OPT1/OPT1 Subnet, OPT2/OPT2 Subnet
Allow lan subnet, any service, any port, destination !OPT1 Subnet.This would allow Lan to anything that isnt in the OPT1 Subnet. You can create aliases for combinations of these, similar to node/object groups in enterprise firewalls.
-
@isolatedvirus said in Need to understand why traffic is allowed:
youre forgetting about state tables and related/established connections. Checkpoint/Cisco/Palo Alto all do this as well.
Egress matching can be performed in a floating rule. interface/zone firewalls do things slightly differently, but 99% of it is the same.
You can isolate interfaces with inverse matching.
EX: Lan/Lan Subnet, OPT1/OPT1 Subnet, OPT2/OPT2 Subnet
Allow lan subnet, any service, any port, destination !OPT1 Subnet.This would allow Lan to anything that isnt in the OPT1 Subnet. You can create aliases for combinations of these, similar to node/object groups in enterprise firewalls.
States, yes. But that would be per interface/zone. So if I allow outbound traffic from LAN, inbound return traffic would be allowed because the state is tracked. But if I don't allow the traffic into VL498, the state for LAN should not apply.
What I'm reading is each interface would need a rule prohibiting traffic to other interfaces, correct?
-
correct.
An easier way to think about zone vs interface based:
Zone allows multiple interfaces to subscribe to it. Rules are applied according to zone membership.
Interface treats each individual interface as its own separate zone. Rules that would be identical on different interfaces must be replicated. -
@gryman said in Need to understand why traffic is allowed:
If a first level support person adds a rule for customer X to allow outbound traffic to *,
On what planet would any company allow 1st level support to touch a firewall? Really? For rules to get changed on the enterprise you have to go through process, change control.. Not sure where you get the idea that people can just willy nilly change rules on a firewall in a enterprise.
As to an ISP and firewalling customer connection - why would they be filtering anything in the first place.. Seems to me your just not thinking this stuff through with zero real world hands on experience to base any of your assumptions on.
-
@johnpoz said in Need to understand why traffic is allowed:
@gryman said in Need to understand why traffic is allowed:
If a first level support person adds a rule for customer X to allow outbound traffic to *,
On what planet would any company allow 1st level support to touch a firewall? Really? For rules to get changed on the enterprise you have to go through process, change control.. Not sure where you get the idea that people can just willy nilly change rules on a firewall in a enterprise.
As to an ISP and firewalling customer connection - why would they be filtering anything in the first place.. Seems to me your just not thinking this stuff through with zero real world hands on experience to base any of your assumptions on.
this contributed how exactly?
-
Pointing out NONSENSE is how it contributes!
-
@johnpoz said in Need to understand why traffic is allowed:
@gryman said in Need to understand why traffic is allowed:
If a first level support person adds a rule for customer X to allow outbound traffic to *,
On what planet would any company allow 1st level support to touch a firewall? Really? For rules to get changed on the enterprise you have to go through process, change control.. Not sure where you get the idea that people can just willy nilly change rules on a firewall in a enterprise.
As to an ISP and firewalling customer connection - why would they be filtering anything in the first place.. Seems to me your just not thinking this stuff through with zero real world hands on experience to base any of your assumptions on.
I've worked in the datacenter space for almost 10 years now. Private smaller companies, and globally traded public companies. First level support absolutely does touch firewalls, and ISPs absolutely do filter traffic. Now, a public ISP that provides broadband does not, usually, filter traffic. But that's not what I'm talking about.
Anyways, I don't need to speak to my experience and qualifications here. I'm just trying to convey what I believe to be an issue in how the firewall processes rules based on my experience with other platforms. Now, this could just be because I come from a multi-tenant world and that's how I think. It might just be that PFS isn't designed around this model, and that's why I'm having a hard time understanding why it works the way it does.
-
Dude I have worked on juniper netscreen and srx, cisco pix and asa, checkpoint.. Pretty much its a firewall and I have used it... Not ONE of them sets rules based upon exit of a interface..
And you have not had to set return traffic rules on a firewall since the old packet filter days back in the early 90s there was some of those.. By the end of the 90s all packet filter firewalls without states were gone, etc.
You set rules on the interface/zone of where the traffic will first enter the firewall..
Some ma and pop shop with a box hosted in your DC is a bit different than an actual enterprise - sorry... In an Enterprise there are layers and layers of process that has to be followed for rules to get modified on firewall, security signoff on it, more than likely 4 eyes during the change process itself, etc. Then validation right after the change that is is actually doing what its suppose to, etc.
-
@johnpoz said in Need to understand why traffic is allowed:
Dude I have worked on juniper netscreen and srx, cisco pix and asa, checkpoint.. Pretty much its a firewall and I have used it... Not ONE of them sets rules based upon exit of a interface..
First one that comes to mind is a Cisco ASA. Traffic can not flow from a DMZ into a LAN by default due to security levels set.