802.11ac support
-
No.
Buy an access-point, FreeBSD support for Wi-Fi is a bit lacking.
-
Any recommendation?
We're looking for SPEED more than range.
Our WAN ISP can handle 230/30
Thanks -
is this a good choice?
https://www.amazon.ca/gp/product/B00BUSDVBQ/ref=ox_sc_act_title_2?smid=A3DWYIK6Y9EEQB -
Buy a Ubiquity AP, they are flavour of the month round here.
I have one of these:-
https://www.ui.com/unifi/unifi-ap-ac-pro/
https://help.ubnt.com/hc/en-us/articles/115012360487-UniFi-Getting-Started-with-the-UniFi-Mobile-App#2
Do you have a switch that can do VLANS, if you do you can have multiple networks / SSIDs.
If you have an old router that can do Wi-Fi you can switch off DHCP and use that as an AP if you want to do it on the cheap.
-
@Wastapi No, that's a full router. You only want an access point. I have a Ubiquiti AP-AC-LR and it works great.
https://www.ui.com/unifi/unifi-ap-ac-lr/
-
The Ubiquity AP AC Lites work great as well. They're around $80 US each, from Amazon.
https://www.ui.com/unifi/unifi-ap-ac-lite/
Jeff
-
I also have a Ubiquiti AP-AC-LR and have had no problems with it. Great coverage.
The central management stuff is nice but I'm not totally convinced it's worth it if you only have one device.

Steve
-
While I use Ubiquiti Access Points myself, I recently setup a small network with a pfSense firewall where we just used one of these:
https://www.amazon.com/Dual-Band-Super-Fast-Gigabit-MU-MIMO-RT-ACRH13/dp/B01LXL1AR8
Decent specs too:
https://wikidevi.com/wiki/ASUS_RT-ACRH13Even though it is a full router, it takes just a couple clicks in the administration interface to turn it into an AP. Unless you are looking to do things with VLAN's and multiple SSID's, this Asus unit provides great bang for the buck (and you won't need to worry about controller software that the Ubiquiti AP's require).
Hope this helps.
-
I do need to create an employee ssid and an isolated guest ssid.
The employees will have access to whoke network while guests should only have wan access
-
You'll need a switch and AP that supports VLANS if you just want to use a single AP and firewall rules something like this:-
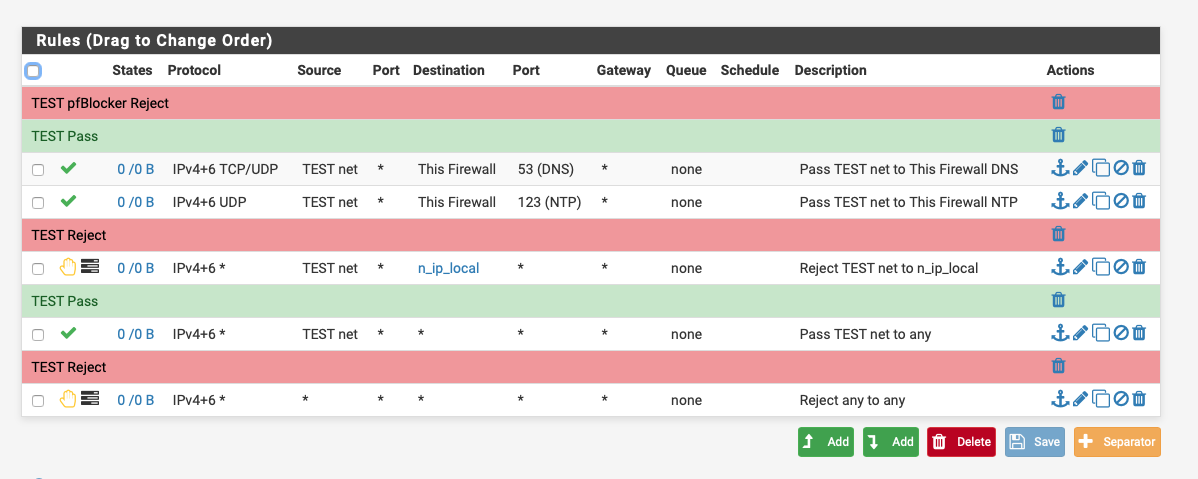
Replace TEST net with the name of your Guest net n_ip_local is an alias that contains my local subnets.
-
You can do without a managed switch if you can connect the AP directly to the firewall in most cases.
Steve
-
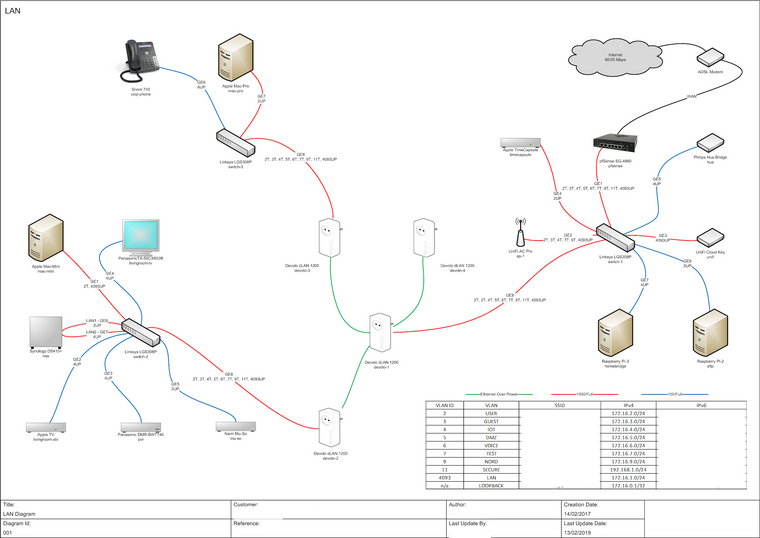
Our topology
WAN - pfSense - Unmanaged Switch - Wifi Router (as AP)
-Employees would connect to Wifi Router with employee SSID get access to whole LAN
-Guests would connect to Wifi Router with Guest SSID get access wan only
-Employees would connect to Unmanaged Switch (wired) get access to whole LANMakes sense?
-
So the ethernet connection comes out the router to a switch and an AP is connected to a switch ?
How are you setting up this "Wifi Router"?
-
Until you actually test it it will be impossible to know if that unmanaged switch will pass the required VLAN from the AP to pfSense.
Much better to either use a managed switch that definitely will pass VLANs oe connect the AP directly to pfSense.Steve
-
@Wastapi said in 802.11ac support:
Our topology
WAN - pfSense - Unmanaged Switch - Wifi Router (as AP)
-Employees would connect to Wifi Router with employee SSID get access to whole LAN
-Guests would connect to Wifi Router with Guest SSID get access wan only
-Employees would connect to Unmanaged Switch (wired) get access to whole LANMakes sense?
The Asus Router administration software does allow the ability to enable a Guest Network and disable access from it to the local intranet:
https://www.asus.com/support/FAQ/1009855/
This would be one option if you're looking to keep things simple (e.g. just one LAN subnet) and don't need more advanced SMB/Enterprise capabilities (e.g. multiple VLAN's, subnets, SSID's, etc.)
Hope this helps.
-
Or should I install an extra LAN card on the pfSense to hold the AP?
WAN - pfSense
pfSense - Unmanaged Switch (for wired only)
pfSense - AP (for wifi only)Yet I don't want to have a different AP for Guests and for Employees (budget)
And I feel that placing the AP (a router) between the pfSense and the Unmanaged switch is weird. -
It depends how you want to set things up:
Ideally LAN, WiFi, and WiFi Guest Networks would all be on separate subnet's (VLAN's) to allow for fine grained access control (since traffic would have to go across the firewall first for any of the subnets to speak with one another). However, if you want to keep things simple, you can put your WiFi and LAN clients on the same local subnet by using e.g. the router I linked to, turning it into AP, and then enabling the guest network on it for guest clients (which will only have access to the internet but not the local subnet).
What security requirements do you have, and which type of setup do you prefer?
-
@Wastapi said in 802.11ac support:
Or should I install an extra LAN card on the pfSense to hold the AP?
Nope you'll need two APs if you do this.
You need a switch that does VLANS and an AP that does VLANS.
-
You can just connect the AP directly to a NIC in pfSense and have multiple VLANs on that. You don't actually need a switch there.
For most installs it's just much easier to use managed switches because of the physical locations involved. APs like to be up high in the center of the coverage area and firewall is probably nowhere near.
Steve
-
@stephenw10 said in 802.11ac support:
Until you actually test it it will be impossible to know if that unmanaged switch will pass the required VLAN from the AP to pfSense.
Here is a list of Ethernet frame types. Any switch that can pass every one of them is defective.