(SOLVED) Suricata Interfaces have to be manually Restarted
-
@bmeeks said in Suricata Interfaces have to be manually Restarted:
Let's compare MD5 hashes to see if your binary is the same as mine. Run this command from a shell prompt on the firewall:
md5 -q /usr/local/bin/suricataThe output should be:
cc5200e8369def9268b9e30c0c3f41c6Let me know what you get.
Here is what I got.
c962d5d995867c5baf3136035a34fac7 -
Okay. Thanks for the information. I've sent an email to my pfSense developer contact who works with me on the Suricata and Snort packages asking him to investigate. It's obvious the binary files are different. I would expect them to be the same.
I will wait to hear from him before taking any further action. The bug is fixed on my end so far as I can tell. I definitely saw the problem in the source code and fixed it there. So I'm wondering why the fix seems to be missing for users.
-
Thanks for the help Bill. I'll keep any eye out for an update on this. In the meantime, I'll try uninstalling and installing again just for the sake of being persistent. If anything changes on my end I'll let you know.
-
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
Thanks for the help Bill. I'll keep any eye out for an update on this. In the meantime, I'll try uninstalling and installing again just for the sake of being persistent. If anything changes on my end I'll let you know.
I doubt that will make any difference so long as it still downloads and installs the same binary. It really looks like to me that the binary built as suricata-4.1.4_2 is not "really" my new 4.1.4_2. It appears to still have the old version of my custom blocking plugin patch. That's the only way I can explain the "tree is null" error. I very explicitly fixed that error ...
 .
. -
@bmeeks said in Suricata Interfaces have to be manually Restarted:
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
Thanks for the help Bill. I'll keep any eye out for an update on this. In the meantime, I'll try uninstalling and installing again just for the sake of being persistent. If anything changes on my end I'll let you know.
I doubt that will make any difference so long as it still downloads and installs the same binary. It really looks like to me that the binary built as suricata-4.1.4_2 is not "really" my new 4.1.4_2. It appears to still have the old version of my custom blocking plugin patch. That's the only way I can explain the "tree is null" error. I very explicitly fixed that error ...
 .
.Yup, uninstall and install of 4.1.4_4 gave me the same md5 results as before.
-
the update appeared to me now on my pf 2.5
[2.5.0-DEVELOPMENT][root@pfSense.localdomain]/root: md5 -q /usr/local/bin/suricata
cc5200e8369def9268b9e30c0c3f41c6 -
I am seeing odd behavior, Suricata was running fine for awhile but when I got home from work around 6 I noticed the WAN instance had stopped, when I restarted it I lost all internet connectivity on all the devices on my network, once I stopped it everything immediately worked again, wondering if this is related to these bugs.
-
@bose301s said in Suricata Interfaces have to be manually Restarted:
I am seeing odd behavior, Suricata was running fine for awhile but when I got home from work around 6 I noticed the WAN instance had stopped, when I restarted it I lost all internet connectivity on all the devices on my network, once I stopped it everything immediately worked again, wondering if this is related to these bugs.
Yes, if you actually still have the non-patched binary running it will cause a crash. As I just posted in another thread, something unusual happened during the posting of the update and the new binary was actually missing my bug fix. You should get the MD5 hash I posted up above (and the same one user @kiokoman just posted about for pfSense-2.5.
-
@bmeeks OK, I got the same md5 as Raffi, should I reinstall, I already tried that but obviously didn't work as I still get the wrong md5. I don't want to go to 2.5 devel, I am on 2.4.4 p3.
-
Just sit tight and try again tomorrow. I reported the issue to the pfSense developer who posts my Snort and Suricata packages to the repository. Since the new file showed up in pfSense-2.5 DEVEL a couple of hours ago, I suspect the correct file will get posted to 2.4.4 RELEASE pretty soon.
-
Is this problem with no blocking and/or having to manually restart Suricata still occurring? I have been unable to reproduce this, and I've tried in both a 2.4.4 RELEASE virtual machine and a 2.5 DEVEL virtual machine. The blocking module now correctly senses and registers firewall interface IP changes without generating a "tree is null" error and without those invalid kernel IP message errors.
The MD5 hash values for the Suricata binary are different for pfSense 2.4.4 versus 2.5. This is due to the differences in the compiling libraries, but both versions do contain my fix for the problems above.
-
@bmeeks said in Suricata Interfaces have to be manually Restarted:
Is this problem with no blocking and/or having to manually restart Suricata still occurring? I have been unable to reproduce this, and I've tried in both a 2.4.4 RELEASE virtual machine and a 2.5 DEVEL virtual machine. The blocking module now correctly senses and registers firewall interface IP changes without generating a "tree is null" error and without those invalid kernel IP message errors.
The MD5 hash values for the Suricata binary are different for pfSense 2.4.4 versus 2.5. This is due to the differences in the compiling libraries, but both versions do contain my fix for the problems above.
Hi @bmeeks, unfortunately the problem is still around for me. I tried uninstall and reinstall this morning to see if anything changed, but the md5 is still the incorrect one I posted before. The behavior is still the same as well. I even tried to un/reinstall just before posting this to be sure nothing has changed since earlier this morning. The md5 is still not correct for me.
-
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
@bmeeks said in Suricata Interfaces have to be manually Restarted:
Is this problem with no blocking and/or having to manually restart Suricata still occurring? I have been unable to reproduce this, and I've tried in both a 2.4.4 RELEASE virtual machine and a 2.5 DEVEL virtual machine. The blocking module now correctly senses and registers firewall interface IP changes without generating a "tree is null" error and without those invalid kernel IP message errors.
The MD5 hash values for the Suricata binary are different for pfSense 2.4.4 versus 2.5. This is due to the differences in the compiling libraries, but both versions do contain my fix for the problems above.
Hi @bmeeks, unfortunately the problem is still around for me. I tried uninstall and reinstall this morning to see if anything changed, but the md5 is still the incorrect one I posted before. The behavior is still the same as well. I even tried to un/reinstall just before posting this to be sure nothing has changed since earlier this morning. The md5 is still not correct for me.
The MD5 hash you posted last Friday (the one ending in fac7) is the same one I have on my 2.4.4 virtual machine, and that's the version I can't see the problem with. So we need to determine what is different between your setup and my virtual machine.
For starters, is your WAN IP a PPPoE interface or is it a DHCP or static IP setup?
-
@bmeeks said in Suricata Interfaces have to be manually Restarted:
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
@bmeeks said in Suricata Interfaces have to be manually Restarted:
Is this problem with no blocking and/or having to manually restart Suricata still occurring? I have been unable to reproduce this, and I've tried in both a 2.4.4 RELEASE virtual machine and a 2.5 DEVEL virtual machine. The blocking module now correctly senses and registers firewall interface IP changes without generating a "tree is null" error and without those invalid kernel IP message errors.
The MD5 hash values for the Suricata binary are different for pfSense 2.4.4 versus 2.5. This is due to the differences in the compiling libraries, but both versions do contain my fix for the problems above.
Hi @bmeeks, unfortunately the problem is still around for me. I tried uninstall and reinstall this morning to see if anything changed, but the md5 is still the incorrect one I posted before. The behavior is still the same as well. I even tried to un/reinstall just before posting this to be sure nothing has changed since earlier this morning. The md5 is still not correct for me.
The MD5 hash you posted last Friday (the one ending in fac7) is the same one I have on my 2.4.4 virtual machine, and that's the version I can't see the problem with. So we need to determine what is different between your setup and my virtual machine.
For starters, is your WAN IP a PPPoE interface or is it a DHCP or static IP setup?
Ah ok, that's good to know.
My secondary WAN IP is configured via DHCP from my Netgear LB1120 4G LTE modem. This modem is configured in bridge mode. That's the one which changes periodically. It is setup as part of a gateway group for failover. Let me know if you need anything else.
Thanks,
Raffi -
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
@bmeeks said in Suricata Interfaces have to be manually Restarted:
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
@bmeeks said in Suricata Interfaces have to be manually Restarted:
Is this problem with no blocking and/or having to manually restart Suricata still occurring? I have been unable to reproduce this, and I've tried in both a 2.4.4 RELEASE virtual machine and a 2.5 DEVEL virtual machine. The blocking module now correctly senses and registers firewall interface IP changes without generating a "tree is null" error and without those invalid kernel IP message errors.
The MD5 hash values for the Suricata binary are different for pfSense 2.4.4 versus 2.5. This is due to the differences in the compiling libraries, but both versions do contain my fix for the problems above.
Hi @bmeeks, unfortunately the problem is still around for me. I tried uninstall and reinstall this morning to see if anything changed, but the md5 is still the incorrect one I posted before. The behavior is still the same as well. I even tried to un/reinstall just before posting this to be sure nothing has changed since earlier this morning. The md5 is still not correct for me.
The MD5 hash you posted last Friday (the one ending in fac7) is the same one I have on my 2.4.4 virtual machine, and that's the version I can't see the problem with. So we need to determine what is different between your setup and my virtual machine.
For starters, is your WAN IP a PPPoE interface or is it a DHCP or static IP setup?
Ah ok, that's good to know.
My secondary WAN IP is configured via DHCP from my Netgear LB1120 4G LTE modem. This modem is configured in bridge mode. That's the one which changes periodically. It is setup as part of a gateway group for failover. Let me know if you need anything else.
Thanks,
RaffiAnd this is an IPv4 address? I'm trying to understand why I can't see the issue in my testing. I simulate WAN IP changes by going to the firewall interface in pfSense and changing the IP. That triggers the same code as a DHCP change would your box, but it works in my test machine.
-
Yes, it's an IPV4 address. Are there any other logs that might help?
This isn't something a system reboot might fix? I like to avoid that, but I might give it a try if all else fails.
To clarify, I'm not sure if I might have two different problems at least according to the suricata error logs.
Problem 1, when my WAN2 IP changes, I get the tree null errors. I'm not sure how that error manifests itself in terms of software issues. Is that what prevented my alert from not being blocked?Problem 2, when suricata performs a rules update, the status on both my LAN and OPT1 interface go from the green check to the red x and each has to be manually restarted. That was indicated in the log by the "[ERRCODE: SC_ERR_PCAP_DISPATCH(20)] - error code -2"
In case it's relevant, here are my packages.
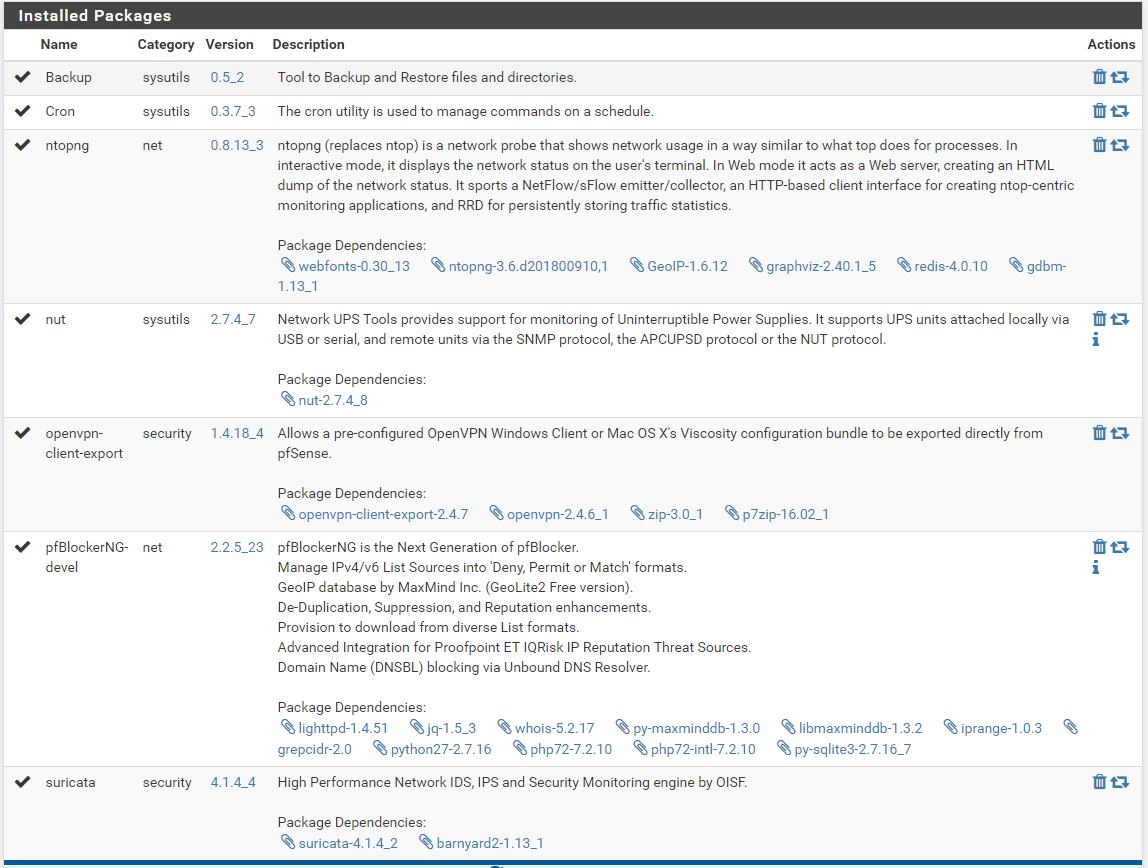
-
Mine seems to be working now, will be keeping an eye on it.
-
I have the same problem, Suricata is not restarting after an update on all the interfaces. Also tried reinstalling the package.
I can start the interfaces manually.MD5: c962d5d995867c5baf3136035a34fac7 -
@digdug3 said in Suricata Interfaces have to be manually Restarted:
I have the same problem, Suricata is not restarting after an update on all the interfaces. Also tried reinstalling the package.
I can start the interfaces manually.MD5: c962d5d995867c5baf3136035a34fac7What messages do you see in the
suricata.logfile for the interfaces that do not restart? I must know what errors are printing to even know where to begin looking for the problem. -
@Raffi_ said in Suricata Interfaces have to be manually Restarted:
Yes, it's an IPV4 address. Are there any other logs that might help?
This isn't something a system reboot might fix? I like to avoid that, but I might give it a try if all else fails.
To clarify, I'm not sure if I might have two different problems at least according to the suricata error logs.
Problem 1, when my WAN2 IP changes, I get the tree null errors. I'm not sure how that error manifests itself in terms of software issues. Is that what prevented my alert from not being blocked?Problem 2, when suricata performs a rules update, the status on both my LAN and OPT1 interface go from the green check to the red x and each has to be manually restarted. That was indicated in the log by the "[ERRCODE: SC_ERR_PCAP_DISPATCH(20)] - error code -2"
In case it's relevant, here are my packages.

Let's first make sure that you don't have a duplicate or zombie Suricata process running. Stop all Suricata instances via the GUI controls, and then open a shell session on the firewall and run this command:
ps -ax | grep suricataYou should see only a single line display (the grep command). If you see any other lines with suricata in them, then kill those processes and try restarting Suricata from the GUI.
Also, at any time in the past have you run a command to manually install Suricata from the shell prompt? Something like
pkg install pfSense-pkg-suricata? Don't do that now, but if you ever did it in the past I found when testing a Snort change a while back that the old copy of the binary installed by the manualpkg installprocess hangs around even when you do a delete and reinstall from the GUI.