Problems with Unifi AP and firewall rules
-
Hey guys just setting up a Unifi AP at my parents house. I have a quad port NIC and have their main network at 192.168.1.0/24 and their Unifi on it's own at 192.168.2.0/24. I manage the AP from a computer on the 192.168.1 network so they are on different subnets.
The problem is if i don't have an allow all rule on the Unifi network, when i try to manage the AP it always says disconnected, even though the wifi still works. Obviously i don't want an allow all rule at the top as i want to segregate my wifi from my main lan.
Here is the rule at the top. Any ideas? I was up all night trying to figure this out.
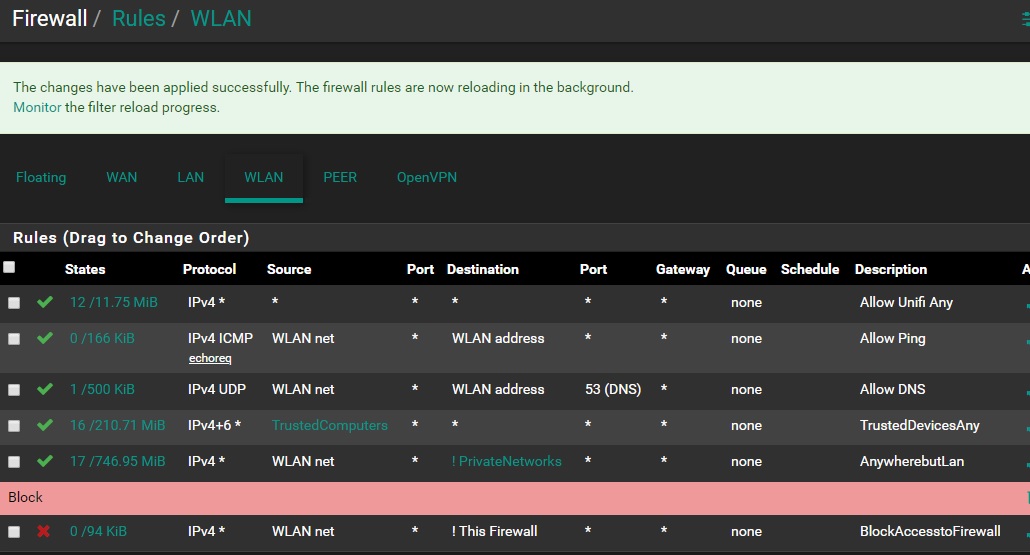
-
You need to allow the access points to communicate to the controller, I don't see a rule for that. If the controller is on the lan, you need a rule to allow the controller to talk to the ap on the lan tab.
-
The unfi AP should have its own static IP assigned by you to it on the wifi network, use that IP in your firewall rule, if you haven't already. I have an unifi AP but set up separate SSIDs and put them on VLANS back to the pfSense device, as SKY Q devices require their tv set top boxes to be on the same LAN as their tablets for viewing recordings. So VLAN 1 bridged and VLAN2 (guest) locked down. But i'm going off topic here.
But from what i remember the AP will remember your PC IP as its controller and will attempt to connect to it, but that is only after device discovery stage, at device discovery stage you need to be on the same L2 network segment.
-
hey guys, thanks for the responses. The unifi has an ip of 192.168.2.2, it is also included in the "Trusted Computers" alias that has an any/any rule on the WLAN interface. That doesn't seem to work. I also do a 192.168.2.2 any/any, that also says disconnected on the controller sometimes. the only way it works is with the first rule that is any/any. That is the only reliable way for some reason but defeats the purpose of segregating my wifi clients.
-
Why do you even bother with segregation at your parents home?
-
only because i bought a box to run pfsense there and it should be fairly easy. my network at home is way more complicated and i am able to do it there. That and the fact that they have their old friends over and they click on anything and everything and i just want to separate them from the lan which also has my backup unraid server on.
-
Understandable. I only asked because, these days, wifi is the LAN with wired devices having fallen by the wayside. As soon as you said you had a server there, that made the difference.
At my house, I don't split off the wifi from the LAN as I've only got a few PCs, tablets and phones to worry about.
-
Kom,
ya, i really just don't want some click happy 70 year old infecting my server with all my kids lifetime photos. I try to go wired for everything, when we had our house built, i was able to fully wire everything and just use wireless like you said with phones and tablets.
-
Hi, in the rule "Allow Uinfi Any" put the SOURCE IP of your UniFi controller.
I do have a rule like that, and it's work with my UniFi controller.
I do have 3 UniFI switcher and one UniFi AP Pro.You can also enable Client Isolation on UniFi AP.
They called it "Access Control". In order to have Access Control applied to a Wireless Network (SSID), you need to enabled "Guest Policy" for your wireless network
I think you can found it under "Settings"---> "Wireless Networks" and EDIT your SSID.Then you can enable "Guest Policy"When enable it they will not be able to communicate with other hosts.
The only why to communicate with other hosts on a guest network is by using the Allowed Subnets section to white lists IPs. (using CIDR notation)
-
for the Unifi controller, can i use just a computer to be the controller when i need to look at something? i don't have an actual cloud key, etc.
-
Yes you can. You can install the UniFi Controller to your computer, just for checking and manage the UniFi AP.
https://www.ui.com/download/unifi/
-
@CiscoX ok that's what I am doing now, just trying to follow the instructions you gave :)
-
You should also read some guides and YouTube, that's what i did
You may found lot of help here too.
https://help.ubnt.com/hc/en-us/categories/200320654-UniFi-Wireless -
thanks CiscoX, really appreciate it!
-
Hi, i have a similar setup but used VLANs to separate traffic. Example:
LAN = 192.168.1.1 (default)
On the LAN network I have internal resources (NAS) and network management (Unify controller)
The Unifi Access Point also has a static ip on the 192.168.1.0 network. That way it can communicate with the controller and no firewall rules are needed.Then I have created a VLAN for WLAN. On the unify AP you can then associate that VLAN with a particular SSID. So while you access point management is on 192.168.1.0 the actual wifi traffic is on the VLAN interface e.g. 192.168.20.0.
You mentioned you are using a 4 port NIC and I don’t know if you have a VLAN capable switch.
If you do have a VLAN capable switch you can run the VLAN ontop of the physical LAN interface and connect the AP to the switch using VLAN tagging.If you must use the 4 port NIC you could bridge 2 interfaces (LAN) and run the VLAN ontop.
Connect your Lan device on one port and the AP on the other.As for unifi controller. You can run it on a PC/linux/mac or just buy a cheap gen1 cloydkey.
I have used a raspberry pi to run the controller.
How about running the unify controller as a VM on unraid ? There are plenty of guides around. -
@xman111 said in Problems with Unifi AP and firewall rules:
Hey guys just setting up a Unifi AP at my parents house. I have a quad port NIC and have their main network at 192.168.1.0/24 and their Unifi on it's own at 192.168.2.0/24. I manage the AP from a computer on the 192.168.1 network so they are on different subnets.
The problem is if i don't have an allow all rule on the Unifi network, when i try to manage the AP it always says disconnected, even though the wifi still works. Obviously i don't want an allow all rule at the top as i want to segregate my wifi from my main lan.
Here is the rule at the top. Any ideas? I was up all night trying to figure this out.

The first rule is passing everything IPv4 to ANY.
-
You do understand if your putting the controller on a different segment than the AP you would have to do L3 adoption of the AP..
https://help.ubnt.com/hc/en-us/articles/204909754-UniFi-Device-Adoption-Methods-for-Remote-UniFi-ControllersThat great and all that you want to isolate a guest wireless network.. But that doesn't mean your AP management network can not be on the same L2 as your controller, and be the lan network.
So put controller and AP on same network.. Then create a vlan for whatever ssids you want to run... You isolate those vlans from talking to what you don't want them to talk to..
BTW: Your rule there on the end that says blockaccesstofirewall.. is actually the OPPOSITE of that... Your blocking everything BUT the firewall IPs, since you have it with ! setup..
-
John,
thanks as always for your advice.. first of all, i fixed that block firewall, don't know how i missed that.
Ya, i read the L3 adoption thing as well. Also, just to confirm, even though I have multiple open physical ports on my NIC, I should still run my main wireless and any guest network on VLAN's?
-
you don't have to run the interface on pfsense as vlan if you have them open..
So you have this say..
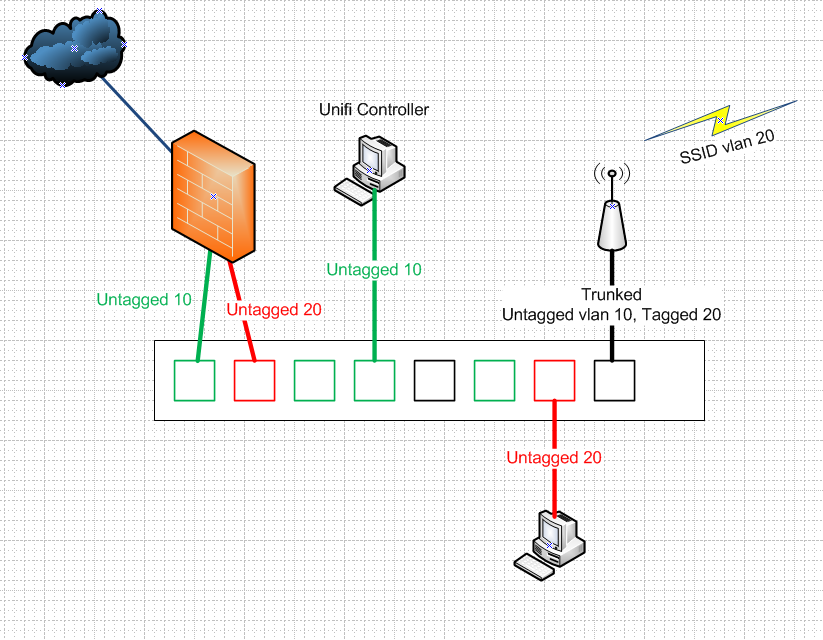
Your vlans would have to be created in your switch... But pfsense doesn't need to know about them.
And your AP needs to know about which network to put on what vlan... But sure uplinks to pfsense can be untagged to different physical nic.
So vlan 10 on your switch is the L2 your lan network is on, where your controller and AP management IP sit, say 192.168.10/24
And guest network vlan 20, is say 192.168.20/24
-
thanks John, that's great!!