Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch
-
@chris-1028 said in Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch:
Interesting: if I understand what you say, I can now use a **tagged"" VLAN as admin for the AC-Pro. Correct?
If it's on a current firmware and you are using a current controller version, yes.
-
atGrimson: Whoooo :)
Problem solved!
Thanks so much (...though you force me into 4 years worth of updates).
And atJKnott: well, yes, apparently there are some ifs ...if you update! Appreciate your input.
regards Chris
-
@chris-1028 said in Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch:
Ummm, I sort of disagree with your "there is no such thing as an untagged VLAN": try working with the UAP AC-Pro. Yes, all VLANs are in principle "tag-able": if you want to talk user data (to a Cisco switch or UAP AC-Pro) you tag, if you want to talk admin (to a UAP AC-Pro) you MUST untag the admin VLAN to talk to the AC-Pro. No ifs, no buts, no doubts.
The only way you're going to "untag" a VLAN is to assign it to a switch port. Everything connected to that port will see only frames from that VLANs as native LAN. However, that AC-Pro will then have no way to know what the original VLAN was.
With VLANs, you add the tag, which indicates the VLAN number. That is the only way a switch can separate the VLANs as needed.
-
@jknott said in Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch:
There's no such thing as an untagged VLAN
Be it you want to call it native or not - I can have multiple vlans on a switch that are all untagged, etc. So saying there is no such thing as untagged vlan is not true.. Seems like your wanting to bring up the age old semantics debate vlan or segment or subnet etc.. The term vlan is used to describe another L2 network, and quite often L3 - that ride on their own L2, etc. The terms are used interchangeable all the time.. And I can see how it could be confusing for the new users to networking, etc.
But saying there is no such thing as an untagged vlan is just not true... you add a vlan to a switch port, be it untagged or tagged, etc. Be it you want to call it native or untagged its still a vlan in the switch...
Seems the user was on REALLY OLD SHIT... since he mentions 4 years of updates... But for sure the you can run tagged vlan for management now on the unifi AP.
-
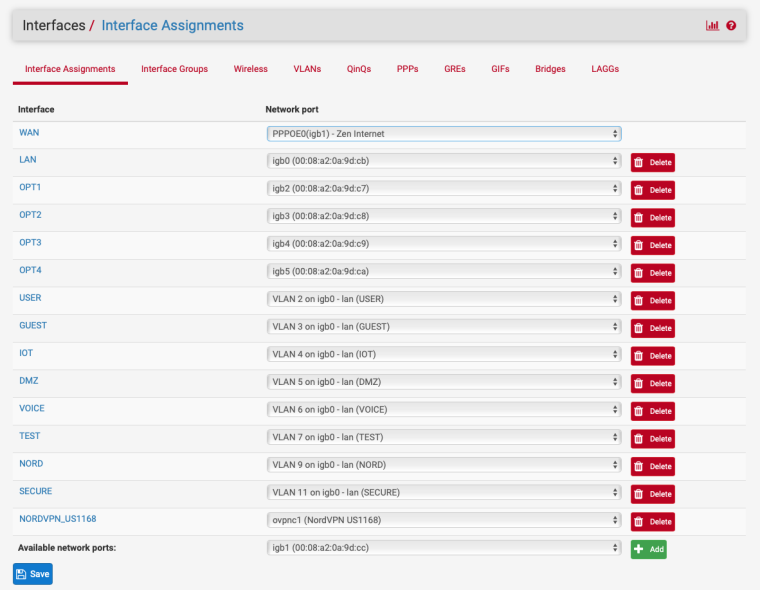
You could also change the default vlan from 1 to 3927.
The config looks like my Linksys switch config at one time Cisco owned Linksys.
-
@johnpoz said in Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch:
But saying there is no such thing as an untagged vlan is just not true... you add a vlan to a switch port, be it untagged or tagged, etc. Be it you want to call it native or untagged its still a vlan in the switch...
If you have multiple VLANs on a switch port, you need tags. Otherwise, you can have only 1 VLAN assigned to that port, as I mentioned above.
-
I am not saying I can put multiple untagged vlans on a switch port... What I am saying is on the switch I can create multiple vlans... And assign them to different ports.. Yes you can use the term native "vlan" etc.. But its still called a freaking vlan - in the makers of the switches own terminology.. So saying there is no such thing as an untagged vlan is just freaking nonsense.
I could have hundreds of different vlans - all untagged and isolated on the network and devices..
Be it its "tagged" in the switch and have an ID... is just semantics..
What do you say, you say its an untagged "vlan" or native "vlan" -- still called vlan..
-
Hmmm,
Be calm guys :)
Four years of missing updates is nothing: if you are looking for ancient $#1t ...that's me personified -- my firmware (wetware) dates from 1950 and has never been updated. If I could download updated wetware, I absolutely wouldn't.
My impending-implementation of pfSense is replacing a firewall appliance that is 16 years old and has not had an update for ... guessing ...4 years (again). Ooooh, it didn't log any attacks either.
Please all have a happy day -- this is a super reactive forum where really clever folk help others with an issue to find a clean solution fast.
In the nicest possible way: love you all. Chris
-
@chris-1028 said in Conflicting Admin VLAN requirements: UAP AC-Pro & Cisco switch:
Four years of missing updates is nothing: if you are looking for ancient $#1t ...that's me personified -- my firmware (wetware) dates from 1950 and has never been updated.
You can update that, it's called education and/or professional training. And if you really think that not updating security related equipment for years isn't a problem you are in dire need for good refresh.
-
Cool.
I've heard about that "education" stuff.
Never tried it personally :)Strictly, you are soooo right.
Factually, I'm behind two firewalls: nothing inbound (updated daily) talks to nothing inbound (ooops X years since f/w update but still no-inbound)
...with all "events" to independent (Rpi) log server)
...eventually
... to clients.
I guess at least not the worst of domestic networks
And I have only very acutely aware non-guest users.
YES guests are aliens, hence my intention to push them further away with the VLAN stuff.Hackable: sure.
Worse than signing up to FacescoopitallBook?
NoF1ng.Way!!!It is not couldn't-be-bothered to update inner f/w fw -- it is reduced confidence in inner f/w appliance: hence the move to pfSense -- at the very least I can now make my own mistakes in the inner f/w.
As of just now I (we the family) had 0.000 intrusions and lost $0.000 as a consequence in the last 5 decades.
Could that all change tomorrow?
Yes.
For you and for me.Fun to discuss, Chris
-
at Grimson,
Thanks much for your hint that ubnt allows management via tagged VLAN.
Since then (and before disrupting my network), I tried some research.
After hours spent on the ubnt site, I see many posts begging for a sysadmin-DEFINEABLE ({as in NOT-vlan1 and NOT-native-VLAN}) TAGGED management VLAN. It seems to have been implemented in ubnt switches, but I can't find any evidence that it is implemented in ubnt APs (or indeed for my specific case of UAP AC-PRO). The issue seems to have still been a "scandal" end-2018.
Do you have a pointer to release notes (or anything else?), concerning this capability? I've seen your posted (and annotated by you) screen-shot on their site, but not any accompanying claim that management is possible from an arbitrarily chosen TAGGED VLAN.
And yes, I agree that this is not a pfSense issue or your issue: just hoping you have the answer at the flick of a mouse. A simple NO from you, and I'll try asking ubnt.
regards Chris
-
It was for sure released for the AP... I run Pro and lite and LR on my home setup... I have not moved to tagged for management since i just don't have any need for it.
But it was for sure released, I am running 5.10.19 controller and 4.0.26 firmware on my AP... When I get a chance will change the management vlan for my AP to tagged, etc.
I currently run the AP and my eap-tls ssid vlan on the same untagged network.. Then multiple other ssid that are tagged. But I can see in the controller where I could switch it over to a tagged vlan without any issues.
Its not a big deal for many a network -- all comes down to if your greenfield and can adjust your network tagging or not.. If not a problem with running your management vlan untagged on the L2 your AP is connected to.. Who really cares if vlan X is tagged or untagged as long as its just the one vlan that is untagged.. The problem is when you need to run vlan XYZ as untagged for other reasons and you don't want to put the AP on that vlan so they need to be tagged, etc.
-
at Johnpoz
Thanks for that.
I'll give it a go (the worst fate is that guests have no access for a while, but then I don't get a million guests a day and I have an unlimited-data 4G modem if my occasional guests are "unhappy").
I am "greenfield" in a sense -- I have total and exclusive control over my networks and report only to myself in the event of a disaster (yeah, I might get some $#1t from Madame, but there is always the 4G modem to calm her down). I have elected to move to "my-net 3.0" -- my decision was unanimous :)
Why do I seek tagged admin?
Most VLAN attacks go for VLAN1, or failing which, go for native-VLAN. I ask myself WHY should I have VLAN1 or native-VLAN connected to anything at all ... let alone to the admin heart of the network -- just seems a silly choice!Off to the mountains for skiing: you wont hear from me for a week or two, but I'll report back.
Appreciate all the feedback so far.
regards, Chris