Unable to get VLAN working
-
In my previous post, I thought I had it, but I've got some strange things happening. Here's a simplified topology:
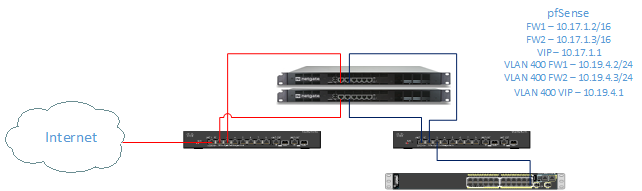
RED is WAN, BLUE is LAN. Due to the way the VoIP system is setup on this network, all ports are trunk ports because the phones are not Cisco compatible. The LAN side 8 port SG300 is all configured for trunking and hasn't been touched. On the Cisco 2960S, ports for PCs are configured as:
interface gig0/XX switchport mode trunk switchport trunk allowed vlan 1,18as there should be no LAN devices on this VLAN. This is for an SSID only.
I've added the new VLAN 400 to every switch in the network. On the IOS 12 devices, I can see this:
vlan 400 name CorpWirelessAll switches only work with 802.1q so "switchport trunk encapsulation dot1q" isn't accepted and doesn't need to be specified.
All links to other switches and Meraki MR access points are configured as:
interface gig0/XX switchport mode trunkWithin the Meraki dashboard, the access points do pick up VLAN 400.
For troubleshooting, I've set one of the switchports to access VLAN 400. The computer plugged in is unable to pull an IP and I have DHCP enabled on the VLAN interface within pfSense.
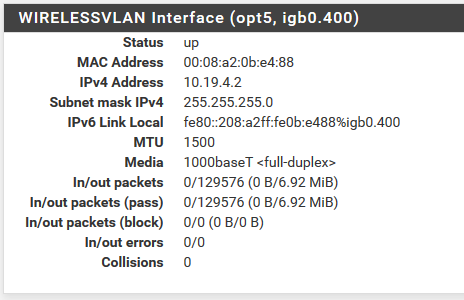
Here's my pfSense configs:
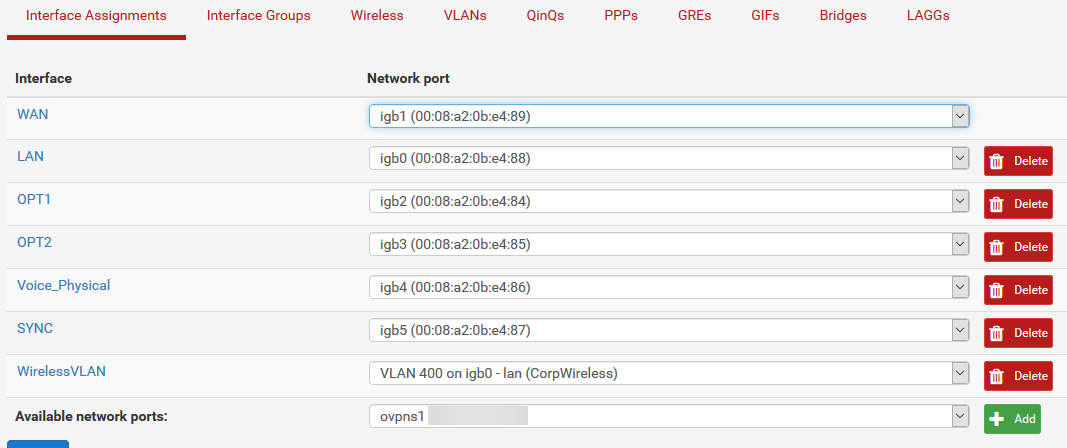
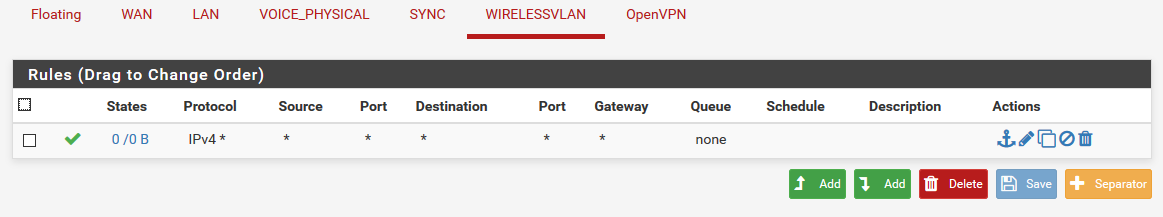
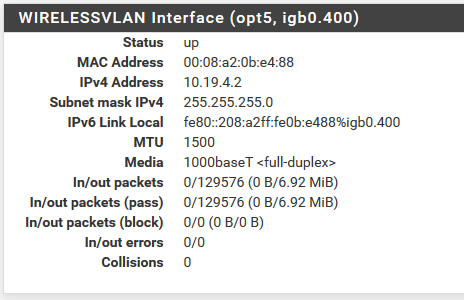
Routing Table:
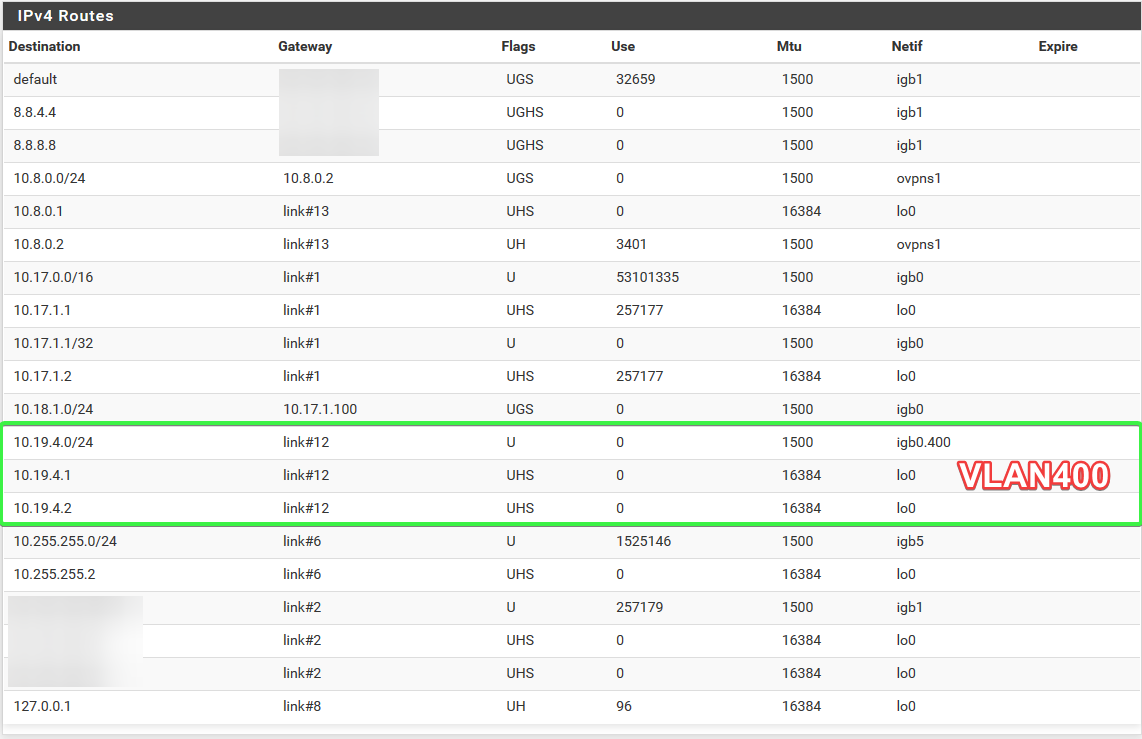
My concern is I see no traffic in the routing table or firewall. Yet using the diagnostics, I can ping from the VLAN interface to a server on the default VLAN so routing is clearly working:
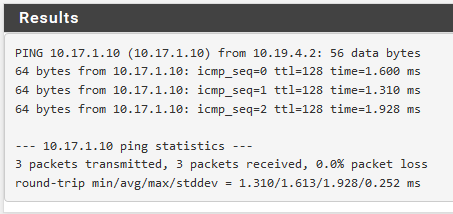
The CARP IP, 10.19.4.1, shows as "master" on both firewalls and from other threads and Google, this seems to indicate that the firewalls aren't sure of each other with this interface. The firewall rules for VLAN 400 do sync across and match up to the secondary firewall. I've noticed during this that if I try to ping 10.17.1.3 or 10.19.4.3 (the physical and VLAN 400 interface, respectively, on FW2, no pings return). Any pointers where I can check?
Edit:
I did a packet capture on pfSense while pinging from the switch to 10.19.4.2 and these are the only packets captured:
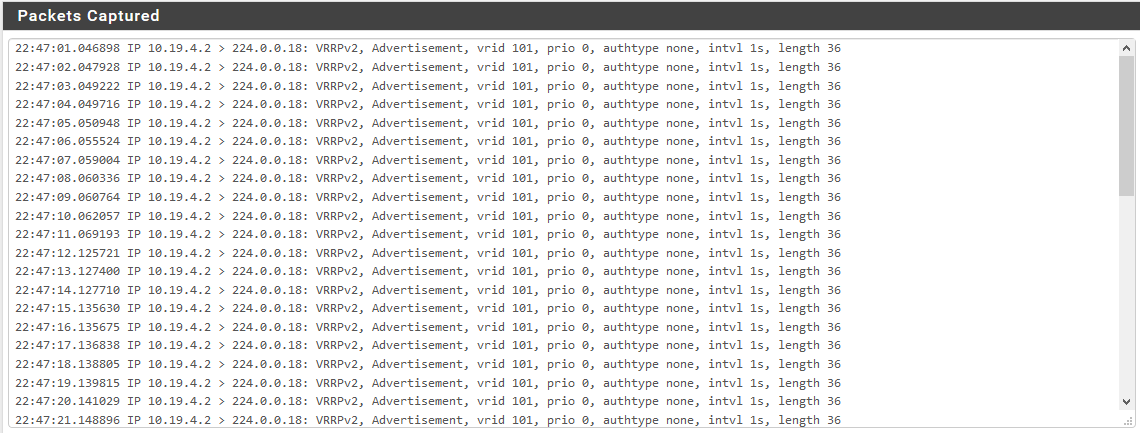
Edit 2: I had a user on site plugin a laptop and configure a static IP. When they set the gateway to 10.19.4.1 (the CARP IP), nothing went through. Running a packet capture, I was able to obtain the following when they set the gateway to 10.19.4.2.
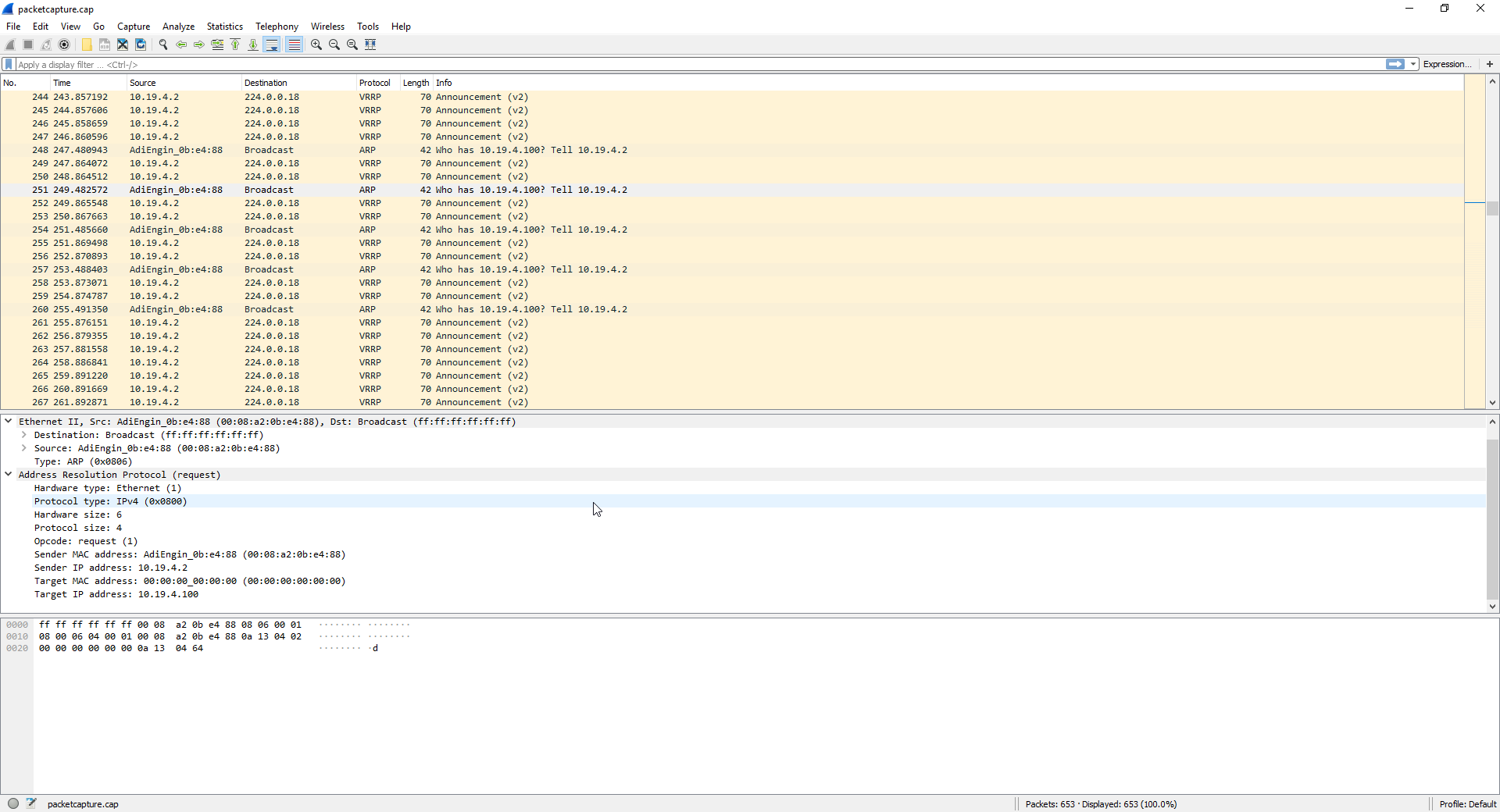
-
Looks like your switching gear is not sending any traffic to pfSense tagged VLAN 400.
-
Finally got this solved! Previous admin never documented anything so I was just stumbling around. There's a layer 3 switch doing VLAN routing (originally it was just passing the routing off to the old router). So I reconfigured the layer 3 switch to handle the VLANs, pfSense just handles everything out to the internet. So we're all good!