odd issue with Vlan?
-
Hi,
I was wondering if someone could shed some light on the issue im having. Currently have pfSense 2.4.4 with VLAN for quests to connect and that Vlan
does not have access to the LAN. Whats odd is that i have an email server on my LAN and if i connect my mobile phone to the VLAN guests
i cannot get email. when i ping i get the WAN which is fine so im not sure why its not getting mail on the phone. i tried looking at states
did not find nothing. then i tried to packet capture also could not find anything odd.
any ideas?
Thank you -
If you don't allow access from the VLAN to LAN, why would email work? The 2 networks are supposed to be isolated aren't they? If you want email on the phone, you'd have to set up routing between the 2 networks, but I'm not sure that's what you want.
BTW, why don't people ever have even issues?

-
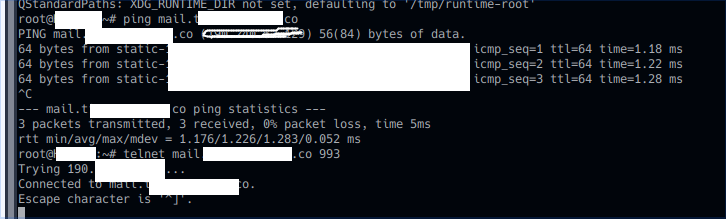
Thanks for the reply, correct the two networks are isolated. but how come i can ping mail.mydomain.com from my guest network which shows the WAN ip and when i try to send and receive it wont work. as soon i disable the isolation on pfsense it works. so my question is how come on the guest network it tries to connect
thought the LAN instead of the WAN and whats odd i ping the mail.mydomain.com and i get the WAN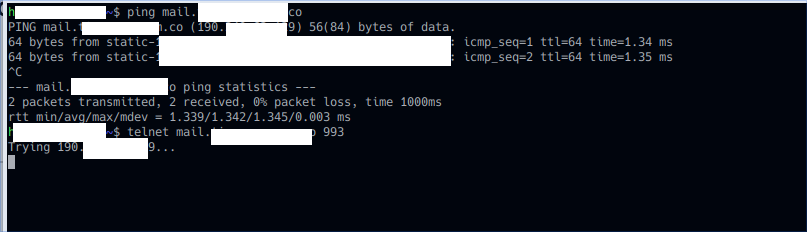
-
@killmasta93 said in odd issue with Vlan?:
how come i can ping mail.mydomain.com from my guest network which shows the WAN ip and when i try to send and receive it wont work.
You'd have to look at logs on the firewall and your mail server and follow the traffic, but I would imagine this is what's happening:
From the guest LAN network, the client tries to connect to the mail server on your LAN, but mail.mydomain.com resolves to a public IP so it's trying to go out the internet and right back in... and things are getting lost in translation due to port forwarding, source IP's, etc.
You pretty much have two options:
-
Enable NAT reflection on the port forwards related to your mail server.
-
The cleaner solution would be to configure split DNS, so internal clients are contacting the mail server locally instead of trying to go out to the internet. You would then need to open pinhole's to your mail server for email.
Both options are laid out here -> https://docs.netgate.com/pfsense/en/latest/nat/accessing-port-forwards-from-local-networks.html
-
-
Thanks for the reply, on pfSense i already had NAT reflection as my LAN has no issue. as for that issue that you said could be right
but i was checking states and logs i dont see that type of traffic going to the LAN. on the forwarder i also did Nat reflection
so im stumped.Thanks for the reply whats odd is that i can access the https traffic because i have fronted nextcloud but cant access ports 465 993 995edit: your right some odd reason its going to the LAN
USER_RULE (1554095281) 192.168.7.13:34768 192.168.3.150:465 TCP:SEC
-
Yep. My suggestion:
- Create a host override for your mail server.
- Configure explicit firewall rules for email traffic sourced from your guest VLAN
Problem solved.
This approach is cleaner and more efficient for the entire network (both LAN and Guest) as traffic no longer has to go all the way out the WAN first and back.
-
Thanks for the reply, currently right now what im doing is removeing the 192.168.3.150 from the block rule i have on the guest VLAN but i dont want users to be able to ping 192.168.3.150
which is why i dont get if i can ping mail.mydomain.com and comes back WAN not sure why its trying to go to the LAN
I have NAT reflection working. If i understood correctly is to create a host overide
but host overide to put host mail and ip to return the WAN ip?
then create an explict firewall rule? to allow all guest VLAN to access 192.168.3.150? -
If i understood correctly is to create a host overide
but host overide to put host mail and ip to return the WAN ip?
Note quite. You want to configure a host override for mail.mydomain.com and point it at the internal IP of your mail server (i.e. 192.168.3.150). Right now, your clients are trying to connect to mail.mydomain.com, which is resolving to a public IP, then being routed accordingly out your WAN and relying on NAT reflection to redirect the traffic back thru the firewall. Once the host override is configured, when your clients initiate a connection to mail.mydomain.com, the DNS query will get resolved locally to 192.168.3.150 and then traffic will get sent to the mail server directly vs. being routed out the WAN interface.
At this point, two things will now happen more efficiently:
-
DNS queries for mail.mydomain.com will be resolved locally by PFsense instead of being forwarded to a server on the internet for resolution.
-
When clients initiate connections to your mail server, the traffic will be sent directly to the mail server instead of relying on a "hack" that loops traffic through the firewall after it hits the WAN interface.
then create an explict firewall rule? to allow all guest VLAN to access 192.168.3.150?
Almost, but even more explicit. You don't want to allow all guest VLAN traffic access to 192.168.3.150... you only want to allow traffic sourced from the guest VLAN and destined to 192.168.3.150 using email ports.
-