Struggling to get VLANs working properly
-
I have an HA setup. The primary network runs untagged. There is VLAN 18 which the voice vendor has setup and routing. I'm trying to setup a second data VLAN and I'm not sure where I'm hitting the wall. This VLAN is going to be used for wireless devices which attach to various Meraki WAPs. On the Cisco 2960 switches, all Merakis are attached to a trunk port and a sample config looks like this:
interface GigabitEthertnet 0/25
switchport mode trunkOn the pfSense HA firewalls, I created a VLAN interface, assigned them and created a CARP IP. On a switch, I can ping the CARP IP just fine.
On my firewall rules, under my VLAN interface, I have source VLAN Net to any and a rule to allow LAN Net to VLAN Net. I setup a DHCP Relay on each firewall to point to a local Windows DHCP server with a scope setup and it's active.
On the pfSense firewall, I can ping using the CARP IP source out to the internet so it looks like NAT is working just fine.
On the Meraki side, I setup an SSID, tagged it 400 (the VLAN tag setup on all switches and pfSense). When a client attempts to join, it cannot pull an IP address and it errors out.
With such a mixed environment, I'm not sure where the problem could be. I've worked exclusively in all single vendor networks and never encountered an issue like this before. Can anyone point me to where it sounds like the issue could be? Maybe Meraki? I know their stuff can be a little challenging with non-Meraki stuff.
Thanks!
RESOLVED: There's a managed Cisco SG300 sitting in front of the LAN ports filtering out the tagged traffic. I am working on this remotely so I was only able to hit this realization once I got pictures of the location.
-
802.1q is 802.1q
Post your Interfaces > Assignments, Interfaces > VLAN, and Firewall > Rules, VLAN.
-
I would verify syncing between nodes is happening properly (you mentioned you set up the relay on both nodes, in theory, shouldn't have to do that if the syncing is working). I would then verify that the active node matches what you think is active. Next would be verifying the trunks to both nodes are up and functioning in trunk mode. Are you pruning unused VLAN's on your trunks? If so, next would be verifying you're allowing VLAN 400 on all your trunks. After that, examine the results of "sh int trunk" and make sure it aligns with everything you just verified.
Next would be re-verifying that the DHCP relay is configured on the correct interface and pointed at the correct IP.
Last but not least, have you verified that the new scope is enabled on the DHCP server?
Of course, this all assumes the VLAN was created on the correct parent interface to begin with and has the proper firewall rules to allow communication. My suggestion would be to add an any/any rule to the interface until basic IP communication is established.
If no smoking gun presents itself after all of that, then you're looking at running packet captures to determine where the traffic is being sent. You may even need to do a capture on the DHCP server itself to determine if the traffic is making to its destination and if so, checking the DHCP logs to determine what the server is doing the discovery requests.
-
Here's the screenshots as requested:
Firewall rules:
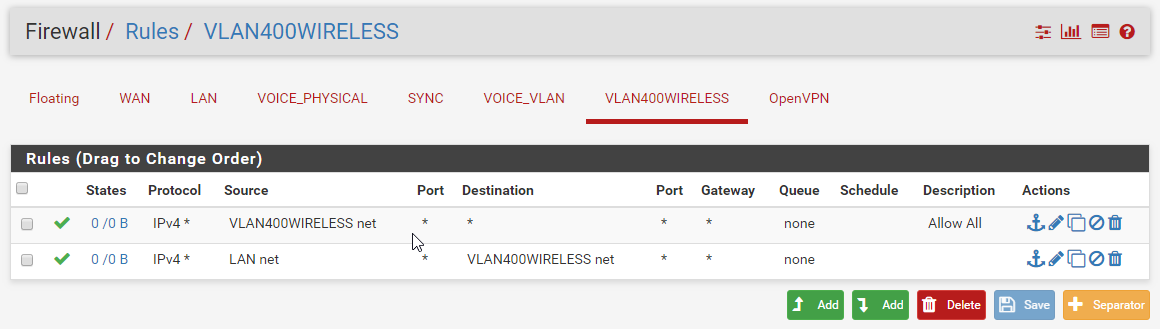
Interface assignments:
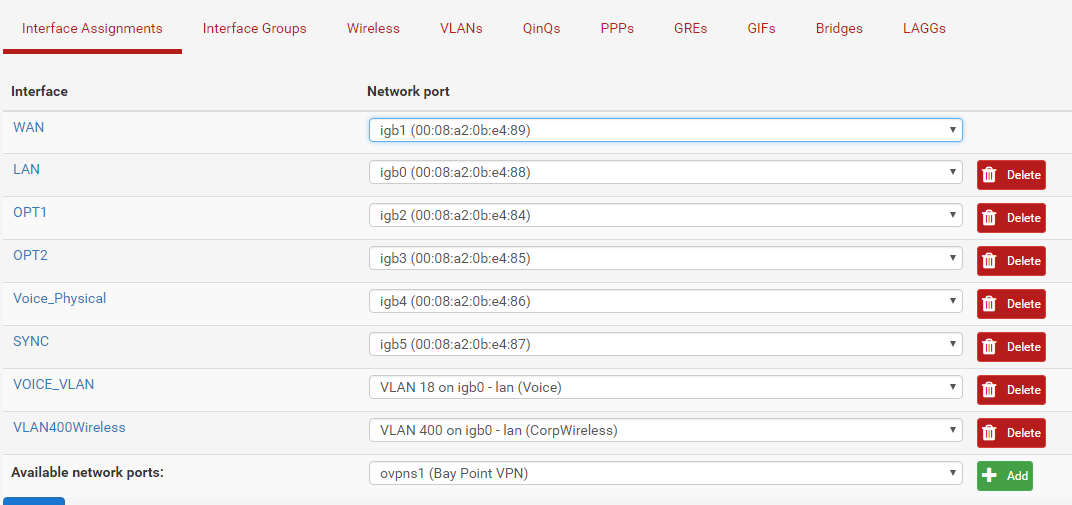
VLAN assignments:
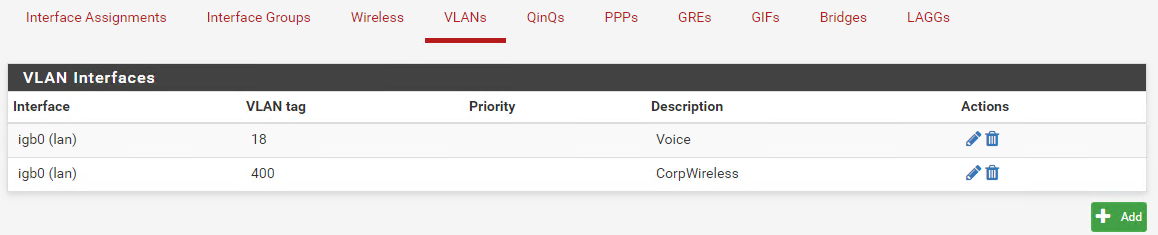
Route table:
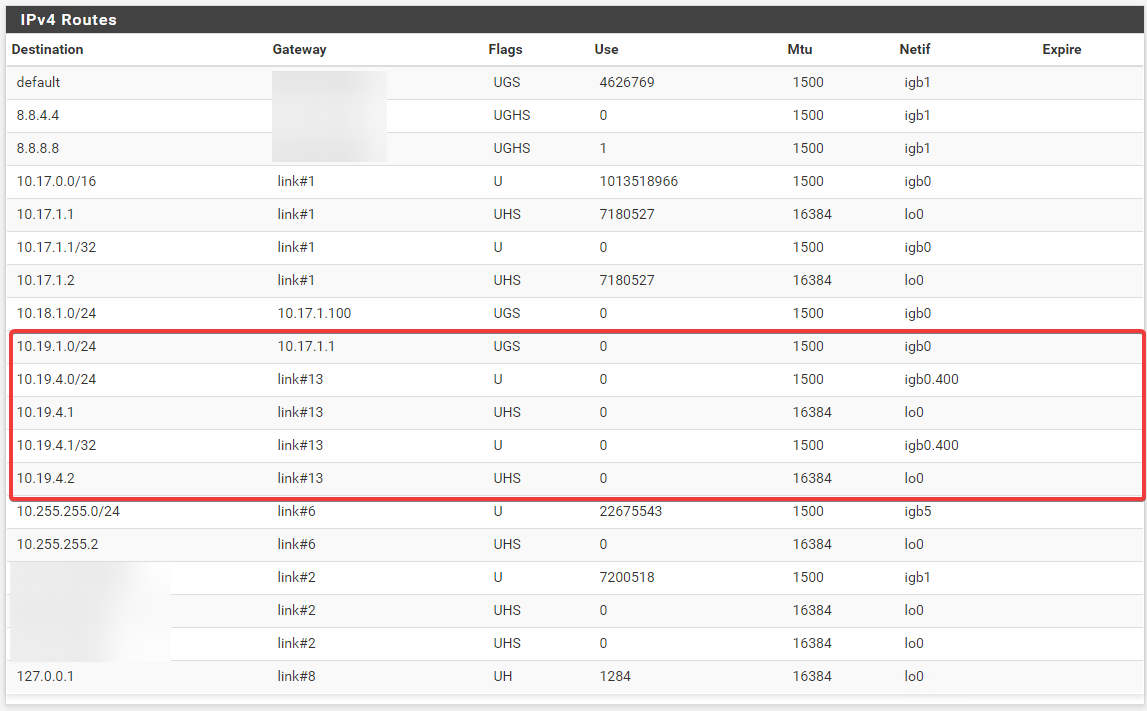
I'm not sure where the 10.19.1.0/24 IP is coming from in the route table as I can't find this anywhere.
Just a note about VLAN 18, I wasn't able to get this one working either but the telecom vendor had their own preferred method
Here's a config from one of the Cisco 2960 switches:
interface GigabitEthernet0/13 description Meraki Uplink Ports switchport mode trunk ! interface GigabitEthernet0/14 description Meraki Uplink Ports switchport mode trunk !I've verified the scope is enabled on the DHCP server. The only thing that is different is the second firewall doesn't have the VLAN 18 interface on it and it's reporting VIP errors:
Interface specified for the virtual IP address 10.19.4.1 does not exist. Skipping this VIP.Would this be causing this issue even though I can ping 10.19.4.1 from all the switches?
-
There is no interface configuration for VLAN 18 (VOICE_VLAN).
There should be an interface address and subnet on igb0.18. There is not.
Did you enable and number that interface and add firewall rules on it?
You will never have traffic arriving on VLAN400Wireless with a source of LAN net so that rule is useless.
Does VLAN 400 exist in the switch's database?
Is VLAN 400 tagged to the interface connected to igb0?
You have igb0 configured for tagged and untagged traffic. The switchport connected to it will have to be configured the same way.
Looks like you've been pretty clicky clicky there. Did you not make a gateway on LAN for 10.17.1.1 and a static route for 10.19.1.0/24 to it? (System > Routing)
-
@Derelict said in Struggling to get VLANs working properly:
There is no interface configuration for VLAN 18 (VOICE_VLAN).
There should be an interface address and subnet on igb0.18. There is not.
Did you enable and number that interface and add firewall rules on it?
Not worried about VLAN 18 - it's being handled through a VPN router to the telecom vendor. This was never cleaned up.
You will never have traffic arriving on VLAN400Wireless with a source of LAN net so that rule is useless.
Ok, I added this rule just for troubleshooting purposes. I have removed it.
Does VLAN 400 exist in the switch's database?
Yep, it's been added to every switch on the network.
Is VLAN 400 tagged to the interface connected to igb0?
You have igb0 configured for tagged and untagged traffic. The switchport connected to it will have to be configured the same way.
Looks like you've been pretty clicky clicky there. Did you not make a gateway on LAN for 10.17.1.1 and a static route for 10.19.1.0/24 to it? (System > Routing)
That may have been previously added. The only static route now is 10.18.1.0/24 to the telecom provider's router.
I've attempted to do a ping 8.8.8.8 source 10.19.4.200 (added a vlan interface to the switch) and nothing is getting through.
-
Where is the configuration for the switch port connected to pfSense?
Do you packet capture out the interface the pings should be egressing on? Are they there? Is there a response?
If you have removed things I have pointed out you should provide new data.
I've attempted to do a ping 8.8.8.8 source 10.19.4.200 (added a vlan interface to the switch) and nothing is getting through.
So what is the switch's default gateway? When you packet capture on LAN do you even see those pings? Did you make changes to outbound NAT?
-
I see a couple of things:
-
Your VLAN's are terminated on PFsense, so when the AP's dump traffic on the wire, all inter-VLAN traffic has to traverse the firewall. Since you have a DHCP relay configured, at a minimum, we should see DHCP traffic hitting the firewall upon every connection to the AP and getting forwarded to the DHCP server, but look at the rules on your VLAN400WIRELESS tab. Both rules have 0 hits, which means traffic is not even getting to the PFsense.
-
It looks like your trunk configs are incomplete. If you examine the results of "sh int g0/13 switchport", you will probably notice those ports are currently operating in "static access" mode instead of "trunk". Your switchport configs should look something like this:
interface GigabitEthernet0/13 description Meraki Uplink Ports switchport trunk encapsulation dot1q switchport mode trunk spanning-tree portfast trunk ! interface GigabitEthernet0/14 description Meraki Uplink Ports switchport trunk encapsulation dot1q switchport mode trunk spanning-tree portfast trunk !Re-configure your trunk ports then bounce both links.
The same config should be on the trunk to PFsense also.
-
-
I got this figured out finally. I'm working on this from about 700 miles away so I was lacking some crucial documentation which I got when I asked for some pictures of the network rack. There's a managed Cisco SG300 switch that connects the pfSense firewalls which has never been configured. I thought I was going crazy when sh cdp neighbor was only showing a single MAC and not two firewalls. I had assumed both firewalls were plugged directly into the Catalyst 2960 which had a left over port description that wasn't updated.
Thanks all - we are good!