Problemi with dns resolution
-
Did you check the DNS Server enable checkbox?
-
yes
-
I had to ask. You didn't explicitly say, and I never assume the obvious. I have a similar config and it works for me. If the client runs:
ipconfig /allwhat is showing for DNS servers?
-
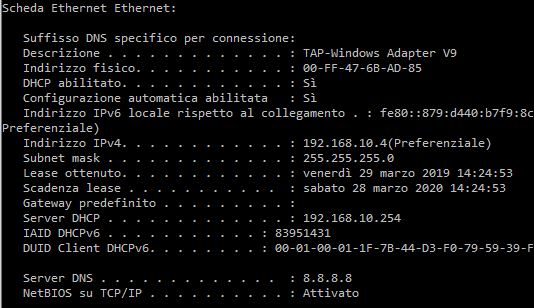
Hi,
the dns shown is:
8.8.8.8
I attach picture.
Thanks.
-
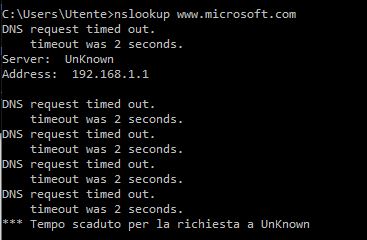
OK, so it seems ot be aware of DNS available to it. Can you ping 8.8.8.8? What happens when you run this on the client:
nslookup www.microsoft.com -
the ping is OK, in attached result about dns resolution.
Thanks.
-
Well, there is your problem. Can you ping 8.8.8.8?
-
yes, ping to 8.8.8.8 is OK.
Thanks. -
OK, so what happens when you run:
nslookup server 8.8.8.8 www.microsoft.comAs I recall, on the OpenVPN page there were some mitigation options for Windows 10 clients. Have you tried checking Force DNS cache update under Advanced Client Settings?
-
the result is in attach.
Yes, force DNS cache update is already selected.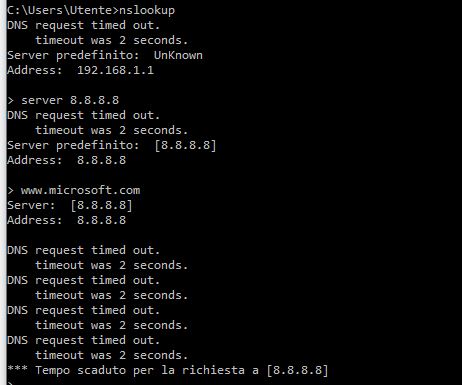
Thanks. -
Show me a screenshot of your firewall rules for the OpenVPN interface. I suspect you're not allowing UDP traffic or something like that.
-
Hi,
attached the required rules.
Thanks.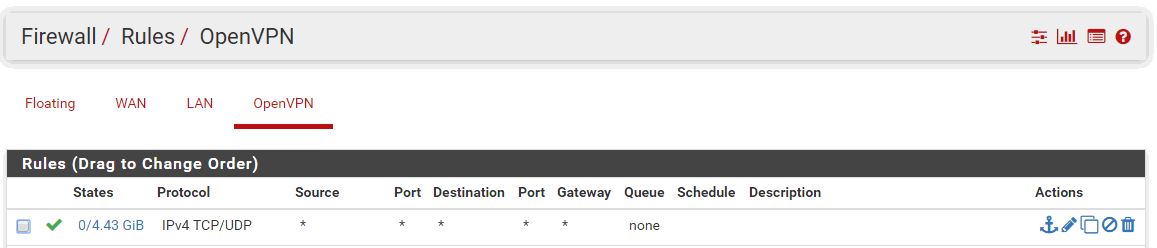
-
Set the protocol to Any and try again.
-
Hi,
unfortunately even with any dns resolution it fails.
Thanks.
-
Very strange. Does your firewall log show any relevant blocks while you're testing?
-
Hi,
no, I don't see deny in the logs.
Thanks. -
Yo @johnpoz Johnny joe ray bob, any thoughts?
-
We need more details on the setup. For clarity, is "host-to-site" referring to a remote access, road warrior setup? If so, post the server1.conf (/var/etc/openvpn).
We'll know more once we see the config, but is all traffic forced thru the tunnel?
-
Hi, attached server1.conf.
The address:
192.168.1.1
is the address of the router / dns referenced by the remote client that connects to my openvpn server.
The pfSense version is 2.3.2, do I need to update it?
Thanks.
server1.txt -
Not seeing anything out of the ordinary in the config. Looks like a standard, split tunnel config. Which raises the question though, since the client is using their own internet connection for the internet, why are you pushing public DNS? It's unnecessary. It's not the issue, but unnecessary.
So, the config tells me you have a split tunnel, remote access solution where the clients are using their own internet connection for everything except for traffic destined to 10.0.0.0/24 (server-side LAN). This is all standard stuff. The config looks nearly identical to all of the split tunnel configs I've deployed.
On split tunnel implementations, all of the subnets have to be unique on both ends, so the only thing that would cause issues, in this case, would be if the client's LAN is either 192.168.10.0/24 or 10.0.0.0/24 (or if the client is trying to connect from somewhere inside the server-side LAN). Outside of those scenarios, this particular issue appears to be on the client-side network. The client's PC is having issues resolving DNS, regardless of the VPN since they're using their own internet.
I would do a few things for starters:
- Update your PFsense firmware. (v2.3.2 is 16 versions behind and almost 3 years old)
- Remove the DNS push for 8.8.8.8 (uncheck "DNS SErver enable")
- Remove the recently checked "Force DNS cache update" option (not needed when not pushing DNS)
- Re-export the full OpenVPN windows installer package, send it to your user, have them uninstall their current package, manually delete the "C:\Program Files\OpenVPN" directory, then install the new package.
I suspect the remote-end had DNS issues even before connecting, but after the above is done, if they continue to have issues then the problem is definitely somewhere on the remote network. The client-end will need to troubleshoot DNS resolution on their end because all internet activity, in this case, is handled by the client-side network.
I would also verify there are no stray, statically set DNS entries or manually added persistent routes on the PC.