TAP, can't access OpenVPN Server external IP address
-
Hi!
I have a very simple bridge situation:
OpenVPN Server, pfsense,
tap
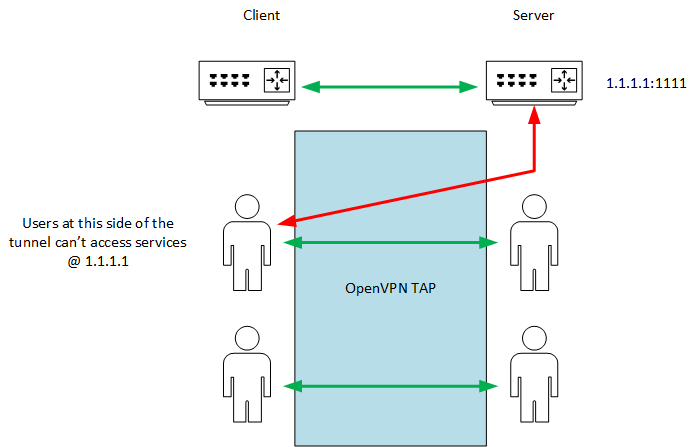
External IP (for example): 1.1.1.1
OpenVPN server port: 1111OpenVPN Client, pfsense,
tap.I have good connectivity between any clients behind both servers in both directions.
But I can't access 1.1.1.1 from OpenVPN Client side.
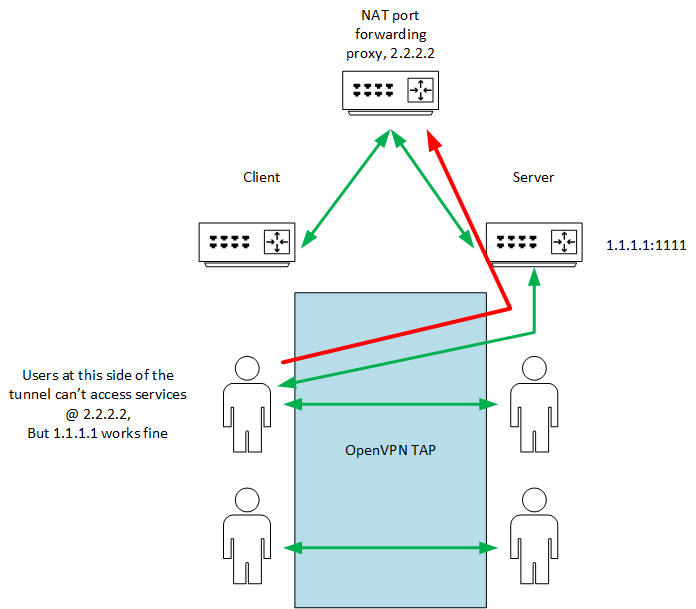
There is nothing wrong with OpenVPN config itself.Let's say I have completely independent server 2.2.2.2. If I'm doing port forwarding (with NAT) from 2.2.2.2:1111 to 1.1.1.1:1111, and changing OpenVPN server address to 2.2.2.2 (So now I'm connecting to 1.1.1.1 via 2.2.2.2), I'm suddenly having a connection to 1.1.1.1 services! While loosing the ability to connect to 2.2.2.2.
So the problem is exactly with OpenVPN client in TAP mode, which filters direct connections to openvpn server ip address.
Packet sniffing shows data goes through connection at the client side, but nothing arrives at server side. It seems like the problem lays on the client side.What am I'm missing there?
P.S. The client config is here, but I don't see anything suspicious:
dev ovpnc3 verb 1 dev-type tap dev-node /dev/tap3 writepid /var/run/openvpn_client3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 192.168.1.253 engine cryptodev tls-client client lport 0 management /var/etc/openvpn/client3.sock unix remote 1.1.1.1 1111 (fictional ip) ca /var/etc/openvpn/client3.ca cert /var/etc/openvpn/client3.cert key /var/etc/openvpn/client3.key tls-crypt /var/etc/openvpn/client3.tls-crypt ncp-ciphers AES-128-GCM comp-lzo no resolv-retry infinite fast-io mssfix 1400 fragment 1400 sndbuf 393216 rcvbuf 393216 mlock fast-ioP.S. To clarify things:
When I use port forwarding proxy, there's nothing wrong with 1.1.1.1
UPD:
Just confirmed the very same behavior with freshly installed OPNSense, which suggests the reason to be quite deep inside.UPD2: Okay, I found the workaround, but it's obviously very messy:
I've created a port forwarding proxy at the client side. So now, pfSense OpenVPN client connects to local proxy (which is actually behind this pfSense firewall), and the proxy forwards traffic to the actual Server ip address.