pfSense Firewall Rules
-
Hi there,
I am quite new at pfSense and firewalling in general. I got the pfSense installed and OpenVPN to connect from external. I got a web server. I want to set up the firewall so that only whitelisted IP address and the VPN clients can access the web sites on the server (http and https). I was able to create the rule to filter the whitelist, but then I am not able to access the sites from my VPN client...Any help please?
D.
-
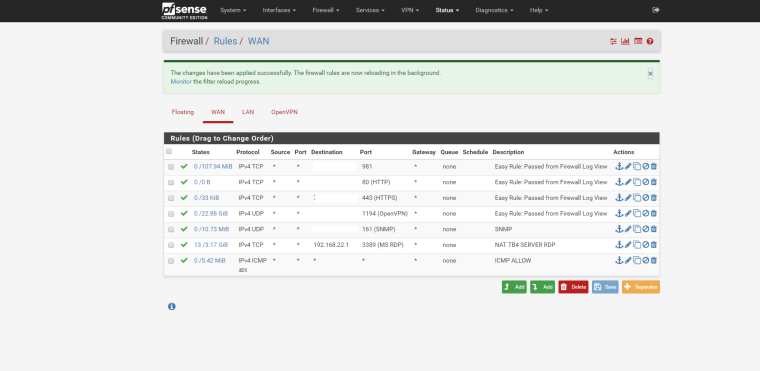
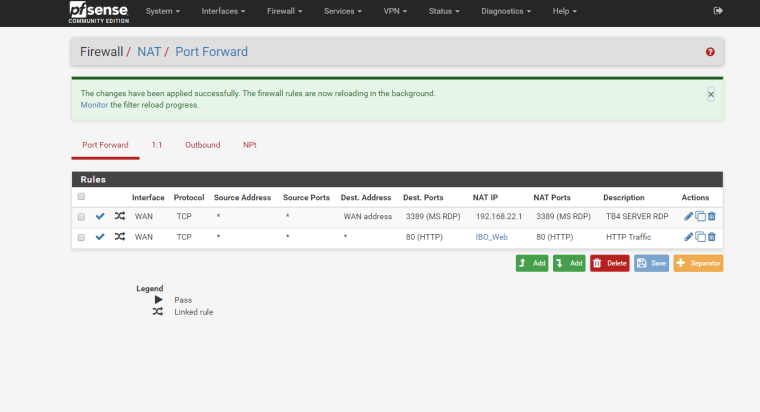
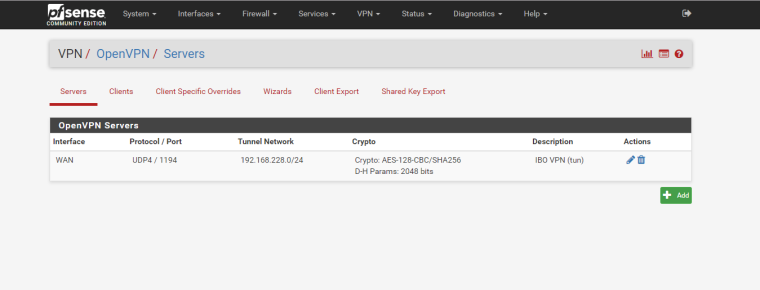
Without any details whatsoever, it's going to be almost impossible to help you. Post some screens of your NATs, WAN rules and OVPN config.
-
Here they are.
Thanks.
-
Have you added any rules on the OpenVPN firewall tab? Only WAN/LAN get default rules. All other interfaces MUST have their rules manually added.
-
Here
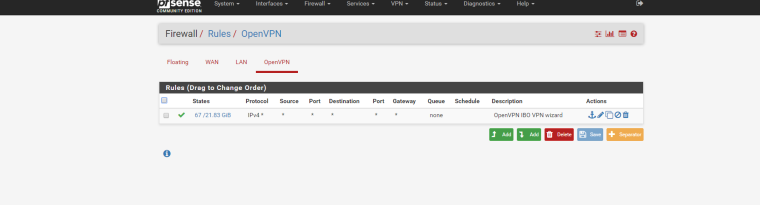
-
How are you testing from inside or outside your network? From the above screens, you aren't limiting access at the firewall so you should be able to hit your web server from anywhere unless you're limiting access via web server directives. Does that work if oyu try to access your web server without being on the VPN? What is in that IBO_Web alias? It should hold the IP address of your web server. You didn't put in the IPs of the allowed clients in that alias, did you?
-
Hi Kom,
i am testing from outside the network, connected to the VPN and not. IBO_Web contains the IP address of the web server.Here some screenshots with some new configuration. I added a NAT entry for the OVPN, but still no luck. IP whitelisting is working, only allowed IPs can access the web server; but OVPN clients cannot. They are being rejected because of the "Default deny rule IPv4 (1000000103)" (from the firewall log). For some reasons even if connected to the VPN they hit the firewall with the machine public IP address. For example, the VPN public IP address is XX.XXX.XXX.XX, if I go to whatsmyip I see it correctly XX.XXX.XXX.XX, but in the firewall log the entry is YY.YYY.YYY.YY:80 TCP:S where YY.YYY.YYY.YY is my machin public IP address. Hope it makes sense...
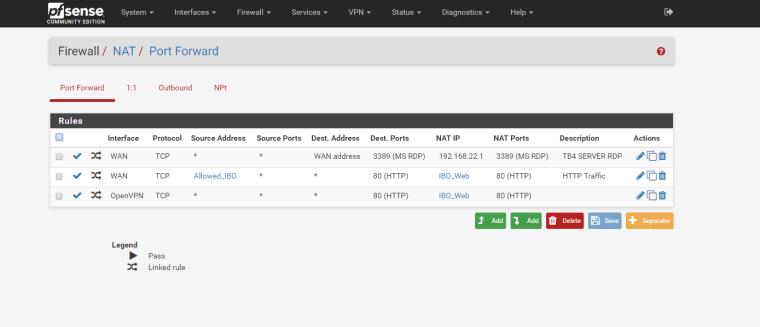
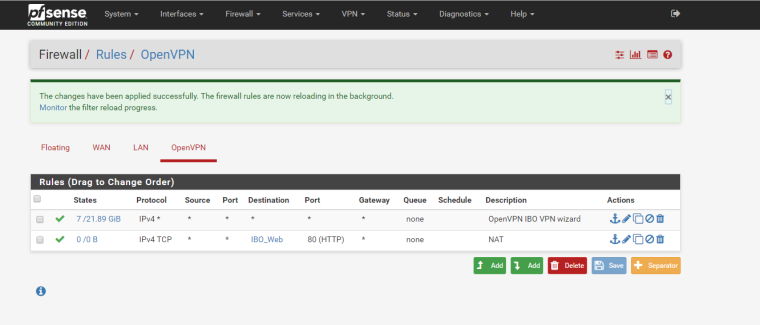
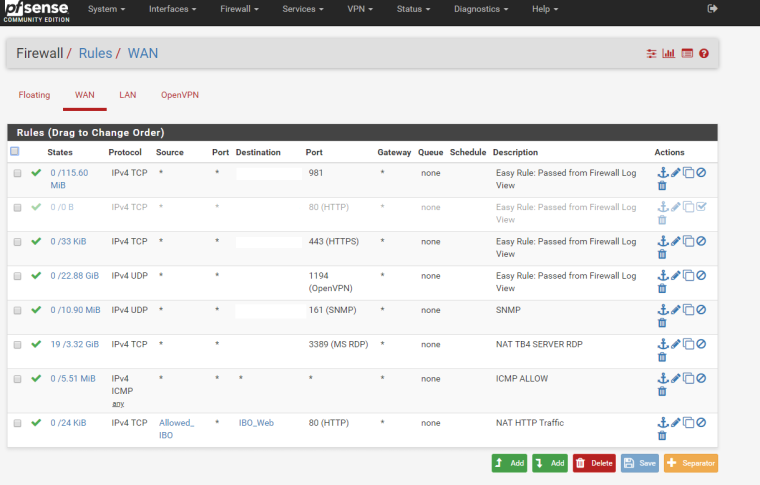
-
What's in your Allowed_IBO alias? Can I assume that you are including the OVPN subnet in it?
-
It wasn't. I added it, but still doesn't work when connected to the VPN.
-
Hold on a sec. Your VPN users are already inside your network, therefore they should not be using the NAT in the first place. Add a host override to your DNS config so that it resolves your web server's hostname to its LAN IP address. Then they should just be able to connect without issue.
-
Kom, this is what I added to the DNS Resolver:
Host Overrides
bo-temp xxxx.com 192.168.22.3 DNSStill not working. If I ping 192.168.22.3 from my machine connected to the VPN, I get a response. If I ping bo-temp.xxxx.com it resolves with the network public IP address.
-
This should be easy. You should be able to access your internal web server via the VPN without any magic. Let's start simple: Can you access it via its LAN IP address? eg http://192.168.22.3/?
-
@19giugno said in pfSense Firewall Rules:
Still not working. If I ping 192.168.22.3 from my machine connected to the VPN, I get a response. If I ping bo-temp.xxxx.com it resolves with the network public IP address.
So what DNS is your machine using? For the DNS overrides to work it obviously has to use the DNS resolver/forwarder from the pfSense instance where the override is configured.
-
-
@grimson said in pfSense Firewall Rules:
@19giugno said in pfSense Firewall Rules:
Still not working. If I ping 192.168.22.3 from my machine connected to the VPN, I get a response. If I ping bo-temp.xxxx.com it resolves with the network public IP address.
So what DNS is your machine using? For the DNS overrides to work it obviously has to use the DNS resolver/forwarder from the pfSense instance where the override is configured.
Hi Grimson,
I am using assigned DNS (Obtain DNS server address automatically). I am not sure how to check if I am using the DNS resolver/forwarder? And how I can be sure to use it? -
OK so your problem is DNS-related. Status - Services will tell you if you're using Forwarder (dnsmasq) or Resolver (unbound). Or you could go to Services - DNS Forwarder and see if it's enabled, likewise for Services - DNS Resolver.
It looks to me like you don't have your OpenVPN config quite right. In your config under Advanced Client Settings, are you pushing pfSense DNS to your VPN clients?
-
Hi KOM,
DNS Resolver is enabled, DNS Forwarder is not.In OperVPN, Advanced Client Settings there is nothing enabled.
Thanks.
-
So then try checking the DNS Server Enable box and then add your pfSense LAN IP address as DNS Server 1.
-
@19giugno said in pfSense Firewall Rules:
Hi KOM,
DNS Resolver is enabled, DNS Forwarder is not.In OperVPN, Advanced Client Settings there is nothing enabled.
Thanks.
Yes! That worked! It works now. Thank you so much!
I got another question now, if the answer is yes I will open a new thread: is it possible to have whitelist specific for websites? I mean, on the web server I have website A and website B. Can I define an alias to access only website A and another one website B?
-
Of course. You can specify the Source for any NAT you create. Create an alias for your whitelist and then use it as the Source in your NAT rule.