-
Hi,
has there been any further developments on the acme dyndns?
-
I know, I know... replying to an ancient thread. But this was the ONLY information that got up and working.
For those of you trying to issue ACME certs through Let's Encrypt on pfSense this should help. I too considered moving to another dynamic DNS provider but got lazy just thinking about updating all the DDNS clients I have out there...
@piperspace Thank you so much for pointing me in the right direction. I was going nuts trying to get this to work.
I had to make the following edits in /usr/local/pkg/acme/dnsapi/dns_nsupdate.sh:
nsupdate -k "${THISNSUPDATE_KEY}" <<EOFbecomes
nsupdate <<EOFthen added:
zone <your domain in DynDNS> key <DynDNS TSIG Key Name> <DynDNS TSIG Key HMAC>(THE SPACE IN BETWEEN THE KEY VALUE IS IMPORTANT!!!)
I also added a "quit" after the "send" statement, dunno if it is needed, but it's working for me.
Make sure you update the dns_nsupdate_add() and dns_nsupdate_rm() functions as well.
Be patient when you renew/issue, the script sleeps for 120 seconds to allow DNS updates to show.
Hope this helps someone.
-
@taius You are welcome. I am glad my research helped you.
FWIW - I noticed in August that the then current version of Acme no longer required my hack. But now I am on Acme 0.3.2_4 and the hack is again necessary. Are we having fun yet?
-
@piperspace, @taius ... Thank you both.
Background: I was unfortunately not able to use the webserver/port 80 method, as I need to forward the port to an internal webserver, on which I can't/won't use the FTP method. Also, the Dyn.com built-in provider does not work with a Standard DNS account at Dyn.com, which meant using the nsupdate method was the only one left available to me. Without this helpful post, I would have given up in despair!
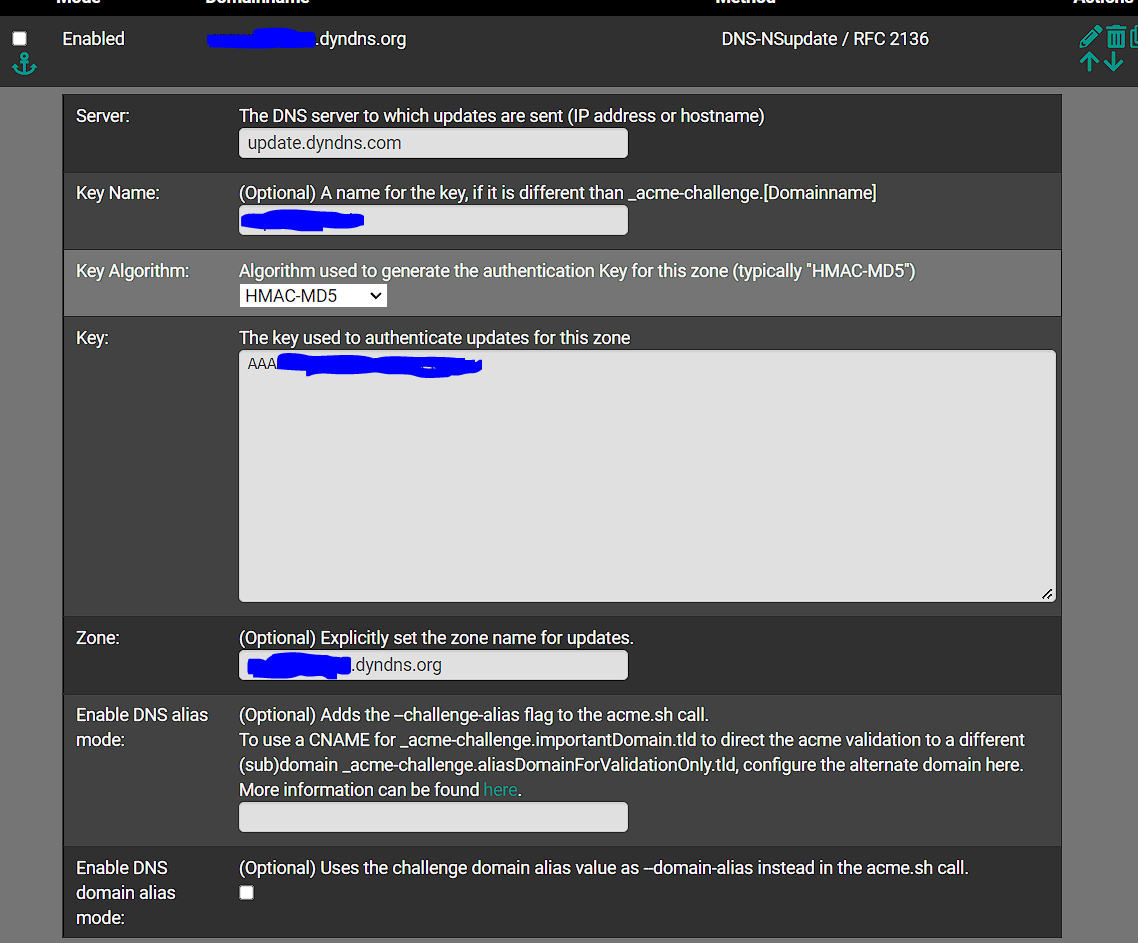
Because I prefer to have my setup configurable through the webGUI, I decided to attack the dns_nsupdate.sh file to allow configuration through the existing webGUI fields. For this I have explicitly checked for "update.dyndns.com" as the target, and therefore used the "KEY" textarea to provide the necessary ZONE and KEY lines required.
First, replace the dns_nsupdate.sh file with the one attached.
Then configure your domains in the webGUI as usual, with the server specified as "update.dyndns.com", and the Key as:zone example.com key [Key Name] [Key HMAC]This way you can use multiple domains/keys/etc. all from the webGUI.
The changes/additions I made to the file are as follows:
_info "adding ${fulldomain}. 60 in txt \"${txtvalue}\"" if [ "${THISNSUPDATE_SERVER}"="update.dyndns.com" ]; then THISNSUPDATE_DATA=`awk -F '"' 'BEGIN{RS=";"}NR>1{print $2}' "${THISNSUPDATE_KEY}"` nsupdate <<EOF ${THISNSUPDATE_DATA} server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update add ${fulldomain}. 60 in txt "${txtvalue}" send quit EOF else nsupdate -k "${THISNSUPDATE_KEY}" <<EOF server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update add ${fulldomain}. 60 in txt "${txtvalue}" send EOF fiand
_info "removing ${fulldomain}. txt" if [ "${THISNSUPDATE_SERVER}"="update.dyndns.com" ]; then THISNSUPDATE_DATA=`awk -F '"' 'BEGIN{RS=";"}NR>1{print $2}' "${THISNSUPDATE_KEY}"` nsupdate <<EOF ${THISNSUPDATE_DATA} server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update delete ${fulldomain}. txt send quit EOF else nsupdate -k "${THISNSUPDATE_KEY}" <<EOF server ${THISNSUPDATE_SERVER} ${NSUPDATE_SERVER_PORT} update delete ${fulldomain}. txt send EOF fiOther than the "cryptic" awk command to extract the text out of the generated key file - everything else is very self explanatory.
Thanks again ... very helpful, and very timely info!
Cheers.
-
I still have issues with this.
It fails on adding _acme-challenge.....
error updating domainThe TSIG is correct.
Perhaps a couple of screenshots?This is so convoluted for a major dyndns provider.
-
I am now having some Acme success with DynDNS on Pfsense 2.4.4-p2 with Acme package 0.5.4_1. I no longer need to engage in script hacking.
Below is a screenshot of my Amce config.
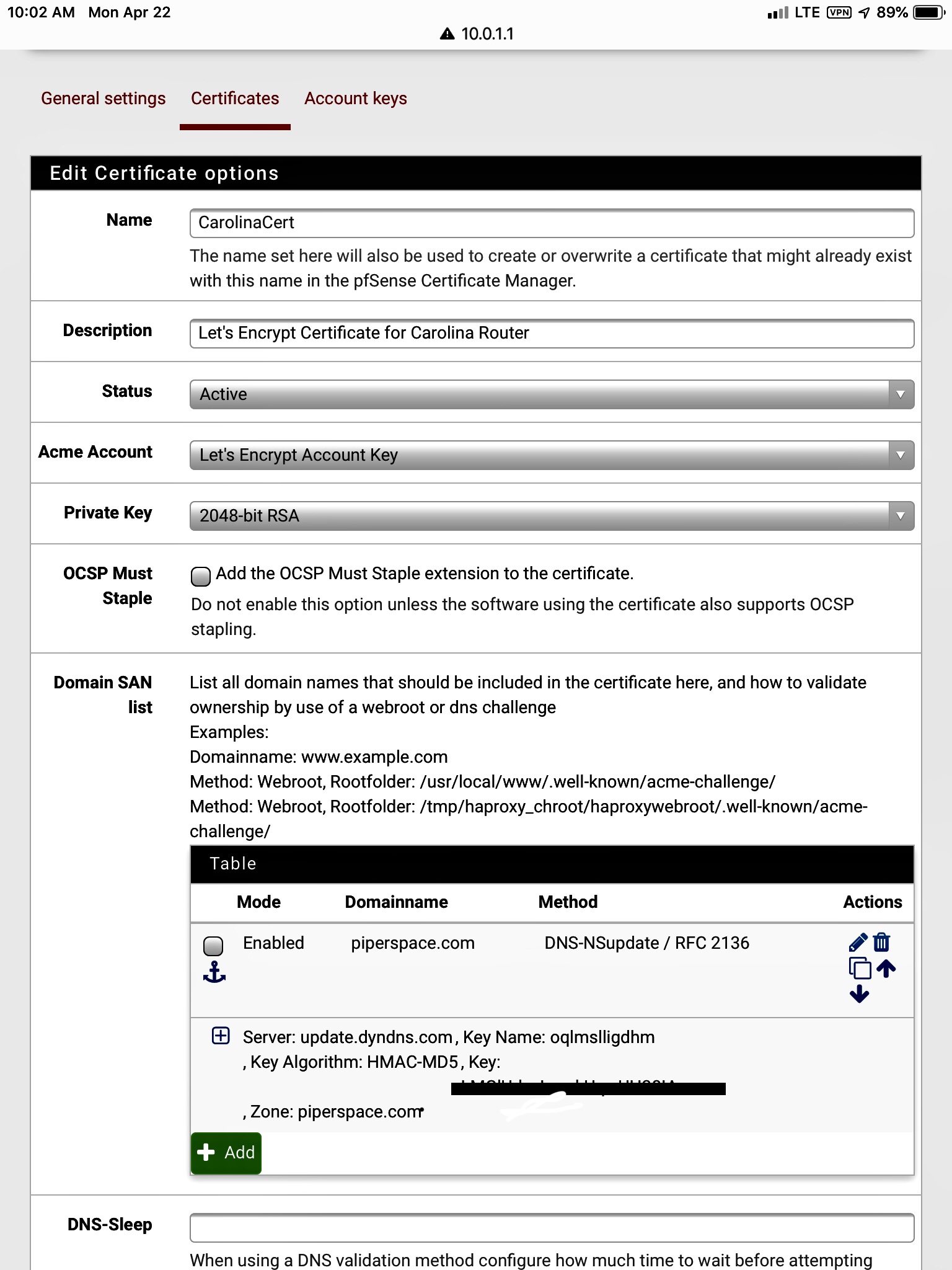
-
I reset the script back to the original.
My settings:
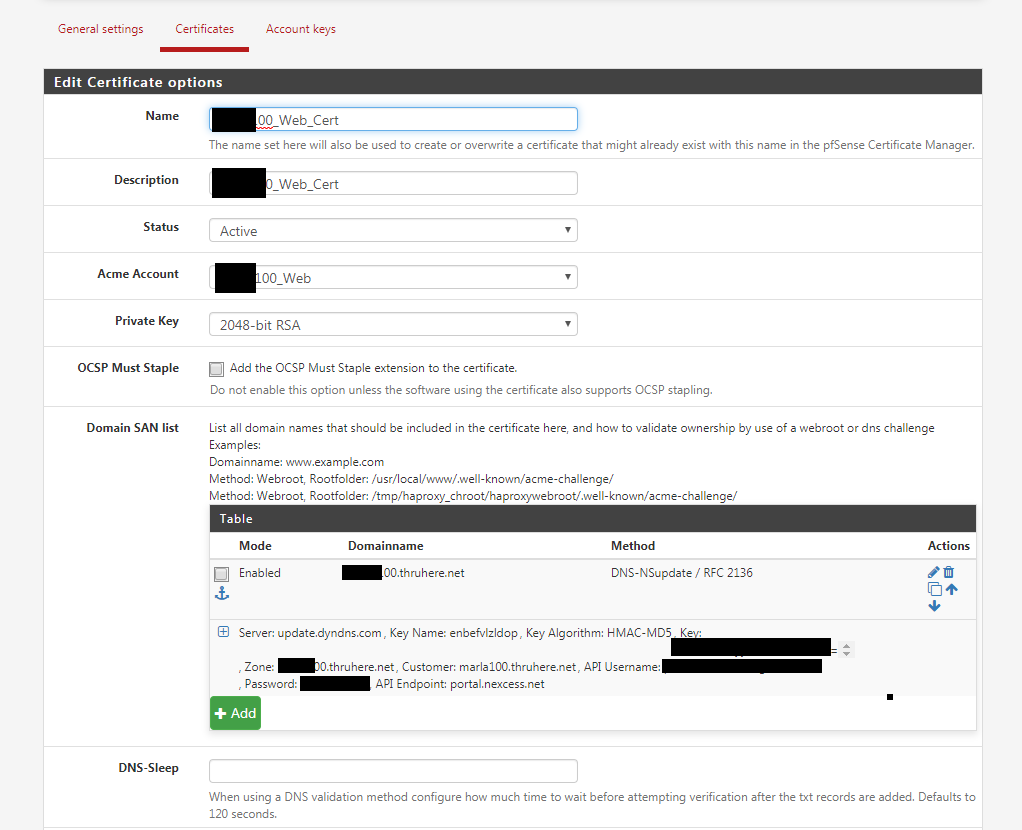
Error message:
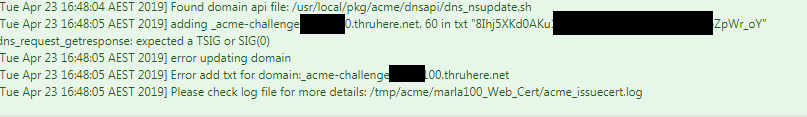
I probably need to get a better understanding of how this process works, can i use a DynDNS as the Zone?
-
No. DynDns.net is not your zone. The parameter you are using for that looks ok. But you are using additional parameters I don’t know about.
I have DynDns Standard DNS which lacks a proper API thus requiring nsupdate. There is also DynDns Pro which may have an API. It’s confusing. Which service do you have? If you have DynDns Pro you are probably barking up wrong tree here.
Also, you can test parameters by connecting to your router and running nsupdate from the command line.
-
The additional parameters auto-filled, so I don't know where they came from and I can't seem to edit them. Perhaps, as you point out, I have a dyndns pro service.
-
You might want to delete your config and start over using the DNS-Manual method.
-
So I upgraded Acme to version 0.5.7_1 and this is busted again.
In /tmp/acme/[mycertname] there is a .key file where my parameters have been stored. Except there is a period mysteriously appends to my key name.
When I edit this key file, remove the period and then feed it to nsupdate it works.I am vexed that Dyn compatibility seems to come and go. Would be willing to beta test new versions if that would be well taken.
-
Just wanted to update things. This is still broken in 0.58!
I suspect this is because the team thinks the dyn support is in the dyn section. Well, I know I for one, cannot get a dynid. So I'm stuck with the nsupdate method. Why can't I get a dynid? NO CLUE! I put in my "old" credentials, which I had just logged in with, and it says invalid. I suspect many of us are in the same boat, so PLEASE people, just because you support the new DynID, doesn't mean you've left a bunch of us high and dry!So, I basically used the script posted above, but for somereason it didn't pull out the keyname. So I added this right below his awk magic
THISNSUPDATE_KEYNAME=awk '{if (NR == 1){ key=substr($2,2,length($2)-3); print key}}' "${THISNSUPDATE_KEY}"
Then, it also didn't include the zone. I'm not sure of the "right way" to get the zone, so here's what I did: ZONE=echo ${fulldomain} | sed 's/_acme-challenge\.//g'
Then I changed the dnsupdate command to dnsupdate -d and added key $THISNSUPDATE_KEYNAME $THISNSUPDATE_KEY
zone $ZONE
This allowed everything to work.Posting this to help others and provide "cloud" backup of my work :)
-
Recently I got a notice from Oracle. The DYN Standard service I have is being phased out next spring. My option at that time is to migrate to an alternate Oracle product.
My plan is to use up the remaining time on my DYN Standard subscription and then migrate to CloudFlare.
-
I got the notice as well, but I have paid domain registrations as well as dyn pro (though I’m not sure I use it anymore...I had originally obtained it so I could do things like device.mysubdomain.dyndns.org...maybe I should audit that.
Regardless, they said it would be “migrated” to an oracle product line. Do they do dns? Or do they mean “rebranded”. Either way, I expect little to change other than eventually...maybe....they’ll fix their dynid bugs :)
-
Just FYI - I have completed migration to Cloudflare’s free service. It includes a DNS which works with Pfsense to handle IP address changes and ACME certificate renewal. No hacking required.
-
This may be OBE in a few months, but I just set this up and wanted to pull everything together for Dyn.com ACME updates as I just got it working with info from a number of posts in this thread.
I'm using Version 0.6.5 of the ACME client on 2.4.4-RELEASE-p3 of PFSense.
Dyn.com has 3 products https://help.dyn.com/dyn-dns-products-compared/
- Managed DNS - you log in at https://portal.dynect.net/
** "Professional DNS Solution" - Standard DNS - you log in at https://account.dyn.com/
** mange domains, the domain registration recently was migrated to name.com - DynDNS Pro, now just called Dynamic DNS - also at https://account.dyn.com/
** get up to 30 hostnames in prepopulated domains.
The new Oracle Cloud DNS service is completely different.
The "Dyn.com" method only works with Managed DNS.
The nsupdate method works with Standard DNS
- server = update.dyndns.com
- keyname = see below
- Key Algorithm = HMAC-MD5
- Key = see below
- Zone = your zone to use
You have to get a TSIG key for the keyname and key. The directions are at https://dyn.com/updater/tsig/ and the key itself can be created or updated at https://account.dyn.com/profile/tsig.html
I suspect this will not work for DynDNS Pro as there seems to be no way to create a TXT entry.
- Managed DNS - you log in at https://portal.dynect.net/
-
Hello I am using the pfsense version 2.6.0. I am having still having issue in renewing my dyndns certificate. I am trying to use nsupdate but this what I am having the issue with
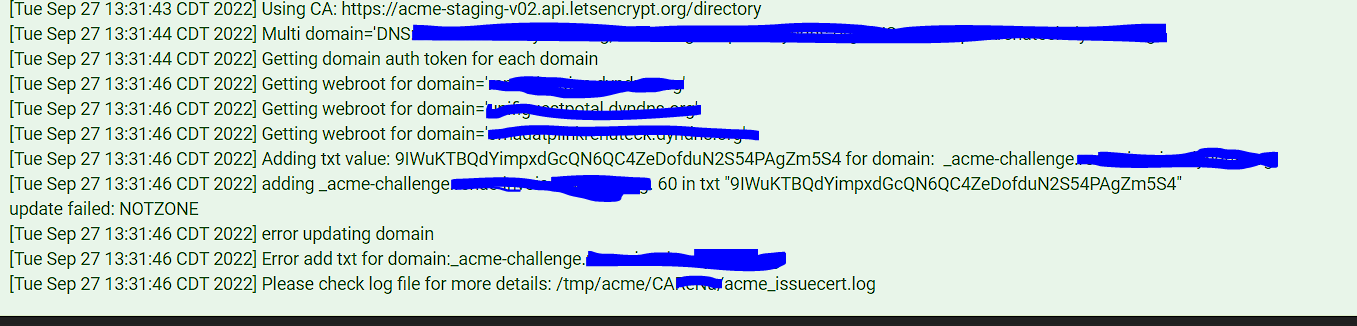
I have try all the method that have been post earlier but no luck
I am using dyndns pro service.
Can anyone can write the full script of nsupdate that would be really help full ? -
@fenil said in Acme and Dyn:
I am using dyndns pro service.
Can anyone can write the full script of nsupdate that would be really help full ?dyndns.org pro did : https://help.dyn.com/tsig/
Instead of
update add $HOST.$ZONE 60 A 10.0.0.1
the acme API plugin dns_nsupdate.sh uses :
update add ${fulldomain}. 60 in txt "${txtvalue}"to add this :

-
@gertjan
Hey man I have contact dyndns pro tech people also and they are saying they cannot accept TXT or API method but they gave me is TSIG key. They only use is nsupdate and I am not able to understand where to make changes property in order to make it work with pfsense.can we bypass TXT method in pfsense acme ?
-
@fenil said in Acme and Dyn:
can we bypass TXT method in pfsense acme ?
The method used has been chosen by you.
Because you chose to use "dyndns pro" so you have to the "dyndns pro" method.
As said : see https://help.dyn.com/tsig/ which is a very close approach to the old nsupdate method.Example : I use my own domain name server (bind), not the ones offered by by registrar (they do offer an API, and an interface has be written, and is present for acme.sh - see many examples here).
when I replace $ZONE, $KEY_NAME $KEY_HMAC with my info, I could add a txt record named "myzone.mydomain.tld" that contains "hello".
[22.05-RELEASE][admin@pfSense.xxxxx-hotel-fumel.net]/root: nsupdate -d > server ns1.xxxx-hotel-fumel.net > zone xxxxx-hotel-fumel.net > key hmac-sha512:update eYQiVAutEEAxxxxxxxxxxxxxxxVoCxOQ/jwBeA10EPeE7vwEdFT11QYs1YhO9zDCaJwzkuZp0w== > update add myzone.xxxxx-hotel-fumel.net 60 TXT "hello" > send Sending update to 2001:41d0:2:927b::3#53 Outgoing update query: ;; ->>HEADER<<- opcode: UPDATE, status: NOERROR, id: 46154 ;; flags:; ZONE: 1, PREREQ: 0, UPDATE: 1, ADDITIONAL: 1 ;; ZONE SECTION: ;xxxxx-hotel-fumel.net. IN SOA ;; UPDATE SECTION: myzone.xxxxxxx-hotel-fumel.net. 60 IN TXT "hello" ;; TSIG PSEUDOSECTION: update. 0 ANY TSIG hmac-sha512. 1664436399 300 64 6+N5xxxxxxxxxxxxhRMphgp69wR 2+t+aFdoPsF8plurhcN0Xo4GpMuQsg== 46154 NOERROR 0 Reply from update query: ;; ->>HEADER<<- opcode: UPDATE, status: NOERROR, id: 46154 ;; flags: qr; ZONE: 1, PREREQ: 0, UPDATE: 0, ADDITIONAL: 1 ;; ZONE SECTION: ;xxxx-hotel-fumel.net. IN SOA ;; TSIG PSEUDOSECTION: update. 0 ANY TSIG hmac-sha512. 1664436399 300 64 IoxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxLsQunveQ5o hwTwviKjz79jiO8Bdre57PF4zzSlZA== 46154 NOERROR 0 > quitOn my master domain dns server (bind) , I saw :
29-Sep-2022 09:26:39.225 update-security: client @0x7f842439cb60 2001:470:1f12:5c0::2#50387/key update: signer "update" approved 29-Sep-2022 09:26:39.225 update: client @0x7f842439cb60 2001:470:1f12:xxx:2#50387/key update: updating zone 'xxxx-hotel-fumel.net/IN': adding an RR at 'myzone.xxxx-hotel-fumel.net' TXT "hello"Now, lets dig :
[22.05-RELEASE][admin@pfSense.xxxx-hotel-fumel.net]/root: dig myzone.xxxx-hotel-fumel.net TXT +short "hello"The acme.sh dnsapi look like pure rocket science, but the concept is actually simple.
You have to prove to Letsencrypt that you own (== rent) your domain name.
There are several ways to do this, and one is : if you can prove that you can access and modify your domain "zone", Letsencrypt accepts that as a proof. It's this domain name that will get stored in your certificate after all.
And if you also can access the place were, for example, the web server files are placed, you can have that web server use the certificate, so the entire https (TLS) scheme start to work.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.