New to pfSense
-
I’ve followed the SG-3100 manual to the letter and configured the port 4 as VLAN port. Every thing seems okay except there’s no internet from that port. I don’t know what to do know.
-
And what rules did you put on that initerface? Did you dick with the automatic outbound nat? Network network did you put on that interface.. Are you clients able to ping pfsense IP on that interface?
-
Hi John,
I put IPv4 and IPv6, allow anything to anything. Haven’t touched NAT outbound rules at all (still default to automatic). I connect FMC transmitter/receiver pair to that interface (LAN port 4 or OPT2). At the other far end is a gigabit switch. An access point plugs into the switch. A music server plugs into the switch as well. I have not yet tried pinging from music server to the pfSense IP.
WAN connects to a Comcast Xfinity modem/router which offers wired and wireless internet.
-
I’ve just pinged pfSense IP 192.168.1.1 on the interface. No problem. Actually, ping works on all 4 ports including the configured one and 3 other “raw” ports.
-
What exact IP did you put on pfsense interface in this new vlan? Sure the mask is not /32? Is dhcp working on this vlan? You didn't mess with outbound nat say per some idiot vpn guide? And its set to automatic for your wan?
-
It’s 192.168.100.1
Before getting on the road, I fiddled with system/advance/system tunables, 2 bridge/filter related parameters and it seemed to work. Laptop connected to that interface shows internet. Will dig more after work.
-
You wouldn't be doing anything with bridging!!! You made no mention of bridging in your OP.. You sure wouldn't be bridging your vlan 192.168.100 to your lan 192.168.1
Set your port to untagged in the vlan you want, set the port 5 (the uplink to the soc) to tagged for your vlan... It really is that simple.
Here I have the switch ports with different vlan on port, with 1 being the default lan
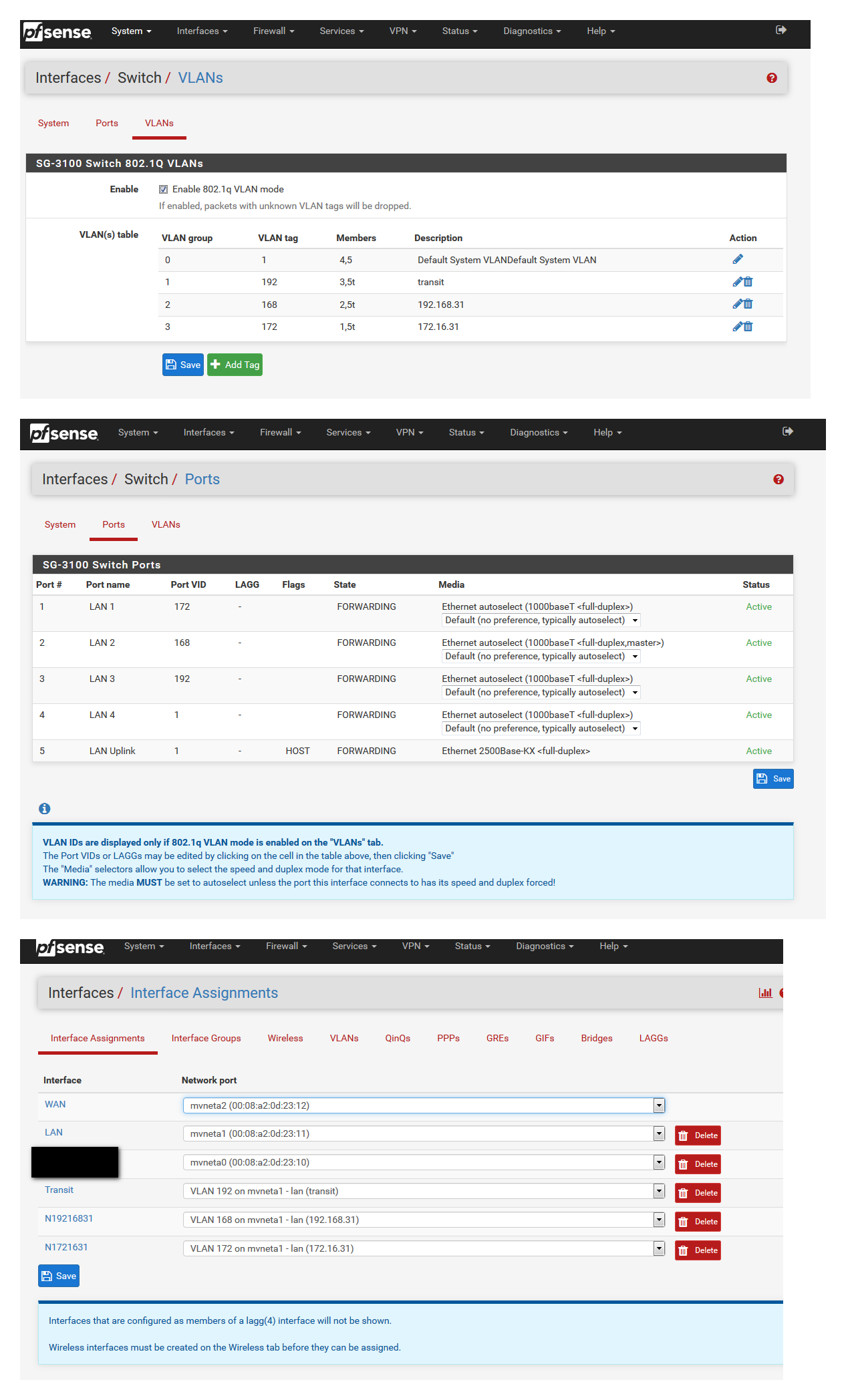
-
No John, I didn’t mention bridging because I had not touched it before posting the last message.
Thanks for the attached screenshot. I’ll get to learn from it after work.
-
@Thuan said in New to pfSense:
I had not touched it before posting the last message.
And why would you think you should? Make no sense!! clicking random shit is not how you correct a problem!
-
You’re right John, it isn’t working. I’m resetting the SG-3100 and starting over again.
-
John, let’s assume that I know nothing about setting pfSense router, and my goal is simple: configure an internet port out of 4 available ports on the 3100. My existing source is Comcast Xfinity modem.
Starting from a factory default 3100 unit, what steps should I take to fulfill my simple requirement: having an internet capable port in which I can plug in a switch and go from there?
-
@Thuan said in New to pfSense:
John, let’s assume that I know nothing about setting pfSense router, and my goal is simple: configure an internet port out of 4 available ports on the 3100. My existing source is Comcast Xfinity modem.
Starting from a factory default 3100 unit, what steps should I take to fulfill my simple requirement: having an internet capable port in which I can plug in a switch and go from there?
It's pretty easy, if you have in fact reset the 3100 to factory defaults.
The SG-3100 has a WAN and 4 LAN switch ports (see image link).
https://www.netgate.com/assets/img/products/sg-3100-back.pngUse the wizard to do all of this. If you setup your WAN port properly (Static IP address or DHCP address from your Comcast modem), that should be good for that one. Then set your LAN switch ports up, using the default 192.168.1.0/24 address range. You can then plug in anything to the LAN ports, even a switch, like you're asking about. Leave the OPT1 port alone for now.
SG-3100 getting-started and setup instructions are here:
https://docs.netgate.com/pfsense/en/latest/solutions/sg-3100/getting-started.htmlIs there anything more complicated with your Comcast connection - VLAN stuff, PPPoE login stuff, TV/Phone/Security thingies, anything...? I don't think Comcast operates their modems with those kinds of settings, but I could be wrong.
Jeff
-
Thanks Jeff for your help, but I have no luck. Not yet. No matter what or how I tried, I can’t see the internet from any port on the SG-3100. I just have no luck with pfSense.
-
And without you posting anything - its impossible to tell you what you are doing wrong...
So your lan has internet? And now you want to do what exactly with the switch ports
-
Hi John,
After configured as instructed in the SG-3100 manual, I have no internet from the only VLAN. The grey areas are firewall and DHCP server setup.
-
And again without you actually posting what you did there is no way for us to tell what your doing wrong.. Users say they did X all the time and come to find out they actually did Y..
You saying it doesn't work is not going to get anyone anywhere.
-
I followed the instructions printed on the SG-3100 PDF manual, pages 7 of 48 thru 12 of 48. At the end, I was told to create firewall rules, so I did. Basically, I created rules that pass ANY from ANY source to ANY destination. Then I was told to enable DHCP, and I did.
In general, I tried to follow exactly what the instructions said, and verified results after each step. Only thing missing is the internet from the newly configured port. That’s why I asked what steps YOU DID to get your results. Experts say doing this or that is easy but they skip the details.
-
And users say they followed instructions xyz... And they really did ABC!!
There is nothing to do other than create the vlan, put an IP on it and create the firewall rules.. That is all that is required.. So until you actually going to post up some pictures of what you actually did..
I showed you how vlans are setup on my 3100.. each port of the switch is on a different vlan. Each one has internet.. When you create a new network/vlan the outbound nat would auto create the outbound nats for you.
There is nothing to do but create the interface, and the firewall rules.. Can your client on vlan X ping the IP you put on vlan X?
What PDF manual? Are you talking about??
https://docs.netgate.com/pfsense/en/latest/solutions/sg-3100/I just went through that - and looks fine... What are you actually connecting to port 4?
-
I have a rather major problem that has only now been brought to my attention via the System Logs. Today, the firewall was reporting many requests on the WAN interface. At the time, I had no idea what the IP address was until I looked further. Turns out, my pfSense gui is available to connect on both my LAN address (10.10.10.10) as well as an address on the WAN DHCP Gateway (100.xx.xx.xx).
I have reconfigured the System settings and changed the port for https, disabled both the webConfigurator anti-lockout rule and Webgui redirect rule (I have created firewall rules to enable me to do this).
There is a VPN connection via OpenVPN however I have disabled all the settings and restarted pfSense and still I am able to access the webgui via the WAN DHCP Gateway address (100.xx.xx.xx).
I have not added any rules to the WAN firewall rules.
I must have overlooked a setting somewhere but cannot find it. Does any one know where else I can look to close this loop hole?
Edit: doing more research it seems the webgui listens on all interfaces. Is there a way to disable this? When I try and access the webgui via my phone on 4G/LTE it is blocked. How did these other external ip’s manage to find my webgui address on the WAN interface?
-
The default rules on the lan would yes allow you to access the gui on the wan address from the lan.. Since the default rules on the lan are any any.
If you want to block lan side access to your webgui on your wan IP, then you would need to specifically block this access.. This is where the "this firewall" built in alias comes in handy.
It will include ALL ips of the firewall..