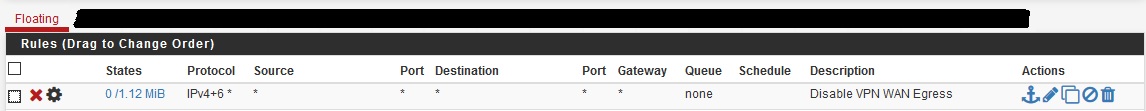
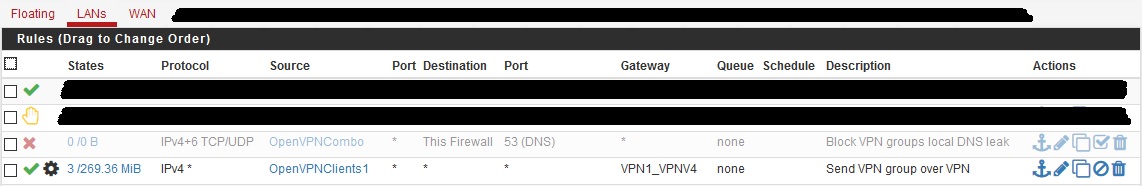
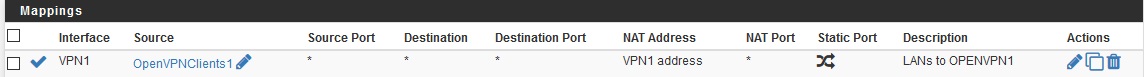
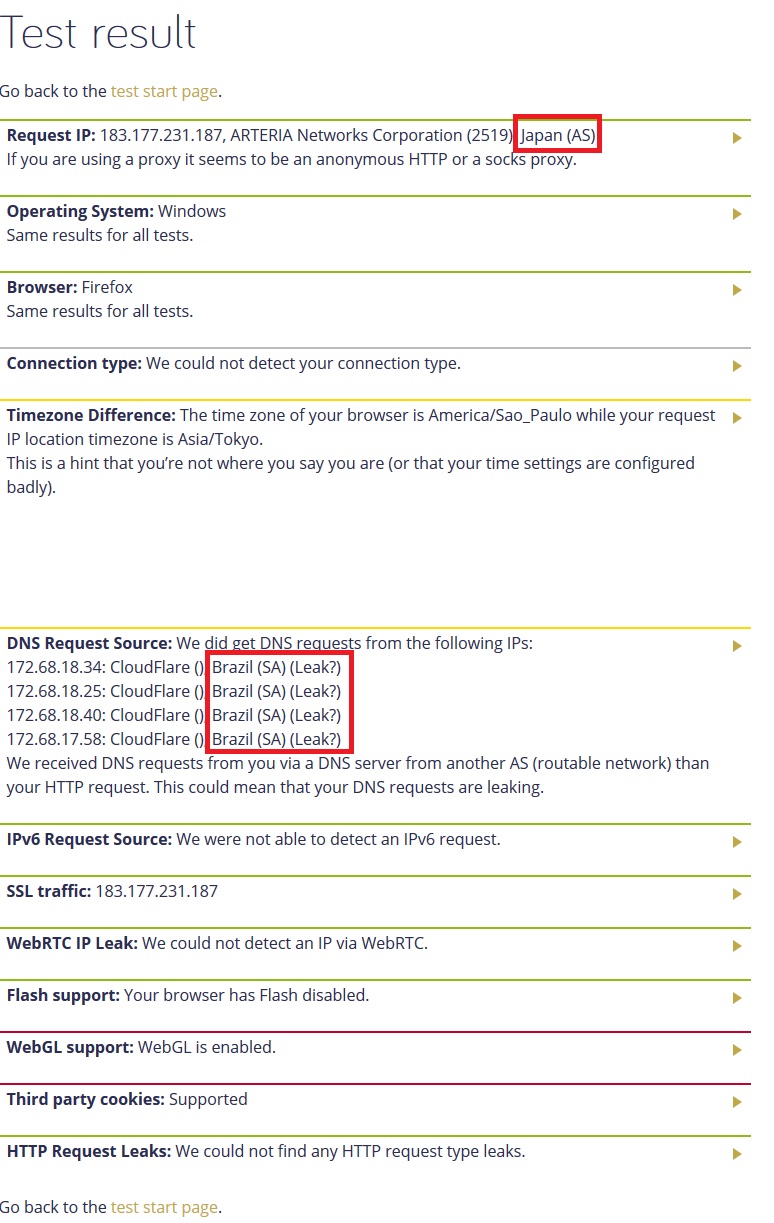
Own Country DNS being used (DNS Leak)
-
You didn't say if you specified your DNS to push to your clients via VPN - OpenVPN - Servers - Edit - Advanced Client Settings - DNS Server enable and DNS Server 1 etc.
-
hmm... i have no openvpn server setup... this is a client setup not a server, are you saying i should set up a openvpn server so the openvpn clients will resolve dns from the country its from ? dont really get it either way....
I want my openvpn clients to use dns resolver, currently they are resolving my own country dns... so right now i have static ips for the vpn (OpenVPNClients1) however i am not setting any dns for the static ip so they will go through the dns resolver.
maybe im not being clear i edited the op with a picture of how its working.
-
No, I misunderstood you. I thought by 'OpenVPN client', you meant your external users trying to connect to your pfSense OpenVPN server instance. I didn't realize you meant you were using pfSense itself as an OpenVPN client to some other server, and by 'clients' you mean users whose traffic you want redirected into your tunnel.
You're trying to fix a DNS leak. You could try editing your resolver config to specify that the outgoing interface is the OpenVPN one only and not All.
-
@KOM said in Own Country DNS being used:
You could try editing your resolver config to specify that the outgoing interface is the OpenVPN one only and not All.
wont that interfere with other lan clients that are not using the vpn server ?
-
No, it just means Resolver will use the VPN tunnel to talk to the roots and authoritative DNS.
-
youre sugestion does work, however isnt there another way? clients not on vpn will resolve the vpn dns too, so perhaps if vpn drops will lan clients also loose connection ? also isn't this a security issue ?
is there really no other way ?
-
however isnt there another way?
Possibly. I Googled for 2 minutes to find that first solution for you. Maybe there are more. Usually the server end pushes DNS down to the client, or it's part of the client config. I don't know as I use user VPNs, not router VPNs.
so perhaps if vpn drops will lan clients also loose connection ?
Definitely. That is a weakness of routing DNS through a VPN tunnel.
also isn't this a security issue ?
Extremely minor IMO. Unless you are an international man of mystery being hunted by the NSA, CIA and FBI, I very much doubt that it matters if some DNS server has logged that your WAN IP did a lookup on it.
-
thanks for your help @KOM however i will not be using this way as that can interfere with lan clients (ie if vpn drops).
will be waiting for some more input on this maybe its possible with a rule without blocking dns completely. -
I don't think you will find an acceptable resolution. To stop DNS leaks, you must use your VPN provider's DNS. That meas you can't use pfSense's DNS Resolver for that unless you tunnel it like I showed you.
You might compromise by routing only your OpenVPNClients DNS traffic through the tunnel via policy routing. Then if the tunnel dropped, only those users would be affected.
-
@KOM said in Own Country DNS being used (DNS Leak):
OpenVPNClients DNS traffic through the tunnel via policy routing
that seems promissing mind showing how or links that may help me ?
-
Actually I'm not sure that would work if you're using resolver. It would only work if you were using an external DNS like Google or Cloudflare. Policy routing simply means specifying a gateway based on the traffic type. You're already doing it when you send traffic from a specific group out the tunnel in your LAN rules.