New to pfSense
-
@johnpoz What I am wanting is for all devices to be able to talk with each other. The FreeNAS server will be connected to the 10g switch however mobile devices on the Ubiquiti need to be able to read files from the server. From the reading I have done on VLANs as long as the rules are set correctly within pfSense (and the individual switch) then they should be able to communicate with each other.
My understanding is the pfSense box is only 1g not 10g?
-
The 7100 has 2 sfp+ ports that can do 10g you just need the sftp+ modules for it. They are $49
And then your switch has sfp+ as well - so need one there and the fiber to connect them.
-
@johnpoz Of course! I totally forgot about the sfp+ ports as I am using ethernet.
Would you happen to have a link to the modules I would require? I had a look online and it seems there are different types of modules that suit different switches.
-
Would these be the sfp+ modules that I need for both the pfSense and NetGear?
pfSense:
https://store.netgate.com/SFP-10GBase-SR-Transceiver-P2575.aspxNetgear: https://www.netgear.com.au/business/products/switches/modules-accessories/axm761.aspx
They’re 50/125um (sr) which I’m guessing they both need to be identical
-
So, I ended up acquiring from a friend a UniFi XG-16 switch and have used this instead of the Netgear.
I have re-configured the Netgate to use ix0 as LAN and have this connected via sfp+
pfSense --> UniFi XG-16 --> UniFi 16-150w (PoE)
Connected to the XG-16 is a desktop computer and the PoE switch has both AP's and the Cloud Key (Gen. 2). IoT devices are connected through the AP's on a separate VLAN (configured in pfSense).
The issue I am having is the wireless AP's show as connected for the first minute or 2 then appear as disconnected however IoT devices can still connect to the network.
Is there a firewall rule I need to add that allows the Cloud Key to see the AP's and communicate with them? I think I read somewhere that the CK requires port 8080 however I could be wrong. I disconnected the pfSense box and used my old router and there are no issues with the CK connecting and monitoring the AP's (and switches). Any help would be much appreciated!
-
I have been at pfSense, the UniFi switches and VLANS for the past week and everything I have watched on YouTube or read doesn’t seem to work.
I have tried pinging devices on different VLANS with zero success. I’m guessing I am doing something majorly wrong but I can’t figure it out.
I have set up 3 VLANS within pfSense 20, 40 & 50. These are:
VLAN 20: 10.10.20.0/24
VLAN 40: 10.10.40.0/24
VLAN 50: 10.10.50.0/24On the UniFi switches, I have both connected via SFP+ passing all VLAN traffic. My wireless network (IoT - VLAN50) is working so I know the VLANs are passing through the UniFi switches correctly. I have tagged the appropriate ports on the UniFi switches for the computers on VLAN’s 20 & 40.
Is there something else I can try? My pfSense box is the xg-7100 and I have assigned the ix0 interface (10gbe) as the LAN if that helps. My configuration is:
pfSense -> UniFi 16xg -> 16-150w
I have VLAN20 on the UniFi 16xg and VLAN50 on 16-150w
-
And what rules did you put on your vlan interfaces with pfsense?
If your unifi controller is on vlan A, and AP is vlan B - then you would have to use layer3 adoption..
-
The UniFi swiitches, AP's & Cloud Key are on the LAN address and have been statically assigned:
16XG - 10.10.10.101
16-150 - 10.10.10.102
AP (1) - 10.10.10.103
AP (2) - 10.10.10.104
Cloud Key - 10.10.10.105The AP's are connected to the 16-150w and are on VLAN50. All mobile devices connecting to this VLAN (10.10.50.2 etc) operate correctly and the Cloud Key can communicate with the switches and AP's to get updates.
16XG has 2 ports tagged for VLAN20 and the 16-150w has 2 ports tagged for VLAN40.
What I am trying to do is ping a computer from VLAN20 on the 16xg switch to VLAN40 on the 16-150w switch however the request times out.
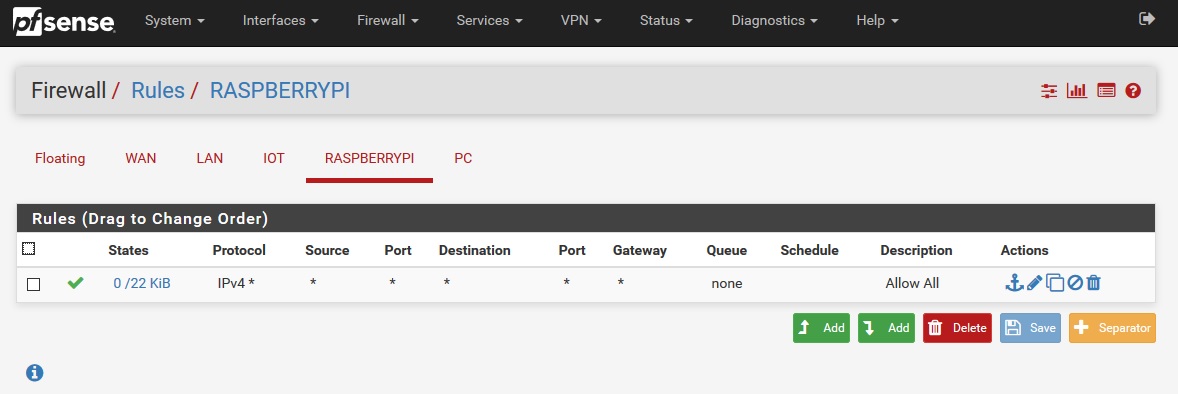

I have only set these firewall rules for now as I want to establish the connection between the computers on different VLAN's then I will add more firewall rules. Is there something else I need to do? I have seen several tutorials on YouTube where they are doing what I require however they are able to ping the other computers.
-
Well your rules would for sure allow ping ;) Between those vlans..
Could be firewall on the actual host your pinging?
Can device in PC vlan ping the IP of pfsense on PI vlan? Can device in PI vlan ping the IP address of pfsense on PC vlan?
I would do a simple sniff on pfsense to see what is going on.. So for example if you know you can ping pfsense PI IP from PC.. Then sniff on PI Interface on pfsense while you while you ping an IP in pi vlan from pc vlan... Do you see pfsense send the ping on to the IP in the pi vlan - where is the answer?
If your devices can not ping the other vlans Pfsense IP - then you have something else wrong.. Like not using pfsense as their gateway..
example here I can ping the IP of pfsense dmz IP (192.168.3.253) from my pc in lan (192.168.9/24)
$ ping 192.168.3.253 Pinging 192.168.3.253 with 32 bytes of data: Reply from 192.168.3.253: bytes=32 time<1ms TTL=64 Reply from 192.168.3.253: bytes=32 time<1ms TTL=64So that tells me hey I can get to pfsense interface for my dmz vlan... So If I could not ping say the 192.168.3.32 device on the dmz.. I would sniff on the pfsense dmz interface.. Do I see that ping being sent?
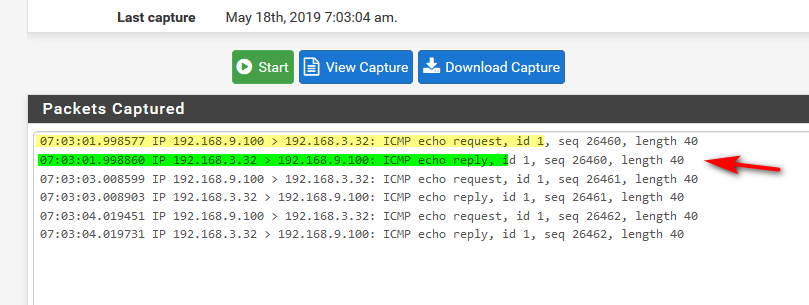
Do you only see the yellow, and not the green?
-
I can't believe it, on my PC tagged to VLAN20 I have Eset Antivirus... disabled it and I am able to ping both the LAN gateway and VLAN50 gateway!
It always seems to be the easiest solution usually works :)
I am having trouble pinging my Raspberry Pi however that could be because it is running Private Internet Access through OpenVPN and changing the gateway.
If I decide to run OpenVPN through pfSense, if there is a disconnection from the PIA server will it automatically reconnect to PIA or does it fall back to the WAN IP?
-
@Sir_SSV said in New to pfSense:
it is running Private Internet Access through OpenVPN and changing the gateway.
Yeah that could be a problem..
As to reconnecting to a vpn service on pfsense - yeah if you set it to reconnect it should.. All comes down to why there was a disconnect, etc. etc
-
Ok, thanks. I’ll have to do some research to see how to set up OpenVPN on pfSense.
To prevent a device on Vlan50 (IoT) seeing a device on either Vlan20 or Vlan40, should I do an Alias to block these or should I set a firewall rule on VLAN50 to block any protocol source: any destination: LAN net?
-
Rules are evaluated on the interface the traffic enters on, from the network its connected too.. So if you don't want devices on vlan X to talk to vlan Y, then on vlan X you would put a rule that blocks access to vlan Y.
Above rules that would allow, say your dest any rule that allows access to the internet..
Rules are evaluated top down, first rule to trigger wins - no other rules are evaluated.
-
Ok, so finally I have everything up and running! It took a while however everything is working perfectly right down to OpenVPN and the RPi's (including a "Killswitch" in case the VPN network goes down it does not default to the WAN address) :)
However, I have one more question: on Vlan30 resides my FreeNAS server. This is only accessible by the computers on Vlan 20. FreeNAS sends email/status updates/critical alerts via Gmail (TLS over port 587). I do not want the FreeNAS server to be connected to the internet but would like it to be able to send these updates via Gmail. I have tried several rules however none seem to be working (it mentions could not resolve Hostname).
Is this possible to do? I was attempting to open the address/port for Gmail however this did not work.
Edit: After having a think about what Firewall rules I was using, I worked it out. Due to not having an internet connection on Vlan30, I made rules for connection to DNS servers then rule for Gmail's IP range (74.125.0.0/16)
-
I’ve followed the SG-3100 manual to the letter and configured the port 4 as VLAN port. Every thing seems okay except there’s no internet from that port. I don’t know what to do know.
-
And what rules did you put on that initerface? Did you dick with the automatic outbound nat? Network network did you put on that interface.. Are you clients able to ping pfsense IP on that interface?
-
Hi John,
I put IPv4 and IPv6, allow anything to anything. Haven’t touched NAT outbound rules at all (still default to automatic). I connect FMC transmitter/receiver pair to that interface (LAN port 4 or OPT2). At the other far end is a gigabit switch. An access point plugs into the switch. A music server plugs into the switch as well. I have not yet tried pinging from music server to the pfSense IP.
WAN connects to a Comcast Xfinity modem/router which offers wired and wireless internet.
-
I’ve just pinged pfSense IP 192.168.1.1 on the interface. No problem. Actually, ping works on all 4 ports including the configured one and 3 other “raw” ports.
-
What exact IP did you put on pfsense interface in this new vlan? Sure the mask is not /32? Is dhcp working on this vlan? You didn't mess with outbound nat say per some idiot vpn guide? And its set to automatic for your wan?
-
It’s 192.168.100.1
Before getting on the road, I fiddled with system/advance/system tunables, 2 bridge/filter related parameters and it seemed to work. Laptop connected to that interface shows internet. Will dig more after work.