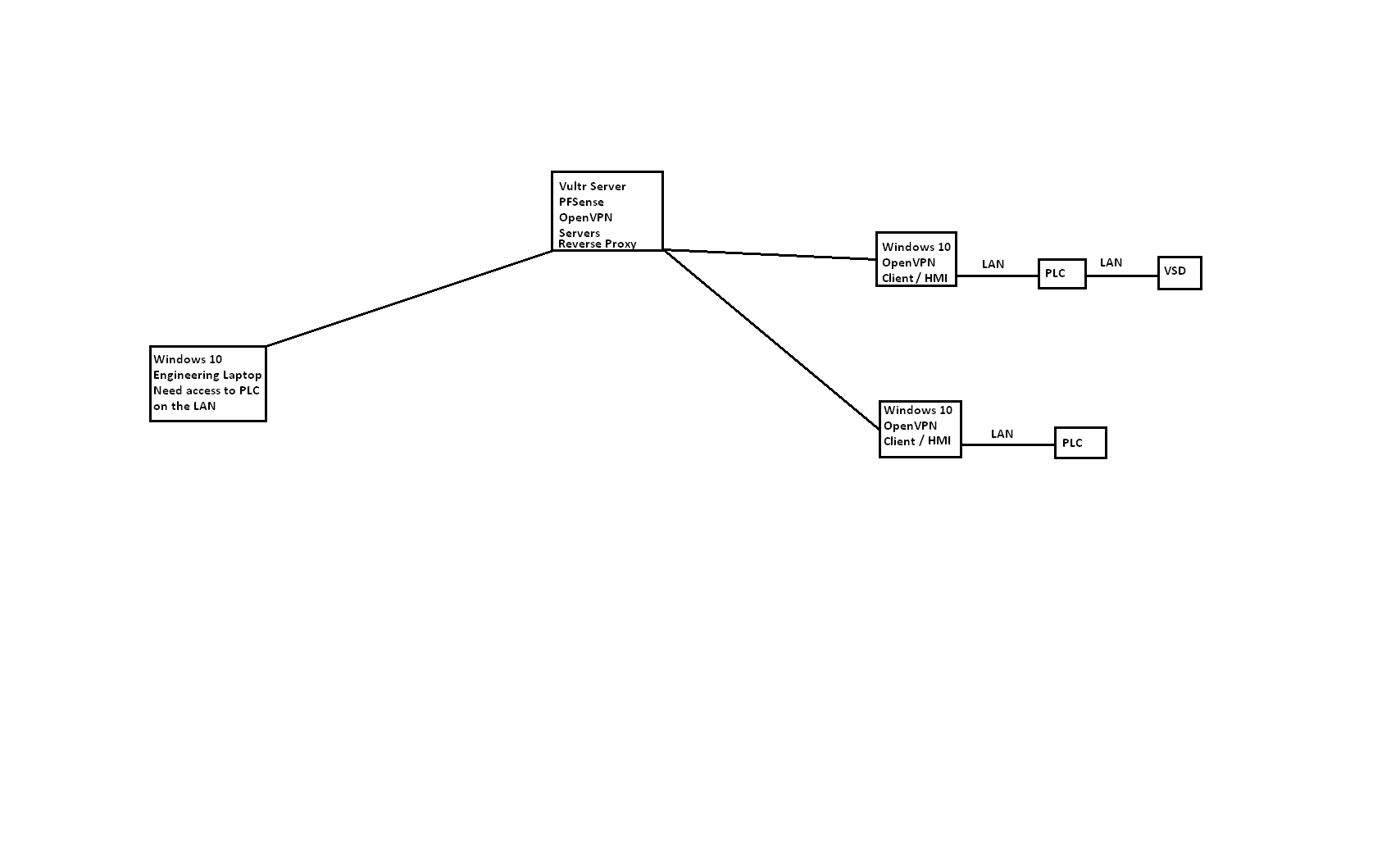
OpenVPN routing windows to access lan on client side of windows
-
@marvosa The laptop connects to the same OpenVPN server as the Panel PC client is connecting to. There is currently no LAN setup on the server side in PFSense. I have just used push routes in the OpenVPN configuration. Should I add local LAN in the client-specific overrides as well on both clients, my laptop and the panel PC?
There is no external firewalls or anything on the remote site when I'm using internally built-in 4G LTE module on the panel pc. Sometimes I connect into existing Internet connection but don't have any access to configure router or firewalls etc
I have no way to add static routes on the PLC, I can only give the PLC a static IP address. Would running RouterOS on the panel PC allow the required settings and configuration to route VPN Tunnel out to the LAN the PLC is on?
So I take it there is no way to route the OpenVPN tunnel Network to the Local LAN Network?
It seems I have really got myself into the deep end. There is a device called Ewon that's based off OpenVPN and they are used to connect to PLC and networks remotely. I take it my bottleneck and issue is using windows which doesn't give much flexibility -
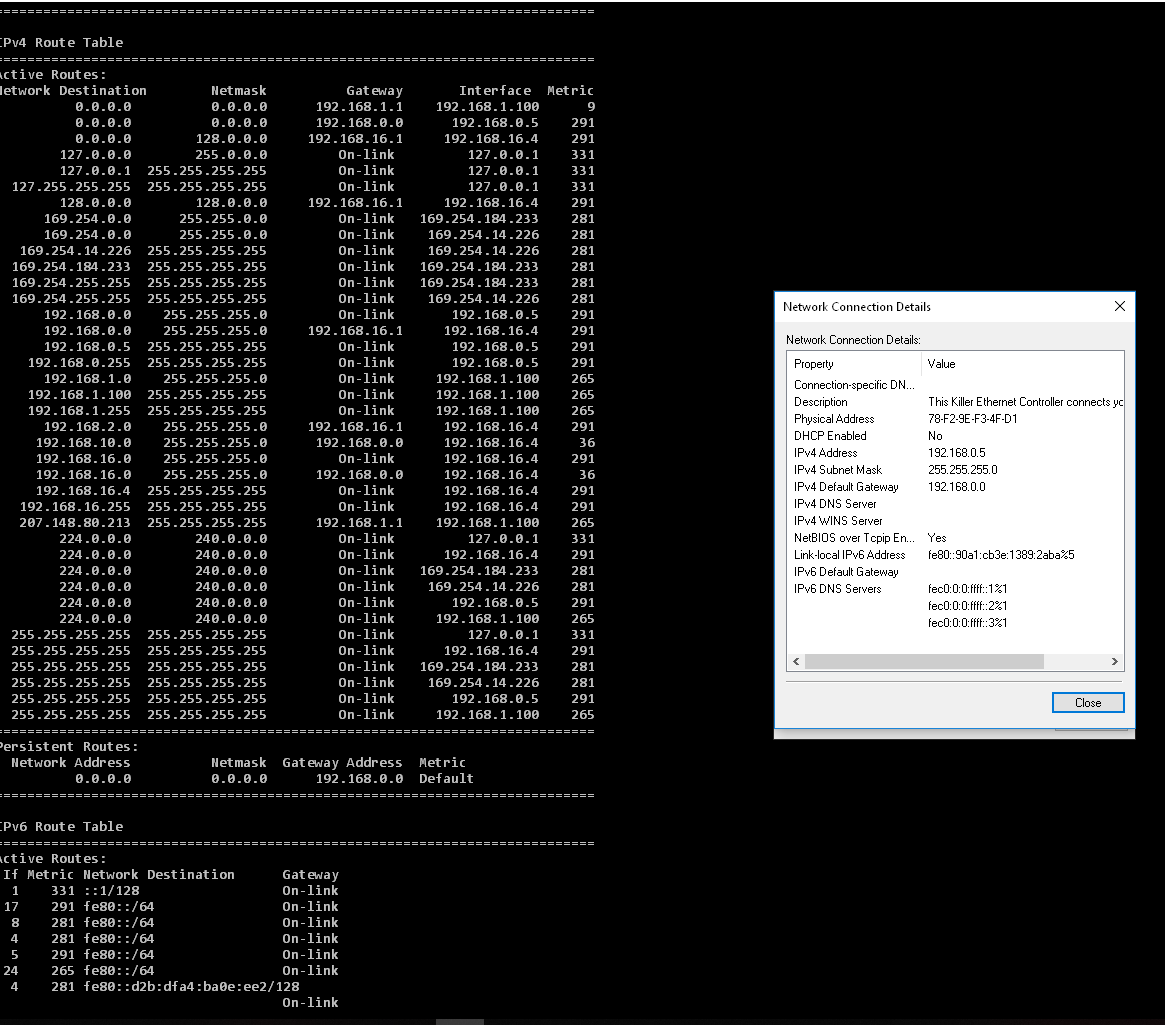
I have still been at this with no success. I have attached the routing table. Gone over all the OpenVPN configurations again and again and all documentation, have all the push routes and routes and Iroutes all set. It seems it's just not possible to do with windows. Does anyone have any other ideas I can try? seems I am just running into a dead end. The 192.168.16.4 Is the tunnel IP and the 192.168.0.0 network is the local lan and the 192.168.1.0 is the wifi network
-
If you're routing traffic between OpenVPN clinets the OpenVPN daemon at the server will need to know what subnets are behind which clients in order to send that traffic to them. You would do that using client specific overrides in pfSense.
The PLC will need to be using the panel PC as it's gatrway in order to have a route back to the client laptop unlesss you are NATing the traffic leaving Windows but.... I have no idea on that!
Steve
-
Hi @stephenw10 I am already using the client-specific overrides in PFSense. I have the subnets under ipv4 remote networks, the only thing I don't quite understand the Note as there is no option to add those subnets in the server settings. In the server settings, I have added route and the subnets and the push route and the subnets which I would suspect that's what it is referring to.
"These are the IPv4 client-side networks that will be routed to this client specifically using iroute, so that a site-to-site VPN can be established. Expressed as a comma-separated list of one or more CIDR ranges. May be left blank if there are no client-side networks to be routed."
"NOTE: Remember to add these subnets to the IPv4 Remote Networks list on the corresponding OpenVPN server settings."From the picture, you can see the LAN has been set with static IP and mask and the gateway set to 192.168.0.0 so I would suspect that would provide the gateway?
-
This is what I get when I try to ping the PLC from PFSense. Note I have now changed the IP address range to 192.168.2.10 just to make sure there were no conflicts etc so above routing table is not valid now.
PING 192.168.2.10 (192.168.2.10): 56 data bytes
92 bytes from 192.168.16.4: Redirect Network(New addr: 192.168.16.1)
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 0054 3a2a 0 0000 3f 01 ae23 192.168.16.1 192.168.2.1092 bytes from 192.168.16.4: Redirect Network(New addr: 192.168.16.1)
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 0054 ef17 0 0000 3f 01 f935 192.168.16.1 192.168.2.1092 bytes from 192.168.16.4: Redirect Network(New addr: 192.168.16.1)
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 0054 3886 0 0000 3f 01 afc7 192.168.16.1 192.168.2.10--- 192.168.2.10 ping statistics ---
3 packets transmitted, 0 packets received, 100.0% packet loss -
What is 192.168.16.4? And 192.168.16.1?
-
@stephenw10 192.168.16.4 is the VPN Tunnel IP address and the 192.168.16.1 is the tunnel gateway IP
-
Ah, so pfSense is sending traffic to the panel PC at 192.168.16.4 to pass to the PLC at 192.168.2.10 but is replying with a redirect to it's gateway. That implies the panel PC doesn't know where the 192.168.2.10 IP is.
Steve
-
@stephenw10 I can ping the PLC from the panel PC in cmd and get a response and works fine. Is setting the default gateway correct under the LAN settings correct?
-
@mxracer303 said in OpenVPN routing windows to access lan on client side of windows:
Is setting the default gateway correct under the LAN settings correct?
In pfSense? No.
I have no idea why the panel PC is replying with that if that subnet is local to it. It is not forwarding the traffic as a router would.
Steve
-
@stephenw10 The gateway is set under the LAN adapter IPV4 Settings along with static IP on the Panel PC itself. There is no router between the Panel PC and PLC, PLC is connected directly to the Panel PC. Could having no router be the issue? Is there a way to forward traffic with Windows?