Match floating rules do not appear to be matching traffic
-
none of those rules show any hits -- the 0/0... What exactly are you trying to match on??
-
What interface(s) are those on?
What is the content of the Dell_XPS alias?
-
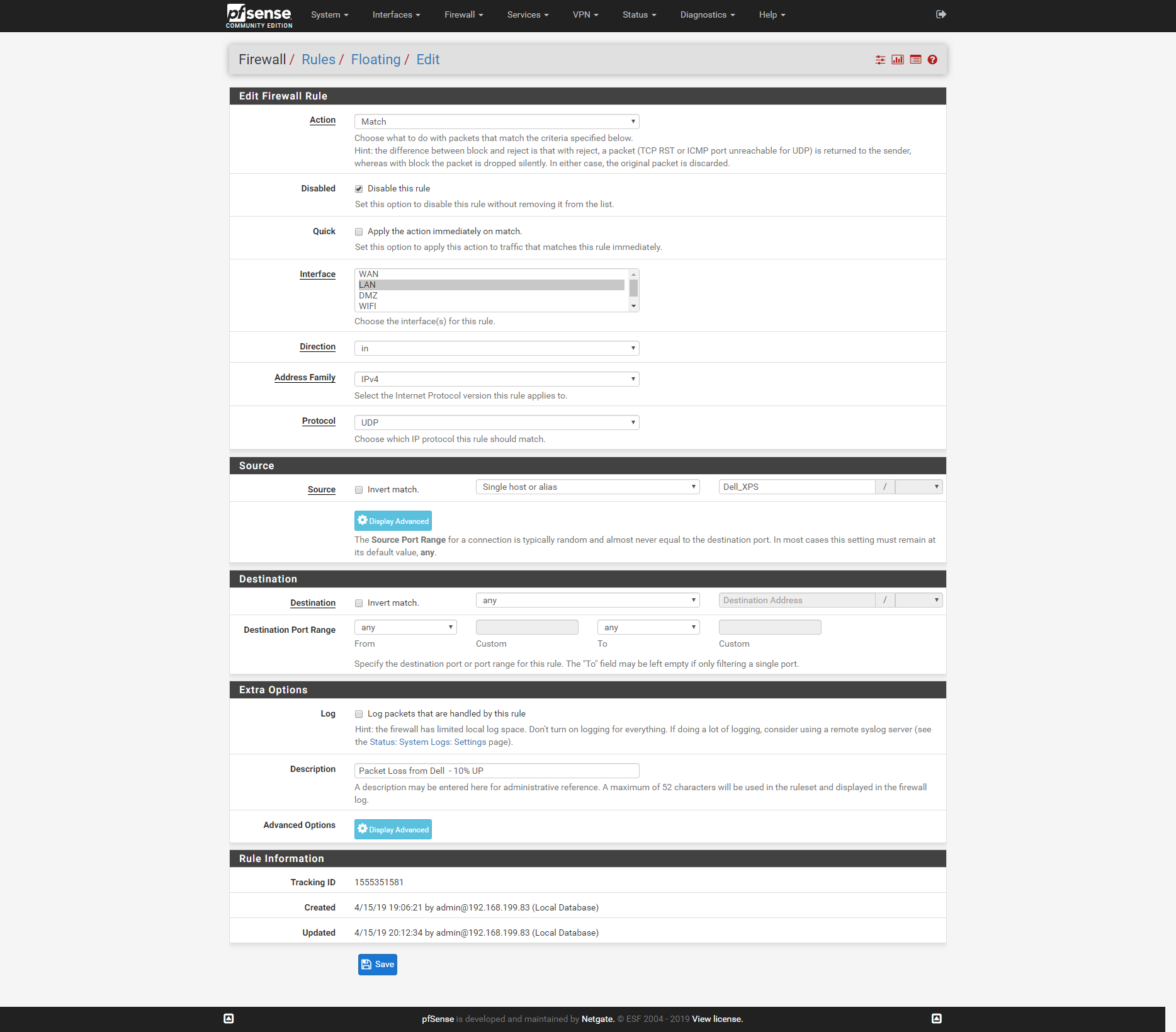
Apologies, I had just activated them for the screen grab (they would be off generally). I can certainly generate traffic and you will see the first rule match a few packets, but the second rule will still match nothing. This should be a relatively straightforward rule, just matching IPv4 UDP traffic with either source or destination address of the Dell_XPS (I have also tried with a direct IP address as well).
FWIW, I have also tried these rules directly on the LAN interface as a PASS action. In this case, the first rule works exactly as expected, however the second rule still matches nothing.
First Rule:
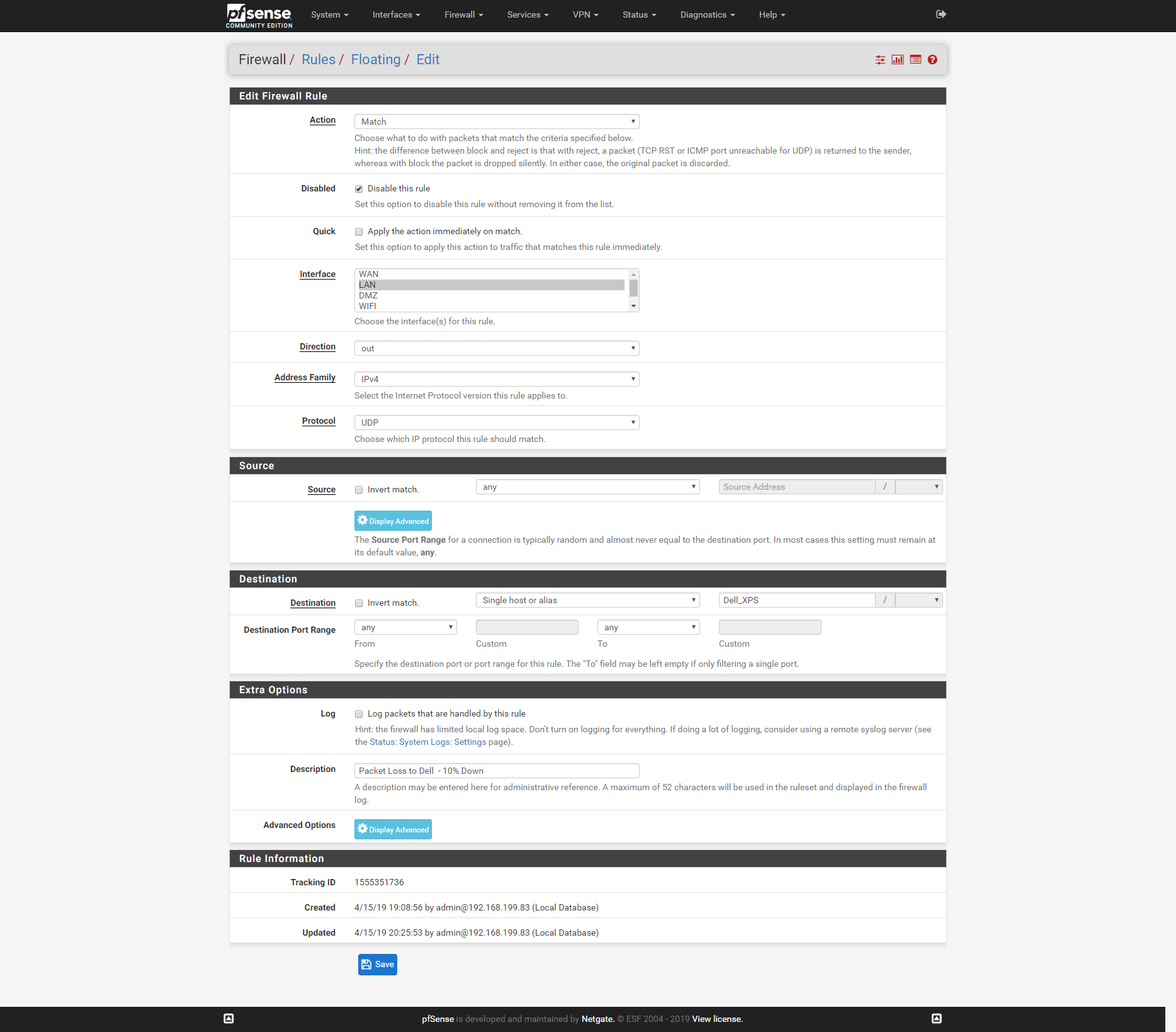
Second Rule:
-
The second rule will only match if you have passed connections into the Dell_XPS destination. Those rules match on connection establishment and cover the reply state as well. pfSense is a stateful firewall not a packet filter so reply traffic is automatically matched by the state created for it on state establishment.
-
@Derelict said in Match floating rules do not appear to be matching traffic:
Those rules match on connection establishment and cover the reply state as well. pfSense is a stateful firewall not a packet filter so reply traffic is automatically matched by the state created for
Hmm, so the intention was to create separate rules to enable separate Traffic Shaping Limiters, that could be enable and disabled to simulate packet loss for up or down traffic.
-
So make them. You match on connection establishment and set the in and out limiters.
https://docs.netgate.com/pfsense/en/latest/book/trafficshaper/limiters.html
Make a rule that sets limiters that have packet loss in one direction. And another rule that sets limiters that have packet loss in the other.
-
@Derelict Ah, I think I gotcha (and trust me I have read that documentation page a few times).
So the two rules will actually match the same thing (i.e. source Dell -> anything), but then have differing limiters.
-
Yes.
-
@Derelict Hmm, not quite! OK, I switched the second rule to be source IP matched on the XPS. This didn't work as it didn't match anything still. So, I switched direct to "IN", which of course matches, but the limiter doesn't affect the outbound packet TO the XPS. The limiter TO the XPS is set the the a destination mask.
The matches still don't make any sense either. By this I mean that whilst I can injected packet loss via the first rule for packet IN to the LAN interface (upstream) at a constant 10%, the rule says it has only matched 100 or so packets, yet 5000+ have passed.
-
Then the rule is wrong. This really does work.
How about you post everything you have done. The limiters, how they are set on the rules, the alias contents, etc. If you post floating rules be sure you detail the whole rule so we can see what interface the rules are on and the direction, etc.