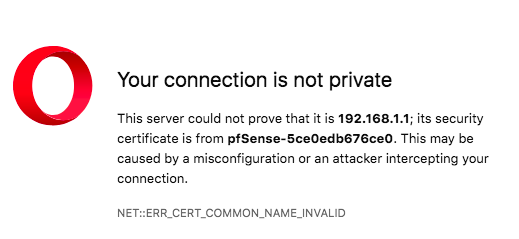
Opera Not Accepting Certificate (solved)
-
The solution is to create an actual cert with actual fqdn and ip that are listed in san of the cert and created by ca you trust. create a ca in pfsense, trust it and then create cert with that ca and use it for your web gui
-
@johnpoz Tried that before. I used the Internal CA I created for OpenVPN. Added the CA cert to Trusted Roots. Created a new webConfigurator cert and added it to Trusted Roots as well. Still prompted at FW logon. Don't know why but not a big deal. Must be me.
-
@johnpoz said in Opera Not Accepting Certificate:
"The solution is to create an actual cert with actual fqdn and ip that are listed in san of the cert and created by ca you trust. create a ca in pfsense, trust it and then create cert with that ca and use it for your web gui"
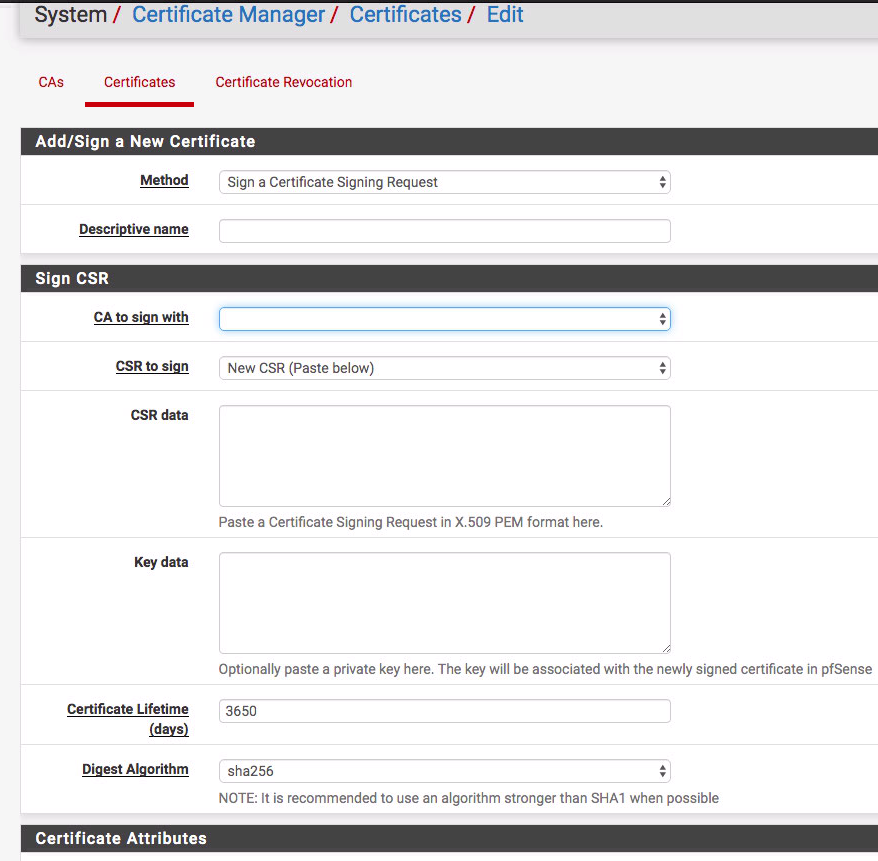
Thank you John for responding. I looked at creating a CA however, where in pfSense to trust it? See image below.
I looked here also, see image below. Thanks!
-
@provels said in Opera Not Accepting Certificate:
@johnpoz Tried that before. I used the Internal CA I created for OpenVPN. Added the CA cert to Trusted Roots. Created a new webConfigurator cert and added it to Trusted Roots as well. Still prompted at FW logon. Don't know why but not a big deal. Must be me.
Just for knowledge Provels, where or how to add to Trusted Roots?
-
@NollipfSense After you create the CA, from the CAs tab, choose the gear icon and export the CA cert.
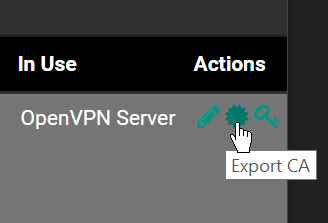
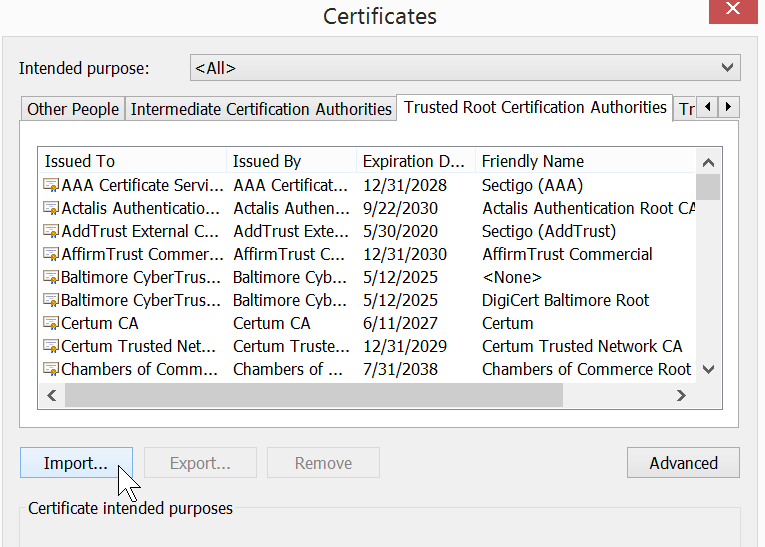
Then you can go to Opera's Menu\Settings\Advanced\Privacy and Security\Manage Certificates, choose the "Trusted Root Certificate Authorities" tab, click the "Import" button and browse to the cert that you exported. If you're a Windows person you can also Google up using the Microsoft Management Console to manage certs.
-
On a Mac click on the cert and trust it in keychain.
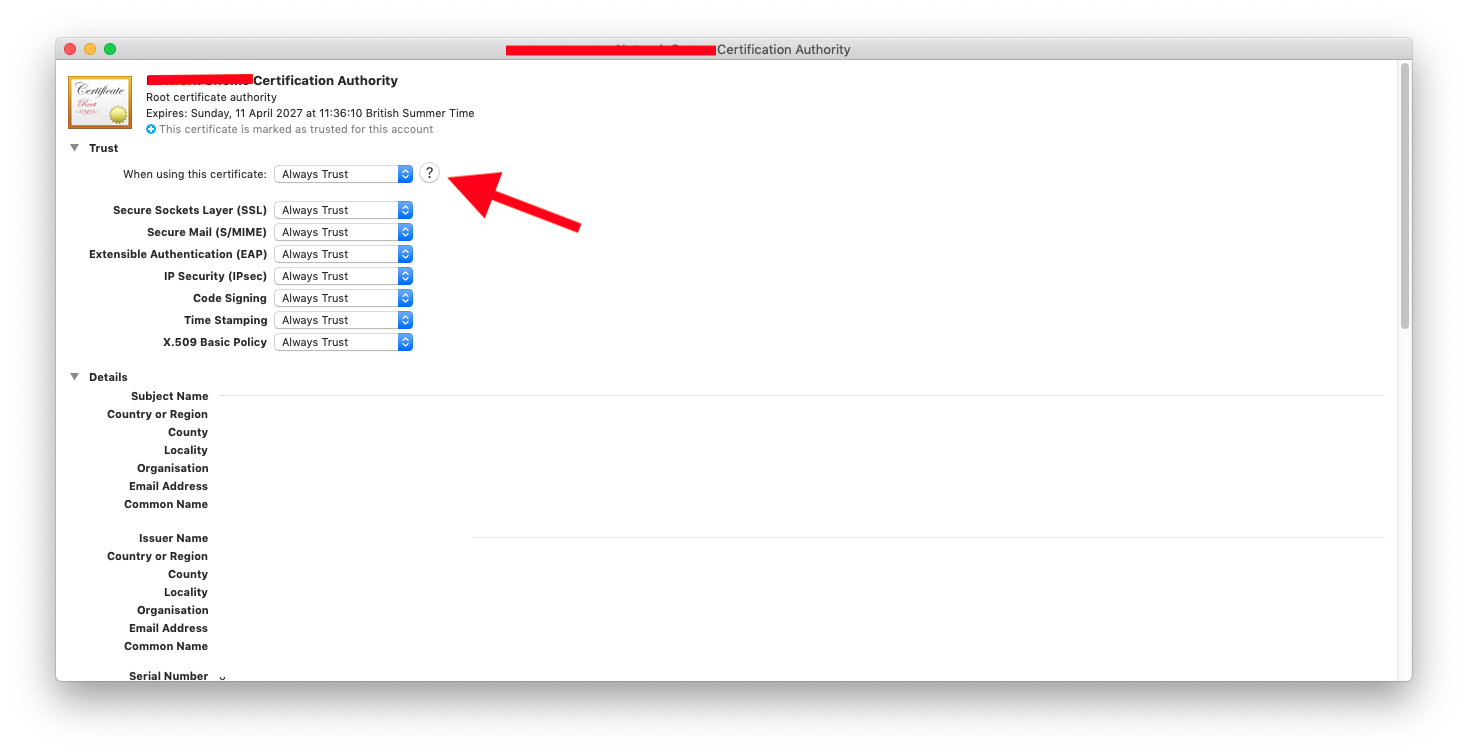
-
Here i have gone over this like 4 or 5 times over years with pictures every time... Here is the latest version since pics got lost in the forum update.
https://forum.netgate.com/post/831783
I use these certs singed by ca on all devices on my local network that need certs.. Make them good for 10 years and never have to touch them again. No need for acme, etc. And you can use rfc1918 in the san to access them without any complaints from the browser.
-
@provels I am using Opera version 60 and when one clicks on manage certificate, it launches Keychain...there is no option to import the. certificate.
-
This https://wiki.wmtransfer.com/projects/webmoney/wiki/Installing_root_certificate_in_Opera ?
-
@NogBadTheBad I had already done that before my first post...still no luck as Proovels had also discovered.
-
@NollipfSense said in Opera Not Accepting Certificate:
@NogBadTheBad I had already done that before my first post...still no luck as Proovels had also discovered.
Well Opera isn't looking at the Certs trusted by your computer, works fine for me using Safari.
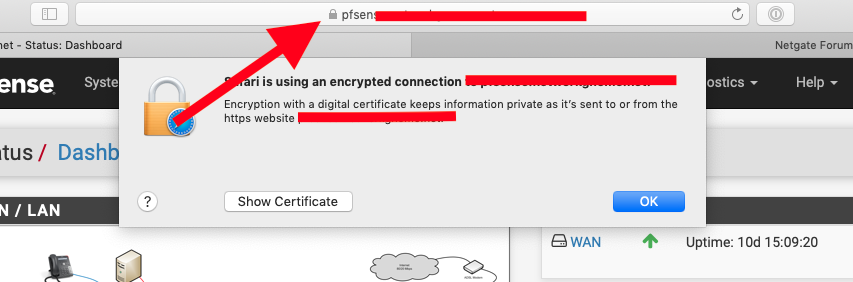
You should either use a browser that works or post on the Opera forum, it's not a pfSense issue.
https://forums.opera.com/topic/25032/certificates-refused-by-opera-accepted-by-other-browsers
-
@NogBadTheBad Well, I might try another browser other than Safari or Firefox as these are my regular web browsing browsers.
-
@Gertjan I am using Opera version 60 and when one clicks on manage certificate, it launches Keychain...there is no option to import the certificate. It doesn't present those pop up window as in the Windows OS.
-
Not a solution, but :
I just tried a self-mode cert, installed it in IE11 (Windows 7) -> This was a no go : vert is self signed IE refuses without any possible exception possible.
Firefox was more specific : self signed certs are refused - although I guess this could be over ridden with some internal settings. But in that case ALL self signed certs would be trusted, also the ones it finds on the net. That's a huge no go.
Better : I was using a Let's Enscrypt cert for my pfSense ** access, and "HTTP Strict Transport Security" was active.
this means I just can't replace certs for other certs (using other signing offices like myself) : this was a no go also.What works just great : if you can trust a 30 cm long Internet cable, it is possible to leave the GUI on plain http.
It's just you on the LAN - and only YOU - communicating over a 30 cm cable. Just watch that cable, and check that no body is wire tapping it, and you'll be safe. You shouldn't mind that info goes over that cable non-encrypted.
Put all other users on an second OPTx interface, and on this interface you just lock down any GUI access.
You'll be very safe, no cert hassle - nothing to set up, nothing to maintain.** Let's Enscypt root certs are trusted by any browser so this is also a click-it-and-forget-it solution.
-
Not sure why this is so difficult - can you not google?
On windows opera 60 just uses the windows cert store... Click on the manage your certs and install it..
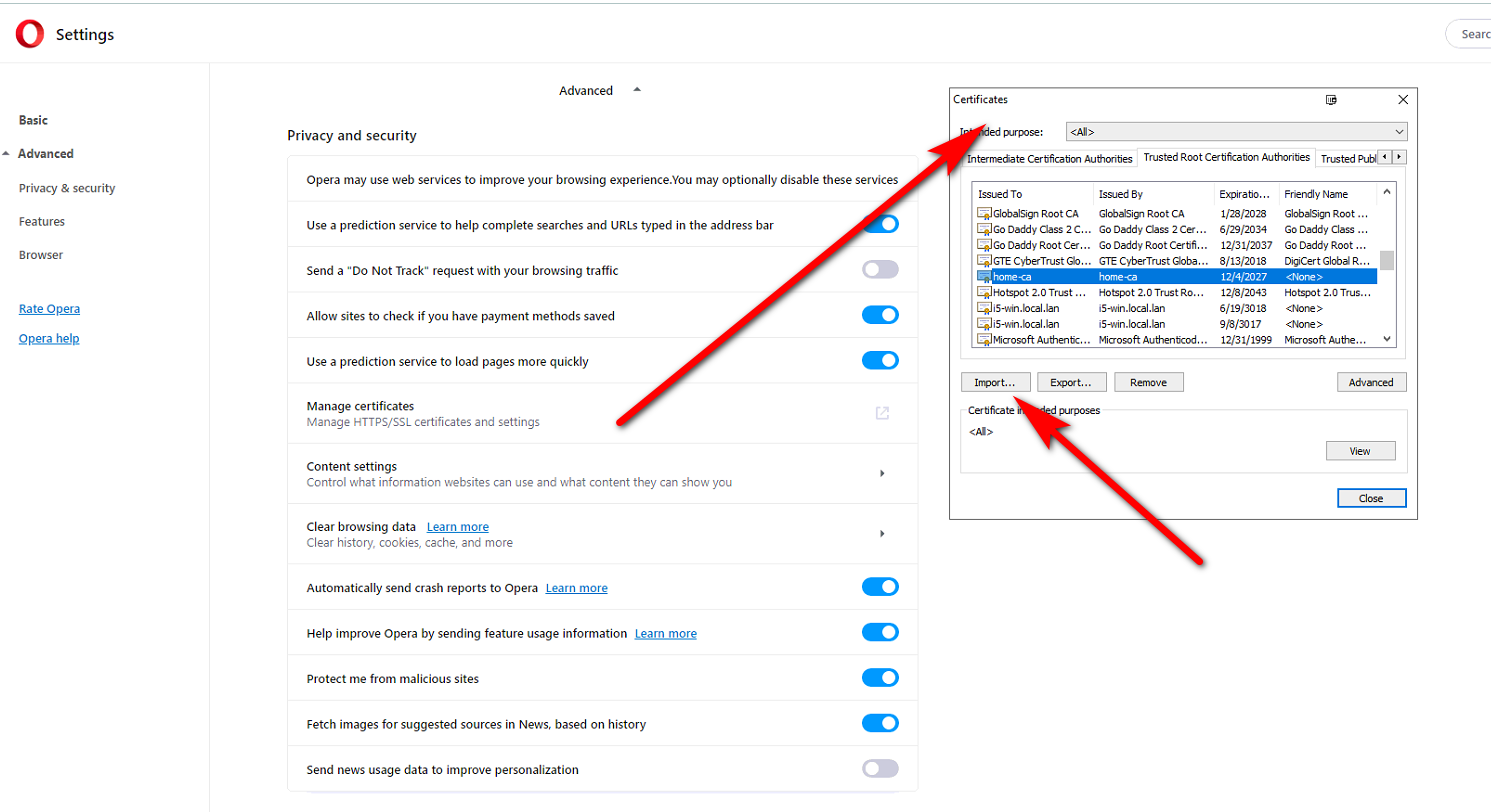
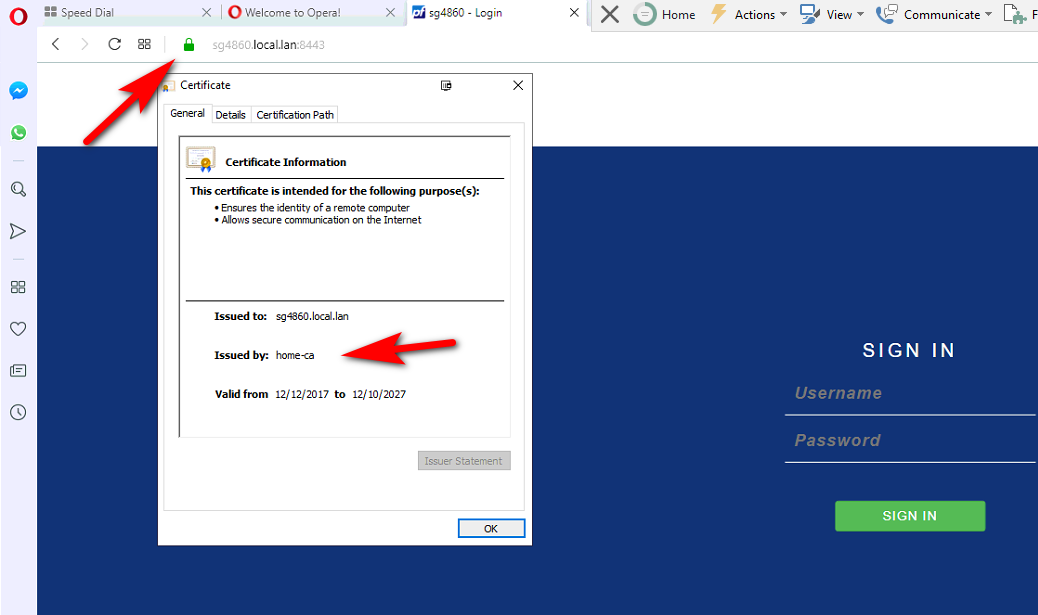
-
Thanks guys for chiming in...I got it working with Vivaldi browser that is very surprising considering it's a chromium like browser just like Opera. So, Vivaldi is for WebGUI.
-
@johnpoz He's using a Mac John

-
Then trust the CA on the mac..
Simple google show to click it to open it up on keychain access, copy it to system and then set its trust to always trusted..
-
@johnpoz said in Opera Not Accepting Certificate (solved):
Then trust the CA on the mac..
Simple google show to click it to open it up on keychain access, copy it to system and then set its trust to always trusted..
John, I said in the first post that it was set to always trust. It not the first time I am dealing with certificates.
-
I see this §$%&#!+ behaviour as well and that's why I switched to Opera (from Safari) where it was handled a bit easier.
I still don't get it why this is enforced on RFC1918 addresses as well. Makes no sense and is a PITA. Safari wants me to enter admin pwd just to access the GUI of a new bought switch (to unsuccessfully save an exception in keychain).
RFC1918 is RFC1918. That's why we have it.
</rant>