Unable to block wyzecam
-
Hi, i bought a couple of those $20 wyzecams with the intent of blocking them outside the LAN and only use them locally. Somehow they are able to get through my firewall.
Here are the observations:
-
To set them up, they actually connect to their server so initially the blocking rule is off. They connect, validate whatever and start to work. I can see them on the app.
-
I enable the rule:
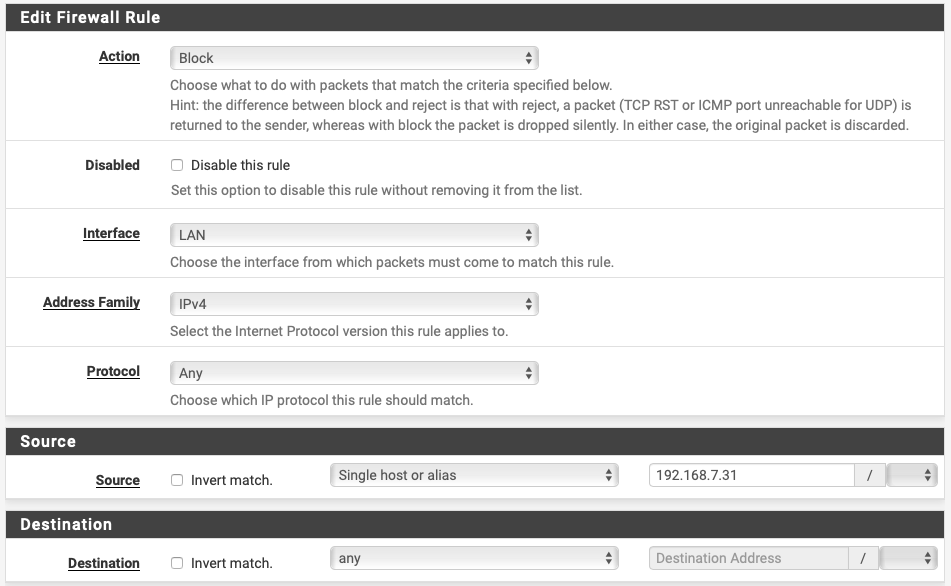
- They continue to work. I can access them from outside the LAN via cellular.
Why?
If i power cycle the cameras, they are effectively blocked, in this case they dont ever leave the LAN they cant connect to the iOS app outside the LAN.
If i repeat the procedure: disable rule, let them connect to WAN, then re-enable rule, they continue to be connected to the iOS app via cellular. UPNP and NAT PMP is disabled. How are they able to continue the connection? is it that after the connection is established the firewall cant stop the traffic?
please help me understand this
thanks
-
-
by default firewall rules apply to new connection, they don't close connection already established. after you enable the rule eventually you can go to diagnostics / states , search for the active connection of the wyzecam and manually remove it
-
@kiokoman thanks that makes sense. So when you enable a rule, it doesn't apply to already established connections. Didnt know that. Sounds basic :)
-
If you have a firewall rule that allows ANY to ANY on an interface, that should create an entry in the state table, behind the scenes on your firewall. Until that original rule is changed and saved, or another rule is created that limits/blocks/restricts that same traffic somehow, the state "should" remain open and traffic will move accordingly.
First paragraph here:
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.htmlSate monitoring can be found here:
https://docs.netgate.com/pfsense/en/latest/book/monitoring/firewall-states-summary.htmlHere's an entertaining video on how it works, behind the scenes:
Firewall State TableSo, I would leave that rule active (your block rule you first posted), move it to the top of whatever interface your net-cameras are on, and if you learn there's a firmware or software update for them, simply disable the block rule temporarily. Let them get the update(s), then activate the rule again to keep them from talking to the internet.
Jeff
-
Forgot to ask... do you want/need to monitor them from "outside" your LAN network?
Jeff
-
@akuma1x hi, no. only local LAN. Actually i returned the cameras. They don't work on LAN-only mode. Even for that they need to send a heartbeat and ack from their cloud server which is stupid and an unnecessary security exposure, so you can't fully block them with the firewall as every 10 mins or so they need that heartbeat signal to keep working so they need to have "open" access to the internet.