openvpn server connected to lan, no internet
-
so im routing all lan and wan traffic thru a VPN service as per this guide ( https://airvpn.org/topic/17444-how-to-set-up-pfsense-23-for-airvpn/ )
it works fine, but i've also set a openvpn server up on pfsense to access local network remotely, which is working (can ping and connect to devices) but there is no internet.
I'd like to run the remote clients traffic through the vpn, and out the VPN's wan
I found a similar setup ( https://www.reddit.com/r/PFSENSE/comments/9mvgma/openvpn_server_no_internet/ ), checked their mistakes against mine, and still nothing
Doesnt work on a 4g LTE network with android either
-
vpn server
 link text
link textvpn server

-
vpn server

-
ok everything is being flagged as spam even if I post a single image at a time?
-
client conf

-
wan

lan g

-
nat outbound

openvpn

-
print route

ipconfig

Ill take a screen cap of aliases later, but its just the lan ip and the vpn IP in an alias
all other ports are just like the airvpn guide.
any help would be appreciated, im at a loss
-
I am using AirVPN also and have this scenario working. There are a few things that need to be in place, most of which look like they are already done. The issue you're having is due to the rules on your OpenVPN tab.
On the OpenVPN tab, notice that all traffic from your remote access server is being matched by the any/any rule and routed according to the routing table, which will send internet traffic to the next hop in your default route and out your WAN if the NAT's are in place. Also, there are no rules that explicitly tell PFsense to route only internet traffic thru AirVPN.
I achived the objective by configuring two different rules on the Firewall -> Rules -> OpenVPN tab:
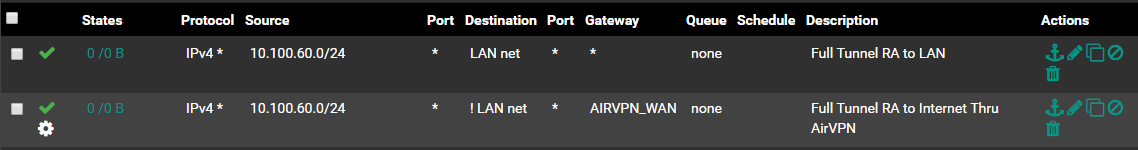
The top rule passes all traffic sourced from my tunnel network and destined to my LAN. The bottom rule passes all traffic sourced from my tunnel network and destined to anything but my LAN (i.e. the internet) and then policy routes it thru AirVPN. This is accomplished by clicking the "Invert match" box on the destination. Obviously, if you have multiple interfaces/subnets/VLAN's you will need to use an alias, but you get the idea.
The last step would be to add a NAT on the AirVPN interface for traffic sourced from your remote access tunnel network, which I believe you have already done.
In summary:
-
Remove what you currently have on your OpenVPN tab
-
Add rule #1 on OpenVPN tab:
a. Source = 192.168.8.0/24 (remote access tunnel network)
b. Destination = alias containing LAN subnets -
Add rule #2 on OpenVPN tab:
a. Source = 192.168.8.0/24 (remote access tunnel network)
b. Destination = Invert match alias containing LAN subnets
c. Gateway = AIRVPN_WAN
-
-
THANK YOU
this worked perfectly. I figured it was something involving the gateway, being that I wasn't using the default gateway.