Problem routing back traffic not coming through the default gateway
-
My ISP, while it does not include a static IP address with my plan, weirdly so it does include a 4-core 4GB mem VPS instance no extra cost. Like most VPSes it comes with a static IP address and so I've been trying to tunnel or somehow link it to my local network with an always-on tunnel so I'm not relying on DDNS which tends to fail most of the times to have access home.
I tried two approaches and both gave me the same result; I can ping from any place in the network and get a response, I can even run remote Wireshark and capture the traffic but when I try to access remotely from a public IP address that's when traffic is blocked at the first router on the way out. It does make it to the destination and the server tries to respond but it is blocked.
Using the local public IP address works fine. For the remote public IP address I duplicated the existing NAT inbound rules and attached them to the new interface handling the remote traffic.
This was my first approach:
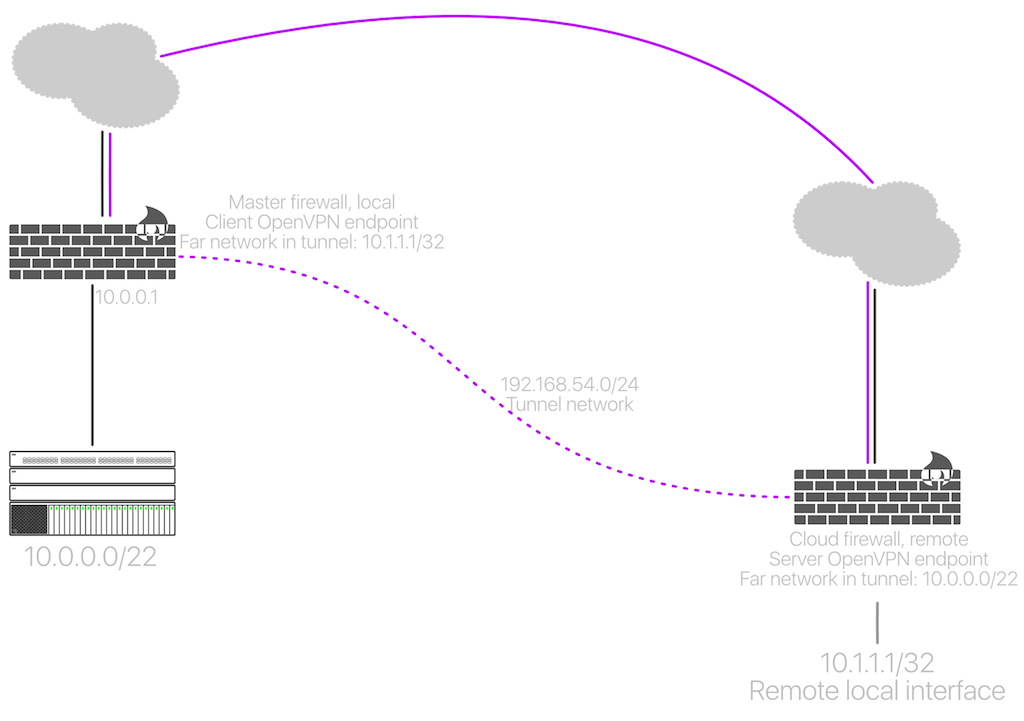
In Wireshark there was a lot of retransmissions on the way out, it was slightly a different error than the second method but I'm failing to remember and I lost the screenshots. :/
This is the other way:
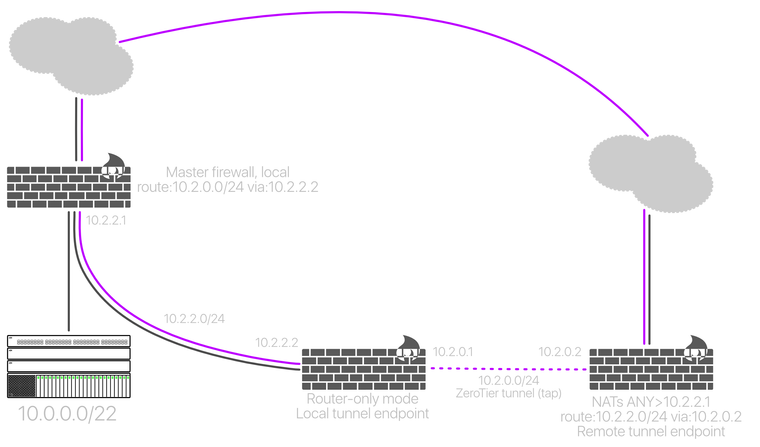
This time I didn't just take screenshots, I saved the capture:
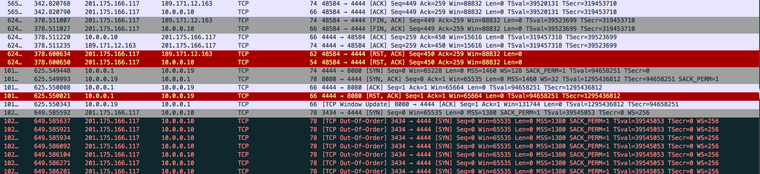
I tried using the local public IP --the light colors-- then I tried using the remote public IP. I'm trying to connect to TCP port 4444.
Right now the tunnel is still up (the second approach), unlike my main firewall, the middle box that tunnels to the remote is a physical endpoint and I just left it there. I can log in to it and I can log in to the cloud instance from the local network.
I know very little, if at all, about Wireshark just a few tidbits I've picked up browsing here, "TCP Out-Of-Order" makes me think it's an asymmetric routing problem and it kinda fits, I'm just not sure how to solve it.
Outbound NAT is performed only in the interfaces directly connecting to public IP addresses, that's two points only. Anywhere else is only pure routing end to end.
I'm logging every single rule on any interface too: the firewall won't log the blocked traffic, it only is seen in Wireshark.
Any ideas what am I doing wrong?
Thanks !
-
I just tried another method, the "layer 2 approach" as I'm naming the artboards in my I-didn't-have-the-patience-for-Visio app:
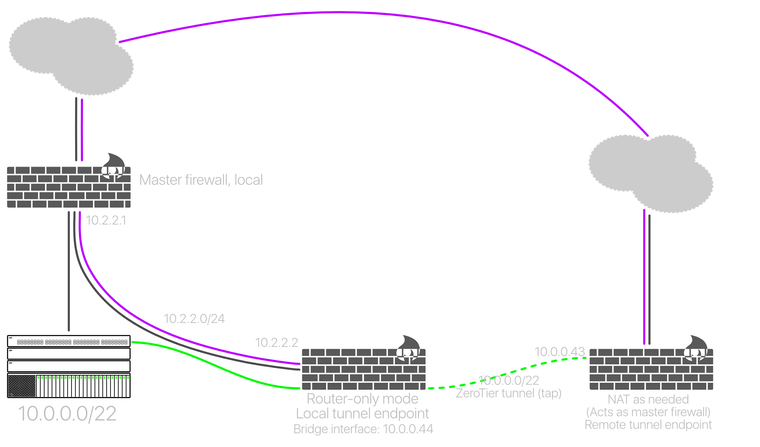
I figured: if I cut the middle man it should work without issues. It didn't turn out as planned:
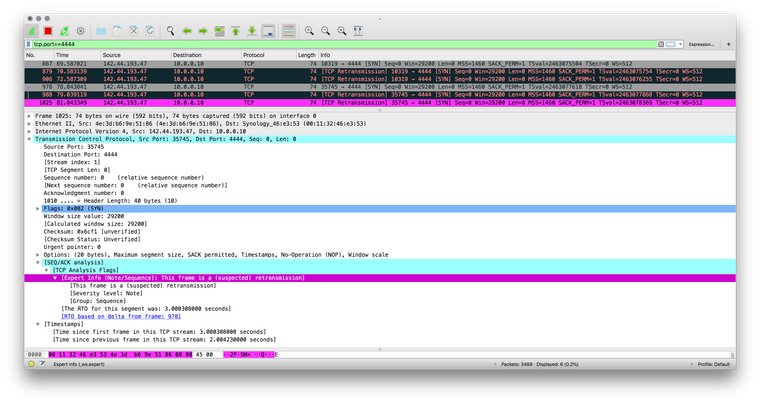
The capture above is taken from the internal (tunnel) interface of the remote firewall. It's still blocked. Now I'm really confused as to what's going on. The only thing I can think of is adding it as a second gateway in the DHCP server but I'm not holding my breath...and won't work for devices not using DHCP. :(
The remote firewall's public IP address is in a subnet (i.e; a single address of a /23) contrary to the local which is a /32 PPPoE address, I'm thinking about some sort of static routes hack to that but then how would it be reached to bring up the tunnel in the first place. I need to finish my TCP/IP-something-something-drawings book ASAP.
At this rate I'm going to end up becoming a graphic designer with a broken network.
