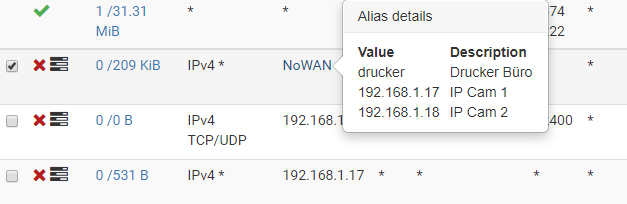
Alias firewall block rule not blocked!
-
This is a rule that passed the traffic from one client on LAN to my Cable Modem interface:
@181(1526110841) pass in quick on igb4 route-to (igb5 134.3.212.1) inet from 192.168.1.20 to 192.168.100.1 flags S/SA keep state label "USER_RULE: PC TC4400 Modem" [ Evaluations: 1048 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: pid 79204 State Creations: 0 ] @182(1417115627) pass in quick on igb4 inet from 192.168.1.0/24 to any flags S/SA keep state label "USER_RULE: Allow ALL IPv4" -
@mrsunfire said in Alias firewall block rule not blocked!:
Does
pfctl -vvsr | grep -A3 1526110841show anything more? -
Are you mixing and matching current data with old?
-
Right now the old config works. But I post it anyways:
@181(1526110841) pass in quick on igb4 route-to (igb5 134.3.212.1) inet from 192.168.1.20 to 192.168.100.1 flags S/SA keep state label "USER_RULE: PC TC4400 Modem" [ Evaluations: 946 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: pid 41920 State Creations: 0 ] @182(1417115627) pass in quick on igb4 inet from 192.168.1.0/24 to any flags S/SA keep state label "USER_RULE: Allow ALL IPv4" -
Are the states that you posted citing rule 181 old data or new?
We need to be looking at the same rule set as the state table or we are just wasting time.
-
They were the same rule set. I restored the config againto that point. But this time its working.
I will try to get the problem up again and post the same things again...
-
OK I've now checked the latest config again and now here are connections to WAN, I'm really confused:
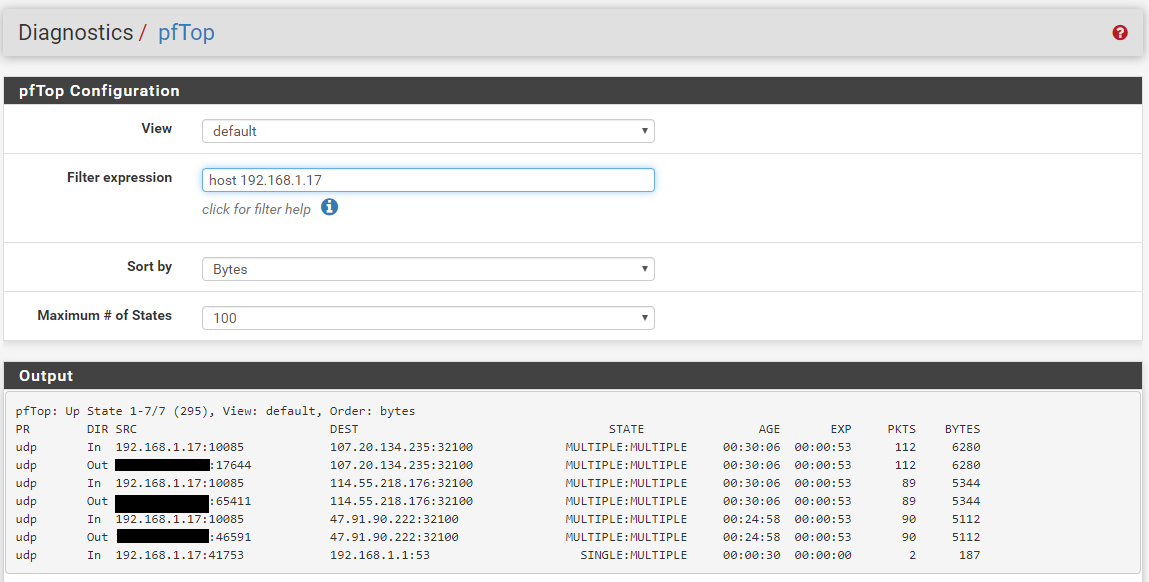
igb4 udp 114.55.218.176:32100 <- 192.168.1.17:10085 MULTIPLE:MULTIPLE age 00:28:43, expires in 00:00:48, 54:33 pkts, 3840:1352 bytes, rule 175 id: 000000005cd29094 creatorid: 732cab7f igb5 udp xxx:65411 (192.168.1.17:10085) -> 114.55.218.176:32100 MULTIPLE:MULTIPLE age 00:28:43, expires in 00:00:48, 54:33 pkts, 3840:1352 bytes, rule 139 id: 000000005cd29095 creatorid: 732cab7f lo0 tcp 127.0.0.1:6379 <- 127.0.0.1:26058 ESTABLISHED:ESTABLISHED -- igb4 udp 107.20.134.235:32100 <- 192.168.1.17:10085 MULTIPLE:MULTIPLE age 00:28:43, expires in 00:00:48, 54:54 pkts, 3840:2208 bytes, rule 175 id: 000000005cd29098 creatorid: 732cab7f igb5 udp xxx:17644 (192.168.1.17:10085) -> 107.20.134.235:32100 MULTIPLE:MULTIPLE age 00:28:43, expires in 00:00:48, 54:54 pkts, 3840:2208 bytes, rule 139 id: 000000005cd29099 creatorid: 732cab7f lo0 tcp ::1[3493] <- ::1[26068] ESTABLISHED:ESTABLISHED -- igb4 udp 47.91.90.222:32100 <- 192.168.1.17:10085 MULTIPLE:MULTIPLE age 00:23:35, expires in 00:00:48, 45:41 pkts, 3200:1680 bytes, rule 182 id: 000000005cd295e5 creatorid: d0585f4d igb5 udp xxx:46591 (192.168.1.17:10085) -> 47.91.90.222:32100 MULTIPLE:MULTIPLE age 00:23:35, expires in 00:00:48, 45:41 pkts, 3200:1680 bytes, rule 141 id: 000000005cd295e6 creatorid: d0585f4d igb3 udp 255.255.255.255:4944 <- 0.0.0.0:6134 NO_TRAFFIC:SINGLE -- igb4 udp 192.168.1.1:53 <- 192.168.1.17:44606 SINGLE:MULTIPLE age 00:00:06, expires in 00:00:24, 1:1 pkts, 59:128 bytes, rule 182 id: 000000005cd2a1af creatorid: d0585f4d igb4.200 udp 8.8.8.8:53 <- 10.0.1.5:11824 SINGLE:MULTIPLE -
So what are rules 175, 139, 182, and 141 in the current rule set?
-
175 is forcing a VOIP client to use a specific gateway (Multi WAN config).
@175(10000001) pass in quick on igb4 inet proto udp from 192.168.1.19 to <negate_networks:2> keep state label "NEGATE_ROUTE: Negate policy routing for destination" [ Evaluations: 1632 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: pid 41920 State Creations: 0 ] @176(1524056818) pass in quick on igb4 route-to (igb5 134.3.212.1) inet proto tcp from 192.168.1.19 to any flags S/SA keep state label "USER_RULE: VOIP UM Gateway"@139(1000011065) pass out inet all flags S/SA keep state allow-opts label "let out anything IPv4 from firewall host itself" [ Evaluations: 16781 Packets: 3841 Bytes: 285161 States: 0 ] [ Inserted: pid 41920 State Creations: 13 ] @140(1000011066) pass out inet6 all flags S/SA keep state allow-opts label "let out anything IPv6 from firewall host itself"@182(1417115627) pass in quick on igb4 inet from 192.168.1.0/24 to any flags S/SA keep state label "USER_RULE: Allow ALL IPv4" [ Evaluations: 2225 Packets: 471566 Bytes: 563093528 States: 42 ] [ Inserted: pid 41920 State Creations: 1750 ] @183(1525366696) pass in quick on igb4 inet6 from 2a02:8071:xxx::/64 to any flags S/SA keep state label "USER_RULE: Allow ALL IPv6"@141(1000011161) pass out route-to (igb5 134.3.212.1) inet from xxx to ! 134.3.212.0/22 flags S/SA keep state allow-opts label "let out anything from firewall host itself" [ Evaluations: 8760 Packets: 477427 Bytes: 563273095 States: 76 ] [ Inserted: pid 41920 State Creations: 4639 ] @142(1000011162) pass out route-to (igb5 fe80::201:5cff:fe6b:e046) inet6 from 2a02:8071:xxx to ! 2a02:8071:800::/56 flags S/SA keep state allow-opts label "let out anything from firewall host itself" -
Oh I see that the second host in that Alias (192.168.1.18) also is not working and passes the traffic to WAN! That's new.
pfTop: Up State 1-6/6 (673), View: default, Order: bytes PR DIR SRC DEST STATE AGE EXP PKTS BYTES udp In 192.168.1.18:10090 107.20.134.235:32100 MULTIPLE:MULTIPLE 00:41:52 00:00:22 150 8412 udp Out xxx:50497 107.20.134.235:32100 MULTIPLE:MULTIPLE 00:41:52 00:00:22 150 8412 udp In 192.168.1.18:10090 114.55.218.176:32100 MULTIPLE:MULTIPLE 00:41:52 00:00:22 114 6940 udp Out xxx:22381 114.55.218.176:32100 MULTIPLE:MULTIPLE 00:41:52 00:00:22 114 6940 udp In 192.168.1.18:10090 47.91.90.222:32100 MULTIPLE:MULTIPLE 00:31:10 00:00:22 98 5704 udp Out xxx:2161 47.91.90.222:32100 MULTIPLE:MULTIPLE 00:31:10 00:00:22 98 5704 -
@mrsunfire said in Alias firewall block rule not blocked!:
igb4 udp 47.91.90.222:32100 <- 192.168.1.17:10085 MULTIPLE:MULTIPLE
age 00:23:35, expires in 00:00:48, 45:41 pkts, 3200:1680 bytes, rule 182
id: 000000005cd295e5 creatorid: d0585f4d@182(1417115627) pass in quick on igb4 inet from 192.168.1.0/24 to any flags S/SA keep state label "USER_RULE: Allow ALL IPv4"
[ Evaluations: 2225 Packets: 471566 Bytes: 563093528 States: 42 ]
[ Inserted: pid 41920 State Creations: 1750 ]Was not blocked. I still maintain you are confused. I have no idea what state things are in, what should be blocked and what is or isn't because you keep saying you are restoring configs, etc. Stick with ONE configuration, detail exactly what you think should or should not be happening, don't click around trying to fix it, and we might be able to find out where the misconfiguration is.
-
The 182 is the LAN to WAN allow any:any rule.
-
Yeah I know.
-
I‘m still at the same config. Now I rebooted and it works again. I will try to reboot and see if the problem reappears.
-
Remember that the block rule was above the 182. I don‘t get it why that rule passes for that host.
-
Was it? I would need to see it in the current active rule set at the time the state was created.
-
Dude stop rebooting and restoring old configs and work with what is there and can find out what you have misconfigured..
-
Well I did that because I want to find out what was the problem with the old config. Right now it works. Maybe after next boot it's not working anymore. I don't know.
-
@mrsunfire said in Alias firewall block rule not blocked!:
Maybe after next boot it's not working anymore. I don't know.
nonesense.. Unless you change freaking your confings around again.... Or you have problems with the rules loading? in general? Or you have delay in aliases working.. But if your putting in IP vs fqdn there should be no delay like resolving them.. that could maybe cause a problem.
But if your trying to figure out what is allowing something out you have to work with current rules and states, and don't reboot in the middle, etc.
-
Thats the actual state:
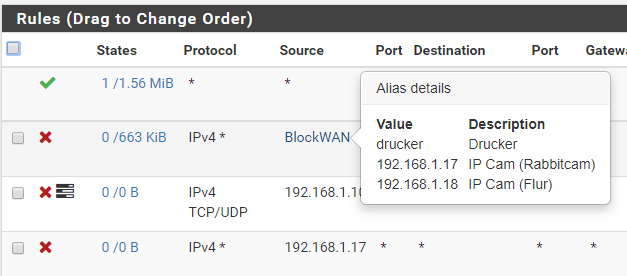
And nothin in pfTop. How it should be. But it's the same as the old config. Thats what confused me.