Strange behavior. IP ending with .2 works, ending with .3 not.
-
Hey guys,
I'm running an OpenVPN Server on a pfSense for road warriors. And I have a reeaally strange problem since a couple days:
13:12:34.338995 IP 10.225.226.3 > 10.225.226.1: ICMP echo request, id 14, seq 1, length 32 13:12:35.332080 IP 10.225.226.3 > 10.225.226.1: ICMP echo request, id 14, seq 2, length 32 13:12:36.331939 IP 10.225.226.3 > 10.225.226.1: ICMP echo request, id 14, seq 3, length 32 13:12:51.894961 IP 10.225.226.2 > 10.225.226.1: ICMP echo request, id 2, seq 1214, length 40 13:12:51.894967 IP 10.225.226.1 > 10.225.226.2: ICMP echo reply, id 2, seq 1214, length 40 13:12:52.913033 IP 10.225.226.2 > 10.225.226.1: ICMP echo request, id 2, seq 1215, length 40 13:12:52.913036 IP 10.225.226.1 > 10.225.226.2: ICMP echo reply, id 2, seq 1215, length 40 13:12:53.913385 IP 10.225.226.2 > 10.225.226.1: ICMP echo request, id 2, seq 1216, length 40 13:12:53.913389 IP 10.225.226.1 > 10.225.226.2: ICMP echo reply, id 2, seq 1216, length 40When I'm connecting to the VPN as the first client, recieving IP 10.225.226.2, it works flawless. However, when I'm connecting and recieve the IP 10.225.226.3, it stops working. I can't even get a replay from the VPN Gateway (10.225.226.1) or anything.
This happens on multiple devices, with multiple configs. I even created a second roadwarrior vpn by the wizard, with a different transport network and it still doesnt work for the IP ending with .3.
I have checked the logs when logging in, it all looks the same, for both IPs, and it shouldn't work ever, if theres a wrong configuration I guess.
I have firewall rules to pass any on the openvpn Interface and the corresponding road warrior interface.
I hope someone has an idea :)
Regards
-
Show your OpenVPN settings and Firewall Rules (screenshots).
Do you maybe share the same cert for all Users in SSL/TLS mode?-Rico
-
hey Rico,
here are the screenshots
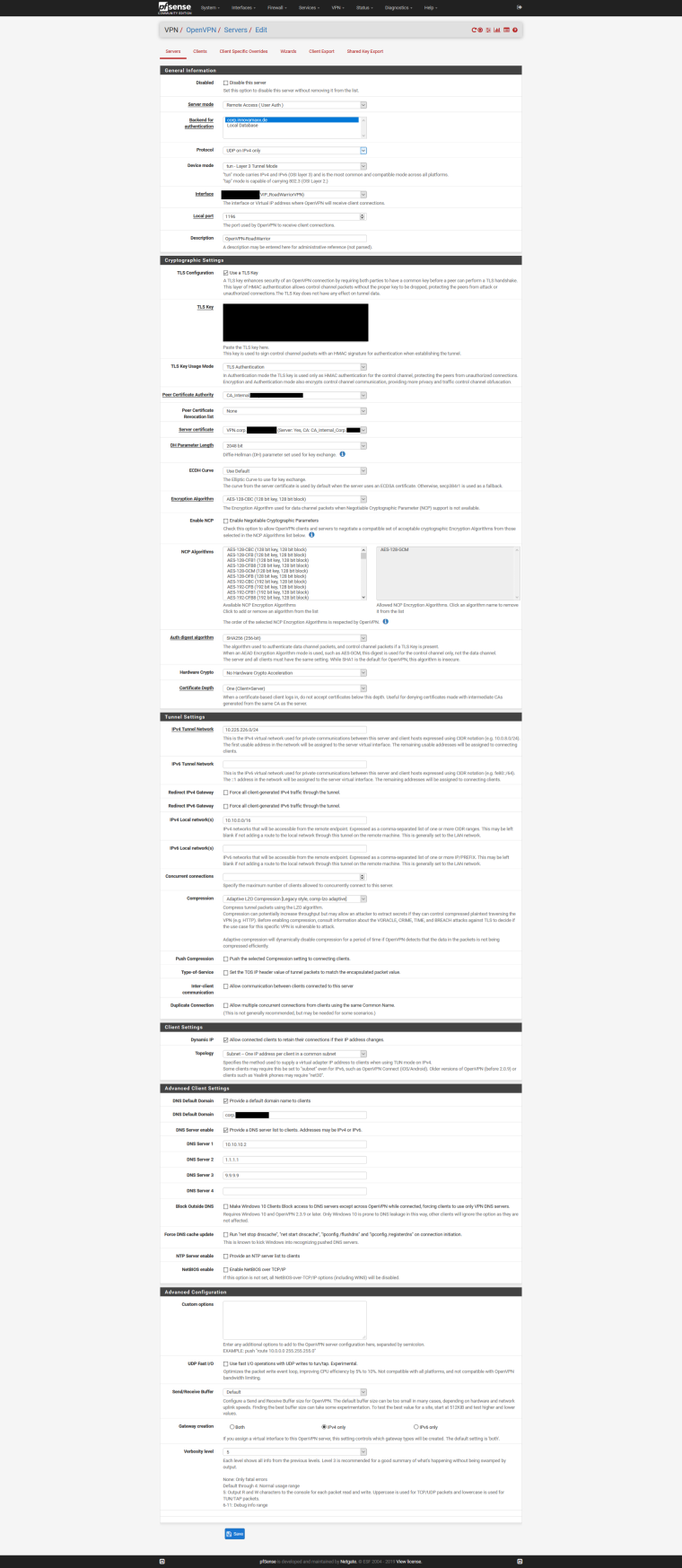
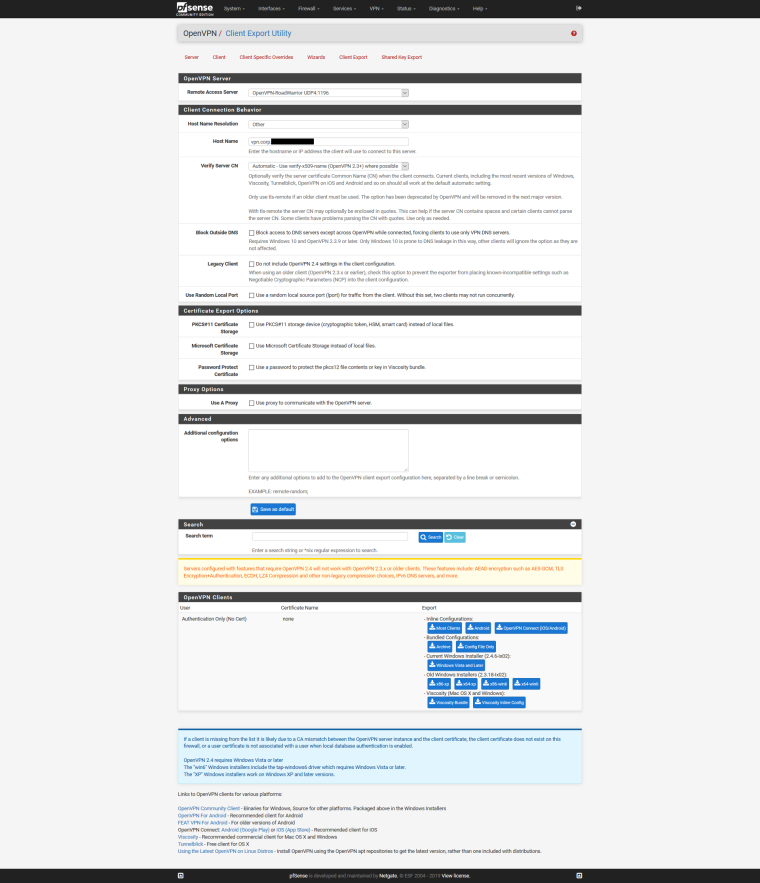
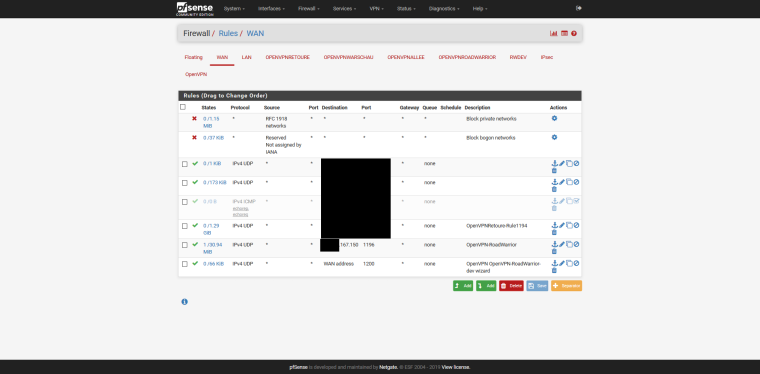
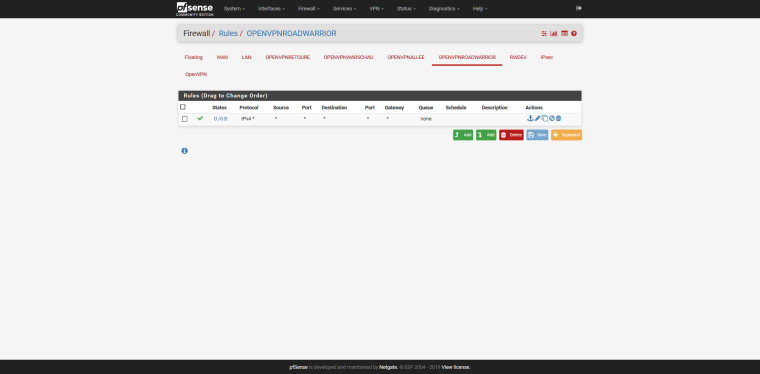
thank you for your time :)
-
Looks OK to me.
How about the routing table?
I see you added the OpenVPN RAS as Interface...did you maybe add any strange setting to this interface?-Rico
-
Routing tables Internet: Destination Gateway Flags Netif Expire default ......167.145 UGS ix1 5.28.101.167 .....167.145 UGHS ix1 10.3.103.1 link#11 UHS lo0 10.3.103.2 link#11 UH ovpns2 10.5.105.1 link#17 UHS lo0 10.5.105.2 link#17 UH ovpns6 10.6.106.1 link#14 UHS lo0 10.6.106.2 link#14 UH ipsec100 10.10.0.0/16 link#1 U ix0 10.10.10.12 link#1 UHS lo0 10.102.202.1 link#13 UHS lo0 10.102.202.2 link#13 UH ovpns1 10.104.204.1 link#15 UHS lo0 10.104.204.2 link#15 UH ovpns4 10.225.226.1 link#12 UHS lo0 10.225.226.2 link#12 UH ovpns3 10.227.228.0/24 10.227.228.2 UGS ovpns5 10.227.228.1 link#16 UHS lo0 10.227.228.2 link#16 UH ovpns5 78.88.188.166 212.36.167.145 UGHS ix1 127.0.0.1 link#8 UH lo0 192.168.1.0/24 10.6.106.2 UGS ipsec100 192.168.155.0/29 10.102.202.2 UGS ovpns1 192.168.165.0/29 10.102.202.2 UGS ovpns1 192.168.202.0/24 10.102.202.2 UGS ovpns1 192.168.203.0/24 10.3.103.2 UGS ovpns2 192.168.205.0/24 10.104.204.2 UGS ovpns4 192.168.206.0/24 10.5.105.2 UGS ovpns6traceroute to 10.225.226.3 (10.225.226.3), 64 hops max, 40 byte packets 1 .....167.145 (.....167.145) 1.333 ms 39.956 ms 0.322 ms 2 *** [2.4.4-RELEASE][root@FW01.corp]/root: traceroute 10.225.226.2 traceroute to 10.225.226.2 (10.225.226.2), 64 hops max, 40 byte packets 1 10.225.226.2 (10.225.226.2) 11.706 ms 10.196 ms 9.799 ms [2.4.4-RELEASE][root@FW01.corp]/root: traceroute 10.225.226.3 traceroute: findsaddr: failed to connect to peer for src addr selection.When I add a static route (10.225.226.0/24 via 10.225.226.1) it says "failed to connect to peer for src addr selection." upon tracerouting. Without the static route it simply tries to route that through the ISP Gateway (...167.145), instead of the OpenVPN one
dev ovpns3 verb 0 dev-type tun dev-node /dev/tun3 writepid /var/run/openvpn_server3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local .....167.150 tls-server server 10.225.226.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server3 verify-client-cert none username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user Y29ycC5pbm5vdmFtYXh4LmRl false server3 1196 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'vpn.corp.......' 1" lport 1196 management /var/etc/openvpn/server3.sock unix push "route 10.10.0.0 255.255.0.0" push "dhcp-option DOMAIN corp....... push "dhcp-option DNS 10.10.10.2" push "dhcp-option DNS 1.1.1.1" push "dhcp-option DNS 9.9.9.9" ca /var/etc/openvpn/server3.ca cert /var/etc/openvpn/server3.cert key /var/etc/openvpn/server3.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server3.tls-auth 0 ncp-disable comp-lzo adaptive persist-remote-ip float topology subnetBasically it's really just the IP. 10.225.226.2 works without problems. On any device. As soon as a device gets the 10.225.226.3 or higher, it just doesn't work anymore. If the device had .2 before, it worked during that time too, but up until it gets the .3
-
I also noticed, when I create a new server on a different port, with the exact settings (wich worked before all this began to happen), and that new server also has the exact same problem. I created a tunnel network 10.226.227.0/24, and as soon as someone gets the .3 or higher, it doesnt work.
-
Any overlapping IPsec networks?
-Rico
-
No there were not.
I have deleted everything related to the RoadWarrior Server now and recreated it with another cipher, but same settings/TunnelNetwork/Buffer/Rules. It seems to work now. Could it be that pfSense sometimes doesn't activate rules unless you recreate them? It felt like that, though I dont really know why it didn't work and now works.