Cert update dates
-
@jimp one more question - is there a simple way to test that email works from letsencrypt ? I don't think I got any before Acme updated certificates and now have to wait for 60 days...
-
No test I'm aware of. I know they still do it, though, as I received an e-mail from them over the weekend. I forgot to check the cron box on one of my lab systems.
-
@chudak said in Cert update dates:
is there a simple way to test that email works from letsencrypt ?
Oh, yes !
Get some certs from the Staging server. As soon as you get one of them, you'll be mail stormed after de delay.
I never received a mail that told me that I was late to renew a 'real' certificate. All my certs just renew by itself after 60 days - or the period I choose, which is generally somewhat less then 60 days.Be aware that you can 'redo' your cert manually 5 times a week - just hit the renew button.
You could also renew from the command line : just run what the cron runs :
/usr/local/pkg/acme/acme_command.sh renewallYou'll see that it comes back with
.... Renewal number of days not yet reached.So, force it like this :
/usr/local/pkg/acme/acme_command.sh renewall -forceYou'll be seeing a boat-load of lines on the screen, and finally, after the DNS delay etc, you obtain a new cert.
(don't forget to restart all services that use the certificate- as you already figured out)....... Rm2nmWhlbYL+R+4lLJmrPlkl6tSkxk05AOHF -----END CERTIFICATE----- [Mon Apr 15 13:03:04 CEST 2019] Your cert is in /tmp/acme/V2_brit-hotel-fumel.net//brit-hotel-fumel.net/brit-hotel-fumel.net.cer [Mon Apr 15 13:03:04 CEST 2019] Your cert key is in /tmp/acme/V2_brit-hotel-fumel.net//brit-hotel-fumel.net/brit-hotel-fumel.net.key [Mon Apr 15 13:03:04 CEST 2019] The intermediate CA cert is in /tmp/acme/V2_brit-hotel-fumel.net//brit-hotel-fumel.net/ca.cer [Mon Apr 15 13:03:04 CEST 2019] And the full chain certs is there: /tmp/acme/V2_brit-hotel-fumel.net//brit-hotel-fumel.net/fullchain.cer [Mon Apr 15 13:03:04 CEST 2019] Run reload cmd: /tmp/acme/V2_brit-hotel-fumel.net/reloadcmd.sh IMPORT CERT V2_brit-hotel-fumel.net, /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.net/brit-hotel-fumel.net.key, /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.net/brit-hotel-fumel.net.cer update cert![Mon Apr 15 13:03:11 CEST 2019] Reload success [Mon Apr 15 13:02:54 CEST 2019] key /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.netnsupdate.key is unreadable [Mon Apr 15 13:02:54 CEST 2019] Error rm webroot api for domain:dns_nsupdate [Mon Apr 15 13:03:00 CEST 2019] key /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.netnsupdate.key is unreadable [Mon Apr 15 13:03:00 CEST 2019] Error rm webroot api for domain:dns_nsupdate [Mon Apr 15 13:03:00 CEST 2019] key /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.netnsupdate.key is unreadable [Mon Apr 15 13:03:00 CEST 2019] Error removing txt for domain:_acme-challenge.brit-hotel-fumel.net [Mon Apr 15 13:03:00 CEST 2019] key /tmp/acme/V2_brit-hotel-fumel.net/brit-hotel-fumel.netnsupdate.key is unreadable [Mon Apr 15 13:03:00 CEST 2019] Error removing txt for domain:_acme-challenge.brit-hotel-fumel.net[2.4.4-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: ls -al /tmp/acme/V2_brit-hotel-fumel.net total 248 drwxr-xr-x 5 root wheel 512 Apr 9 16:50 . drwxr-xr-x 3 root wheel 512 Feb 7 14:37 .. -rw-r--r-- 1 root wheel 431 Apr 15 13:03 accountconf.conf -rw-r--r-- 1 root wheel 209317 Apr 15 13:03 acme_issuecert.log drwxr-xr-x 3 root wheel 512 Apr 9 16:51 brit-hotel-fumel.net -rw-r--r-- 1 root wheel 105 Apr 15 12:59 brit-hotel-fumel.netnsupdate_acme-challenge.brit-hotel-fumel.net.key -rw-r--r-- 1 root wheel 13 Apr 15 12:59 brit-hotel-fumel.netnsupdate_acme-challenge.brit-hotel-fumel.net.server drwxr-xr-x 3 root wheel 512 Feb 7 14:37 ca -rw-r--r-- 1 root wheel 592 Apr 15 13:03 http.header drwxr-xr-x 2 root wheel 512 Apr 9 16:50 httpapi -rwxr-xr-x 1 root wheel 394 Apr 15 12:59 reloadcmd.sh [2.4.4-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root:Strange. It tries to delete
brit-hotel-fumel.netnsupdate.key
But the file is really called :
brit-hotel-fumel.netnsupdate_acme-challenge.brit-hotel-fumel.net.keyLooks like the "_acme-challenge.brit-hotel-fumel.net" part is missing when it constructs the file to delete.
Minor issue actually.@jimp : can you confirm ?
My settings :
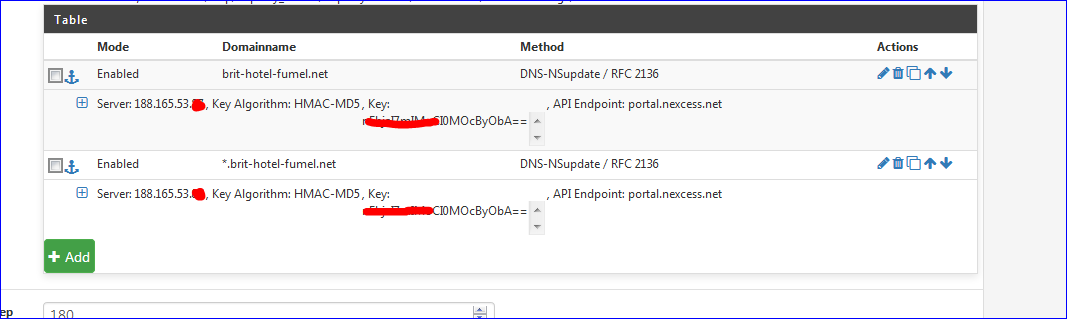
-
@Gertjan said in Cert update dates:
@chudak said in Cert update dates:
is there a simple way to test that email works from letsencrypt ?
Oh, yes !
Get some certs from the Staging server. As soon as you get one of them, you'll be mail stormed after de delay.
I never received a mail that told me that I was late to renew a 'real' certificate. All my certs just renew by itself after 60 days - or the period I choose, which is generally somewhat less then 60 days.I was looking for a simple way to either trigger email or see what certificates associated with my email.
Thanks for details !
-
@chudak said in Cert update dates:
Valid From: Tue, 08 Jan 2019 09:01:48 -0800
Valid Until: Fri, 05 Jan 2029 09:01:48 -0800That is not a ACME cert
-
To help with some of this confusion, ACME 0.5.7, which I just committed a few minutes ago, now uses RFC 2822 format dates to show the last renewal. This makes it consistent with the dates shown on other certificate-related pages.
-
@jimp Thanks looks good !
-
I am still not 100% sure what's going on with update dates.
So I am a new user of ACME and like it a lot!Last time I manually updated certificates were April 7th
I expected to start seeing emails 20 days before expiration sometime around 10th of July.
I actually saw that certificates were renewed yesterday June 7th.
What am I missing ?
Thx
-
It was automatically-renewed like it was supposed to be.
Certbot runs every day. It checks the dates. If it needs to be renewed it runs the process. If everything works you have a refreshed cert.
-
@Derelict said in Cert update dates:
It was automatically-renewed like it was supposed to be.
Certbot runs every day. It checks the dates. If it needs to be renewed it runs the process. If everything works you have a refreshed cert.
I get that, but why I did not get any emails ?
-
@chudak said in Cert update dates:
I get that, but why I did not get any emails ?
From who ?
acme works has the FreeBSD/Linux mentality : no news is good news.
There isn't a checkbox that states : "send me a mail" neither.
Although the question was asked before.When you visit your setup, and the cert is 3 or 4 week, just hit the Renew yourself, and observer the process.
When no errors, and you don't break things afterwards, renewing will just go fine in the future.edit : or : help yourself : write a small shell script that collects some data , activate it in the Action list and our done.
/usr/local/pkg/acme/acme.sh --home /tmp/acme/[your-domain]/ --listto see actual cert details.
-
Emails from where?
-
If you put your e-mail on the ACME key then Let's Encrypt (NOT pfSense/the firewall/etc) will send you an e-mail when it is close to expiring, but that only triggers if it's not renewed before the time they warn you.
Since the ACME package checks every day to see if it needs renewed, it gets renewed before that e-mail warning would fire off.
The firewall won't e-mail you anything about the certificates, but it makes entries in the main system log. If you have a central logging system you could have it flag those messages and alert you when things happen.
-
Hmm
letsencrypt has 90 days cycle, no ?
why then I see this (using the script by @Gertjan ):
/usr/local/pkg/acme/acme.sh --home /tmp/acme/XXXYYY/ --list Main_Domain KeyLength SAN_Domains Created Renew XXXYYY "" no Fri Jun 7 10:16:07 UTC 2019 Tue Aug 6 10:16:07 UTC 2019renew in 60 days ?
Also you say "If you have a central logging system you could have it flag those messages and alert you when things happen."
Any example of you do to flag messages ?
Thx
-
@chudak said in Cert update dates:
letsencrypt has 90 days cycle, no ?
The certificates expire in 90 days.
@chudak said in Cert update dates:
renew in 60 days ?
It renews then so that if there is a failure, you have time to fix the problem.
@chudak said in Cert update dates:
Also you say "If you have a central logging system you could have it flag those messages and alert you when things happen."
Any example of you do to flag messages ?No, that's all up to your logging/alerting/NMS system.
-
-
@chudak said in Cert update dates:
renew in 60 days ?
Check your own settings of your cert : bottom of the page :
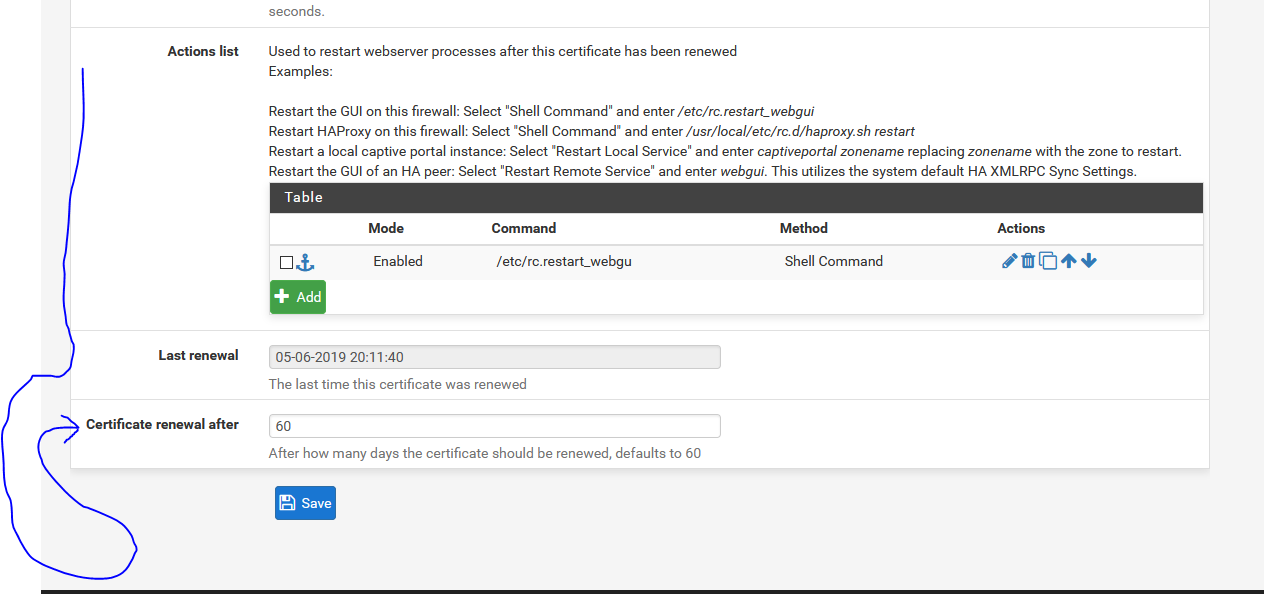
You see the last renewal date.
And the time - default 60 days - when it gets renewed.See my edit above how to implement a small shell script that sends a mail as an Action script.
-
Makes sense, changed to 90 days, and added the script to Certificate options Actions list (not sure if it will send email, but will be seeing in the logs for sure)
Thx!
-
Why would you want to wait until the certificate has already expired before you renew it?
Leave it at 60 and ignore it unless it fails to renew. The default settings are best.
-
I’m trying to find best way to be remained to do some manual actions for one certificate that is being managed by acme.
For pfsense 60 days overlapping/advanced updates will work fine.
But I need to get some emails in order to copy new certificate to my other server. (need to see how further automate this process)
Thx all for suggestions and useful tips