VPN blocked?
-
@gertjan so it really depends on how much you trust the one handling your envelope/DNS request.
By your reasoning, what is stopping the postman from opening and reading your mail. Nothing, but it is a relatively easy measure to put in place that provides a reasonable level of protection/privacy, but not full protection/privacy. The same could be said about DNS providers. Find one that appears to be trustworthy and use DNS over TLS/SSL and this will provide you with a reasonable level of protection/privacy for the effort involved.
The same could be said about VPN providers. Yes, it provides some level of privacy/protection in general, but the provider would still have the ability to see all of that data, and comes down to how trustworthy they are.
Is this fair/accurate?
@JeGr wait, so I want to make sure I follow what you were saying. So if I want to use DNS over TLS/SSL, I am running all of my lookup requests through 1 service, and they would have the ability to know what domains I am requesting. Correct? And it would just depend on how much I "trust" them with that data.
Conversely, it sounds like I could use unbound to lookup requests from the root servers. So the root servers would know what I am requesting from them, but not all of my queries. So they only see a piece of my traffic. Is that the idea?
-
@ryanm said in VPN blocked?:
t I am requesting from them, but not all of my queries. So they only see a piece of my traffic. Is that the idea?
If you do query minimization that yeah that would be true... So you would only ask the ROOTs for the NS of the tld your looking for say .com, then you would ask the .com NS hey I am looking for domain.com, you would only ask the domain.com NS for host.domain.com
Problem is that this sort of minimization breaks down and you will find that multiple things will fail to resolve.. Mostly because of odd ball cname configurations for the domain, etc.
If you are sending dns over tls to some service - then yes that service sees everything you ask for, you just handed them your surfing habits on a silver platter.. I am sure they are thankful ;)
And yes your vpn provider is going to see everything as well.. The thing I don't get is how come you distrust the company you actually pay for service so much, that your willing to pay for some other service that just because they say they don't log you trust them more?? makes Zero Sense to Me!!!
If your going to take this distrust model to its extreme - then you should only be using burner phones that you bought with cash.. And use of CC is just plain out the window because they see all your transactions. And to be honest you can not even go outside because their are camera's everywhere and more than likely your paying tolls electronically as well..
Be it Doh or Dot, you should really understand exactly before you go jumping on any such bandwagon if you ask me.. Keep in mine that your https traffic doesn't hide where you are going either because the domain your going to is going to be in the SNI in the clear..
-
@johnpoz It is a fair point John and I may re-evaluate my need for a VPN. It does add some frustration and nuance.
The way I understand the query minimization is that it keeps any single entity of seeing all of your browsing habits, at the expense of dealing with some resolving issues. With a single provider having the reverse pro/con. I suppose it is weighing convenience against privacy.
I do appreciate everyone's patience explaining these topics to me. It has been extremely educational.
-
I don't get this "rush to VPNs for privacy" thing either. It's like the VPN providers out there have used slick marketing to create a demand for their product. They get a potential goldmine of information from their users. They say they "don't log", but do you really believe that? Do you not realize that any provider in any Western democracy can easily be coerced via legal means to divulge everything about a user or even a group of users in the name of a criminal investigation or "national security". So if you are paranoid about "big brother" watching you, then a VPN provider is the very last thing you want because that just serves to draw attention to you. Why? Because the favorite haunt of cyber bad guys are services like VPNs and TOR. That's one reason VPN services have started to get on "bad reputation" IP lists.
My beef with VPN services is that folks jump into using them without understanding the true ramifications, then they come here and to other forums whining about various "broken" things wanting to blame it on other software. For example, it's not unusual for a user to post about some issue they are blaming on a pfSense bug; but, you finally drag it out of them 4 or 5 posts later in their rant about their problem that "oh, yeah, I am using VPN provider xyz" and it turns out that is the problem because these VPN IP net blocks are winding up on so many blacklists.
Finally, using a VPN bogs your firewall CPU down with encrypting and decrypting every single packet that traverses the wire. It also adds lots of latency to your connections as traffic has to bounce back and forth from your VPN provider's entry and exit points and your local ISP.
-
It seems I am having the same issue. I am currently using AIRVPN provider and I cannot open this forum.
Is it possible that the AirVpn ip addresses servers are blacklisted?
Thanks -
Spammers use VPNs....so they all get blacklisted bit by bit.
-Rico
-
Fair enough even if criminals use cars, mobile phones, computers but all of those can still be bought
 ... I am a newbie and i am wondering if someone would be able to tell me if (and how eventually) I can bypass the VPN connection to connect to the pfsense forum without having to change network.
... I am a newbie and i am wondering if someone would be able to tell me if (and how eventually) I can bypass the VPN connection to connect to the pfsense forum without having to change network.
Thank you very much -
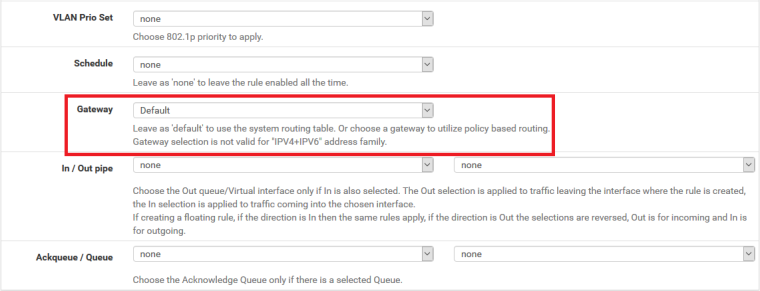
Depending on your VPN Setup it should be no problem to policy route by setting destination IP to 208.123.73.199 (this forum) and choosing your default gateway (Advanced options in the Firewall Rule).
-Rico
-
@zapoteknico said in VPN blocked?:
Fair enough even if criminals use cars, mobile phones, computers but all of those can still be bought
 ...
...Right but if you choose to drive a car that was just used in a bank robbery you'll get pulled over.
-
Hello Rico.
Thank you very much.
I understand what you say however I have no understanding of how I would be able to achieve that in pfesense.
I understand i might be asking a lot but any help in pointing me to how to create thoae rules would really help -
@derelict indeed... However the difference here is the brand of the car, not exactly the same car...if a Mercedes is used in a bank robbery, not all Mercedes drivers will be stopped

-
You create this Firewall Rule for the Interface you want to bypass forum.netgate.com (typically LAN) and put on top of your Rules:
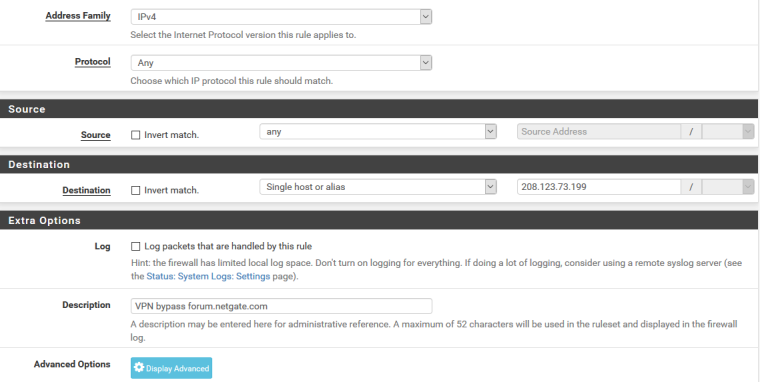
hit Display Advanced and set your ISP Gateway (or default if your ISP GW is still the system default):
-Rico
-
If your going to policy route, make sure your not pulling routes from your vpn service - most of their crap guides want you to pull their route so they are default, and most of them mistakenly tell you to do manual outbound nat, etc.
-
Thank you very much for the help but i am surrendering.
I understand half of the things you talk about and I think i have rules setup that makes impossibile to create those exemptions (followed the above suggestions but it didn't work)
I don't want to bother anyone more than needed as I am going to reconfigure everything tomorrow (getting a new mini pc)Thank you :)
-
This post is deleted!