Odd issue accessing local webserver
-
I thought I would post images of various settings
Please excuse any ugly firewall settings, as I started going ham on some of the settings, trying to figure out where a problem could be.
I was under the assumption at first that it must be a firewall issue.These are all the interfaces
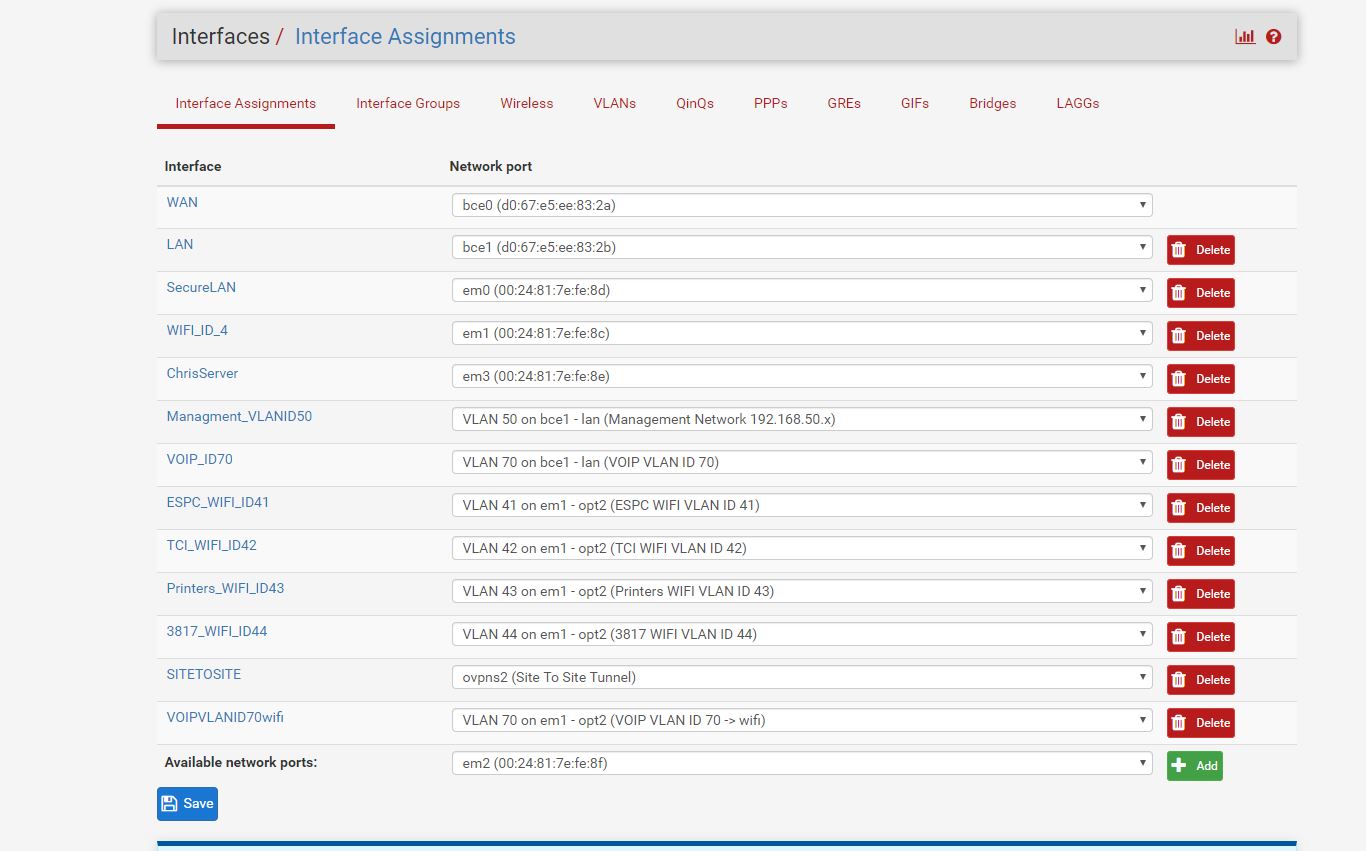
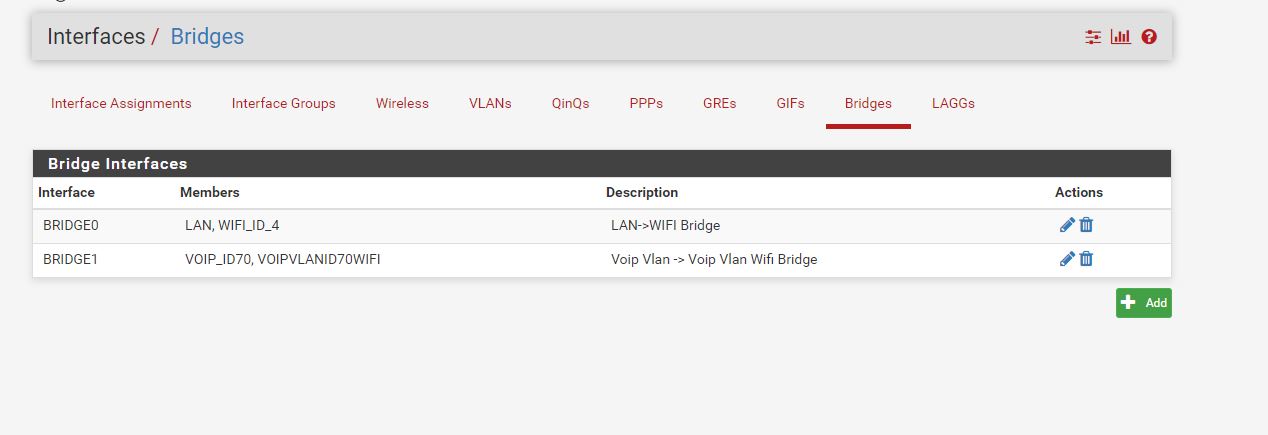
These are the bridges
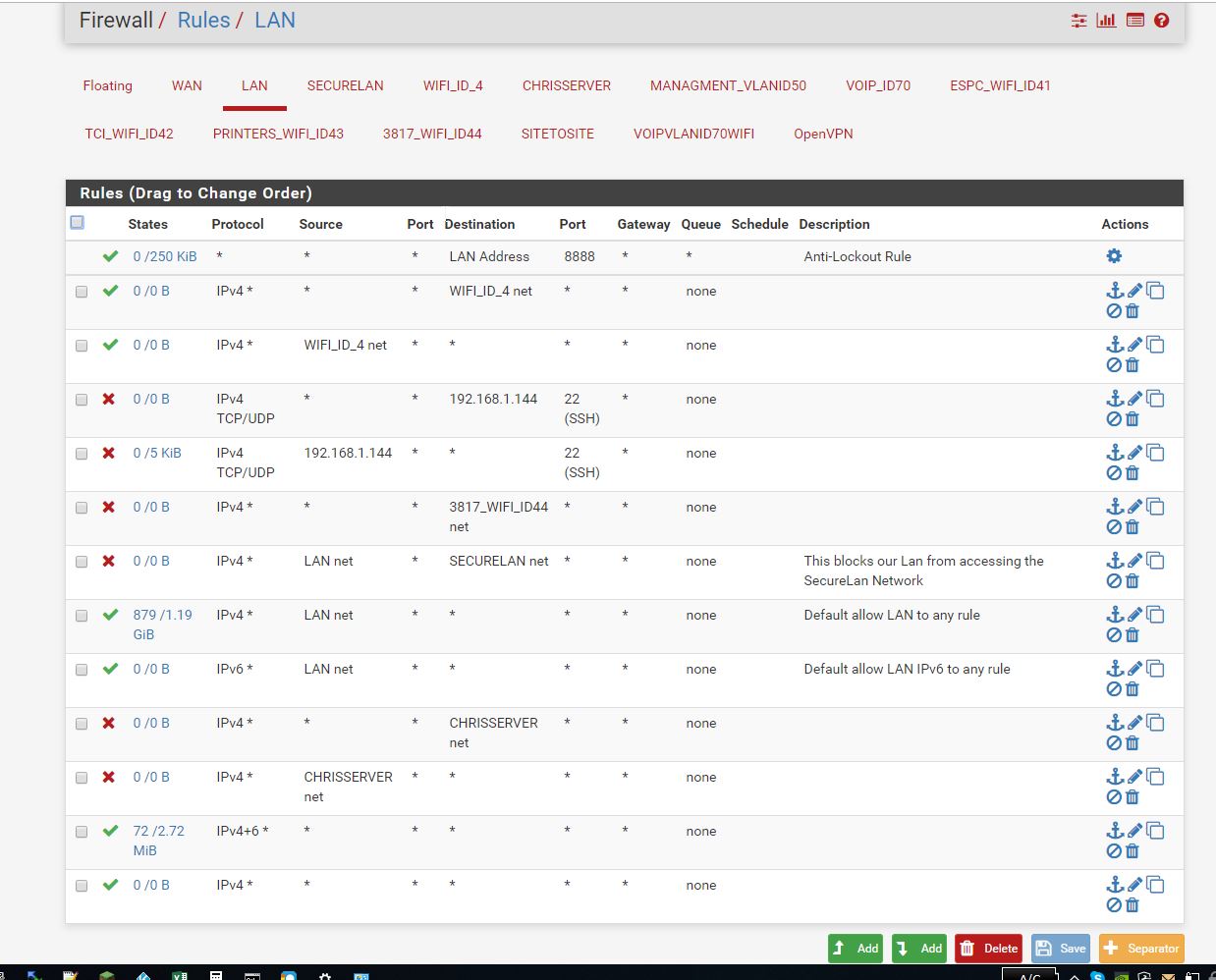
These are the LAN firewall settings
These are the WIFI interface firewall settings.
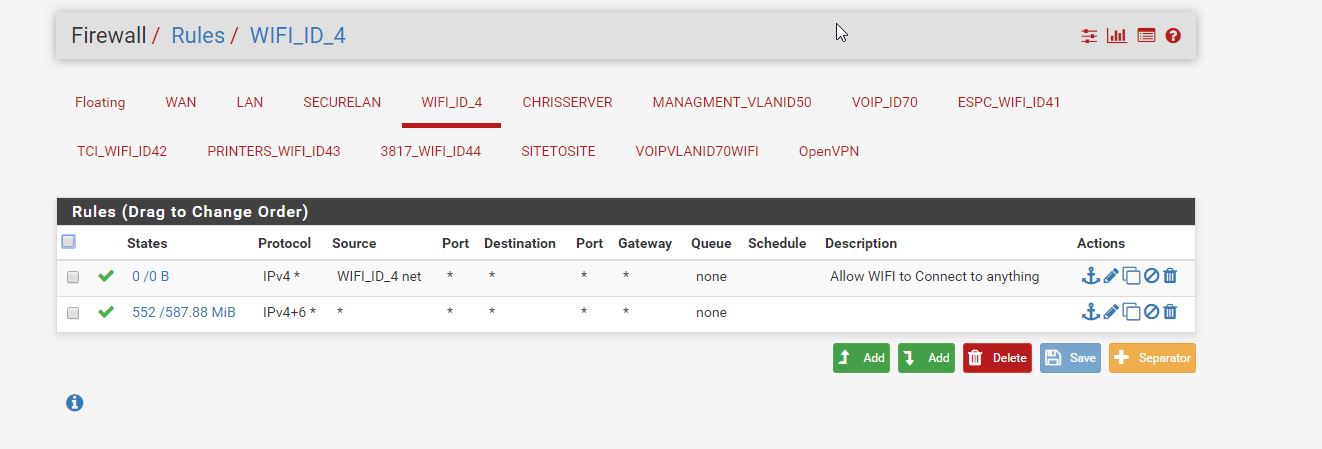
Keep in mind, the SSID I am currently using, should go directly to this interface and skip any vlan interfaces etc.
However I can post the vlan and other firewall settings etc if needed, but those vlans do have access to the webservers without any issues, so I dont think they are involvedPlease excuse me any moderators, if I am posting in the wrong section or something, I am not very familiar with this forum feel free to move my post etc
-
@RigidConduit said in Odd issue accessing local webserver:
I have bridged the wifi interface to the lan interface.
Why would you do that?? If the devices are suppose to be the same vlan then do that, why would you bridge the interfaces?
-
Like I said, being a DIY, I may have misunderstood some things.
But to understand what I did there...
For testing purposes, I built an ssid that I wanted to show up as a lan device
Aka 192.168.1.XXX device connecting to a 192.168.1.XXX server but through a wifi connection for example.
So it was my understanding that I would need to run a bridge between the two interfaces, and leave this special SSID with no vlan tagging.
And it seems to function as I thought it would.I had used this lan before for screwing around, and diagnosing issues when setting things up like a wireless printer on its own vlan connecting to a windows server running on a different vlan, etc etc.
It has proved handy in the past, and if i turn on the original intended vlan on this wifi ssid, I'm sure it will all the sudden operate properly.
However, I am more curious as to why it doesn't work with any web server at the moment.
More for better understanding/learning purposes than anything else.The rest of the ssid's are indeed set up for separate Vlans, (some vlan's have access to certain services, others don't). And they operate properly despite the bridge.
I am open to criticism though, let me know.
Edit - Note: Just for informational purposes. The lan interface connects to a series of normal switches, while the wifi interface connects to a POE switch that runs any special hardware like phones and wifi access points requiring POE. I did it this way, just because I guess. I wanted wifi on its own interface that I could have complete control over if I wanted.
-
If you want an untagged SSID to be on your lan vlan, then do that.. Your saying the AP is directly connected to your pfsense interface? Why would it not be connected to your switch infrastructure?
-
I added the above note to the last post but after you replied.
But it seems to be related to your response.
The lan interface connects to a series of normal switches, while the wifi interface connects to a POE switch that runs any special hardware like phones and wifi access points requiring POE.
I did it this way, just because I guess. I wanted wifi on its own interface that I could have complete control over if I wanted.But you are correct in terms of simplicity, and my original setup was just everything linked together on one interface.
Despite all that, I am still puzzled as to why one particular service doesn't work with the above-listed setup.
But being a hard headed person, wanting to know why something doesnt work, I have been trying to investigate the issue.
However I could easily resolve it, I'm just stuck on one of my "question everything" rampages lol, and really want to resolve this for the sake of learning why it broke in the first place.
It is usually how i learn things, my method tends to be, break something accidentally, figure out why it broke, then resolve it. -
I assume someone might know the problem off the top of their head.
However, I can just leave it be if it is a waste of everyone's time.
But as they say, curiosity killed the cat lol. -
You don't have enough info really to help you.. Your filtering on the specific interfaces and not the bridge interface, since you don't seem to have assigned one? But you don't list that other interfaces firewall rules, etc. Or I missed them?
https://docs.netgate.com/pfsense/en/latest/interfaces/interface-bridges.html
I wouldn't software bridge like that.. Just create an uplink from your switch to the other switch that will carry a specific vlan
Having a hard time figuring out what your trying to do here, you have 2 different bridges but the same physical interfaces are in each bridge.. You have that 70 ID on bce1 and em1?
Makes no sense - sorry!
-
You are correct, I do not have a bridge interface setup.
The picture listing the interfaces is indeed up to date.
So you didnt miss anything.I set these bridges up and they seemed to operate correctly as is.
So I hadn't gotten as far as adding an interface for the bridge.
And was unsure of what it would provide or not provide in terms of functionality if I indeed added the interface for the bridges.
But I did notice the option in the past
I assume it allows me to do some filtering between the two connections in the bridge? o.0
I will look into it.Otherwise, for the "I wouldn't software bridge like that" comment, I assume this method is not best practice or maybe just part of me misunderstanding.
"Having a hard time figuring out what your trying to do here, you have 2 different bridges but the same physical interfaces are in each bridge.. You have that 70 ID on bce1 and em1?"
yes, and should probably be deleted, after thinking about it, it does indeed seem like a redundancy.
Thanks for pointing it out.I think I probably have a lot more studying to do into bridging and its purpose, I may have misunderstood it entirely I guess.
It has been 12+ years since my old networking classes, and I think I did a lot of assuming on how things work in pfsense when it comes to interface to interface interaction. -
Bridging on your router/firewall is never going to be "best" anything... Your trying to use a router interface as a switch port.. Pointless waste of a good interface..
Unless you has some specific need to filter part A from part B of the same L2 kind of zero point to using your router interfaces as switch ports.
You have not made any mention of any change in media type, another reason you might bridge on pfsense... Say you had fiber connection and ethernet and only place you could join these L2 sections via these connections were on your bridge.
I would remove your bridging and do it on your switches ;)
-
@johnpoz said in Odd issue accessing local webserver:
Bridging on your router/firewall is never going to be "best" anything... Your trying to use a router interface as a switch port.. Pointless waste of a good interface..
I would remove your bridging and do it on your switches ;)
Yes very true, and I'm guessing, it is possible that the switches might be even faster/more efficient at the task anyhow.
@johnpoz said in Odd issue accessing local webserver:
You have not made any mention of any change in media type, another reason you might bridge on pfsense... Say you had fiber connection and ethernet and only place you could join these L2 sections via these connections were on your bridge.
I have been tempted to use pfsense to serve as a router on a 10g network I am running in between two servers. I could see where this point makes a ton of sense, especially if I wanted that 10g network to have access to the rest of the world. Or using optics to extend the network into a much farther point of the network. Or point to point connection between buildings etc.
@johnpoz said in Odd issue accessing local webserver:
Pointless waste of a good interface..
While I have you here, this question would be on a separate subject.
And is mostly for curiosity sake on best practices.
I have that "Secure Lan" that you see there on the interface list.
This network needs to be entirely separate from the rest for security reasons, its best to pretend it is a network that has a million hackers running around in it.. lol
As a result, I ended up using another interface and then firewalling it away from everything but the internet.
I did this because I was worried about someone managing to somehow get some data through "cross-contamination. " for lack of a better wordMaybe sniffing packets or something else, but my goal was to ensure it couldn't touch anything else.
Would you consider this a waste of an interface?
And are there any best practices for this goal, or was I in the right direction for what I am thinking?
Just to be clear, it is actually a network that is indeed a concern for hacking due to the purposes it serves, and I was intending on making sure I provided security from it being able to touch anything else in any creative way someone might try.
Edit: grammer -
No that is a router interface - if you then bridged that to some other interface you defeated the whole point of your segmentation.
If you take the paranoid to the next level that whole L2/L3 network is on its own switching infrastructure as well, no vlans on the "fear" of vlan jumping... But are you really in a dod type setup here? ;)
Yes segmentation of your network is whole point of firewall/router - but your trying to use its interfaces as switch ports when you bridge..
If you want "switch" ports on your router - then get a router with built in switch, the sg3100 for example has switch ports.
Did you say that your lan interface connects to "dumb" switches - but then your bridging vlan 70 (tagged) to these dumb switches??
-
Ah no sorry, I should have been clear with some of those comments.
The Secure Lan stays far away from any bridging and just to be safe I have directed the firewall to block all communication with the other networks
And this network runs a cable straight from the router interface into the server that is providing the service, no switching or interconnection anywhere.
To stay vague here, It has to deal with money..
So for me, DOD level paranoid, totally justified, at least in my mind XDso overall I ran a cable straight from the server -> an interface on the router -> internet, with firewall explicitly blocking any other internal network just in case they could talk to each other.
as for "Did you say that your lan interface connects to "dumb" switches - but then your bridging vlan 70 (tagged) to these dumb switches??"
No, they are smart switches, and at the time of setup (im sure it was misunderstanding) some of the phones ran off their own power plugs and thus did not connect to the POE switch on the wifi interface
And thus to be sure they functioned, bridged them just in case I needed too as I was in a rush to rebuild after a hardware failure, and decided to change some things along the way due to curiosity lol. A sort of " I wonder if I can do this instead" momentRealistically, its the first time I am actually using the bridging feature on pfsense.
But yes the original setup was all wifi, lan, and voip vlans through one interface, and using the switches to sort out who gets what.
Edit: I need to stop blasting through these posts, and start proof reading lol. Edited for grammar -
@RigidConduit said in Odd issue accessing local webserver:
Realistically, its the first time I am actually using the bridging feature on pfsense.
For zero value add... You have not actually stated a reason on why your trying to do it.. Use your switch ports for switch ports.. Use your router interfaces for that.. Not switch ports.
I can see no value add to what your attempting to do with bridges vs adding complexity.